Table of contents
- What is a computer worm?
- How do computer worms spread?
- What kind of damage can computer worms do?
- What kinds of worms are out there?
- How can I tell if my computer has a worm?
- How to get rid of a computer worm?
- How to prevent computer worms from damaging you?
- Conclusion
Computer worms have been around for a few decades now. They’ve continued to evolve over time, becoming ever more sophisticated and trickier to detect. While worms in computers don’t tend to attract as much media attention as other cyberthreats, they still pose a very real threat to you and your computer. For example, MyDoom — the most devastating malware to date — is, in fact, a computer worm. In 2004, it caused damage estimated at $38 billion.
Recent years have shown that worm-like malware is still actively used in real-world attacks. For example, Raspberry Robin continues to spread through removable media and network connections, often acting as an entry point for more advanced malware. Other modern worms focus on rapid lateral movement inside corporate networks, exploiting unpatched systems to move silently rather than causing immediate disruption.
Although some of the most notorious computer worms appeared years ago, this threat hasn’t gone away. Modern worms increasingly target unpatched systems, cloud-connected services, and even smart devices, allowing them to spread silently and at scale. This makes computer worms a current, not historical, cybersecurity risk.
If you’re curious to find out what computer worms are and how you can fight them, then you’ve come to the right place.
Pro tip:
No computer is immune to malware. Luckily, Clario Anti Spy is here to provide you with a worry-free digital experience. Go ahead with Clario Anti Spy and keep your devices secured.
What is a computer worm?
Computer worms are often confused with other types of malware. The table below highlights the key differences between worms, viruses, and Trojans.
| Malware type | How it spreads | User interaction required | Main risk |
| Computer worm | Spreads automatically across networks and connected systems | No | Rapid network infection and delivery of malicious payloads |
| Virus | Attaches to legitimate files or programs | Yes | File damage, data loss, system instability |
| Trojan | Disguises itself as legitimate software | Yes | Unauthorized access, data theft, further malware installation |
Computer worms are a subset of Trojan malware, capable of spreading multiple copies of themselves across a network or via an internet connection. These copies then go on to attack any unprotected computers connected to the initially infected device — meaning worms can propagate across the web at breakneck speed.
You might recall the infamous NotPetya worm that wrought havoc across the EU in 2017. It spread throughout multiple systems, taking advantage of vulnerabilities in the Windows code. Microsoft patched those vulnerabilities long before 2017, but we all know how people hate to update their operating systems... There have been lots of other worms throughout history — and many new threats are active now.
How do computer worms spread?
There are several different ways computer worms can infect your computer. These include unpatched security loopholes in your operating system, booby-trapped email attachments, or links to worm-infested websites (ew!).
In most cases, a computer worm follows a predictable infection pattern:
- Initial access: The worm exploits a software vulnerability or enters through a malicious attachment, link, or removable device.
- Self-replication: Once inside, it creates copies of itself without user involvement.
- Network spread: The worm scans for other vulnerable devices on the same network or online and infects them automatically.
- Payload activation: Additional malicious code may be deployed, enabling data theft, remote control, or further malware downloads.
There are other popular infection methods:
- External devices (such as USBs)
- IM networks and IRC software (various messengers like Skype, WhatsApp, or Facebook Messenger)
- Peer-to-peer (P2P) file-sharing or torrent files, and more
For example, Stuxnet, the worm created by the US and Israeli intelligence services to derail the Iranian nuclear program was delivered on-site via a USB stick. It was done this way because the Natanz research facility has no internet access.
In 2025, computer worms increasingly spread through cloud-connected services, outdated home routers, and internet-connected devices such as smart cameras or network storage. Collaboration tools and shared online platforms can also accelerate worm propagation when security updates are delayed.
Unlike viruses, which need to inject a working application with malicious code, worms only need to gain access to a computer; they can propagate on their own after that. What kind of damage can computer worms do then?
What kind of damage can computer worms do?
Unlike viruses, which do immediate damage, worms are fairly harmless on their own and will just slow down your computer in most cases. Their biggest threat is that they come with a malicious payload — code designed to make your computer prone to other forms of malware. This can lead to your device becoming part of a botnet, losing sensitive information such as your passwords or banking information, or suffering from other kinds of online attacks.
The damage caused by computer worms usually falls into several categories:
- Performance and stability issues: Slower system performance, frequent crashes, and excessive network activity.
- Data and privacy risks: Exposure of passwords, personal data, or financial information through secondary malware.
- Network and financial impact: Devices may be absorbed into botnets used for spam campaigns, DDoS attacks, or fraud.
What kinds of worms are out there?
There are various types of computer worms capable of affecting your computer in different ways. Below we list the most common examples.
- Network worms: Exploit network services and open ports to spread rapidly within corporate or public networks.
- IoT worms: Target internet-connected devices such as routers, smart cameras, or home automation systems, often using default or weak credentials.
- Cryptomining worms: Use infected devices to secretly mine cryptocurrency, leading to performance degradation and higher energy consumption.
- Email worms. Most worms hide in email attachments and are only activated once you open the email. An ILOVEYOU worm is a well-known example.
- IM worms. This type of network worm spreads across instant messaging (IM) networks, including Facebook Messenger, Skype, and WhatsApp. It hides in message attachments, just like the previous one. Never click short messages like “That’s a must-see!” coming from a friend — more often than not, these are IM worms.
- Bot worms. A bot worm is specifically designed to transform your computer into a “bot” — a machine under external control. The ultimate goal here is to create an “army” of infected computers for spreading viruses, spam, and mass attacks to a victim’s servers or networks. The Conficker bot worm was huge news when it first emerged back in 2008.
- File-sharing worms. This type of worm spreads by copying itself into a shared folder that users then go on to download. It’s most often used to infiltrate corporate networks.
We’ve now covered the main ways that worms spread in a computer. But what are the infestation symptoms to look for?
How can I tell if my computer has a worm?
If you suspect your computer could be infected with a worm, look for one or more of the following signs:
- Your computer has started working slower than before and/or crashing often. Worms love to monopolize your device’s processing power.
- You’ve run out of storage space. Worms eat up a whole lot of space on your computer’s hard drive by continually replicating themselves.
- You’re seeing strange activity on your computer. This includes files and documents continually appearing and disappearing.
These warning signs are not unique to computer worms and may also indicate other forms of malware or system issues. The only reliable way to confirm a worm infection is through a dedicated malware scan.
A worm might make its presence known through some of these telltale signs. However, it’s important to remember that even if your computer seems to be running perfectly, you still need to check for worms and other types of malware on a regular basis.
How to get rid of a computer worm?
Unfortunately, there’s no universal remedy. But if you do suspect a worm infestation on your device — or you just want to be careful — there are a few steps you should take. And by the way, since Macs aren’t immune to these “parasites” either, you can also use these tips to protect your Apple device:
- Disconnect your device from the internet. This will stop the worm from spreading any further. It will also prevent any malicious software the worm may have introduced onto your computer from doing further damage.
- Scan your device with trusted security software. Use a reputable security solution to scan your system and remove any detected threats. For macOS users, tools such as MacKeeper can help identify and remove malware-related components and suspicious system behavior.
- Review and remove suspicious files or apps. After the scan, check recently installed programs, browser extensions, or system changes you don’t recognize and remove them if advised by the security tool.
- Update your operating system and software. Install the latest OS and app updates to close vulnerabilities that worms commonly exploit.
Traditional computer worms don’t behave the same way on mobile devices, but phones are often targeted by spyware and stalking tools instead. On iOS and Android, dedicated anti-spy solutions like Clario Anti Spy focus on detecting hidden spying apps, suspicious permissions, data exposure risks, and unauthorized access rather than classic worms.
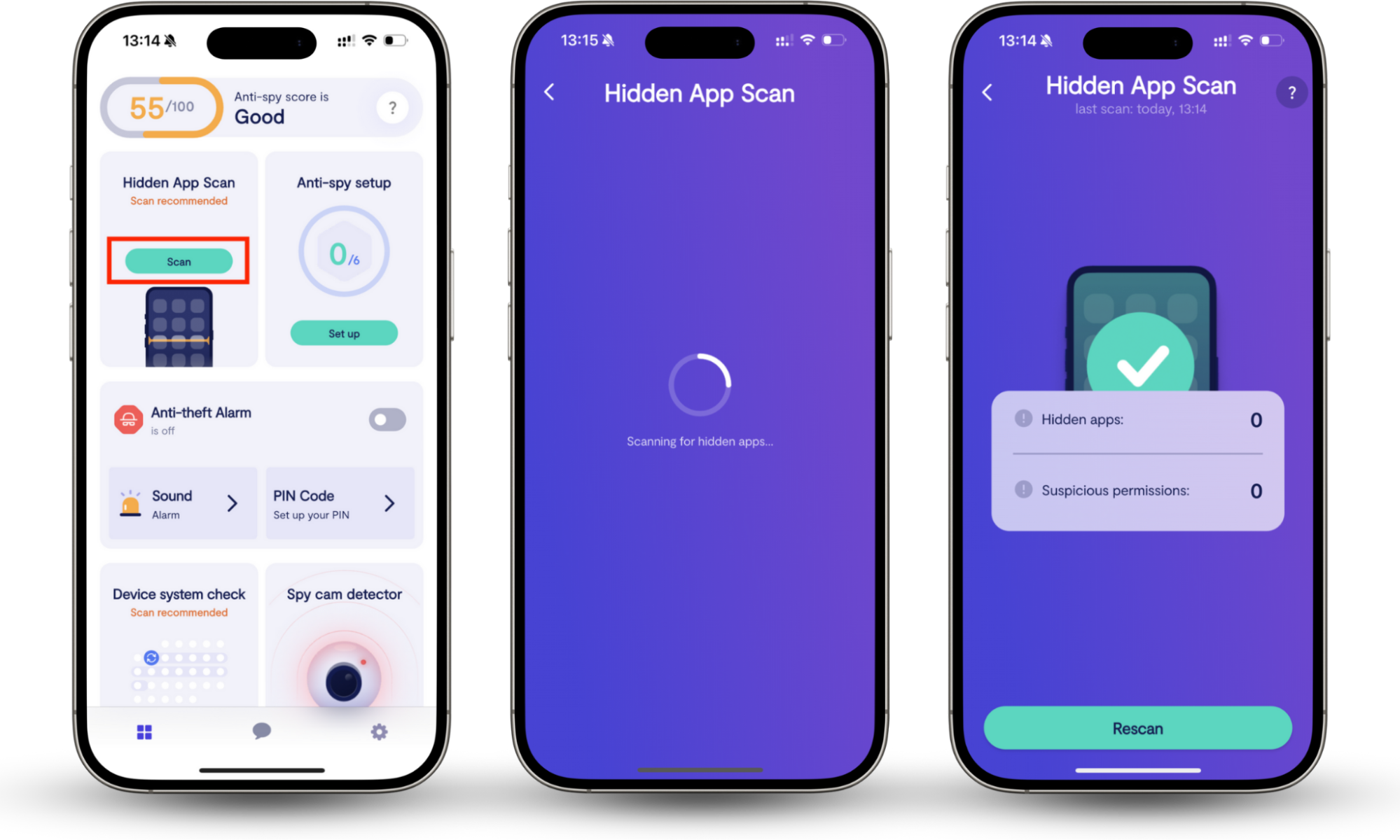
If you’re concerned about spying or unauthorized monitoring on your phone, Clario Anti Spy’s Hidden app scan can help identify concealed surveillance apps and suspicious permissions.
- Open Clario Anti Spy and select Scan under the Hidden app scan feature.
- Clario will run a full scan of your mobile device. This looks for signs of spying apps, like spyware and parental control apps that someone may have secretly installed.
- Review the results. The tool analyses all requested app permissions, helping you to detect suspicious ones that don’t belong.
In some cases, not even the best antivirus will be able to remove the infected files. In these rare instances, reinstalling your operating system (or even more serious measures, like flashing your hardware to delete and reinstall the firmware) may be the only solution. The important thing is to remove the worm once and for all. If you don’t, both your computer and personal information could be continually compromised.
After removing a computer worm, take the following steps to make sure your system is secure:
- Run a second malware scan: Re-scan your device to confirm no malicious components remain.
- Change important passwords: Update passwords for email, banking, and other sensitive accounts in case credentials were exposed.
- Review system and network activity: Watch for unusual behavior such as unexpected slowdowns or unknown connections.
- Apply pending updates: Install any remaining operating system or software updates to close known security gaps.
How to prevent computer worms from damaging you?
Effective protection against computer worms relies on both technical safeguards and safe online behavior. While solutions to a worm infection exist, the best thing to do is take steps in order to avoid a fallout in the first place. Firstly, remain vigilant for early warning signs of a worm infection (we’ve covered those above). Next:
- Update your OS and apps in time. Remember, worms need to take advantage of security loopholes before they can spread across networks. Microsoft regularly releases security updates that fix dozens of critical vulnerabilities, including flaws that can be exploited by self-propagating worms if left unpatched. Have you installed it yet? Enabling automatic updates helps reduce this risk, as delays in installing patches are one of the most common reasons worms are still able to exploit known vulnerabilities.
- Enable the firewalls on your computer. Firewalls can help block malicious software and keep worms from infecting your computer. It’s easy to enable a firewall — just follow instructions specific to your OS.
- Avoid email spam, suspicious websites, and other online scams. Avoid clicking on unknown or unverified links and email attachments. Also, we recommend not downloading software from potentially unsafe websites or P2P file-sharing networks.
- Use reliable cybersecurity software. For example, Clario Anti Spy makes it easy to detect and remove computer worms and other malware. Besides, the app will give you personalized recommendations on your online behavior and grant you unlimited access to 600 cybersecurity experts.
Conclusion
Computer worms and spying tools may work quietly, but the risks they pose are real. Staying protected means understanding how these threats operate, keeping systems updated, and checking devices regularly for suspicious activity. For mobile users, Clario Anti Spy adds an extra layer of confidence with features like Hidden app scan, helping uncover concealed surveillance apps and reduce the risk of unauthorized monitoring.


