Table of contents
- What is HawkEye malware
- Signs of HawkEye malware
- How you can get infected with HawkEye
- 1. Email phishing campaigns
- 2. Malicious attachments and droppers
- 3. Social engineering tactics
- How to remove HawkEye malware
- Conclusion
What is HawkEye malware
HawkEye malware is a combination of a remote access trojan (RAT) and a keylogger, allowing threat actors to steal credentials and monitor user activity across infected systems. It was intended to be a legitimate system monitoring tool. Over the years, though, it has grown to be one of the most hazardous spyware apps to look for and a threat to be wary of when browsing the web.
HawkEye targets Windows-based systems, reaching users' devices via phishing emails, mainly as a malicious Microsoft Office file, such as a .docx file.
This malware can harvest user credentials, capture screenshots of user activity, record video through connected cameras, and collect clipboard data. The ultimate goal behind HawkEye spyware attacks on your computer is most likely to use victims' sensitive information for financial gain. So, when attackers have your credentials, they are likely to hack your accounts to make online purchases, make money transfers, etc.
But it is not just your computer that can get infected with malware. See, cyber attacks are primarily all aiming at your data, and they target all types of devices. As you might’ve guessed, mobile devices are the prime target for threat actors. That is why you need to protect your phone with a reliable and robust tool that can combat cyber threats.
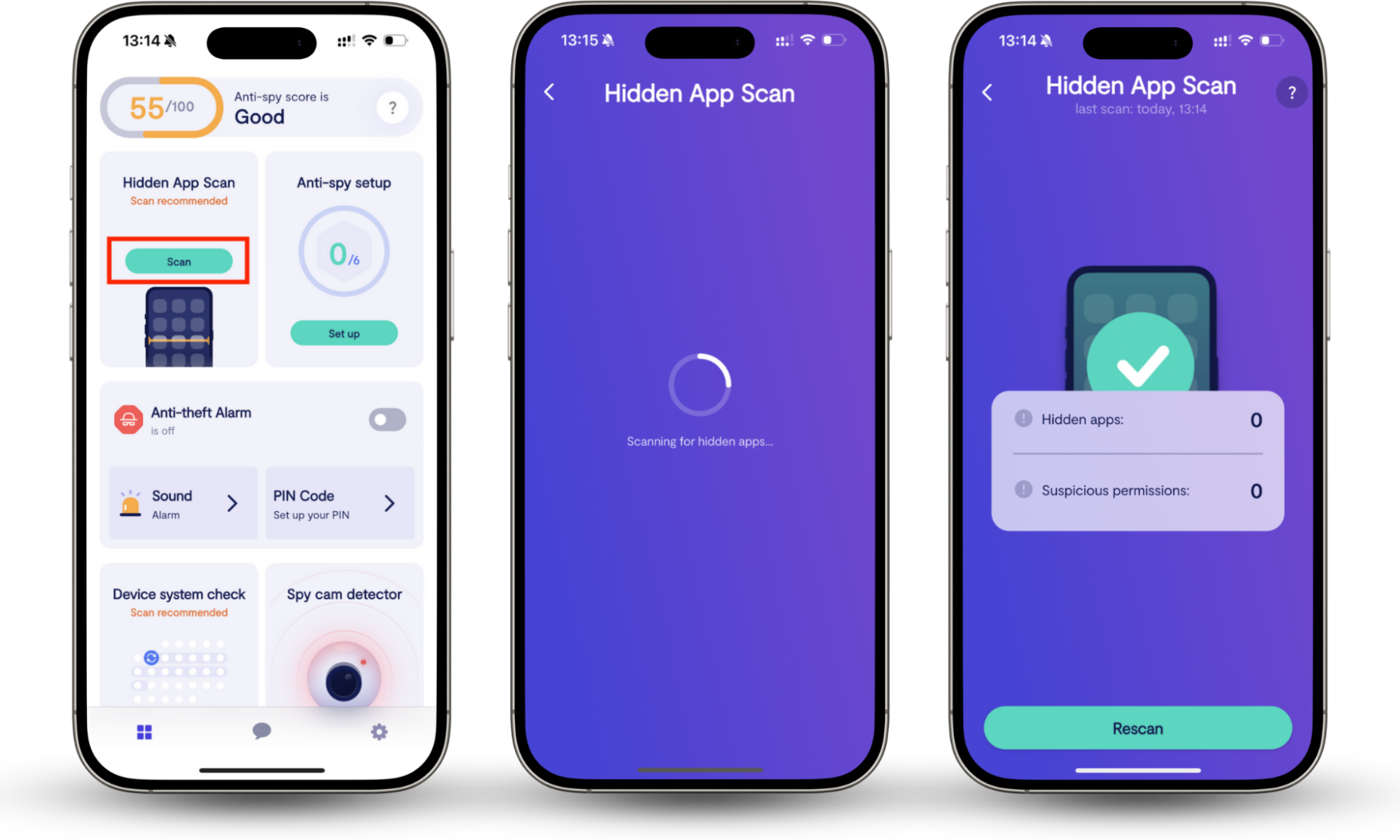
Clario Anti Spy is a cybersecurity tool that aims to protect both Android and iPhone users from hackers. Our Hidden app scan checks your mobile phone for suspicious apps installed without your knowledge, and may appear to be malicious. It will also examine your existing apps and their permissions, so you can make sure you're comfortable with the access these apps have to your data.
Here’s how to start with Clario Anti Spy’s Hidden app scan:
- Download Clario Anti Spy and create an account.
- Go to Hidden App Scan feature and tap on Scan.
- Wait for the scan results. If the tool identifies suspicious apps, it will alert you and advise on further steps.
Signs of HawkEye malware
HawkEye runs in stealth mode, so it can be hard to notice it unless you know what signs to look for. Here are several indicators of possible HawkEye infection:
- Your computer performance has degraded: malware-infected computers typically exhibit high CPU or network usage even during minimal user activity. You may notice system freezes, crashes during startup, or when running security software.
- You receive unexpected credential prompts and security alerts: HawkEye may trigger false security warnings or prompt users to re-login for accounts they've previously accessed without problem. You may also notice new user accounts on your system that you didn't create or authorize.
- Your computer starts running processes you didn't initiate: you may notice indicators informing you that some processes are launched and running in the background. Also, HawkEye may disable or block your access to security tools like antivirus software, leaving your system vulnerable to even more threats.
- You have new or modified existing files in system directories: Malware often hides in or modifies critical system files. Files infected with Trojans, for instance, often contain double file extensions, such as, e.g., invoice.pdf.exe.
Note
Mobile devices act in a similar way when infected by malware. The signs may include abnormal data usage, unfamiliar applications, unusual activity on linked accounts, and slow performance. Look for those indicators when you wonder is there spyware on your phone.
How you can get infected with HawkEye
HawkEye malware spreads through phishing, social engineering attacks, malicious attachments, and fake software downloads. Hawkeye may spread through infected removable media (USB drives, external hard drives) or by exploiting vulnerabilities in your OS.
Let's go through the most common distribution methods.
1. Email phishing campaigns
Phishing is the primary access vector for HawkEye spyware. Hackers send emails pretending to be from legitimate businesses and services. Using urgent language, they prompt you to click on links that lead to downloads of malicious attachments. These files exploit software vulnerabilities or prompt users to enable macros, which then initiate and run the HawkEye payload.
Note
What makes HawkEye keylogger especially dangerous is that it is essentially promoted through Malware-as-a-Service (MaaS) platforms on the dark web. Cybercriminals typically only need to obtain a license, which is usually active for 90 to 365 days. Since the HawkEye itself is easy to use, even for non-tech-savvy attackers, it makes it a powerful surveillance tool.
2. Malicious attachments and droppers
Dropper mechanisms that HawkEye employs allow it to conceal the malware within file types that seem legitimate. For instance, hackers use various types of Microsoft Office documents (.docx, .xlsx, .potx, etc.) to hide malicious macros. They disguise files to seem legitimate business correspondence, resumes, financial statements, etc.
When installed, a HawkEye malware sets up a connection to a command-and-control server. This allows an attacker to remotely access files, webcams, and capture keystrokes. In this case, Hawkeye basically behaves like a remote access Trojan (RAT) that can open the backdoor to your system, gaining full administrative access. So, if you ever wondered if someone can spy on your phone without touching it or if hackers can control your computer remotely, the answer is yes, and they most probably will use RATs.
3. Social engineering tactics
Hackers are known for psychological trickery. With HawkEye, they combine it with technical delivery to increase infection rates. They may contact victims by impersonating trusted contacts or technical support representatives to try to convince them to disable security tools or install software that turns out to be malware.
Creating a false sense of urgency is another tactic hackers use. Using publicly available info, they create highly personalized and convincing messages. They then push users to install security updates, system maintenance requirements, or compliance mandates.
How to remove HawkEye malware
If you suspect your computer is infected with HawkEye malware, you need to remove it asap. To do this, you need to address both the active infection and any persistence mechanisms the malware might have established.
Here's what you need to do to remove HawkEye:
- Disconnect and isolate the infected computer from all networks. Boot the system into Safe Mode to limit the malware's ability to operate.
- Run comprehensive antivirus scans using reputable antivirus software. Better yet, use multiple tools, as HawkEye may be detected by some tools while evading others.
- Try to remove it manually. Check the %APPDATA% and %TEMP% directories for suspicious files, paying close attention to their names. The issue is that HawkEye often uses "Reborn" in the filename or generic process names, such as "BST.exe." Remove any suspicious files and associated registry entries.
- Once you’ve removed the malware, update your OS and security application. Consider changing passwords for accounts that may have been compromised during the infection period.
- Monitor your computer performance closely in the following weeks after HawkEye removal. Consider installing reputable endpoint detection and response (EDR) solutions. Also, monitor network traffic for unusual patterns that might indicate persistent infections or reinfection attempts.
Conclusion
The evolution of HawkEye malware from a monitoring system to a sophisticated Trojan has allowed it to steal user login credentials for the past decade. Due to its commercial availability and modular nature, it is likely that new variants will continue emerging.
But there are ways to prevent your computer from this type of threat. You need to stay cautious about emails and messages that contain links or attachments. Regularly update your OS and have reliable antivirus tools in place that will stay on guard for your computer system security.
For comprehensive protection of your digital life, you also need to protect your mobile devices. If you don’t know how to check for spyware on iPhone or Android, you are in the right place. We have created Clario Anti Spy’s Hidden app scan, which can help you detect and eliminate malicious apps installed without your knowledge and posing a threat to your data safety.


