What Is a Zero-Day Attack And How to Protect Yourself From It
Table of contents
Zero-day attacks exploit vulnerabilities in software or hardware discovered before developers have had a chance to create a fix. Users are potentially put at risk as there is limited protection against any quick-witted cybercriminals looking to exploit this security flaw for their own ends.
Recently, thousands of companies were caught up in the zero-day attacks on the Microsoft Exchange server, prompting the tech giant customers to issue recommendations and guidance for users to help them avoid the online commotion.
Elsewhere, Apple has been forced to rush out an update to macOS Big Sur 11.3 to provide a patch for a recently uncovered vulnerability.
It sounds worrying but don’t panic as zero-day attack prevention can be enhanced by following some simple steps. Here we will explore:
- What is a zero-day attack?
- What are the most famous zero-day attack examples?
- Why are zero-day attacks dangerous?
- How to prevent zero-day attacks
While zero-day attacks target unknown vulnerabilities in your software and devices, an all-round cybersecurity solution like Clario can cover most of the known gaps. Test it out now by downloading Clario. And read on to know how to avoid getting harmed by a zero-day attack.
What is a zero-day attack?
A zero-day exploit is a cyberattack that occurs on the same day a vulnerability is discovered in a software.
This attack targets this lack of defense before a fix is made available by a service’s company.
Users will often report a bug or vulnerability to a developer, then an update will be developed as a patch and applied. It’s during the development time spent creating this patch that zero-day attacks are often launched.
Zero-day attacks are so-called as developers often have ‘zero days’ to create a security fix. They therefore need to design one as fast as possible to help keep users secure from any malware or zero-day viruses.
What are the most infamous zero-day attack examples?
Operation Aurora is one of the most infamous zero-day attacks. It was carried out in 2010 by Beijing's Elderwood Group that reportedly had ties to the Chinese military.
This attack (actually, a series of attacks) hit dozens of American companies — Adobe, Yahoo, and Symantec, among others — but the primary aim was Google.
The attack was, presumably, a retaliation for Google.cn notifying users when some of the results were censored out of their searches, and meant to make Google more compliant.
We’ve all come to love and loathe video conferencing platform Zoom in equal measure during the last 12 months. But in 2020, a zero-day vulnerability was discovered in the service for Zoom users utilising Windows 7 or earlier versions of the operating system. It allowed cybercriminals to gain remote access to devices and files or information stored on them.
Back in 2011, security firm RSA was attacked by hackers exploiting an Adobe Flash Player vulnerability. Its network was breached by attackers sending employees emails with Excel spreadsheets. A member of staff opened a file with an embedded Flash file which allowed the cybercriminals to take control of their machine and infiltrate their IT systems.
Such is the potential risk presented by zero-day attacks, Google established its own Project Zero team of security experts in 2014, tasked with finding any zero-day vulnerabilities.
Why are zero-day attacks so dangerous?
A zero-day vulnerability can pose a real threat to computer users of all kinds regardless of how tech-savvy you are.
Malware could potentially infect your device through usually harmless activity such as opening emails, downloading attachments or browsing websites.
As the name suggests, developers are often under great pressure to come up with a fix quickly once details of a zero-day vulnerability enter the public domain. Despite this, sometimes developers may be unable to come up with a fix before this security issue is exploited. It can take days, weeks or even months for fixes to be released.
The compromised software or service may need to be used during this time, leaving their personal information at risk.
How to stay safe from zero-day attacks?
While zero-day attacks often put you at risk, you can follow best practice to keep your cybersecurity defenses up to date and give yourself a better chance of protecting your personal information.
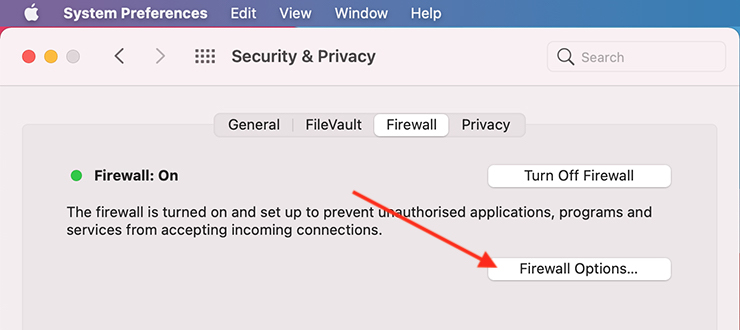
Use a firewall: setting up a firewall can be an effective way of maintaining your security. You can configure your firewall to scan for certain threats to keep your data safe.
To enable a firewall on Mac:
1. Head to the Apple Menu, then System Preferences.
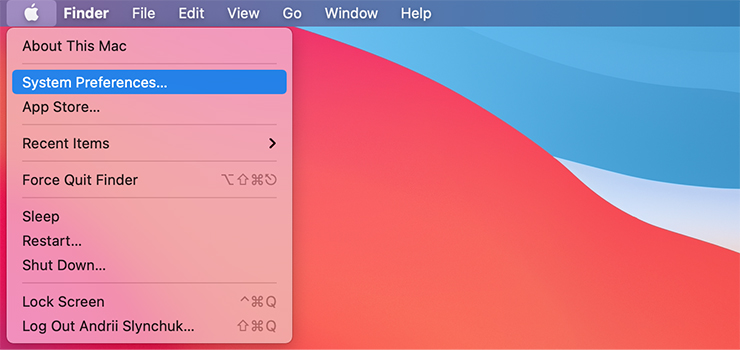
2. Click Security & Privacy, then head to the Firewall tab.
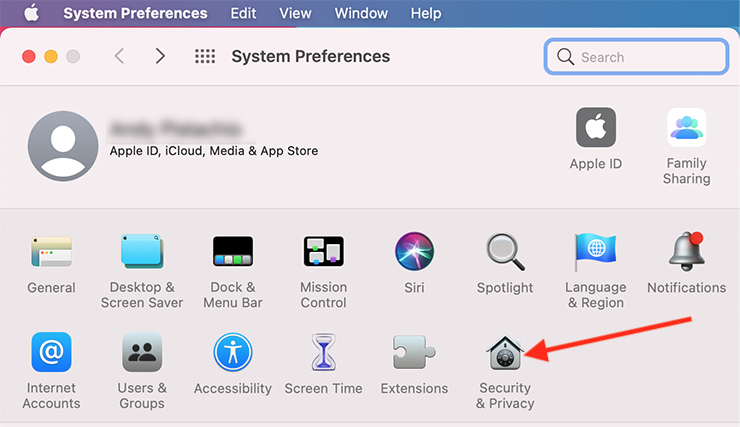
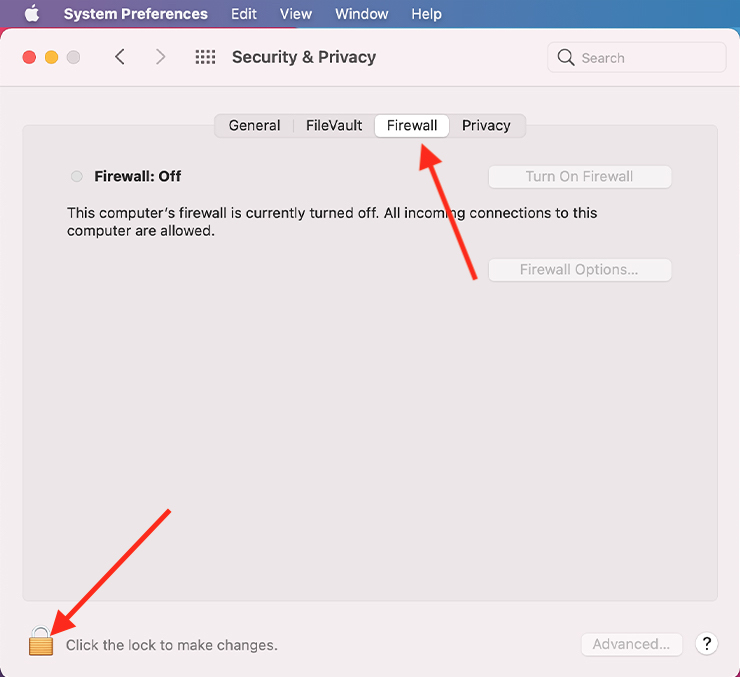
3. Click the lock in the bottom left of the pane, then enter login details.
4. Click Turn on Firewall.
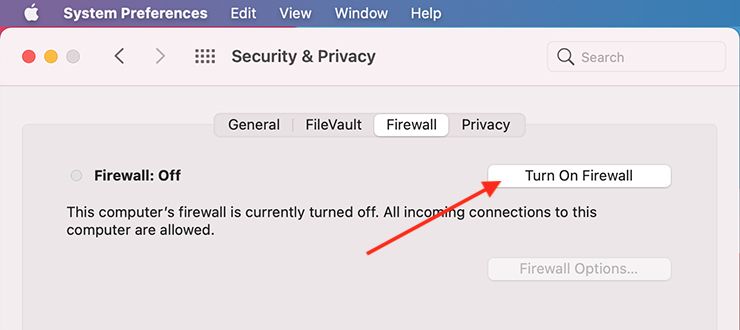
To set firewall options for Mac, click the Add button under the list of services. You can then select any services or apps you want to add from here.
Always update operating systems: developers often release updated versions of operating systems to fix bugs and implement patches to enhance security. So rather than delaying an update, you should always install the new software as soon as it is launched by a manufacturer. This will shore up your defenses and reduce vulnerabilities surrounding a device.
Stay informed of the latest cybersecurity news: try and stay up to date with the latest cybersecurity news and trends so you are aware of any actions you need to take. Clario’s blog is a one-stop shop for all the latest news and guides on cybersecurity issues.
Only utilise essential applications: the more applications you run, the more exposed you are to these kinds of threats. Keeping the number of trusted applications you use to a minimum will mean less vulnerabilities in your network.
Zero-day exploits can get the best of your software's and hardware's unknown vulnerabilities, and we've just advised you on how to dodge this zero-day bullet. Now, a surefire way to safeguard yourself from known cyber threats is to use an all-in-one solution like Clario. Try it today.
Zero-day attacks often occur without warning which make them difficult for online users to anticipate or protect themselves against.
But by adhering to cybersecurity common sense, you should be able to limit the chances of becoming caught up in one. Stay tuned to Clario’s blog for all the latest news and updates on cybersecurity concerns.
Read more:


