Table of contents
- Common methods used by scammers to get your personal information
- 1. Phishing attacks: Deceptive emails and links
- 2. Social engineering: Manipulating victims for information
- 3. Spyware and malware: Secretly stealing data
- 4. Data breaches: When your data is leaked
- 5. Publicly available information: Scammers scouring your social media
- 6. Data brokers and people search sites: Buying your identity
- 7. SIM swapping: Hijacking your phone number
- Who is most at risk from scammers
- Signs that your personal information has been compromised
- Legal and practical steps to take if your information is stolen
- 1. Contact affected institutions
- 2. Place fraud alert
- 3. Review your credit reports
- 4. Freeze your credit
- 5. Report to FTC
- 6. Report to police
- 7. Notify IRS
- 8. Inform your health and insurance providers
- 9. Call DMV
- 10. Inspect your devices
- 11. Secure your online accounts
- How to protect yourself from scammers
- Conclusion
Common methods used by scammers to get your personal information
Scammers get your personal information using various methods, from simple social tricks to sophisticated cyberattacks. Here are some of the most common:
- Phishing attacks
- Social engineering
- Malware and spyware
- Data breaches
- Publicly available data
- Data brokers
- SIM swapping
- Dark web
Understanding these methods can help you recognize and avoid becoming a victim. Let's explore each one to discover the best ways to spot them.
1. Phishing attacks: Deceptive emails and links
Phishing is one of the most popular and effective techniques employed by scammers. They send spoofed but deceptively convincing messages via emails, text messages, or social media containing malicious links or attachments. The moment you click on them, Fraudsters can get your personal information by hijacking your login credentials, payment account details, or other confidential data.
Not every phishing email comes in the form of a malicious link—some are good old-fashioned plain-text emails from someone pretending to be your bank manager or a delivery service. Some are more subtle, setting up fake sites that look like hotel booking services. You enter your payment details, and, bam—fake charges start flooding your account.
Some of the most popular phishing scams include email phishing, voice phishing (vishing), and smishing.
2. Social engineering: Manipulating victims for information
Social engineering is the art of psychological manipulation. Criminals impersonate trusted parties—such as customer care agents, relatives, or government officials—to deceive you into revealing confidential information.
Strategies include:
- Pretexting: Creating a fictitious scenario to obtain information
- Baiting: Offering something free (e.g., a prize)
- Romance scams: Establishing false emotional connections
- Quid pro quo: A favor in return for access or information
- Scareware: Scaring consumers into installing harmful software
These techniques utilize emotions—fear, curiosity, trust—to bypass your logic. This eventually causes you to share your personal information, which may help scammers access your social media or banking accounts.
3. Spyware and malware: Secretly stealing data
Scammers employ malware to track your computer and access personal information. Here's a list of tools they can use to monitor you:
- Keyloggers record your keystrokes.
- Trojan viruses masquerade as normal apps while maliciously gathering info in the background.
- Spyware secretly tracks your actions without your consent.
- Ransomware encrypts files on your device until a ransom is paid.
Malware is often bundled with pirated software, false downloads, or phishing attachments. Once it infects a computer, it can capture everything from passwords to online banking information.
4. Data breaches: When your data is leaked
Data breaches happen when fraudsters hack and leak massive databases of user information. These breaches can target:
- Social media websites
- Online marketplaces
- Financial institutions
- Healthcare providers
Exposed information generally includes:
- Names
- Emails
- Passwords
- Social Security numbers
- Credit card details
Where does this information go? It usually goes to the dark web—a secret corner of the internet where stolen information is traded like currency. Your data will likely be sold to the highest bidder. They then use this information to commit fraud, impersonate you, or carry out phishing attacks.
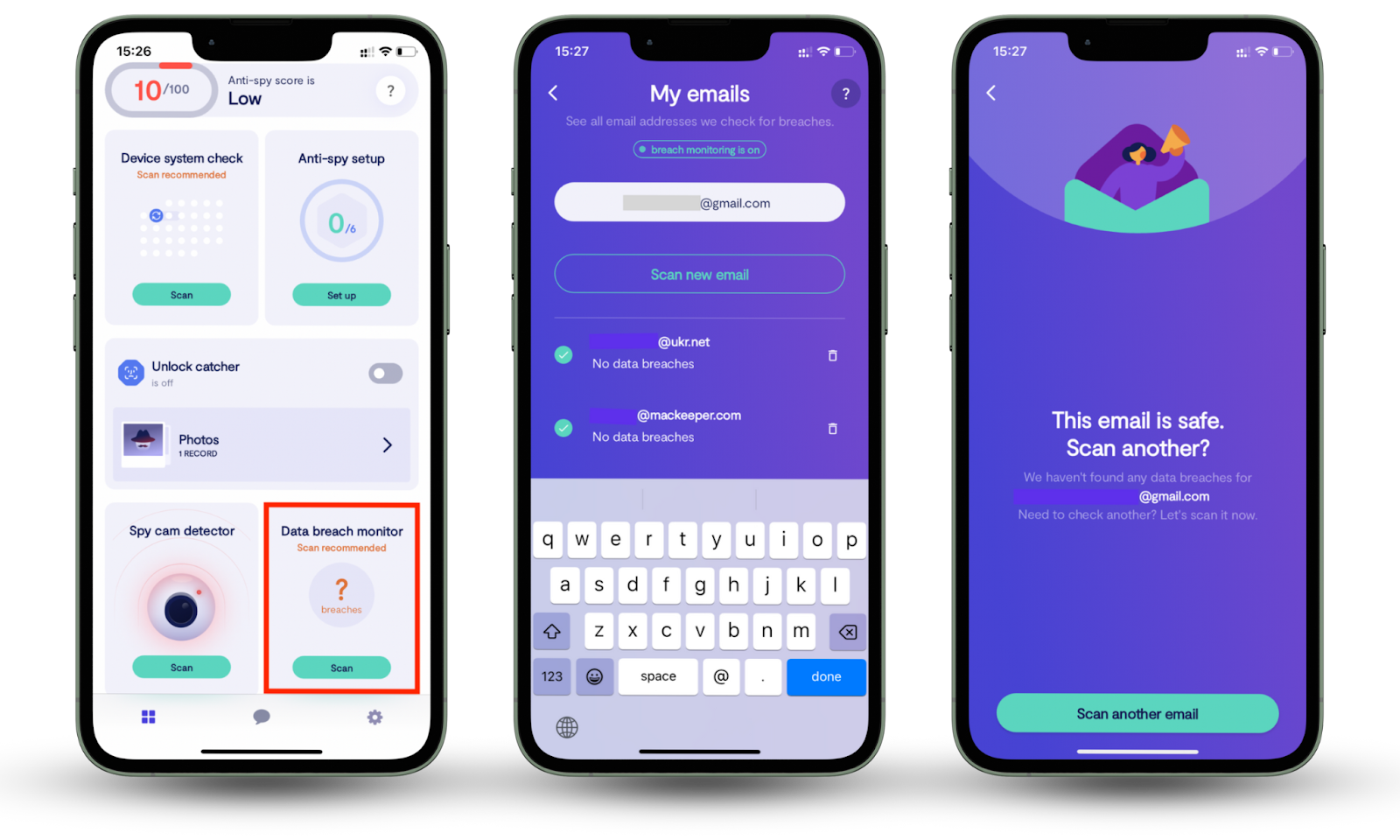
If you are worried your data is floating somewhere in the dark web’s murky waters, there is a way to check. Use Clario Anti Spy’s Data breach monitor to scan the dark web for information associated with your email and learn when your data has been part of a new data breach.
Here’s how to use Clario Anti Spy’s Data breach monitor:
- Download Clario Anti Spy and subscribe.
- Open the app, and under the Data breach monitor, tap Scan.
- Enter your email address and wait for the scan to be complete.
- Follow the on-screen guidance to review any data breaches.
- Repeat the process for any other email addresses.
5. Publicly available information: Scammers scouring your social media
Many people share too much online—and scammers know this all too well. They often comb through public social media profiles, web directories, forums and comment sections, and public documents, such as business licenses or voter registrations.
They collect little bits of information—your birthday, hometown, pet names, or even where you're spending the holidays—to guess passwords, get around security questions, or pose as you with eerie authenticity. A simple family snapshot or "Throwback Thursday" posting would be enough for them to try and target you.
6. Data brokers and people search sites: Buying your identity
On other occasions, scammers take a shortcut and just purchase your data. Data brokers and other people search websites to gather your information to sell it online—sometimes legally. Data brokers can provide:
- Full name, address, and phone number
- Email addresses and social networking profiles
- Work and study background
- Relationships and connections
- Property title and financial statements
Scammers create detailed profiles to commit identity theft or carry out targeted scams. To make things worse, removing your information from these websites can be a real challenge. If you want to erase your information from the internet, you’ll need to opt out of data broker sites manually or use a reputable removal service.
Pro tip
To remove your information from data broker websites, search your name on sites like Whitepages, Spokeo, and BeenVerified. Use their opt-out pages (e.g., whitepages.com/suppression). You may need to verify via email or phone. Or, use a third-party service like GoInvisible or DeleteMe. Recheck monthly—many sites relist data. Pair these steps with Clario Anti Spy’s Data breach monitor to stay alert to new leaks and take fast action when necessary.
7. SIM swapping: Hijacking your phone number
SIM swapping occurs when fraudsters persuade your cellular company to move your phone number to their SIM card. Having succeeded, they can block your messages and calls, bypass two-factor authentication (2FA), and log on to your bank, email, or social media.
They usually employ breached or social-engineered stolen personal information to pose as you when the phone company verifies. By understanding these tactics, you can proactively protect your information. Tighten your privacy settings, avoid oversharing, monitor breaches, and utilize security software like Clario Anti Spy to stay ahead of the scammers.
Who is most at risk from scammers
Individuals between the ages of 35 and 44 are most exposed to and victimized by scams, whereas 18 to 24-year-olds have the highest median financial loss per victimization. Let’s consider the vulnerabilities of each age group:
18–24 years old: Excessive financial losses
- Median loss: $155 per scam
- Common scams: online retail scams, bogus job offers, and social media phishing
- Why at risk? High digital exposure, overconfidence, and lower scam awareness
35–44 years old: Highest rate of exposure and victimization
- The probability of losing money: 58.2% for every scam reported
- Types: investment scams, business impersonation, and computer support scams
- Why at risk? Busy professionals with many responsibilities, regular online shopping, and an increased digital footprint
65+ years old: Largest individual losses
- Median loss: As much as $1,500 per scam
- Typical scams: Government impersonation, tech support scams, Medicare scams
- Why vulnerable? Less digital literacy, more faith in authority figures, easier access to savings
The majority of scam victims never report the crime because they are ashamed, oblivious, or think that reporting the case will not matter. However, underreporting means real risk levels may be even higher for all age brackets.
Read more on the different types of online scams to stay informed and prepared to defend your online privacy.
Signs that your personal information has been compromised
Carefully review scam types and warning signs that your information has been compromised. This will help you identify fraud before substantial damage happens.
| Scam type | How it works | Where it happens | What scammers want | What you can do | Warning signs |
| Phishing | Fake emails, texts, or websites trick you into revealing info | Email, SMS, social media, fake websites | Login credentials, card numbers | Don’t click unknown links, always verify the sender's identity | Unfamiliar charges, password reset emails, 2FA codes you didn’t request |
| Social engineering | Psychological manipulation through impersonation | Calls, messages, in-person, social media | Passwords, SSNs, financial data | Verify identity, never share info over the phone | Unexpected calls from “support,” emotional requests, or fake emergencies |
| Malware & spyware | Software that records keystrokes or silently steals data | Infected apps, fake software, downloads | Everything from passwords to account logins | Use antivirus, avoid pirated software | Your device suddenly runs slow, crashes, or strange popups appear |
| Data breaches | Hackers steal data from company databases | Any online service or institution | Bulk personal info for resale or fraud | Use breach monitor, regularly update passwords | Account lockouts, breach notifications, strange new accounts |
| Publicly available data | Scammers gather info from what you’ve posted or registered | Social media, forums, public directories | Build realistic impersonation for scams | Make accounts private, avoid sharing too much | Scam messages with details you posted online |
| Data brokers | Scammers buy your data from legal or shady vendors | Broker sites, search aggregators | Complete identity profiles for targeted scams | Opt out of data brokers, use removal tools | You appear on people-search sites or get more spam |
| SIM swapping | Scammers hijack your phone number to bypass 2FA | Mobile providers via social engineering | Access to your accounts and messages | Use app-based 2FA, set a PIN with your provider | Sudden loss of service, SIM change texts, 2FA hijacks |
If you notice at least two of the signs described above, learn what to do if you have been scammed.
Legal and practical steps to take if your information is stolen
If your personal information has been stolen, act fast: notify companies where fraud has occurred, place fraud alerts on your credit bureau records, report to the FTC, and report to the police. You should also freeze your accounts and monitor for further exploitation.
1. Contact affected institutions
Notify banks, credit card companies, or other institutions where your data may have been compromised immediately. Attempt to close or freeze accounts and contest any illegitimate charges.
2. Place fraud alert
Call one of the three largest credit bureaus (Equifax, Experian, or TransUnion) to place a one-year fraud alert. This alerts creditors to verify your identity before issuing credit. The bureau you contact will be required to contact the other two.
Here are the contact numbers of the largest credit bureaus you need to call:
- Equifax: 1-800-525-6285
- Experian: 1-888-397-3742
- TransUnion: 1-800-680-7289
It is extremely important to know how to check if your personal information has been compromised in situations like this. Time is of the essence to avoid any serious financial damages.
3. Review your credit reports
Obtain free credit reports from all three bureaus at AnnualCreditReport.com. Mark any unrecognized accounts, hard inquiries, or debts they reported that you did not incur.
4. Freeze your credit
A credit freeze will prevent new accounts from being opened in your name. It will not affect your score or existing credit. You must visit each bureau individually to have it performed.
5. Report to FTC
Report identity theft to IdentityTheft.gov. This will produce an FTC Identity Theft Report—a letter that can be used to dispute the fraudulent accounts and as evidence of a crime.
6. Report to police
Bring the following documents with you to your local police department:
- Your FTC report
- Government-issued identification
- Confirmation of residence
- Proof of identity theft, such as credit reports and debt notices
You may be required to file a police report that might be useful in cases of disputes with creditors or insurance providers.
7. Notify IRS
Call the IRS Identity Protection Unit at 1-800-908-4490 if you believe someone is committing tax fraud or making unauthorized returns using your SSN.
8. Inform your health and insurance providers
Call your health insurance company and healthcare providers to look into suspicious claims or possible cases of medical identity theft. If you need to, request copies of your medical records.
9. Call DMV
If your ID number or driver's license number has been stolen, contact your state's DMV. They can mark your record to help prevent future misuse.
10. Inspect your devices
Perform a malware and antivirus scan to eliminate keyloggers or spyware. Look into security software such as Clario Anti Spy for continuous protection.
11. Secure your online accounts
Reset your passwords for all sensitive accounts. Utilize strong, unique passwords and activate 2FA. A password manager can assist in keeping credentials secure.
How to protect yourself from scammers
To protect yourself against scammers, practice good online hygiene: use various passwords, enable 2FA, post as little personal information as you can online, keep your software updated, and monitor for breaches using software like Clario Anti Spy.
Here are the most effective strategies for protecting yourself from scammers:
- Strengthen your cyber defenses: Have robust and distinctive passwords for every account, enable 2FA where available, and employ a secure password manager to create and safely store your passwords.
- Monitor your digital footprint: Limit the personal details you share online; avoid sharing your birthday, home address, or vacation schedule. Close old accounts that you don't use and maximize the privacy controls on all your social networking sites.
- Think before you click. Do not open emails and attachments from unknown senders, hover over links to check URLs, watch out for emergency messages or suspicious requests since these are usually phishing scams.
- Stay updated and protected. Ensure that the software and applications on your device are regularly updated with the newest security fixes, install anti-virus or anti-spyware software, and regularly back up your data to safe cloud or offline storage.
- Beware of AI-created scams. Beware of voice or video messages that sound off—AI-created deepfakes are increasingly utilized in scams. Confirm identities through an alternate channel before responding to unsolicited or emotional requests for money or personal information.
- Remain well-informed. Subscribe to your national cyber agency's alerts, such as CISA or NCSC. Continuously revising scam awareness material and comprehending how approaches evolve are also important. Utilize Clario Anti Spy's Data breach monitor to determine whether your personal information has been compromised online. Defending yourself does not need paranoia—just proactiveness, persistence, and awareness
Conclusion
Generally, scammers are foragers combing through data breach databases and public profiles and even purchasing your details from data brokers. They use phishing emails and malware, social engineering tactics, and SIM swapping—all to steal your personal information. Being aware of how these attacks work is the first step in preventing them.
Use proactive tools like Clario Anti Spy’s Data breach monitor to stay one step ahead. It continuously scans the dark web and data leak sources for your exposed information, alerting you immediately so you can take action before scammers get your personal information. In a world where digital threats are constant, Clario helps you stay private, protected, and in control.


