Table of contents
- How secure are crypto wallets?
- What are the risks of using crypto wallets?
- Lack of regulation
- Risk of getting hacked
- Market volatility
- 5 best and most secure crypto wallets
- Trezor Model T
- DeFi Wallet
- Ledger Nano X
- ZenGo
- Atomic Wallet
- Trust Wallet
- What is a crypto wallet and how does it work?
- Custodial wallets
- Non-custodial wallets
- Hot wallets
- Cold wallets
- Key features of crypto wallets
- Security
- Fees
- Ease of use
- Amount of trading
- Interoperability
- Which crypto wallet is the best and safest?
- Conclusion
| Allows credit, debit, bank transfer, and Apple Pay | Best wallet for beginners | Best wallet for desktop | Best hardware crypto wallet | |
|---|---|---|---|---|
| Wallet name | ZenGo | DeFi Wallet | Tresor Model T | Ledger Nano X |
| Highlights | ZenGo claims it’s never been hacked; multiple ways to pay | Open-source wallet | Tresor Suite can run on your desktop | Supports more coins and tokens than its counterparts |
| Wallet type | Hot storage | Hot storage | Cold storage | Cold storage |
| Cost | Free | Free | $219 | $149 |
| Compatibility with hardware wallets | Yes, WalletConnect | Yes, Ledger and Trezor devices | N/A | N/A |
| Number of supported coins and tokens | Over 70 | Over 1,000 | Over 2,000 | Over 5,500
|
How secure are crypto wallets?
The single most important thing to consider when choosing a crypto wallet is how safe it is. Crypto wallets have a wide range of features, but none are more important than security features. Because crypto is such a valuable digital asset, crypto wallets are at risk of being breached.
It’s no different from the security risk posed by using online banking. With the increased interest in cryptocurrency comes increased threats. Wallet hacks are common in the crypto world, especially if you use a hot wallet. While hackers take advantage of any methods available to obtain your personal information and crypto funds, phishing is a common strategy.
Through phishing attacks, cybercriminals can obtain your seed phrase to access your funds, and it goes downhill from there. Phishing attacks are activities undertaken by hackers to obtain your personal information for malicious reasons. SMS and email phishing are the most common types. Phishing attacks can be sophisticated. They attempt to obtain your sensitive data, including your:
- Phone number
- Name
- Address
- Date of birth
- Bank account
- Social Security Number (SSN)
- Credit card number
- Passwords for online accounts.
Avoid phishing attacks
That’s why you must learn how to spot phishing email attacks. Avoid falling victim to phishing email scams by learning how to identify them.
Here’s what phishing email attempts typically look like:
- Hackers posing as a bank to ask for your credentials
- A scammer posing as the lawyer of a deceased client that left you funds, but you need to submit your personal information to claim them
- A bad actor notifying you that you’ve won a significant amount of money or a gift, which you need to claim
- A hacker posing as a recruiter offering you a job offer and requiring you to click on a link to learn more.
Below are threats that affected crypto wallets in recent years:
- Ledger hack. In 2020, Ledger revealed it had been hacked. In the following months, customers started receiving phishing emails and text messages. By December, a data dump surfaced that exposed a million email addresses and hundreds of thousands of personal information belonging to customers who’d purchased hard wallets. This data included names and phone numbers. Some customers would go on to be victims of extortion, while others received violent threats.
- Ledger data breach. In December 2020, Ledger learned of a breach in which malicious Shopify agents obtained and exported the transactional records of 20,000 more Ledger customers. The data included names, phone numbers, email addresses, and postal addresses. Shopify reported that the breach occurred in April and June 2020.
- Trezor phishing campaign. In February 2022, Trezor, a hard wallet service, experienced a phishing attack in which customers received SMS and email messages notifying them about a bogus Trezor data breach. They were directed to a website to help secure their hard wallets. The website prompted customers to enter their seed phrases, which would help hackers access their crypto wallets.
Incidents like the ones listed above are the reason looking for a crypto wallet with robust security features is key.
Here are examples of security features to look for in a crypto wallet:
- Facial recognition or biometric access to ensure that no unauthorized persons can access your wallet
- Two-factor authentication (2FA) or multifactor authentication (MFA) for an additional layer of security. This makes it nearly impossible for hackers to access your wallet
- Support for multiple signatures if the wallet is owned by several people, like family members and business partners
- Protection against browser fingerprinting to prevent hackers from tracking information about you or your crypto wallet.
The responsibility of protecting your funds doesn't only lie with the crypto wallet service. You should also take the necessary steps to keep your wallet secure. Here are the best practices for keeping your crypto wallet secure:
- Stay on top of news and developments relating to crypto and crypto wallets, especially where security threats are concerned. As the world of cryptocurrency continues to grow in leaps and bounds, bad actors find new ways to compromise your wallets and steal your assets.
- Use a reliable VPN service to maintain your privacy and avoid getting tracked by hackers. A VPN keeps your online activities, including those relating to your crypto wallet, anonymous by masking your device’s IP address. Learn more about how VPNs work.
- Avoid using public Wi-Fi networks, which can be easy targets for hackers. Hackers can use vulnerable Wi-Fi networks to hack and access your crypto wallets.
- Keep your hardware wallet free of damage to avoid losing your funds. Likewise, Use reliable antivirus software to keep the devices you use to access your virtual crypto wallet (including your smartphone and computer) free of viruses and malware.
- Hackers can take advantage of a weak internet connection, so be sure to use reliable internet that isn’t spotty or unsecured.
- Use a wallet that encrypts your seed phrases to reduce the risk of getting hacked. (Seed phrases are a bunch of random words created by your crypto wallet to access your funds in case of emergency).
- Opt for a cold wallet (also called a hardware wallet) instead of a hot wallet. These are more secure because they only connect to the internet when you need to buy, sell, and trade crypto. The keys are stored offline to reduce security threats. Because of this, it’s incredibly difficult for hackers to obtain them. As such, cold storage crypto wallets are typically only compromised when you’ve been a victim of phishing and other security threats or if the wallet itself gets misplaced or stolen.
What are the risks of using crypto wallets?
No matter what anyone tells you, using crypto wallets is risky. Keep the following risk factors in mind when using crypto wallets:
Lack of regulation
Cryptocurrency was launched in 2009 and gained more popularity in recent years. However, governments and organizations are yet to figure out how to regulate it, thereby making it an unregulated currency.
This is probably the biggest risk of using a crypto wallet because it means that users are unprotected against crimes involving cryptocurrency.
Risk of getting hacked
Because crypto is such a valuable digital asset, crypto wallets are at risk of being breached by hackers who would want to get their hands on your stash. It’s no different from the security risks posed by using online banking, which is a target for hackers and cybercriminals.
However, different wallets come with different threats. For example, hot wallets are less secure than cold ones. Regardless, investors appreciate the importance of a secure wallet, no matter which one you use.
Even if your crypto wallet claims to have the best security measures in place, it’s never enough, and you can’t take their word for it.
Here’s why:
- Several crypto wallets have been hacked, which demonstrates the skills and commitment of cybercriminals in compromising your data and digital assets
- Cryptocurrency like Bitcoin is in high demand. Some bad actors will stop at nothing to get their hands on your funds.
- In many cases, hackers are highly knowledgeable and experienced at what they do, so they can easily spot security flaws and exploit them to get what they want.
What should you do?
Stay on top of data leaks to keep your crypto funds safe.
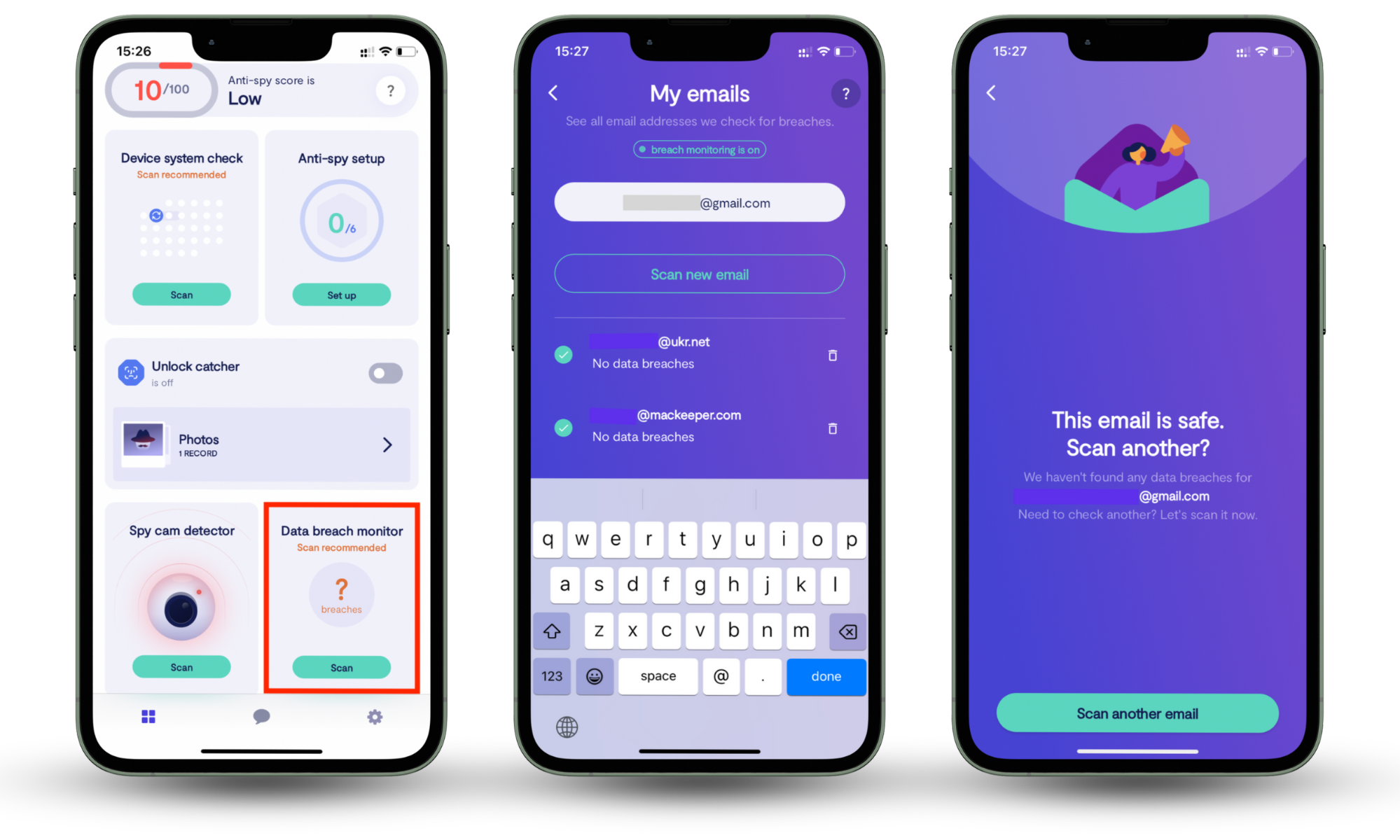
Clario Anti Spy is an anti-spying app that makes it difficult for hackers and bad actors to track you. Its Data breach monitor is a reliable tool that scans the web for data dumps containing your email address. If your email and passwords are stolen during a phishing attack and sold on the dark web, Clario Anti Spy’s Data breach monitor will notify you. This allows you to take action fast, before hackers can use this data to access your crypto wallet to steal your funds. That’s how Clario Anti Spy protects your digital assets.
Whether you use your crypto wallet on your iPhone or Android mobile, you can use Clario Anti Spy’s Data breach monitor tool to secure your email address.
Follow these steps to turn on Clario Anti Spy’s Data breach monitor on your phone:
- Install Clario Anti Spy on iOS or Android and pick a subscription.
- Open the app, go to Data breach monitor, then tap Scan.
- Enter the email you use for exchanges or wallets.
- After the check finishes, review any breach details and follow the prompts to secure your accounts.
- To check more addresses later, tap Scan new email and repeat.
- Keep Clario Anti Spy’s Data breach monitor enabled for round-the-clock protection.
Is your computer behaving oddly?
It may be infected with viruses. Learn the symptoms and effects of a computer virus.
Market volatility
Cryptocurrency is a very volatile currency. You’ve probably seen online or on the news how investors have lost millions in cryptocurrency overnight. The market is unpredictable. Your crypto wallet can be wiped out at any time, and there’s nothing you can do about it. This volatility makes the future of cryptocurrency unpredictable.
5 best and most secure crypto wallets
The market offers countless crypto wallets, which presents a difficult case in choosing the most suitable wallet for you. Worry not — we’ve made it easier for you by picking the five best crypto wallets out there. Most of these are highly rated and considered trustworthy.
Trezor Model T
Trezor T is a second-generation cold wallet with open-source software and one of the most trusted crypto wallets. Its user interface, Tresor Suite, is run on your desktop, which makes it safer than browser-based crypto wallets. You can also access it and transact on the Trezor website.
Because it’s a hardware crypto wallet, Trezor T can be connected to your computer using a USB cable. However, it has a microSD card, which you can use for encrypted storage. The wallet itself is compact and features a touchscreen interface.
Trezor T supports nearly 2,000 coins and tokens.
Price: $219 at Trezor
| Pros | Cons |
|---|---|
| The touch screen makes navigation simpler and more convenient | It doesn’t have support for Bluetooth |
| Open-source software, which is high quality, secure, and innovative. | A little more expensive than similar cold wallets |
| The crypto wallet doesn’t have a mobile app to make managing the wallet more convenient | |
| Users have been the target of data breaches, phishing attacks, and cryptojacking. Learn the types of cryptojacking and useful tips to prevent it. |
DeFi Wallet
This is a Crypto.com wallet used in decentralized finance, hence the name DeFI. Decentralized finance comprises cryptocurrency transactions and services that cut out the middleman, like a broker or a bank. These activities and transactions often take place using smart contracts on public blockchains like Ethereum.
Cutting out the middleman (financial institutions) allows investors to have complete control over their transactions. However, this very fact makes Crypto.com’s DeFi wallet susceptible to hacking, phishing, and scams.
DeFi Wallet supports over 1,000 tokens and coins. It’s best for beginners and those who want to be in control.
Here’s what you can use the DeFi Wallet for:
- Purchases
- Swaps
- Storing non-fungible tokens (NFTs).
Price: DeFi Wallet is free to use. However, you may be charged for transactions and related service fees.
| Pros | Cons |
|---|---|
| Can be used on desktop, mobile (app), and in the browser (for example, Google) | Since you’re fully in control of your own cryptocurrency wallet, if you lose your login information, you may never get your crypto back |
| Offers two-factor authentication, thereby making it secure | If your wallet is hacked or suffers a or attack, you’d have no backup |
| Can connect to offline storage devices. | While the wallet has educational tools, some of them aren’t available on the app. |
Ledger Nano X
Ledger is one of the more popular crypto wallets in the market. Like the DeFi Wallet, it’s also a second-generation cold storage wallet that gives you control over your digital assets.
Nano X is a simple solution to buy, grow, and manage your digital assets. The wallet itself looks like a USB stick with a LED interface. You can connect Ledger’s Nano X to your computer using a USB cable, and your mobile (Android or iOS) device via Bluetooth.
It supports more than 5,500 coins, which is significantly higher than other wallets on this list. These include:
- BTC
- DOT
- DOGE
- LTC
- ETH.
Price: $149 at Ledger.
| Pros | Cons |
|---|---|
| Secured with two-factor authentication and multi-signature security | Bluetooth functionality is only supported on the mobile app |
| Users can add up to 100 apps, including Ethereum and Bitcoin | You can’t buy assets and tokens through this wallet |
| Supports major operating systems for mobile and desktop. | You’re limited to storing 100 apps |
| At $149, Nano X is quite pricey. |
ZenGo
ZenGo is a popular self-custodial wallet that boasts a major achievement: It’s never been hacked. ZenGo is, by all accounts, bulletproof. So bulletproof, in fact, that it previously challenged hackers to intercept accounts holding 1BTC, and they failed.
The wallet also boasts a guaranteed recovery model, no seed phrase vulnerability, and has a Web3 firewall built into the wallet.
However, ZenGo only supports 70 assets, which is much lower than its counterparts.
Price: Free at ZenGo.
| Pros | Cons |
|---|---|
| Offers a plethora of options to buy crypto coins, including Apple Pay, debit, and bank transfer | The lack of a private key makes some traders skeptical to use the wallet |
| Features a keyless entry system, which reduces the chances of cybercriminals compromising the keys and using them to gain access to the wallet | Limited cryptocurrency options |
| Encrypted biometric system | ZenGo is not a fully custodial wallet. |
| 24/7 live in-app support | |
| Uses three-factor-authentication (3FA) | |
| User-friendly interface | |
| “Chill Storage” feature guarantees access to your funds if something happens to your wallet or the company | |
| Available in over 70 countries. |
Atomic Wallet
This is a completely open-source wallet. It offers several paid membership options, which reward customers for transacting on the wallet through a cashback program. You can buy, exchange, and stake digital assets within the wallet.
Atomic Wallet supports over 500 tokens. One of the main elements it lacks is a browser extension, which could help customers access decentralized apps.
Price: Free at Atomic Wallet with paid membership options.
| Pros | Cons |
|---|---|
| Uses encrypted private keys (stored on your device) | Makes converting to hardware storage difficult |
| User-friendly interface | Limited cryptocurrencies available. |
| Compatible with most operating system software, including iOS, Android, Linux, macOS, and Windows. |
Given that Atomic Wallet is cold storage, it can be targeted for malware. Can ransomware attack Android?
Trust Wallet
Trust Wallet is an open-source self-custody wallet from Binance — a global company that runs the largest cryptocurrency exchange. The wallet is comprehensive and allows for the purchasing, exchanging, and staking of digital assets.
It offers tools to track your price performance. Novices can benefit from the educational resources on the website, too.
Trust wallet is best for the following traders:
- Those who are cost conscious
- Those who already use Binance
- Those with a wide range of digital assets.
Price: Free at Trust Wallet.
| Pros | Cons |
|---|---|
| Secure | Can’t directly convert to cold storage |
| Easy to use | Given that this is a self-custody wallet, it would be difficult to recover your funds if it gets hacked |
| Supports a wide range of digital assets | Doesn’t offer two-factor authentication or multi-signature support. |
| Compatible with Android and iOS devices | |
| Has desktop, mobile, and browser support | |
| Users can earn interest on their digital assets | |
Doesn’t collect personal data, which reduces the probability of hacking.
|
What is a crypto wallet and how does it work?
Crypto wallets are virtual wallets for your cryptocurrency. They can be divided into several categories:
- Custodial wallets
- Non-custodial wallets
- Hot wallets
- Cold wallets.
Custodial wallets
Custodial wallets typically rely on third-party software to manage your keys. They’re great for people who forget their passwords if they don’t mind someone else protecting their funds on their behalf.
| Advantages of custodial wallets | Disadvantages of custodial wallets |
|---|---|
| Initial setup is easy | You don’t have full control over your keys |
| The interface is user-friendly | Given that the wallet company is responsible for securing your device if the wallet gets hacked, your funds could be compromised |
| You can recover your account if you forget your password. | Losing your seed phrase or private keys could result in a loss of funds. |
Non-custodial wallets
If you want complete control over your funds and public and private keys, non-custodial wallets are for you. As such, cold wallets are better choices for non-custodial wallets.
Non-custodial wallets come in two categories: Hot and cold wallets.
Hot wallets
A hot wallet is a virtual, software-based wallet that stays connected to the internet. Hot wallets are usually free, making them a more cost-effective option. They can only be unlocked using an encrypted key. Hot wallets often charge for additional features, like trading and staking.
Hot wallets can either be mobile-based (for tablets and smartphones), desktop-based (for browsers and laptops/computers), or both. They’re the easiest to use because, unlike cold wallets, there are no extra steps needed to access them. Because they’re always connected, you can use them often.
- The upside: Hot wallets are typically user-friendly and work well for fast transactions.
- The downside: Although secure, hot wallets can be vulnerable to cyberattacks like hacking and ransomware.
Cold wallets
A cold wallet, also known as a hardware wallet, is a device that isn’t connected to the internet. Cold wallets are believed to be more secure than cold wallets, but they can be misplaced or stolen. They’re suitable for investors who keep large sums in their wallets.
- The upside: Cold wallets are more secure than hot wallets.
- The downside: Cold wallets are less convenient than hot wallets, as they aren’t connected to the internet. It’s difficult to recover a lost or stolen cold wallet.
For security reasons, it’s advisable to use both hot and cold wallets. This will also allow you to enjoy the benefits offered by both wallets. Think about it like this: A cold wallet would give you peace of mind, and a hot one offers the utmost convenience. In other words, each wallet type offers benefits that are missing from the other, so they balance each other out.
| Advantages of non-custodial wallets | Disadvantages of non-custodial wallets |
|---|---|
| You have full ownership over your funds | Losing your private keys could lead to a loss of funds |
| Private keys are kept offline, which makes them particularly challenging to hack. | Losing your seed phrase would leave you with no options to recover your account, so you could lose your funds |
| The interfaces are sometimes complex. |
Key features of crypto wallets
With so many crypto wallets on the market, you must base your decision on several key factors to narrow down your search. The most popular crypto wallets take these elements into account. Look out for them when choosing a crypto wallet:
Security
If you compromise on anything, it shouldn’t be security. It’s important to trust that your crypto wallet is fairly secure. We say fairly because there’s no real guarantee that it can never be hacked.
Determined hackers can find a way around the toughest security measures, but it helps if your wallet is fortified with good security features.
Having said that, the safer option would be a cold wallet. However, you’d still need to keep it safe to avoid having it get lost or stolen. Look for crypto wallets with security measures such as biometric access and two-factor authentication.
Fees
Many crypto wallets are free, although some charge for additional functionalities. Overall, hot wallets are cheaper than cold ones, as there’s no hardware needed. Keep your budget in mind when searching for a crypto wallet in 2023.
Don’t overextend yourself if it’s unnecessary. If you’re a beginner, start with a free, streamlined wallet. You can change it when you’re an advanced user at a later stage.
Ease of use
It’s hard to find a crypto wallet that is difficult to use. Most are user-friendly, but hot wallets offer more ease of use than cold wallets. Cold wallets are more complicated and less convenient, as you need to connect them to your computer each time you use them. However, the wallet itself is simple to use.
Amount of trading
Consider how much trading you’ll be doing before choosing a crypto wallet. The more trading you plan to do, the more features you’ll need in your wallet. A crypto wallet that caters to numerous coins would be a better option for anyone wanting to engage in a lot of trading. Conversely, a wallet like ZenGo would be best for someone starting out with a limited number of coins.
Interoperability
Interoperability refers to the flexibility offered by crypto wallets in viewing and sharing information between various blockchains. (Blockchains are systems used to record cryptocurrency transactions.) In simple, everyday terms, it’s similar to the flexibility offered by email services — the ability of Gmail and Yahoo! users to email each other easily.
Consider the following factors when looking for the best crypto wallet. It should:
- Support a wide range of currencies
- Support the digital assets you’re interested in
- Easily stake your crypto
- Easily lend your crypto.
Which crypto wallet is the best and safest?
When it comes to crypto wallets, there’s something for everyone. There are great options on the market, which we’ve listed in this article. However, the best and safest crypto wallets are DeFi Wallet for hot storage and Ledger Nano X for cold storage. These wallets have all the functions and features you need in a crypto wallet.
DeFi Wallet is free and compatible with a cold wallet like Legder Nano X, making it an excellent choice. Because it’s open-source software, any viruses and threats that creep up can be quickly identified and eliminated. Ledger Nano X is compatible with an unusually large number of coins and tokens. While it comes at a cost, $149 is relatively cheaper than its counterparts. Consider using DeFi Wallet and Ledger Nano X together to get the best of both worlds.
Conclusion
Remember, when using any hardware or software like a crypto wallet — hot or cold storage — you must add another layer of protection to prevent hackers from stealing your crypto. Clario Anti Spy’s Data breach monitor scans the email you use for exchanges and alerts you if it’s in a known leak, so you can secure your accounts fast.
Don’t wait for the next crypto breach, though. Scan your email with Clario Anti Spy now. Download Clario Anti Spy on iOS or Android and run a quick breach check now


