Table of contents
- Сan someone put spyware on your phone without touching it?
- 1. Phishing attacks
- 2. Malicious apps
- 3. Exploiting system loopholes
- How someone can spy on your phone without physically touching it
- Signs that your phone is being spied on
- How to protect your phone from remote spying without physical contact
- 1. Update your operating system on time
- 2. Use anti-spy software
- 3. Be careful online
- 4. Use a VPN
- Conclusion
Сan someone put spyware on your phone without touching it?
Yes, spyware can be installed on your phone without physical contact with the device. Cybercriminals and bad actors employ several tricks to gain access to vulnerable devices and steal their sensitive information. While physical access makes it easier to breach your phone and compromise your privacy, remotely breaching it is a commonly used method of invasion.
Good to know
How does spyware work? Spyware steals your personal information and sends it to third parties, such as advertisers, malicious actors, or data collection firms, for profit.
Hackers and bad actors can use the following methods to gain access to your phone and compromise it with spyware:
Read below for more information about the various phishing methods leveraged by cybercriminals to learn what to look out for.
1. Phishing attacks
Phishing attacks are likely the most common method used to compromise your privacy. From a cybercriminal’s perspective, it’s a no-brainer—phishing attacks are a low-cost, low-resource way to hack vulnerable devices.
Interesting
According to a Statista report, in 2023, approximately nine million phishing attacks were detected worldwide. Additionally, almost one million unique phishing sites existed in the first quarter of 2024.
Phishing attacks rely on human error. Here’s how they work:
- Point of contact: Cybercriminals send you a deceptive piece of communication, usually an email, text message, or private message on social media.
- Deceptive methods: In an email or message, they pose as a representative of a company or service you’re likely familiar with. For example, they may pretend to be an official from your bank.
- Obtaining your data: They deceive you into either clicking on a malicious link or asking you to send them your sensitive information.
Unfortunately, the consequences of engaging with a phishing email or message are far-reaching. Clicking on the link can send you to a malicious website that contains spyware. Alternatively, it can prompt your device to download and install spyware without your knowledge. The spyware can remain undetected on your phone for an extended period, negatively impacting its performance and silently collecting your data.
2. Malicious apps
Malicious apps are another entry point for hackers to spy on your phone without touching it. They can take on many forms.
Here’s how bad actors can use malicious apps to collect your data:
- Using fake apps. Cybercriminals can code fake apps with spyware. Such apps mimic legitimate ones with some caveats. Therefore, you can easily overlook them if you don’t know how to spot fake apps. Think of fake apps as bootleg versions of official apps. Apple does a good job of vetting apps and developers, so it’s highly unlikely that you’d download malicious apps from the App Store, though not impossible. Instead, you may unknowingly download and install them from websites on the internet.
- Using legitimate apps such as parental control apps. While inherently innocent, bad actors can use parental apps maliciously. For instance, your partner can send you a link via SMS. Clicking on it can prompt you to download a malicious app, though you might not be aware, as many parental control apps provide an option to hide the app icon to avoid detection. Both of these methods eliminate the need for a spy to physically access your phone and install a malicious app. Here’s a list of apps that spy on you.
3. Exploiting system loopholes
The older your phone’s software is, the more vulnerable it is to being compromised, as cybercriminals can identify and take advantage of security loopholes. Mobile phone manufacturers regularly release software updates to implement new features and fix bugs. Therefore, it’s important to stay on top of software updates to ensure you’re implementing security patches released by your phone’s manufacturer. Failure to do so can result in your device’s system being compromised by bad actors.
What about your camera—can someone see you through your phone camera? Yes, bad actors can breach your camera to spy on you.
How someone can spy on your phone without physically touching it
Bad actors leverage various methods to spy on your phone without physically touching it.
Here’s how:
- Spying apps, including malicious apps and parental control apps.
- Remotely installed spyware, usually through phishing attacks.
- Exploiting vulnerable Wi-Fi networks, underscoring the importance of avoiding public Wi-Fi networks.
Signs that your phone is being spied on
Here are the signs that someone is spying on your phone:
- Spike in data usage. Malicious apps constantly collect your data in the background, causing a sudden spike in data usage.
- Battery draining faster than usual. Your battery suddenly dying faster than it used to is a telltale sign that your phone may contain malware.
- Overheating. Ongoing background activity can cause your phone to overheat.
- Unknown apps. Noticing strange apps is an indication that someone may be keeping tabs on you.
- Suspicious and annoying pop-ups. Spyware can cause annoying pop-ups to appear in your browser.
- A jailbroken device. Jailbroken devices no longer have their security measures in place and are therefore at risk of breaching.
- Strange permission requests. Receiving requests to grant privacy-geared permissions, such as camera and microphone access, could be a sign that someone is attempting to spy on you.
- Strange sounds in the background. Hearing strange sounds or noises while on the phone with someone could indicate someone is listening to your phone calls without your permission. Be particularly suspicious if the noises aren’t coming from the actual call or the person on the other end of the line can’t account for them.
- Activity while unattended. Your phone should remain inactive when you lock it or place it down. If it lights up or shows signs of activity, chances are someone is accessing it remotely.
- Weird text messages. Receiving an influx of text messages from unknown senders could indicate that someone has access to your phone.
- Unexplained browser history. Likewise, noticing searches you don’t recognize in your browser history could point to someone else using your mobile browser.
- Compromised performance. A compromised phone eventually shows signs, such as significantly slower performance and apps behaving erratically.
More signs can alert you when someone is monitoring your phone. Learn more tricks on how to know if your phone is being tracked.
How to protect your phone from remote spying without physical contact
Now that you know how to identify and promptly deal with signs of spying, the next step is learning how to stop someone from spying on your phone.
Implement these solutions to prevent remote spying on your phone:
Successfully preventing remote spying entails implementing a multi-pronged approach. Use the tips below to proactively prevent bad actors from spying on you.
1. Update your operating system on time
Software updates are designed to install software patches that hackers can exploit on your device. By tightening up your system's security, you’ll make it difficult for hackers to breach your phone. Ensure you install iOS or Android updates regularly to keep your phone secure and hackers at bay.
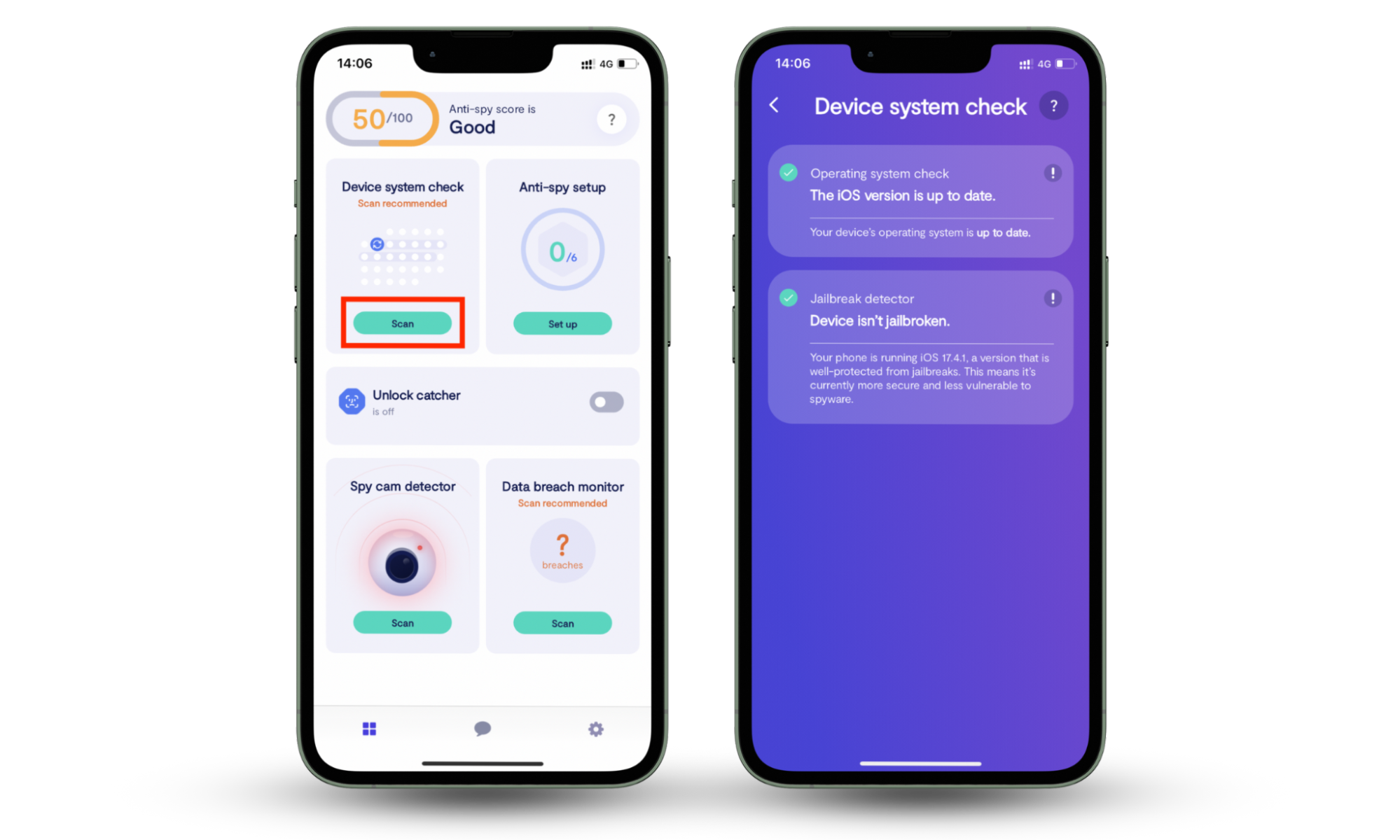
Use Clario Anti Spy’s Device system check to look for software updates and signs of tampering.
- Download Clario Anti Spy on your mobile phone and set up an account.
- Open the app, head to the Device system check section, and tap Scan.
- Clario Anti Spy will check your phone and present a report on what it finds.
2. Use anti-spy software
One of the most effective ways to find out if your phone is compromised is by thoroughly checking it for signs of spying. What better way to achieve that than with specialized software designed to identify and safely remove spying threats? Built with your privacy in mind, Clario Anti Spy’s suite of features comprehensively keeps your mobile phone secure and protects your privacy.
3. Be careful online
We previously mentioned that hackers rely heavily on human error to breach and exploit your device. Therefore, it’s imperative to stay alert and be mindful as you navigate the internet.
- Avoid visiting shady websites.
- Never download attachments from unknown senders.
- Avoid clicking on links in emails, text messages, and social media messages.
- Remove pop-ups in your browser or close the web page—don’t engage with them.
- Be particular about where you download apps from. Your best course of action is downloading apps from official app stores like Apple’s App Store and Google Play. If you intend to download apps from websites, ensure those websites are safe to visit and download from by conducting thorough research first.
To be safe, we recommend that you immediately delete any communication that seems suspicious or from unknown senders. Additionally, block the sender from your emails, phone, or social media accounts to prevent them from contacting you again.
4. Use a VPN
Speaking of the internet, if you aren’t already using a VPN service, it’s high time you considered it. Most people use VPNs to access streaming content that is restricted in their country or region, but they offer way more benefits than that.
Since someone can spy on your phone without touching it, VPNs can help protect your privacy. They connect you to a server in another location, making it seem as though you’re somewhere you’re not. This makes it difficult for bad actors to track your location and spy on you, making it a great solution for keeping them off your tail. Plenty of good VPN services exist. Do your research to find one that best fits your needs.
Conclusion
Can someone spy on your phone without touching it? Yes. Unfortunately, bad actors can spy on your phone without touching it. Due to the nature of remote spying, more bad actors can compromise your phone (rather than the individuals in your circle). This includes your family members, friends, spouse, and even hackers and cybercriminals who don’t know you. For this reason, it’s important to learn how others can spy on you and how you can prevent it.
Use our helpful tips in this guide to empower yourself, including learning how remote spying works and how to avoid falling victim to it. One of the best ways to safeguard yourself against remote spying is by using anti-spying software. Clario Anti Spy’s Device system check is a safe and trusted solution that identifies security loopholes on your mobile phone. Use it to ensure your phone is uncompromised and protect your privacy.


