Table of contents
- What is browser hijacking?
- Signs your browser has been hijacked
- How to remove browser hijackers from Chrome
- How to remove browser hijackers on Mac Safari
- How to prevent browser hijacking
- Conclusion
What is browser hijacking?
Browser hijacking happens when malicious software (called hijackware) changes the settings of your internet browser without your permission. Hijackware can cause a lot of damage, like crashing your browser, holding your device hostage with ransomware, installing spyware, or replacing your homepage with a malicious website.
You can accidentally infect your computer with hijackware from an infected website, file-sharing platform or by downloading freeware, a browser extension, or email attachment.
Right now, you’re probably wondering why anyone would want to hijack your browser. Well, hijackers want to make money from your data and online activities. And some hackers attack browsers just for the fun of it. It helps them elevate their status within the hacking community.
Don’t get rattled, though, because we’ll help you fend off these attackers. But first, you must learn to spot the hijacking signs.
If you're using an iPhone and notice signs of browser hijacking, it could point to something serious, like a hidden jailbreak. Normally, iPhone browsers are hard to hijack because of iOS restrictions, which is why running a scan is a smart move.
Clario Anti Spy is an anti-spyware solution that can help with that. Its Device system check feature detects hidden jailbreaks and compromised versions of iOS that might let malicious apps hijack your device.
Here's how to run a Device system check with Clario Anti Spy:
- Download Clario Anti Spy and subscribe to create an account.
- Tap Scan under Device system check.
- Follow the on-screen steps to address any security issues.
- Tap the Message icon for 24/7 expert support if you need help.
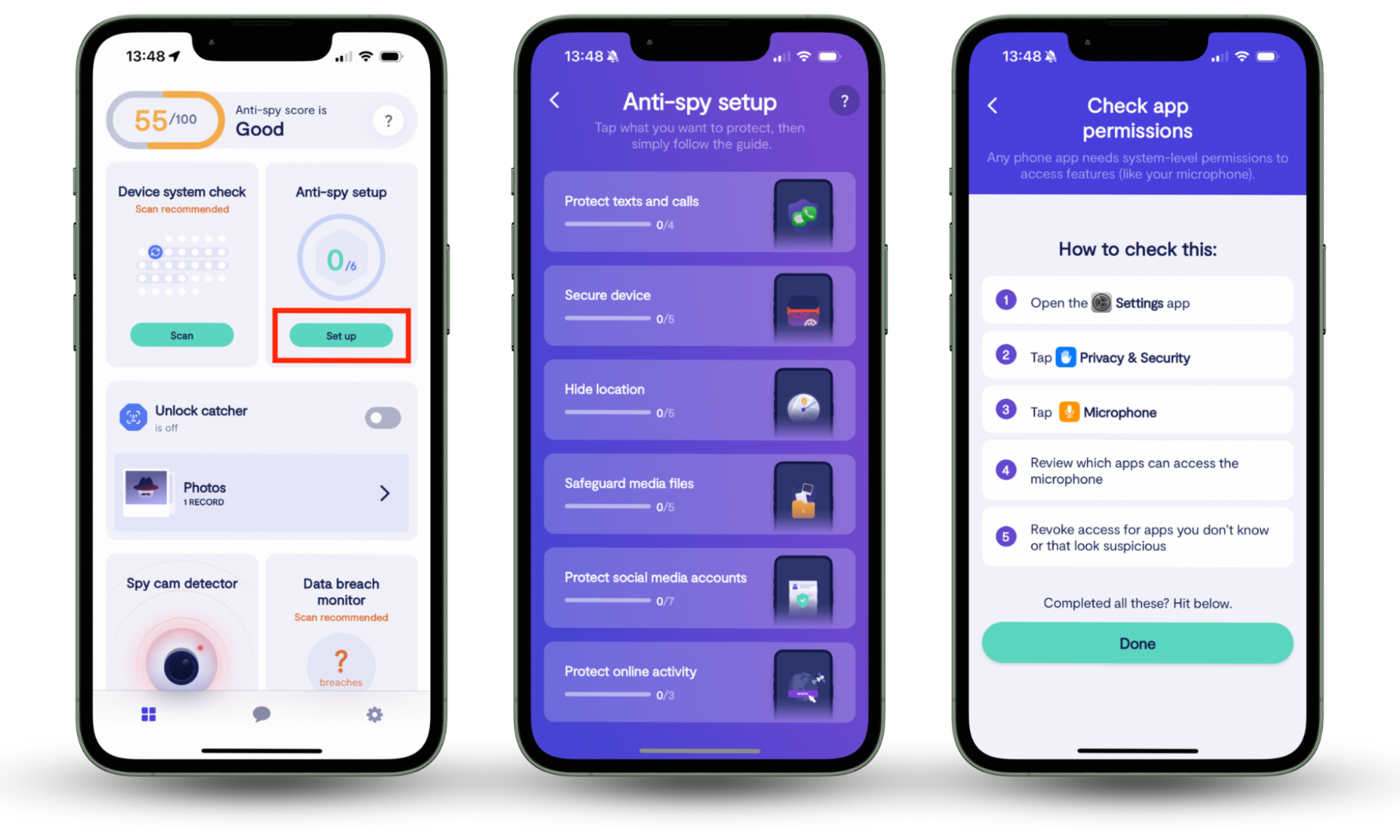
We recommend running an Anti-spy setup as well to tighten privacy settings related to web browsing, social media, and app permissions. Also, don't forget to activate the Data breach monitor to get alerts if your email and passwords end up in a data breach.
Signs your browser has been hijacked
In general, you can easily spot if your browser has been hijacked. Here are some telltale signs to watch out for:
- Your homepage looks different
- Your passwords won’t work
- You see new favorites or unknown sites in your bookmarks bar or bookmark manager
- Your browsing sessions become too sluggish
- Your browser settings change back after you’ve made your own modifications
- Your mouse starts moving on its own
- Unusual pop-ups suddenly appear, asking you to buy something or visit particular pages
- Your internet searches get redirected to sites you didn’t intend to visit, and the results make no sense. This is called DNS redirection, and means a hacker has control of your browser and can send you to websites of their choice
- You’re missing money in your online accounts. Hackers access private bank details and use them before you even realize you’ve been hijacked
- You see your confidential information online. If your data turns up somewhere unexpected, you should immediately check to see if you’ve been hacked
- You see scareware or ads saying your antivirus software is out of date and you need to purchase it again right away. In these cases, you’ll be redirected to a malicious website where hackers can access your credit card details
- You fall victim to ransomware, and hijackers restrict access to your files unless you pay them money
- New browser toolbars that you didn’t select start appearing in your browser
If you notice these signs but ignore them because you believe in the invincibility of Macs, we have some bad news. Although Macs are less vulnerable to malware than PCs, they’re still vulnerable, and browsers are frequently a point of entry for malware. We’ll show you how to get rid of browser hijackers on Chrome and Safari.
How to remove browser hijackers from Chrome
Do you see signs of infection in your Chrome browser? Then follow these quick and easy steps to remove browser hijackers:
1. Launch Chrome and type chrome://extensions in the address bar.
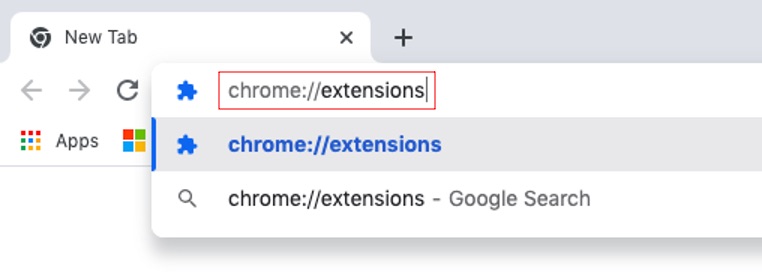
2. Look for any browser extensions you didn’t add.
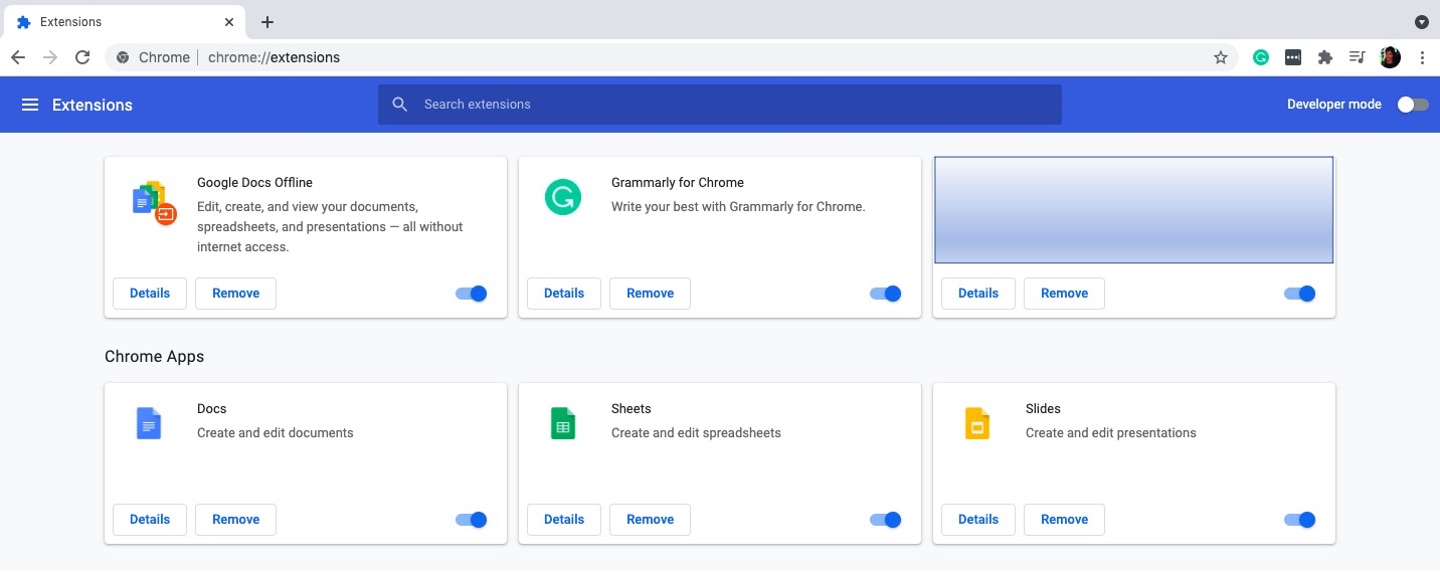
3. If you see an extension you don’t recognize, click Remove.
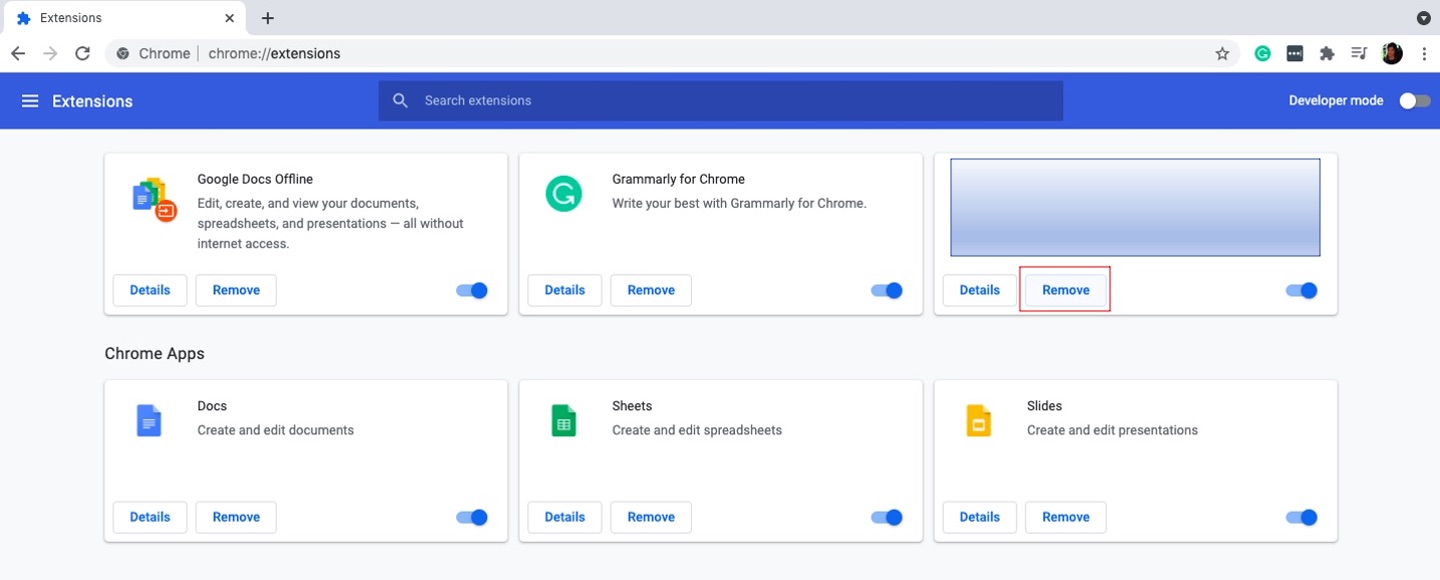
4. Next, type chrome://settings in the address bar.
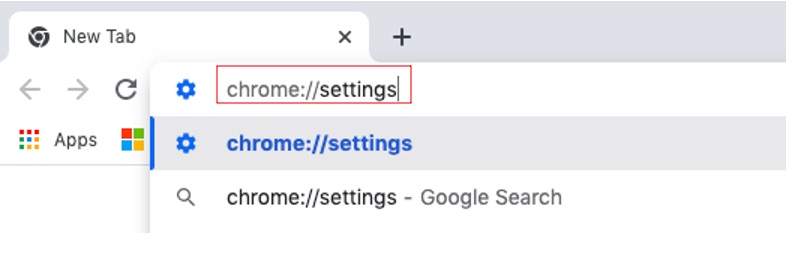
5. Click On startup.
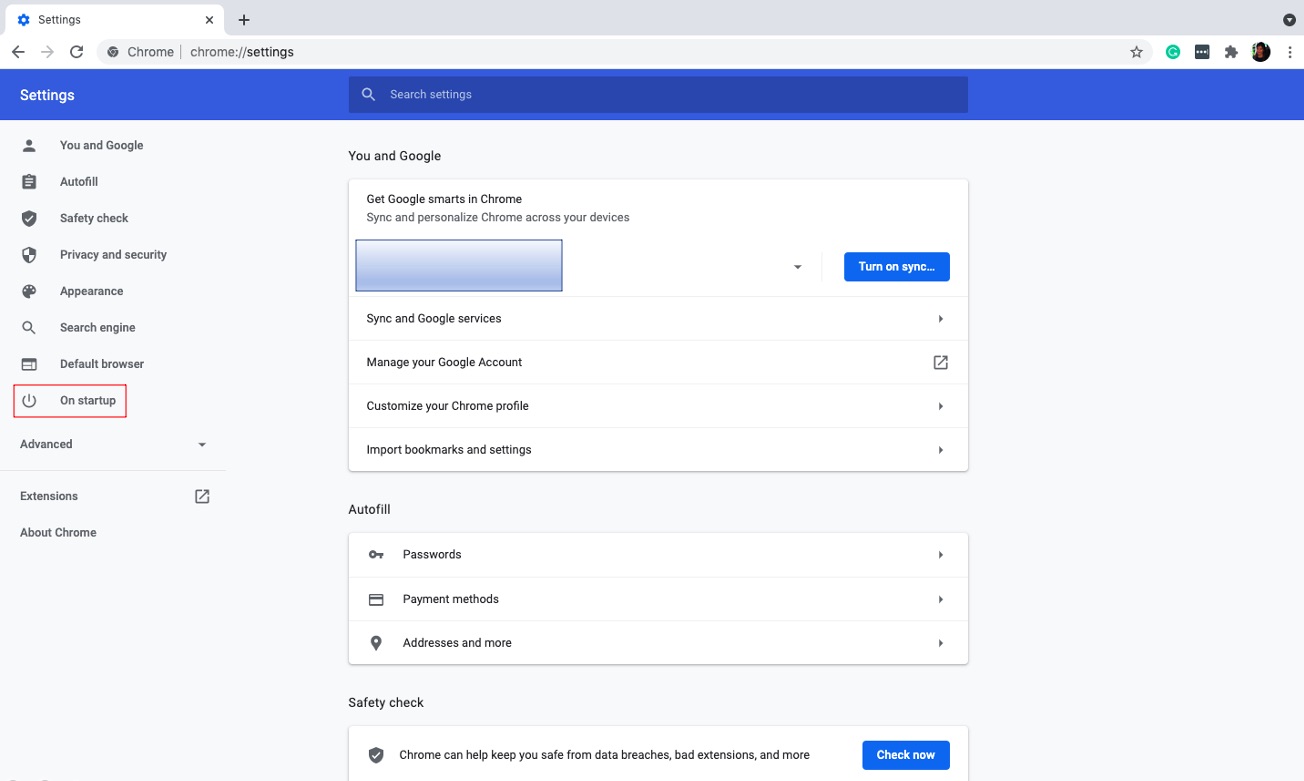
6. Choose the page you’d like to see when launching the Chrome browser.
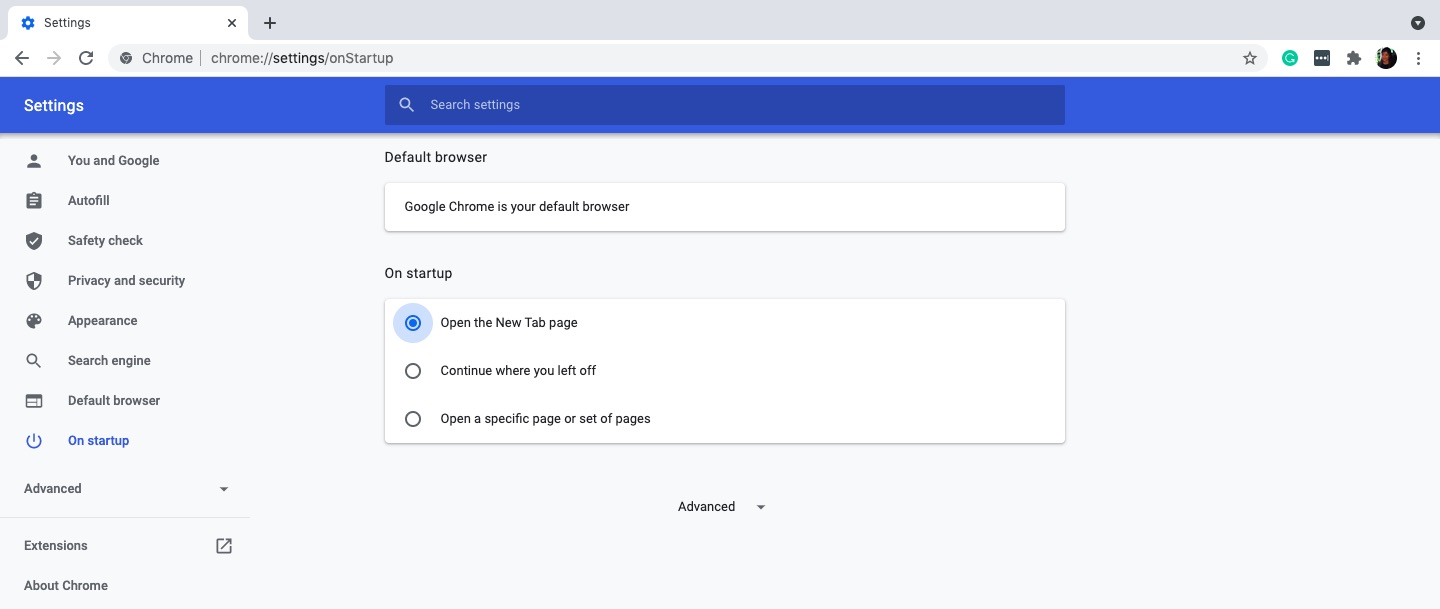
You can add a specific site as your Chrome startup page.
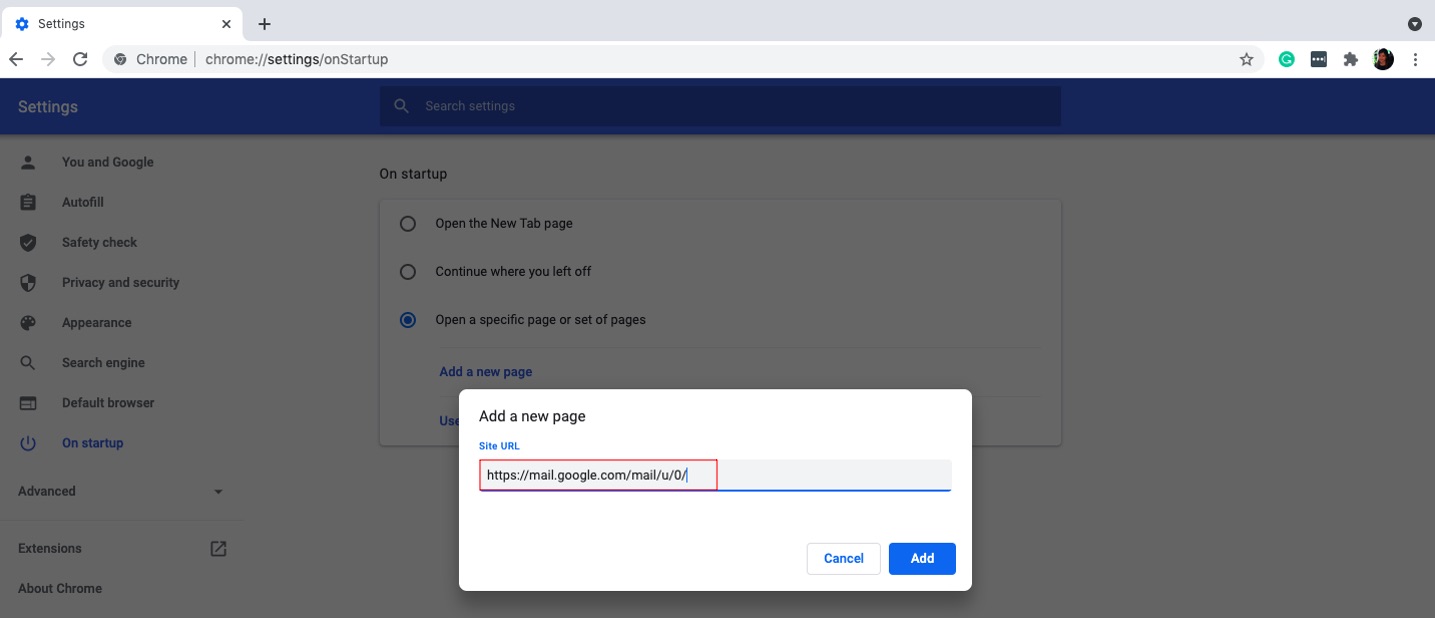
7. Go to the Search engine section.
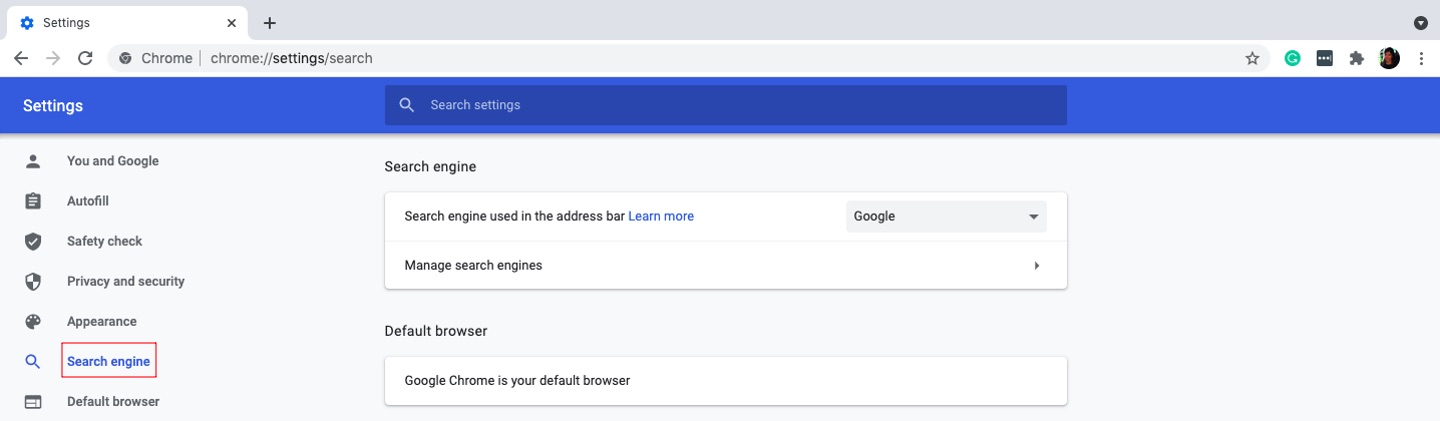
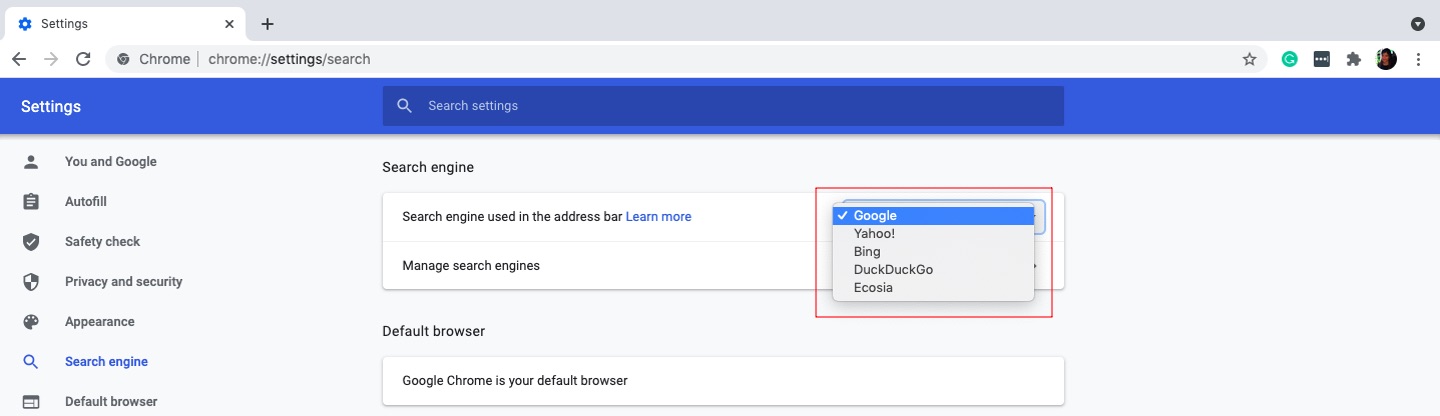
8. Choose a default search engine.
Taking these steps will help keep your Chrome browser safe from hijackers!
How to remove browser hijackers on Mac Safari
Do you see signs of Safari browser hijacking? Here’s how to manually remove any hijackware:
1. From the Safari menu in the upper left corner of your screen, select Preferences or Settings.
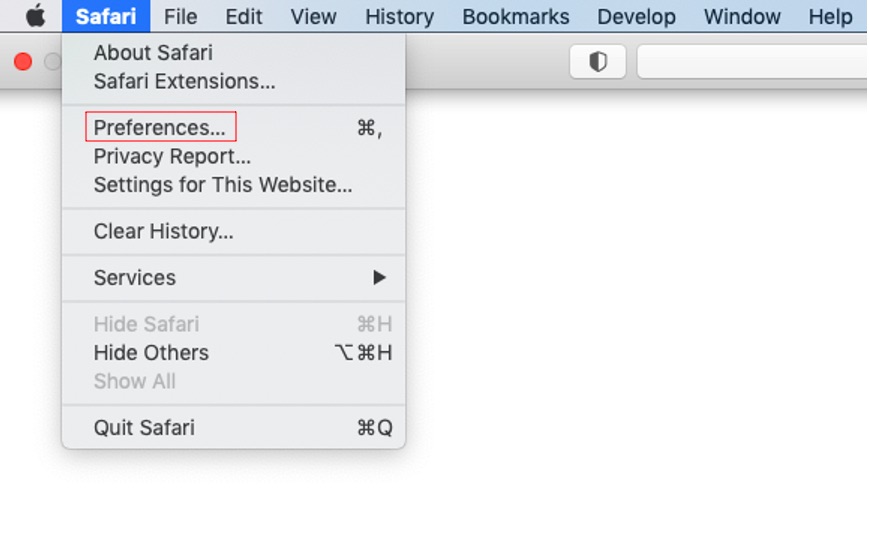
2. Go to the Extensions tab.
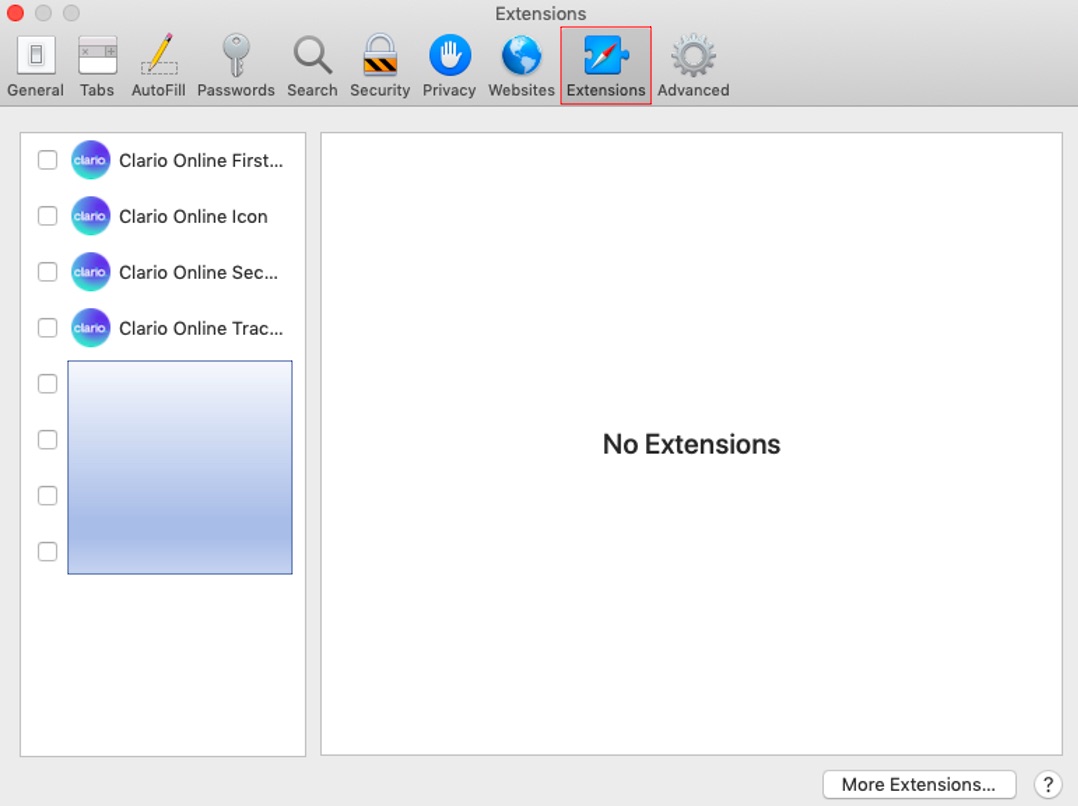
3. Click Uninstall to remove any unknown extensions.
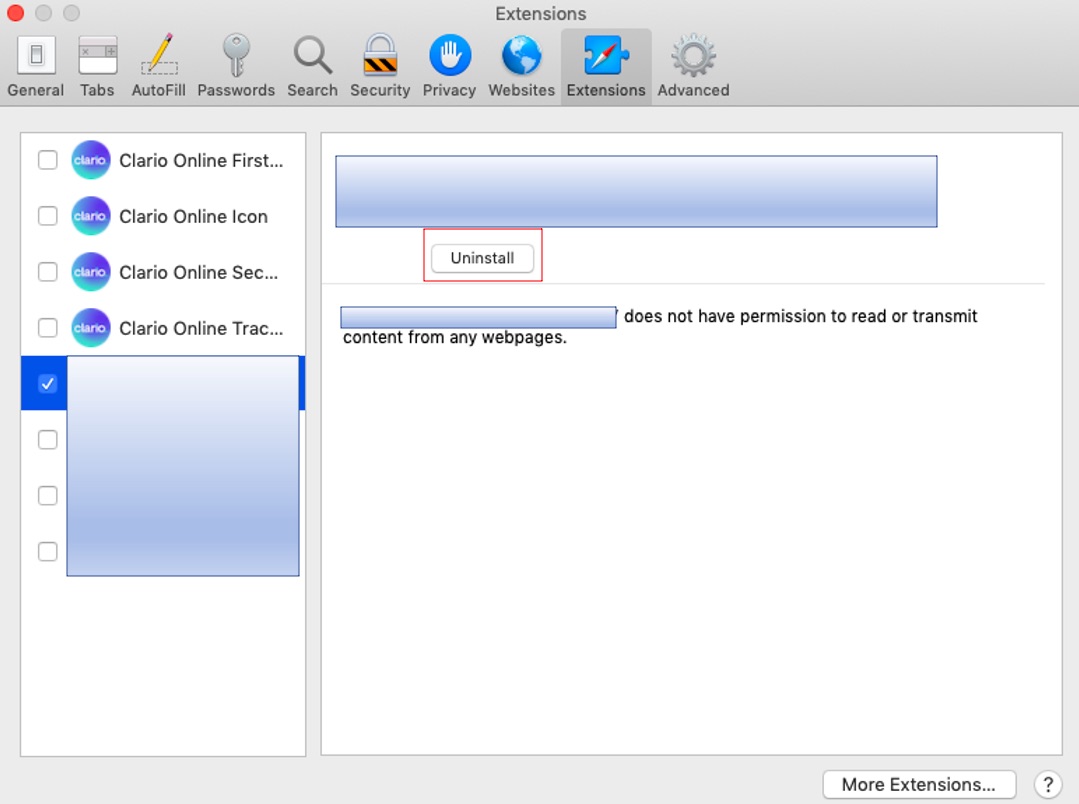
4. Next, navigate to the General tab.
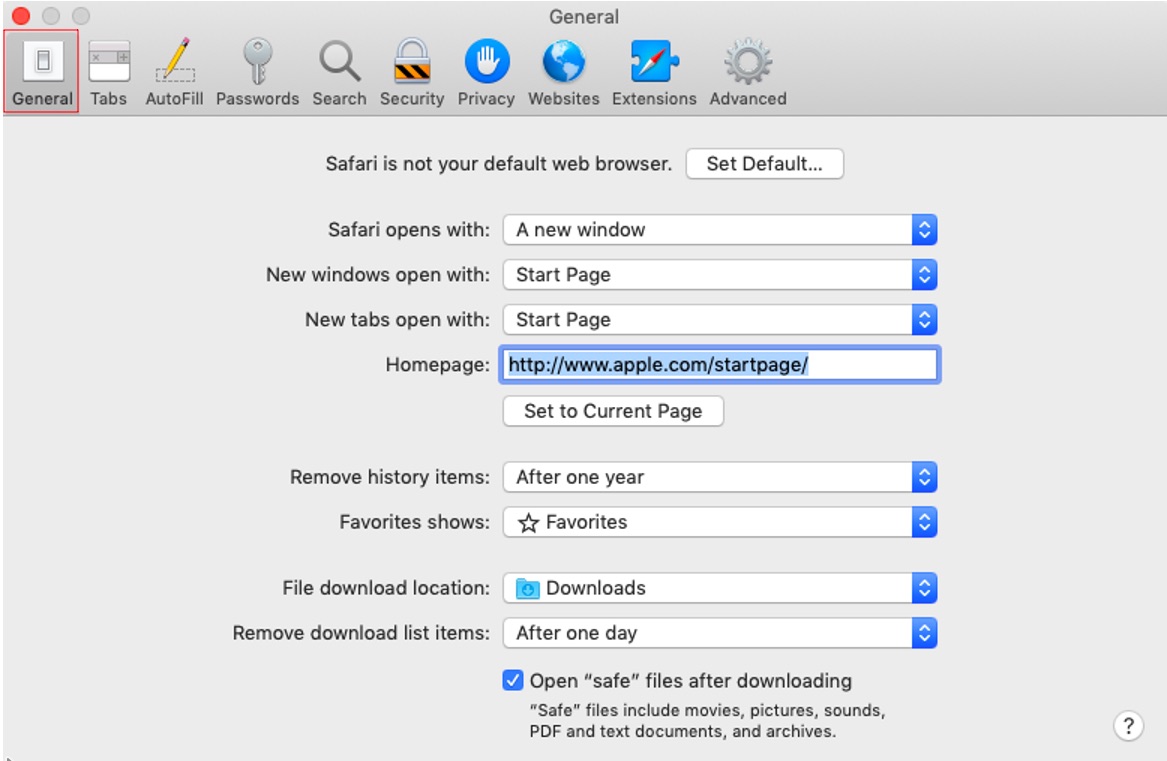
5. Add your preferred startup page to the Homepage field.
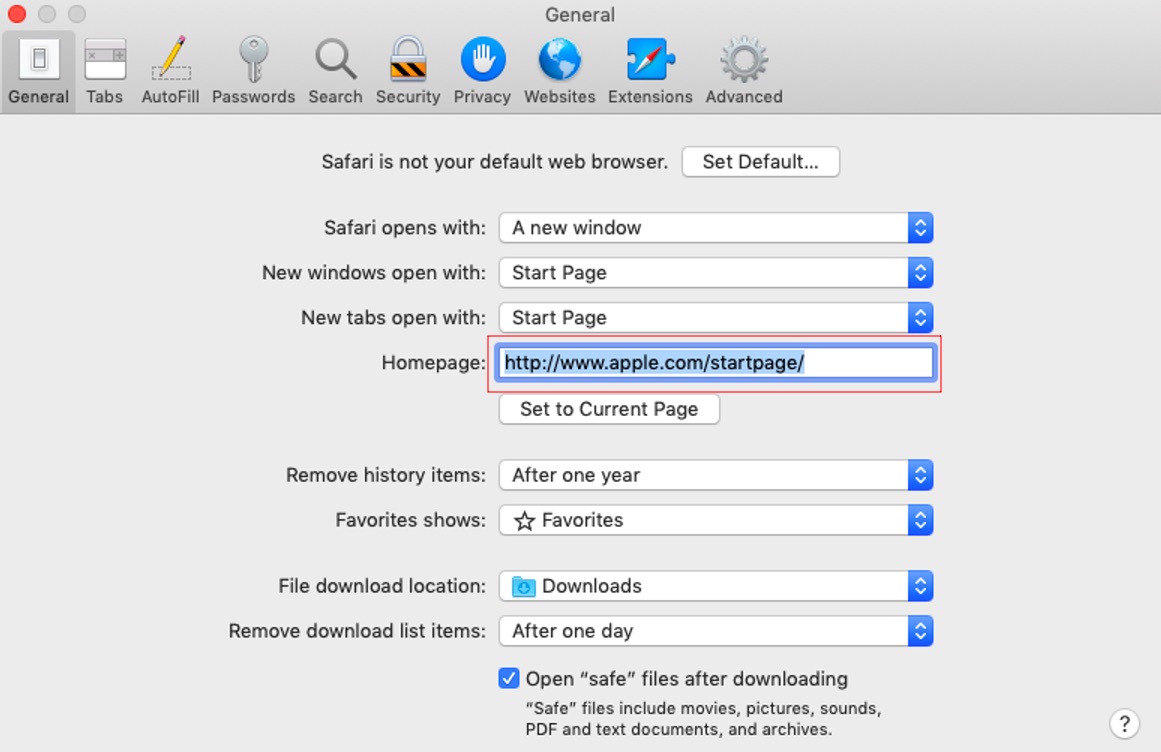
6. Finally, go to the Search tab.
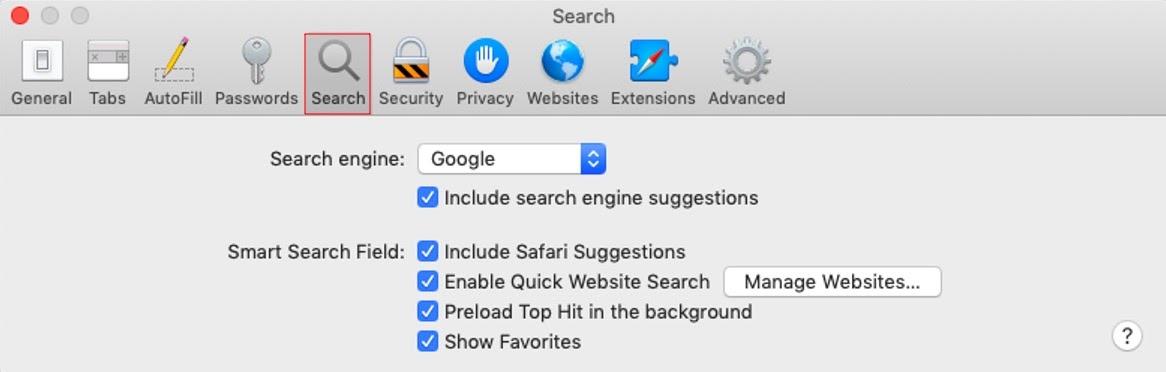
7. Select your preferred search engine.
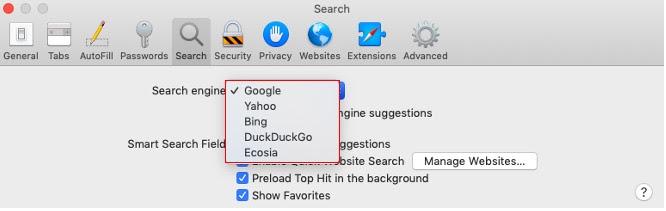
Voila! Enjoy your hijacker-free Safari. Now, how can you keep the hijackers at bay?
How to prevent browser hijacking
There are lots of ways to protect yourself against browser hijacking. We list some top tips below:
- Use Google Safe Browsing. This Google service lets you browse online in a safe mode and alerts you if you happen upon a malicious site or network. Google crosschecks a vast list of phishing and malicious sites to protect you.
- Never click attachments from unknown senders. Just as you might be suspicious of a large, anonymous package in the mail, don’t open an email if you don’t know who it’s from.
- Make sure you use the latest versions of your browsers and operating system (OS). Browser hijackers look for vulnerabilities in your browsers and OS. One purpose of updates is to fix vulnerabilities. By making sure browsers and OS are up-to-date, you prevent hijackers from exploiting these vulnerabilities.
- Only download trusted software or attachments. Always take the time to read the small print.
- Use an alternate DNS resolution provider to stop DNS hijackers from redirecting you to pages you don’t intend to visit.
Conclusion
Browser hijacking leaves you open to different forms of browser manipulation and fraud. It’s increasingly an online threat and, if left unchecked, can expose your confidential personal data and cost you money. But you can’t protect yourself against it. To protect your Chrome or Safari browser from hijackers, practice digital hygiene, like updating your browsers regularly. On iPhone, Clario Anti Spy provides strong all-around security by helping you fix vulnerabilities that could be exploited to spy on you


