Table of contents
- What really happened
- Who’s affected?
- What are the consequences?
- What you can do now?
- Why MOAB is unreal and why using Clario Anti Spy matters
- Final take
What really happened
The MOAB isn’t a single corporate breach—it’s a massive compiled breach list, aggregating data from years of smaller leaks, info-stealing logs, and credential-stuffing dumps. Yet the sensitive data appears recent—frighteningly fresh, not decades-old remnants—making this a true mother of all breaches.
According to Cybernews, these datasets hold login/password combos, cookies, session tokens, and more—from services like Google, Facebook, Apple, Telegram, GitHub, and even government portals.
Malware known as infostealers appears to be the primary culprit, quietly siphoning credentials from infected devices.
Who’s affected?
- If you reuse passwords across platforms, you may be compromised. If one password is leaked, all are at risk.
- Developers, businesses, and government users are targeted by infostealers for corporate espionage or nation-state hacking.
- Users of major platforms (Google, Facebook, Apple), though those platforms weren’t themselves breached, threats arise because of malware and credential stuffing.
What are the consequences?
- Account takeover: Cybercriminals can exploit credentials and tokens to bypass controls, even 2FA in some cases.
- Phishing and scams: Weaponized data fuels phishing, identity theft, and extortion.
- Mass exploitation: With credentials leaked in troves, attackers can target millions at once.
By comparison, a mysterious 184 million record leak now seems small next to this latest MOAB event.
What you can do now?
- Immediate hygiene fixes: Change all weak or reused passwords, enable 2FA or, better yet—passkeys—on every service.
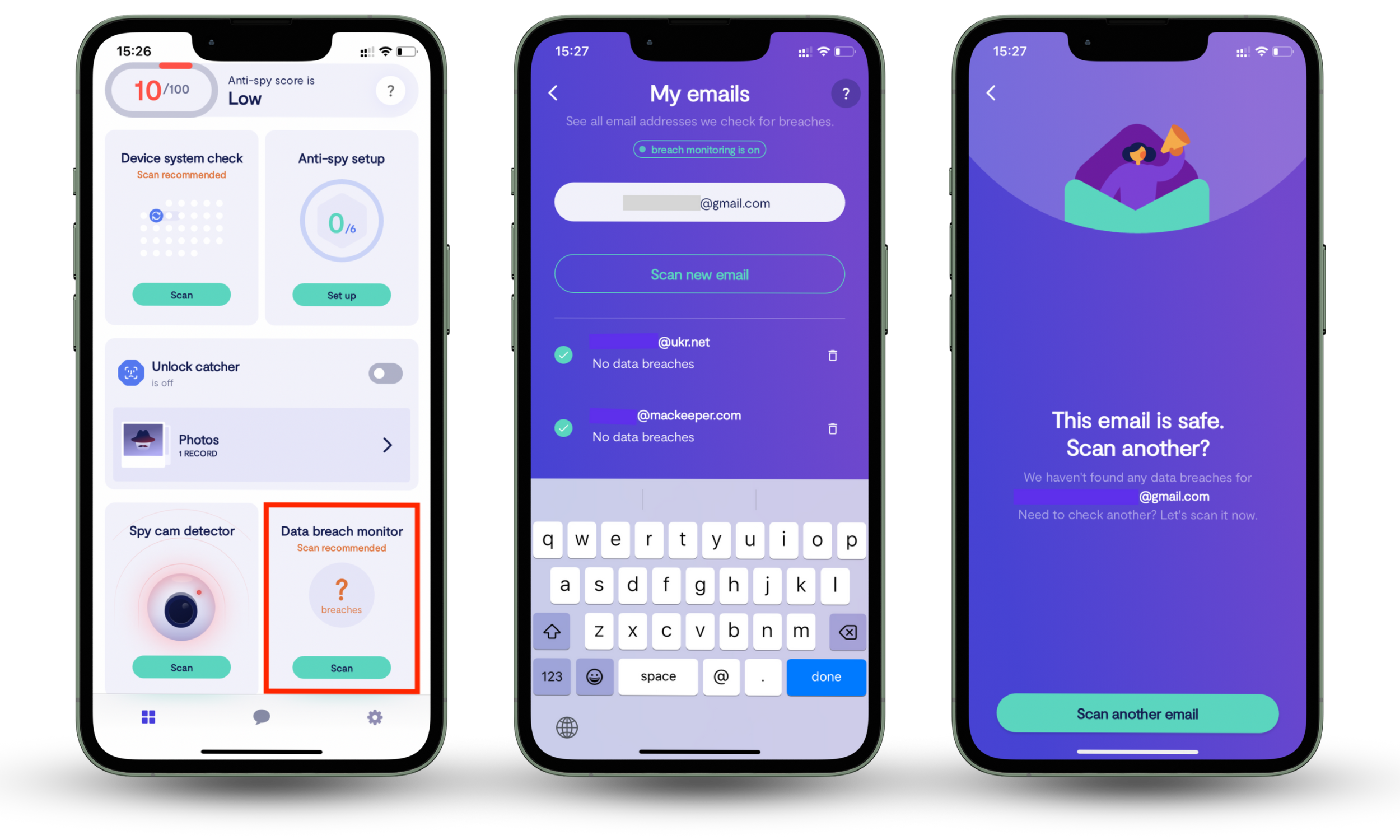
- Audit with data breach monitors: Tools like Clario Anti Spy’s Data breach monitor check whether your credentials appear in the MOAB or other compilations.
Here’s how to use Clario Anti Spy’s Data breach monitor to check if your passwords have been exposed in the MOAB leak:
- Download Clario Anti Spy and subscribe.
- Open the app, and, under Data breach monitor, tap Scan.
- Enter your email address.
- When the scan is complete, follow the on-screen guidance to review any data breaches.
- Repeat the process for any other email addresses.
Pro tip
Enable real-time alerts to get notifications when new leaks match your info.
With the breach listing crossing 16 billion entries, the only safe assumption is that the MOAB contains credentials from nearly everyone. Clario Anti Spy’s service flags exposures, so you can change passwords before attackers exploit them.
3. Adopt better login habits: Use a password manager to generate unique, strong passwords. Favor passkeys or FIDO2/biometric logins where supported.
Why MOAB is unreal and why using Clario Anti Spy matters
The sheer volume of this MOAB breach—“one of the largest data breaches in history”—makes it the ultimate compiled breach list. It's not just another data leak; it’s 16 billion login credentials you need to treat as weaponizable intelligence.
That’s exactly why Clario Anti Spy’s Data Breach Monitor isn’t optional—it’s essential. It takes the guesswork out of tracking threats:
- Proactive monitoring of global leaks
- Informed security actions (password resets, 2FA enactment)
- Peace of mind knowing you’re alerted fast if any of your data appears in future leaks
Final take
The MOAB—Mother of All Breaches—shows the scale of our vulnerabilities. A single hack didn’t cause it, but decades of malware and data leaks compiled into the biggest password leak ever seen. Now, sitting at the top of the digital food chain with 16 billion credentials, it’s time to act fast:
- Lock down accounts and enable 2FA or passkeys
- Use Clario Anti Spy’s Data breach monitor to check for exposure
- Change compromised passwords, protect the rest
Because once the MOAB is out there, your safest move is knowing. Before they do.


