Table of contents
- What is a CVV number?
- How can a hacker get my CVV number?
- 1. Phishing
- 2. Malware and spyware
- 3. Skimming
- 4. Data breaches
- 5. Public Wi-Fi networks
- 6. Stolen wallets or lost credit cards
- 7. Dumpster diving for cards and account details
- 8. Formjacking on websites you use and trust
- 9. Account takeovers on your online bank
- How to tell if your credit card numbers have been stolen
- How can I protect my credit card and CVV number?
- 1. Remove CC info from websites
- 2. Review your statements
- 3. Set up alerts
- 4. Use antivirus software and VPNs
- 5. Check websites for a secure URL
- 6. Use strong passwords and two-factor authentication
- 7. Don't write down your CVV or credit card information
- What should you do if your credit card information is stolen?
- 1. Contact your credit card issuer
- 2. Report it to the police
- 3. Update your passwords
- Summary
What is a CVV number?
The CVV number (Card Verification Value) – also known as the card security code, CSC, or CVV2 – is the three or four-digit security code found on your debit or credit card. This is different from your PIN or credit card number.
Where do I find my CVV code?
On MasterCard®, VISA®, and Discover® cards, you can find a three-digit CVV on the back of your card. On American Express® cards, you’ll find CVV on the right side of the front of your card, just above the credit card number.
CVV codes add an extra layer of security to online purchases. This makes it more difficult for hackers to make purchases with your credit card if they gain access to your CC number.
How can a hacker get my CVV number?
Hackers may try to obtain your credit card and CVV number in a myriad of ways, from simply stealing your card to complex cyber attacks.
Protect yourself from credit card fraud by becoming aware of some of the most common ways to steal credit card data.
1. Phishing
Phishing emails are fraudulent messages with the sole purpose of getting you to click on a link and enter your private data into a website.
These emails often look official. They may say they are from your bank and have your bank’s logo and branding. Or they may be from an online store you recently purchased from.
Hackers try to get these messages to appear legitimate to get you to trust them and click through to their site to enter your information.
A common example of a phishing email is PayPal. The victim receives an email that appears to be from PayPal, telling them that their account has been compromised and that it will be deactivated if they don’t confirm their credit card information. A link in the email will take them to a fake PayPal website to enter their information.
2. Malware and spyware
Malware and spyware are common ways hackers will access your credit card information. Similar to phishing, you could receive an email with a link that, when clicked, will download malware onto your device. Clicking suspicious links on websites can have the same effect.
Certain malware has the capability to change your system settings on computers and phones, allowing hackers to gain access to them.
3. Skimming
Credit card skimming is an offline method of stealing your credit card information. The perpetrator will tamper with a credit card reader at an ATM, gas station, or other location and plant a skimming device.
When you put your credit card in, the skimming device will pass your credit card information to the thief.
Other types of skimming include RFID skimming and shoulder surfing.
RFID uses radiofrequency identification technology to intercept transactions from smartphone payments or cards with chips.
Shoulder surfing is what it sounds like. It’s when someone peers over your shoulder (or far away with binoculars) while making you’re making a payment and recording your information, including PIN and CVV.
4. Data breaches
We hear about new data breaches all the time. High-profile companies are usually the targets of these breaches because they have access to tons of user data, which often results in leaked credit card info.
A large online store, subscription service, social media network, or even an online banking system could become the victim of a data breach. So it’s essential to understand what companies have access to your data and stay aware of potential breaches.
Check if your data has been compromised with Clario’s data breach monitor. Follow these simple steps:
- Download Clario and get a subscription to create an account
- Choose Identity on the dashboard
- Click Add email
- Enter your email address and hit Check
- Wait for Clario to tell you if your data has been found in the sold databases
- If Clario finds a breach, follow the steps to mitigate the risk ASAP.
5. Public Wi-Fi networks
You could fall victim to stolen credit card information if you use public Wi-Fi networks. Hackers often create a free, public Wi-Fi network to gain access to sensitive information, like CC info.
One of the most common public Wi-Fi hacks is an evil twin attack. This occurs when a hacker creates a free Wi-Fi network that appears to be a legitimate network.
For example, if you were at an airport, the hacker would set up a Wi-Fi network to mimic that airport’s network. The network's name would look similar to the airport's, sending you to a login screen that looks identical to the airport's legit Wi-Fi login screen. From there, the hacker can access your login credentials and see your internet activity as you browse their network.
6. Stolen wallets or lost credit cards
Sometimes, the easiest way to access credit card information is to find a credit card. Some of the most common places stolen wallets or lost credit cards are found include:
- Public bathrooms
- Fitting rooms
- Restaurant tables
- Checkout counters.
If you lost your wallet or credit card and suspect someone stole it, call your bank or CC provider and cancel it immediately or put a hold on the card until you find it.
7. Dumpster diving for cards and account details
Do you ever throw away documents with sensitive information or even a credit card you're no longer using?
Thieves often look in trash bins for these items. Even if you cut up your credit card, a thief could dig through your trash and piece it together to get the information.
Be careful about throwing out sensitive documents and credit cards, especially in public environments like your workplace.
8. Formjacking on websites you use and trust
Some hackers use a technique called formjacking to hijack a web form. They gain access to a website and add a piece of code that sends the website's form data to them and the website host.
For example, a payment form on your doctor's website was formjacked. When you fill out the form and enter your credit card information, the moment you hit send, all of the information will be sent to your doctor's billing office and the hacker.
9. Account takeovers on your online bank
An account takeover is when someone gains access to your private online banking information and logs into your account, posing as you. Once the hacker is in your account, they can access your banking information and transfer funds out of your account.
How to tell if your credit card numbers have been stolen
When a thief steals your credit card information, there are usually signs. You can monitor your credit report and credit card statements to see if there has been any fraudulent activity on your card.
You may also consider a credit and identity theft monitoring service to review this information for you regularly. These companies can monitor your data and notify you if they see any suspicious activity on your account.
Check with your credit card provider or bank to see if they provide these services.
How can I protect my credit card and CVV number?
Generally speaking, if your credit card has been used for fraudulent purchases, you won’t be responsible for the charges. But that isn’t always the case.
To protect yourself from a stolen credit card, incorporate these security practices into your life.
1. Remove CC info from websites
Don’t save your credit card information, including CVV, on websites.
Common websites that users save credit card info on include:
- Subscription services
- Shopping websites
- Social media networks.
Protect your info by removing your credit card information from personal websites, and don’t allow your browser or phone to autosave this information.
2. Review your statements
Review your credit card and bank statements regularly (at least weekly). This will help you keep track of your purchases.
Watch for any purchases that you didn’t make or don’t recognize. Credit card thieves often start with small purchases to test the card.
If you see any suspicious card activity, contact your bank immediately and pause or cancel your card.
3. Set up alerts
Most banks and credit card companies can set up and send you alerts for your transaction activity. You can set up alerts to receive notifications every time a purchase is made or when a suspicious transaction occurs.
4. Use antivirus software and VPNs
Because hackers frequently gain access to credit card information through public Wi-Fi networks and other online methods, it’s wise to use antivirus software and a VPN (a virtual private network).
You can utilize antivirus software for scanning your devices for malware and other suspicious files regularly, alerting you to any suspicious activity on your computer or phone.
A VPN helps encrypt your online activity, so even if you log into a hacker's Wi-Fi network, your information will be more difficult for them to unravel and steal.
Clario’s software provides powerful antivirus capabilities and gives you a VPN to encrypt your data.
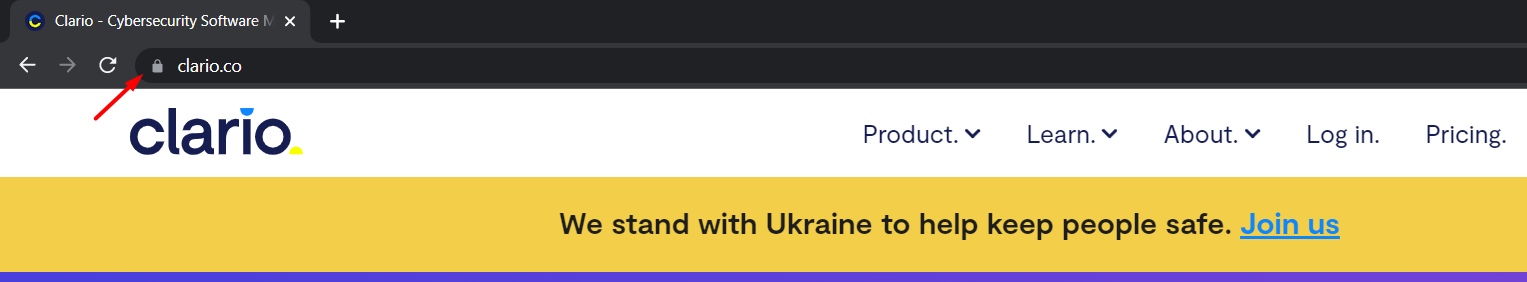
5. Check websites for a secure URL
If you enter payment information into a website–to make a purchase or pay a bill–make sure the payment form has a secure URL.
This means that it has the lock symbol next to it and "HTTPS" in the URL. The S in HTTPS indicates that activity and information that passes through the website are securely encrypted.
6. Use strong passwords and two-factor authentication
Don't use the same password for everything. Always use a unique password for each different login that you have. Include a combination of lowercase and capital letters, numbers, and special characters when possible.
And, when available, opt for two-factor authentication on your personal accounts. Then, if a hacker does access your device or login information, a second layer of security can prevent them from logging in and stealing your credit card information.
7. Don't write down your CVV or credit card information
It can be tempting to write down your credit card information so you don’t have to pull out your credit card every time you need to make a purchase. Don’t do it.
Someone could easily swipe that piece of paper or file and use it to make fraudulent purchases.
What should you do if your credit card information is stolen?
If someone steals your credit card information, there are a few different steps you should take.
1. Contact your credit card issuer
First, contact your credit card provider and let them know your card was stolen. Then, they can cancel your card so the thief can't make any more purchases.
And they can review any suspicious activity and help you dispute transactions that weren’t yours.
2. Report it to the police
If your credit card or wallet is stolen, you should report it to the police.
If you think someone stole your credit card information (i.e., online through Wi-Fi, a data breach, or a malware attack), contact your credit card issuer first, and then they can advise you whether or not to call the police. On large-scale attacks, the police have often already been informed.
3. Update your passwords
Update any passwords on accounts that had access to your credit card information. Or, if you have the same password used on multiple accounts, update all of your passwords.
Make sure your new passwords are strong, unique passwords. Don’t use the same password twice.
Summary
Credit card theft is no joke. It’s a serious crime that can cause harm to a lot of people.
We hope these tips will help you better protect your sensitive data and feel more secure as you engage in online activity.


