Table of contents
- 1. Multiple unsuccessful login attempts are detected
- 2. You receive targeted phishing messages
- 3. Logins appear from unusual or foreign locations
- 4. New or unrecognized devices are logging in
- 5. Account settings are misconfigured or left insecure
- 6. Unusual account activity is taking place
- 7. You receive unexpected password reset requests
- 8. Changes are made to contact information or 2FA settings
- How does account takeover happen
- 1. Fraudsters gain access to targeted accounts
- 2. Theft of login credentials via data breach
- 3. Phishing for login information
- 4. Data theft using viruses and malware
- 5. Man-in-the-middle (MitM) attacks
- 6. Obtaining or developing malicious bots
- 7. Making unauthorized changes
- Account takeover prevention
- 1. Multi-factor authentication (MFA)
- 2. Risk-based authentication (RBA)
- 3. Biometric authentication
- 4. Malware detection
- 5. Phishing awareness
- Conclusion
1. Multiple unsuccessful login attempts are detected
Repeated failed login attempts are among the most obvious early signs of an account takeover (ATO) attempt, especially within a short time frame. Cybercriminals often rely on brute-force attacks or credential stuffing, testing stolen username-password combinations on multiple accounts until one works. Occasional login mistakes are normal, but dozens of failures in minutes should raise suspicions. Enabling multi-factor authentication (MFA) and monitoring sign-in alerts can help you with account takeover detection.
2. You receive targeted phishing messages
Before criminals can compromise your accounts, they often launch phishing campaigns to trick you into giving away your login details. These emails, texts, or DMs may appear personalized and reference services you use. Unlike generic spam, targeted phishing is a clear red flag that someone is preparing to launch an account takeover attack.
If you’re getting unusual requests to “verify your identity” or “confirm account access”, it’s time to be cautious and stay alert. Learn how scammers get your information to prevent phishing-driven ATOs (account takeovers).
3. Logins appear from unusual or foreign locations
If you notice sign-ins from unfamiliar geolocations or IP addresses far from where you normally access your account, this is often an indicator of a compromised login. While VPNs or business travel can cause false alarms, consistent activity from unexpected countries is a strong account takeover detection signal. Many services now offer login notifications—don’t ignore them; they may be your only chance to stop cybercriminals before they escalate their attacks.
4. New or unrecognized devices are logging in
Another important sign of account takeover activity is a login from an unrecognized device. If your bank or email alerts you to a device you don’t own, it means someone may already have your credentials. Attackers often use this method to test access before committing fraud. Always review your account’s “active devices” section, log out of suspicious sessions, and immediately reset your password.
5. Account settings are misconfigured or left insecure
Weak or outdated security settings can make account takeover detection more difficult. If your account lacks MFA, still uses a recycled password, or hasn’t been updated in years, it becomes a prime target. Sometimes, cybercriminals exploit these gaps by altering configurations so victims don’t get security alerts.
Regularly review your privacy and security settings to ensure that compromised accounts are caught early. As one of our customers did—he contacted our Clario support team expressing mild concern about potential surveillance software on his mobile devices.
He had subscribed to our service seeking peace of mind and trusted expert guidance. To address his concerns, our agent guided him through a comprehensive Anti-spy setup, taking a collaborative approach to assess and strengthen his device’s security:
- Conducted a Hidden app scan to check for concealed or suspicious applications
- Used the Data breach monitor to review associated email addresses for any compromised details or unwanted personal information exposure
- Assisted the customer in securing accounts by updating passwords and enabling two-factor authentication (2FA)
- Shared best practices for ongoing device safety and privacy awareness
After completing the checks, no signs of surveillance software or compromise were found. The customer expressed appreciation for the clear explanations and hands-on guidance, and reported feeling reassured and confident in their device’s security moving forward.
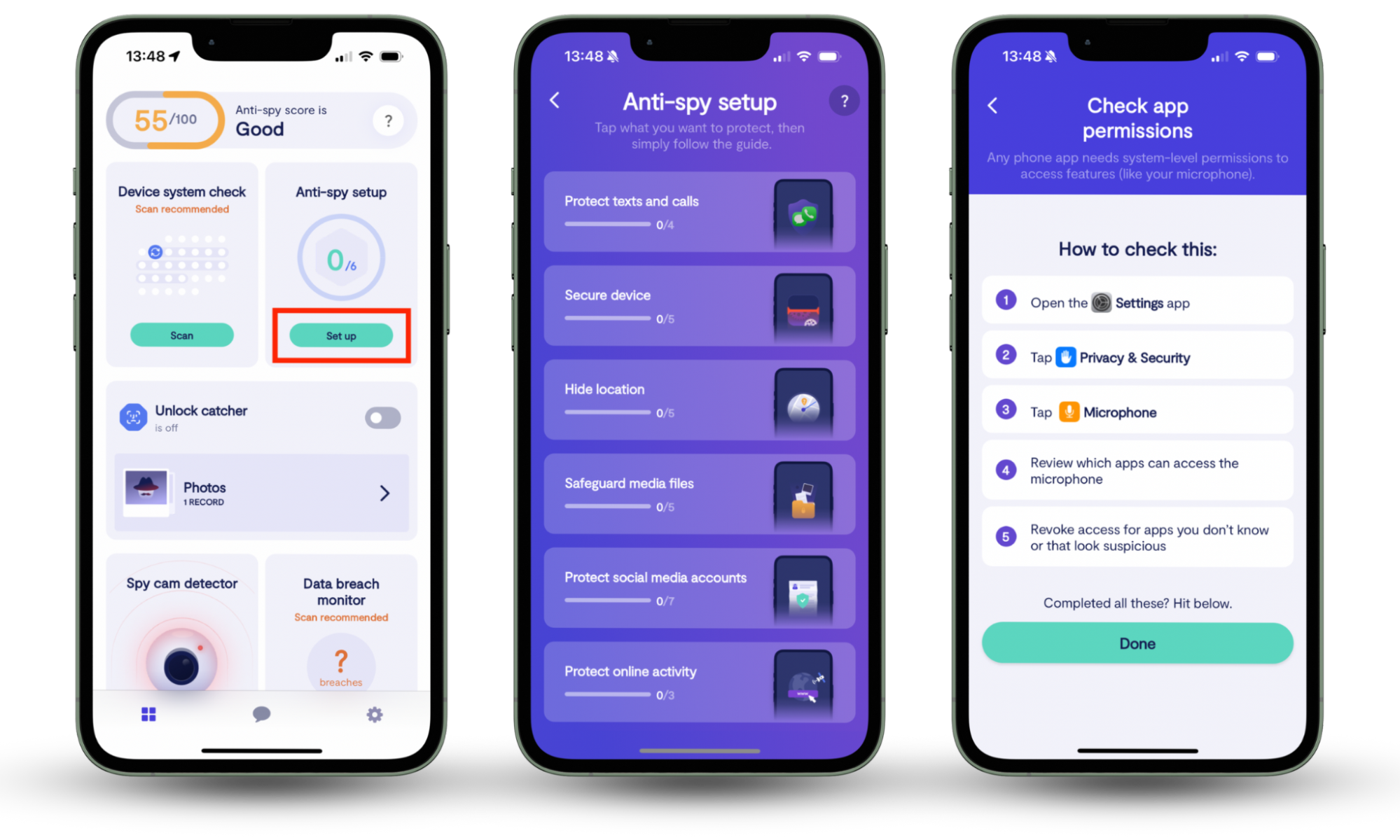
You can feel confident too in the security of your personal details, either by reviewing your security settings every month or choosing a simpler solution—Clario’s Anti-spy setup. This is an actionable checklist that you can use to adjust privacy settings on your device and online accounts to an appropriate level. It is comprehensive, detailed, and effective.
Here’s how to use Clario’s Anti-spy setup:
- Download Clario Anti Spy and set it up on your phone.
- Tap Anti-spy setup and follow each step as instructed.
Pro tip
For additional protection from ATO, use our Data breach monitor. This function scans our recent data breach databases to see if your personal information has been leaked. Why is it important? When your email and passwords are breached, cybercriminals can access your accounts and commit financial fraud. If our Data breach monitor notifies you that your data has been a part of a breach, change your passwords immediately and set up MFA as soon as possible.
6. Unusual account activity is taking place
Unexpected activity, such as strange transactions, modified preferences, or sudden changes in how your account is used, should never be ignored. Fraudsters often start small: testing minor transfers, accessing archived data, or changing notification settings before moving to larger thefts. Monitoring patterns is vital in account takeover detection, as even small anomalies may indicate an attacker is probing your account.
7. You receive unexpected password reset requests
Unsolicited password reset emails or SMS codes are a strong warning sign. Even if the attacker hasn’t gained full access yet, they may attempt to trigger the reset flow to bypass your defenses. Don’t click suspicious links—go directly to the application or website to verify the legitimacy of a request. If these alerts happen repeatedly, change your password immediately and review your account recovery settings.
8. Changes are made to contact information or 2FA settings
One of the most alarming takeover signs is when attackers modify your recovery email, phone number, or 2FA method. These changes aim to lock you out while giving them long-term control. If you receive a notification that someone altered these settings—and you didn’t make the change—it’s critical to act fast. Secure your account, report the incident, and consider placing a credit fraud alert to prevent identity theft tied to the compromised account.
Before we move forward, it is important to note that identity theft is not the same as account takeover. While ATO happens when criminals gain access to an existing account, identity theft involves creating new accounts in your name. You can learn more about the key differences in our guide on identity theft vs account takeover.
How does account takeover happen
ATO happens when cybercriminals steal or trick users into revealing login credentials, often through phishing, malware, or data breaches. Once inside, they may change recovery details, disable security features, and commit fraud. Effective account takeover detection requires monitoring suspicious activity, securing accounts with MFA, and a couple of other methods described below.
Below are some of the ways account takeover happens online:
- Fraudsters gain access to targeted accounts
- Theft of login credentials via data breach
- Phishing for login information
- Data theft using viruses and malware
- Man-in-the-middle (MitM) attacks
- Obtaining or developing malicious bots
- Making unauthorized changes
1. Fraudsters gain access to targeted accounts
The takeover process usually begins with attackers identifying vulnerable accounts. They may choose high-value targets like online banking, e-commerce, or corporate applications. Using stolen personal information or social engineering, cybercriminals attempt to bypass weak security controls, like reused passwords. Early account takeover detection is possible if you monitor for suspicious login attempts or unusual access patterns.
2. Theft of login credentials via data breach
Massive data breaches expose billions of credentials every year. Cybercriminals then reuse these usernames and passwords in credential stuffing attacks, automating login attempts across multiple platforms. Because many people recycle passwords, one compromised account can unlock several others. Regularly updating passwords and avoiding reuse is therefore crucial to preventing fraud.
3. Phishing for login information
Phishing is one of the most common account takeover attack methods. Fraudsters design fake emails, websites, or texts that mimic trusted companies, tricking users into entering login details. Some even use cloned 2FA pages to capture authentication codes. Learning to spot phishing scams is key to avoiding compromised accounts, and understanding the different types of online scams can really help strengthen your defenses.
4. Data theft using viruses and malware
Malware infections can secretly harvest login data. Keyloggers record every keystroke, while spyware can track cookies and browser sessions to hijack active logins. On mobile devices, malicious apps may disguise themselves as harmless games or utilities while stealing passwords in the background. Antivirus tools and cautious app downloads are essential defenses.
5. Man-in-the-middle (MitM) attacks
In a MitM attack, cybercriminals intercept data in transit, often over public Wi-Fi or insecure networks. If you don’t use a VPN while accessing the internet at an airport or a public place, attackers can capture login credentials, personal data, or even inject malicious code. Using a secure VPN is an effective way of staying protected against this form of account takeover.
6. Obtaining or developing malicious bots
Bots are widely used to automate brute-force attempts or credential stuffing at scale. Fraudsters deploy networks of compromised devices to launch thousands of login requests per second. Because bots mimic real user behavior, detecting account takeover through automated traffic is challenging without advanced monitoring. However, unless you hold essential confidential information on your device and are a law-abiding citizen, you should be fine with regular sign-in monitoring and MFA.
7. Making unauthorized changes
Once inside, fraudsters often act quickly to secure their control. They may alter recovery email addresses or phone numbers or disable 2FA. These unauthorized changes prevent victims from regaining access and give criminals time to commit fraud. Monitor security settings closely to detect account takeover in early stages.
Account takeover prevention
To prevent account takeover, enable multi-factor authentication, use strong and unique passwords, and watch for unusual account activity. Organizations should monitor logins in real time, apply device fingerprinting, and train users to avoid phishing. These steps help detect and stop fraud early. Here are the steps you can take to prevent account takeover:
- Multi-factor authentication
- Risk-based authentication
- Biometric authentication
- Malware detection
- Phishing awareness
1. Multi-factor authentication (MFA)
MFA adds an extra security layer beyond just a password. Even if attackers know your credentials, they can’t log in without the second factor, like a phone code or fingerprint.
The first thing you should do after reading this article is turn on MFA for your email, banking, and social media accounts in the security settings and use an authenticator app instead of SMS when possible.
2. Risk-based authentication (RBA)
RBA evaluates login attempts based on context, such as location, device, and time. Suspicious logins trigger extra verification, reducing the chance of unauthorized access. If your bank or service offers “suspicious login alerts” or “adaptive authentication”, enable them so you’ll be prompted for extra checks if something doesn’t look right.
3. Biometric authentication
Biometrics (fingerprint, face, voice) tie your login to your identity, making it nearly impossible for fraudsters to copy. Where available, enable Face ID, Touch ID, or fingerprint login in your mobile apps. For organizations, encourage staff to use devices that support biometric logins.
4. Malware detection
Malware, spyware, or keyloggers can steal login details while operating silently in the background. Cybersecurity tools detect and remove these threats before they compromise your account. Install a trusted antivirus or anti-spyware app, like Clario Anti Spy, on your phone and computer. Keep it updated, and regularly run scans to ensure no malicious software is tracking your data.
5. Phishing awareness
Phishing remains the number one cause of stolen/taken over accounts. Fraudsters mimic trusted companies to trick you into revealing login data. You need to always hover over links before clicking, double-check sender addresses, and never enter credentials on pages you reached through suspicious emails.
Conclusion
Detecting account takeover early is essential to protecting your identity, money, and online privacy. Watch for unusual logins, phishing attempts, and unauthorized changes in account settings. Combine strong authentication with continuous monitoring for effective ATO detection—and use Clario’s Anti-spy setup for an easier, guided, and ultimately more secure solution.


