Table of contents
- What is a VPN tunnel?
- How VPN tunneling works
- Data encryption
- Key exchange
- Kill switch
- What is split tunneling?
- How are VPN tunnels created?
- What are the different types of VPN tunnel protocols?
- 1. PPTP
- 2. L2TP/IPsec
- 3. SSTP
- 4. OpenVPN
- Use VPN tunnels to protect your privacy
None of us like everyone seeing who we are, where we are, or what we’re looking at while we’re online.
It’s just plain creepy to think about, isn’t it?
But the sad fact is, this is just how your connection to the internet works – it’s like an open window into the goings on in your home, and any nosey parker can peep through.
Whether it’s your Internet Service Provider (ISP) looking to track and sell your data to advertisers, or unscrupulous hackers trying to steal your personal information to sell on the dark web, it sometimes feels like the whole world has a vested interest in snooping on your online activity. And the internet doesn’t exactly make it hard for your data to be viewed or hacked by others.
However, there are a number of ways to ward off would-be online snoopers, one of which includes using a Virtual Private Network (VPN). In a nutshell, VPNs help you surf the web securely, privately, and with no restrictions. (We’ve already waxed lyrical on the benefits of using a VPN before, so we won’t harp on again too much here).
Curious to learn exactly how VPNs accomplish this amazing feat in the first place? It’s mainly down to a little-known process called tunneling.
What is a VPN tunnel?
What the heck is a VPN tunnel, and how can it help you maintain your digital security and privacy, we hear you ask? And why should you care about how it all works in the first place?
Let’s dig into it together, kicking off with a quick definition of what exactly a VPN tunnel is.
A VPN tunnel (short for Virtual Private Network tunnel) is a private pathway for data to pass through the internet from your computer or mobile device and another network.
So, think of a VPN connection like a tunnel capable of taking you to a different place on the web. This tunnel opens up at one point (your VPN client) and weaves its way through the internet before emerging at another point (the VPN server).
Just how secure the VPN connection is boils down to four basic elements, which we’ll go into in more detail on in just a moment:
- Tunneling
- Encryption
- Key exchange
- Kill switch
The whole idea behind using a VPN is to shield your activity and, in essence, protect your privacy. Instead of investing in a single service, why not use comprehensive anti-spying software that hides your location and protects your data in other ways, too?
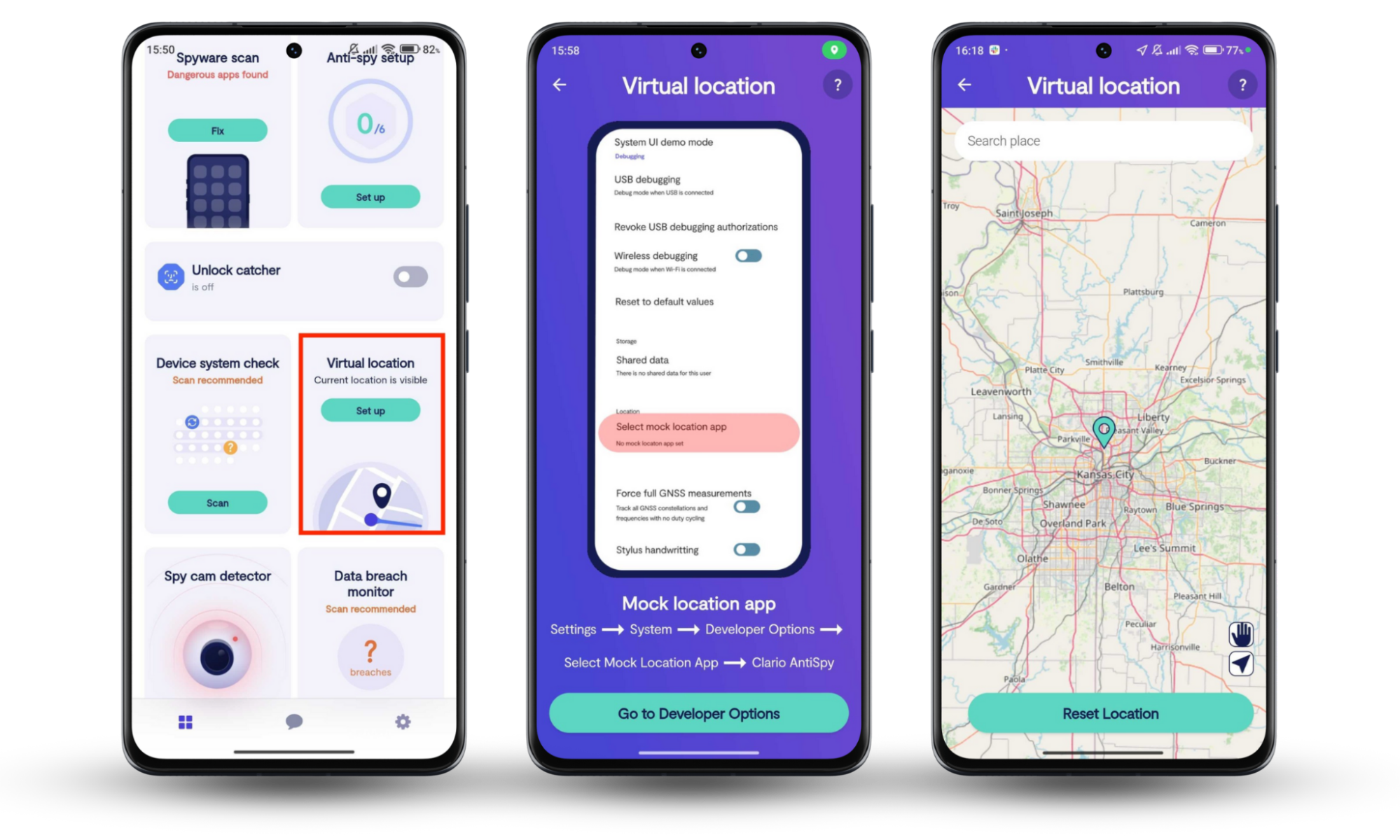
That’s where Clario Anti Spy comes in. It’s an all-in-one app that provides several anti-spying tools to show you who’s trying to unlock your phone, notify you when your email is vulnerable, find spy cams in your home, and more. In particular, Clario Anti Spy’s Virtual location software for Android smartphones works similarly to a VPN service. It helps you avoid stalking and spying by connecting you to servers far from your location to ensure you secure your device and safeguard your data.
Follow the steps below to use Clario Anti Spy’s Virtual location tool on your Android phone:
- Download Clario Anti Spy on your device, get a subscription, and set up an account.
- Open the app and hit Set up under Virtual location.
- Carefully follow the prompts to choose your preferred virtual location on the map, and then tap Reset Location to protect yourself against online spying.
How VPN tunneling works
When your device initiates a VPN connection, your entire network traffic passes through a secure tunnel.
Any data sent through the internet via the VPN tunnel is split and encapsulated within “packets” (in essence, another layer of data). It works a little bit like putting a letter inside an envelope, meaning no third parties (not even your ISP) can see the data tucked away on the inside. Once the packet arrives at its destination (your VPN server), then this outer layer of data is removed so it can access your data.
This tunnel also lets traffic go both ways, back again from the VPN server to your device, shielding the data inside the tunnel as it goes – and protecting it from anyone lurking just outside.
While VPN tunneling is critical to protecting yourself and your data online, it can’t ensure your data remains safe and anonymous on its own. You’ll also want to look for the following in your chosen VPN package:
Data encryption
Encryption is the process of taking the data transmitted through the tunnel established between your VPN client and the server, then scrambling it into an unreadable format known as “ciphertext”.
Key exchange
This is when the VPN client and server variously encrypt (and decrypt) your data packets using keys or certificates. Basically, they are a series of numbers used to encrypt and decrypt data only they have access to.
Kill switch
Hey, dropped connections happen sometimes, even to the very best (and priciest) VPNs. This is why most reputable VPN providers come with a seriously useful feature – an automatic kill switch.
Think of the kill switch as your last line of defense – a digital sentinel standing constantly on guard, monitoring your connection to the server. If your connection to the VPN server does ever drop (even for a split second), then the kill switch will automatically cut off any network traffic traveling to and from your device (or any apps you’ve specified).
Once the VPN tunnel connection is restored, it’s back to business as usual. It leaves you safe in the knowledge that your IP address or any unencrypted data wasn’t accidentally leaked when your connection unexpectedly dropped.
What is split tunneling?
There are likely to be times when you don’t necessarily want all of your traffic to be encrypted through a VPN. Maybe you mostly want your VPN for certain things, like unblocking Netflix while you’re on vacation, or checking your bank account online while using a public Wi-Fi. But you’re fine with shopping on Amazon on an open network from home.
Some VPN clients come with a nifty little feature to allow you direct control of the apps and websites you want to connect to via VPN, and which ones you’d prefer to connect directly to – this technology is known as split tunneling.
(Heads up: split tunneling is also a good way to conserve bandwidth if that’s a particular concern to you.)
How are VPN tunnels created?
Here’s where we’re going to attempt to get all techy with you. VPN tunnels don’t happen by magic – they’re created through different tunneling protocols put in place for different purposes.
What are the different types of VPN tunnel protocols?
The most common VPN tunneling protocols include PPTP, L2TP/IPsec, OpenVPN and SSTP. Let’s go through them below.
1. PPTP
You can thank Microsoft for PPTP (Point-to-Point Tunneling Protocol).
They developed the OG VPN protocol way back in the 90s, otherwise known as the Dark Ages of the internet. While PPTP offers some upsides (mainly, lighting-fast connection speeds), it also comes with a whole slew of security vulnerabilities easily exploitable by cybercriminals. As technology around VPN protocols has advanced significantly over the decades, PPTP is fast becoming obsolete.
2. L2TP/IPsec
Because Layer 2 Tunneling Protocol (more commonly known as L2TP and Cisco’s answer to PPTP) doesn’t come with inbuilt encryption, it’s typically paired with IPsec (Internet Protocol Security) to create a more secure overall tunneling protocol.
3. SSTP
Another VPN protocol Microsoft can claim credit for, Secure Socket Tunneling Protocol (or SSTP) is super secure. The downside? It’s only available to Windows users.
4. OpenVPN
An open-source VPN protocol, OpenVPN is supported by all of the big operating systems (Microsoft Windows, Apple Mac OS X and Linux), as well as Android and iOS. With seriously high-level VPN encryption and a knack for getting around any pesky firewalls, OpenVPN is considered the best, most secure protocol in existence today.
Use VPN tunnels to protect your privacy
VPN tunnels help you steer clear of online spies by encrypting your outgoing traffic. This includes your IP address, which hackers can use to identify your device online. If you’re concerned about your privacy, Clario Anti Spy offers a host of tools to protect it. Its Virtual location feature for Android devices gives you peace of mind, knowing you’ve prioritized safeguarding your data against spies.