Table of contents
- What is phone cloning?
- How phone cloning works
- How can someone clone your phone?
- 1. Clone a phone using Bluetooth
- 2. Remotely clone a phone using a third-party app
- 3. Using iCloud backup
- 4. SIM card replacement attack
- What can someone see if they clone your phone?
- How to tell if someone cloned your phone
- 1. Receiving phone reboot notifications
- 2. Unusual calls
- 3. Incorrect location in Find My Phone
- 4. SIM update notification from your operator
- 5. Not receiving messages or calls
- 6. Locking your accounts
- How to stop someone from cloning your phone
- 1. Enable two-factor authentication
- 2. Use difficult passwords
- 3. Be careful with unknown networks or devices
- 4. Monitor your device's performance
- 5. Install security software
- 6. Keep your device up to date
- Conclusion
What is phone cloning?
Phone cloning is a deliberate attack on your mobile device that aims to produce a perfect replica of it. When someone clones your phone, they can use your data, intercept your calls, or even impersonate you — and in some cases, someone can clone your phone without you knowing.
How phone cloning works
Phone cloning happens when a hacker duplicates your phone’s unique identifiers, such as the IMEI or SIM card data, to create a replica. This means someone can clone your phone without you knowing and gain access to your calls, messages, login details, and cloud backups.
How can someone clone your phone?
Phone cloning is harder without physical access, but it’s still possible, especially with social engineering, leaked credentials, or spyware. Knowing how someone can clone your phone is the first step in protecting yourself. These include:
- Software exploits: malware or spyware can be installed via malicious apps, phishing links, or unsecured Wi-Fi networks.
- Network sniffing: hackers can intercept data transmitted over the network (e.g., through unencrypted Wi-Fi).
Now, let’s discuss the most common ways attackers use to clone your phone:
- Clone a phone using Bluetooth
- Remotely clone a phone using a third-party app
- Using an iCloud backup
- SIM card replacement attack
1. Clone a phone using Bluetooth
Threat actors can exploit Bluetooth hacking apps to target mobile devices. If they successfully connect to your phone, they can access messages, calls, keyboard strokes, etc.
2. Remotely clone a phone using a third-party app
Certain third-party apps disguise themselves as harmless tools (games, fitness, photo editors), but once installed, they secretly harvest your data. This data can be used to access your Google or iCloud account and remotely clone your phone without you knowing.
Such apps can also access your camera and create risks to your privacy. If you are wondering how to tell if someone is watching you through your phone camera, several indicators can help you figure it out:
- apps that do not require camera access for their functions still have permission
- a sudden drop in battery life
- data spikes when you're not actively using your phone
3. Using iCloud backup
Someone who wants to clone your iPhone via an iCloud backup may accomplish this by having your credentials. Hackers use several methods to exploit backups and access your data:
- Phishing attacks
- Two-factor authentication bypasses.
- Social engineering.
4. SIM card replacement attack
Ever wondered how someone can hack your phone via SIM card? AA SIM swap is one of the easiest ways someone can clone your phone without you knowing. By convincing your carrier to issue a new SIM with your number, attackers receive your calls, texts, and 2FA codes. Having control of your phone number, they can:
- Intercept two-factor authentication.
- Reset passwords.
- Access messaging apps.
What can someone see if they clone your phone?
Сan someone read your text messages from another phone? Yes, they can. Once someone clones your phone, they can access your SMS, emails, saved passwords, photos, banking apps, and even see your real-time location. This includes:
- messages and emails
- contacts
- photos and videos
- apps and accounts access
- location
How to tell if someone cloned your phone
If you’re trying to tell if someone cloned your phone, pay attention to unusual system behavior, missing texts, SIM notifications, and unfamiliar devices in “Find My Phone.” These are common signs that someone can clone your phone without you knowing.
- Receiving phone reboot notifications
- Unusual calls
- Incorrect location in Find My Phone
- SIM update notification from your operator
- Not receiving messages or calls
- Locking your accounts
1. Receiving phone reboot notifications
If your phone suddenly urges you to reboot, this can be a sign of cloning. This is a means malicious actors use to disable your device while introducing a SIM clone temporarily.
2. Unusual calls
Get frequent calls from unknown numbers? Or maybe you’ve noticed calls you didn’t make in your log? This can be a red flag. Watch your monthly expenses closely, especially if they seem unusually high.
3. Incorrect location in Find My Phone
If your phone location indicates a place you've never been, this could be a clear indication of malicious actions. To tell if someone cloned your phone, go to Find My Phone and check if it appears in two places simultaneously. If it does, someone might have created a replica of your phone.
4. SIM update notification from your operator
When you receive a notification about a SIM update from your mobile operator without initiating it, someone might be attempting a SIM card replacement attack. We recommend that you contact your mobile network provider immediately.
5. Not receiving messages or calls
As I already mentioned, a cloned phone can intercept your text messages and calls. If your phone suddenly goes quiet, it’s a strong indication that someone else is getting them.
6. Locking your accounts
Notice suspicious activity on your social media accounts or find yourself locked out? Someone may have already cloned your accounts, so they may quickly replace passwords. This is the time for you to reset your passwords and double-check your safety measures. Access messaging apps.
Following these precautions will help you stop hacking your phone before it happens and minimize the risks of being cloned.
Here’s how to reinforce security on your social media accounts:
- Change your passwords.
- Enable two-factor authentication (2FA).
- Review account activity.
- Update security questions.
- Check linked accounts and apps.
Pro tip
Enable login alerts on your Apple ID or Google account. You’ll get instant notifications if someone tries to access your account from a new device — a key way to tell if someone cloned your phone early.
How to stop someone from cloning your phone
Here’s how to stop someone from cloning your phone and protect yourself if someone can clone your phone without you knowing:
- Enable two-factor authentication
- Use difficult passwords
- Be careful with unknown networks or devices
- Monitor your device's performance
- Install security software
- Keep your device up to date
1. Enable two-factor authentication
Consider adding a two-factor authentication for an extra layer of security. This way, even if someone gains access to your passwords, they’ll need to pass a second verification step.
Here's how to set up two-step verification on your Android device:
- In Settings, go to the Security tab.
- Scroll to the Signing into Google section.
- Tap Two-Step Verification.
- Enter your password if prompted.
- Tap Get Started.
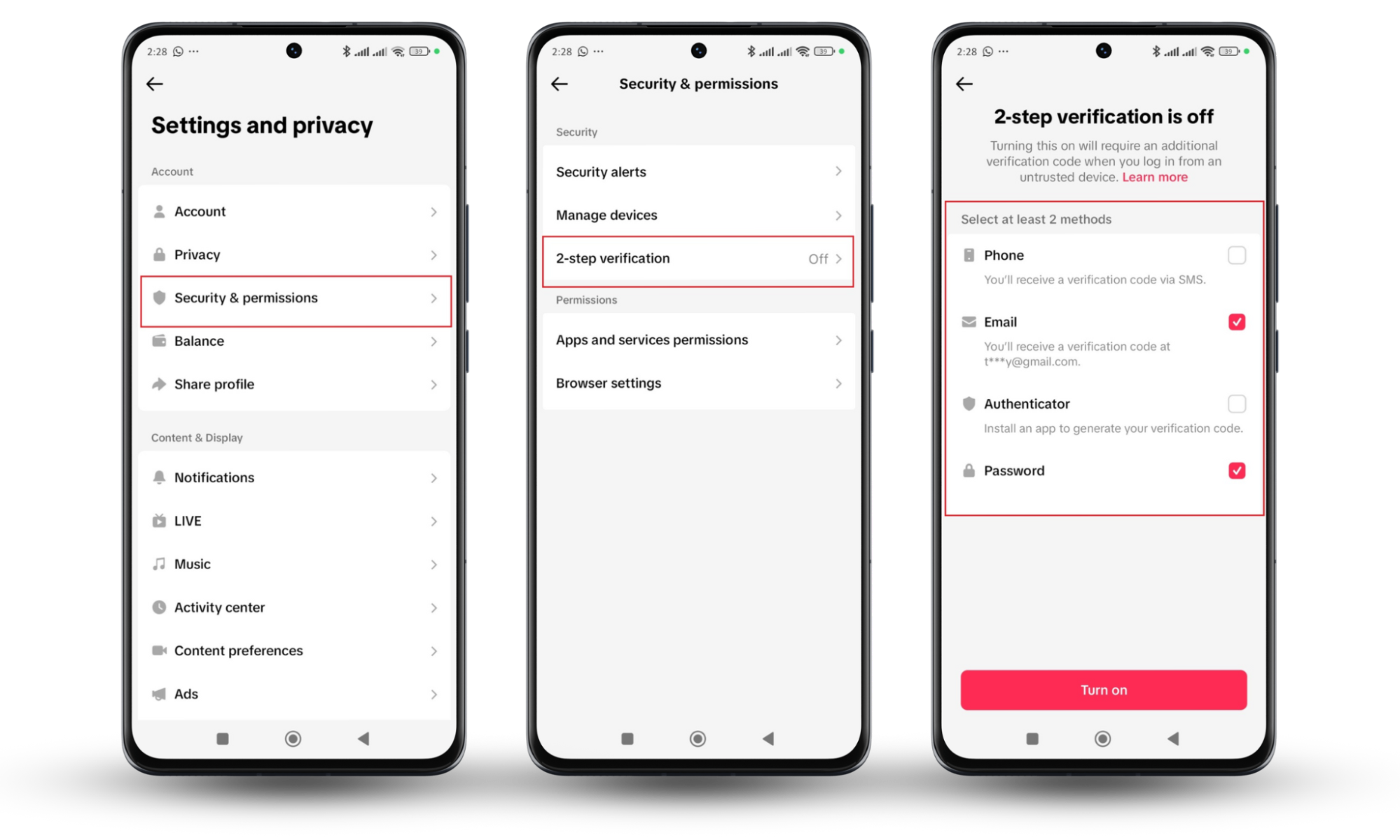
Then, follow the prompts to select your second verification method.
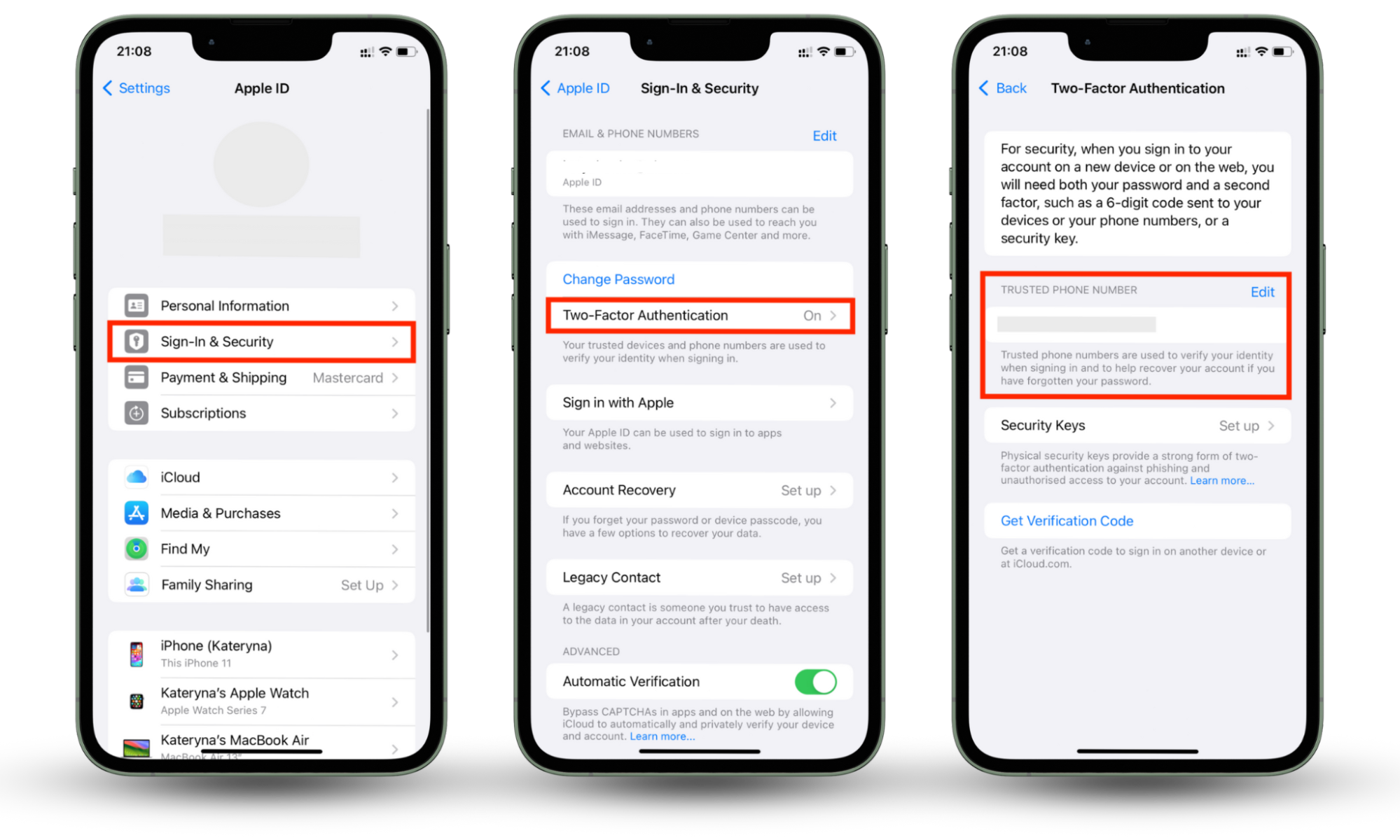
Here’s how to enable a two-factor authentication on your iPhone:
- On your iPhone, go to Settings and tap on your Apple ID.
- Select Sign-In & Security.
- Tap on Two-Factor Authentication.
- Enter a phone number to receive verification codes.
- Enter the verification code sent to your iPhone.
2. Use difficult passwords
When creating new passwords, consider incorporating a diverse array of characters. A strong password includes uppercase and lowercase letters, numbers, and symbols such as @, #, $, %, &, and *.
3. Be careful with unknown networks or devices
Public networks can’t guarantee a safe browsing experience, so you should avoid using them. Also, never connect your phone to an unknown Bluetooth or RFID device. This might be an effort to clone the signals from your phone.
4. Monitor your device's performance
Unusual battery drain, slowdowns, or unexpected behavior can indicate cloning or other malicious activities.
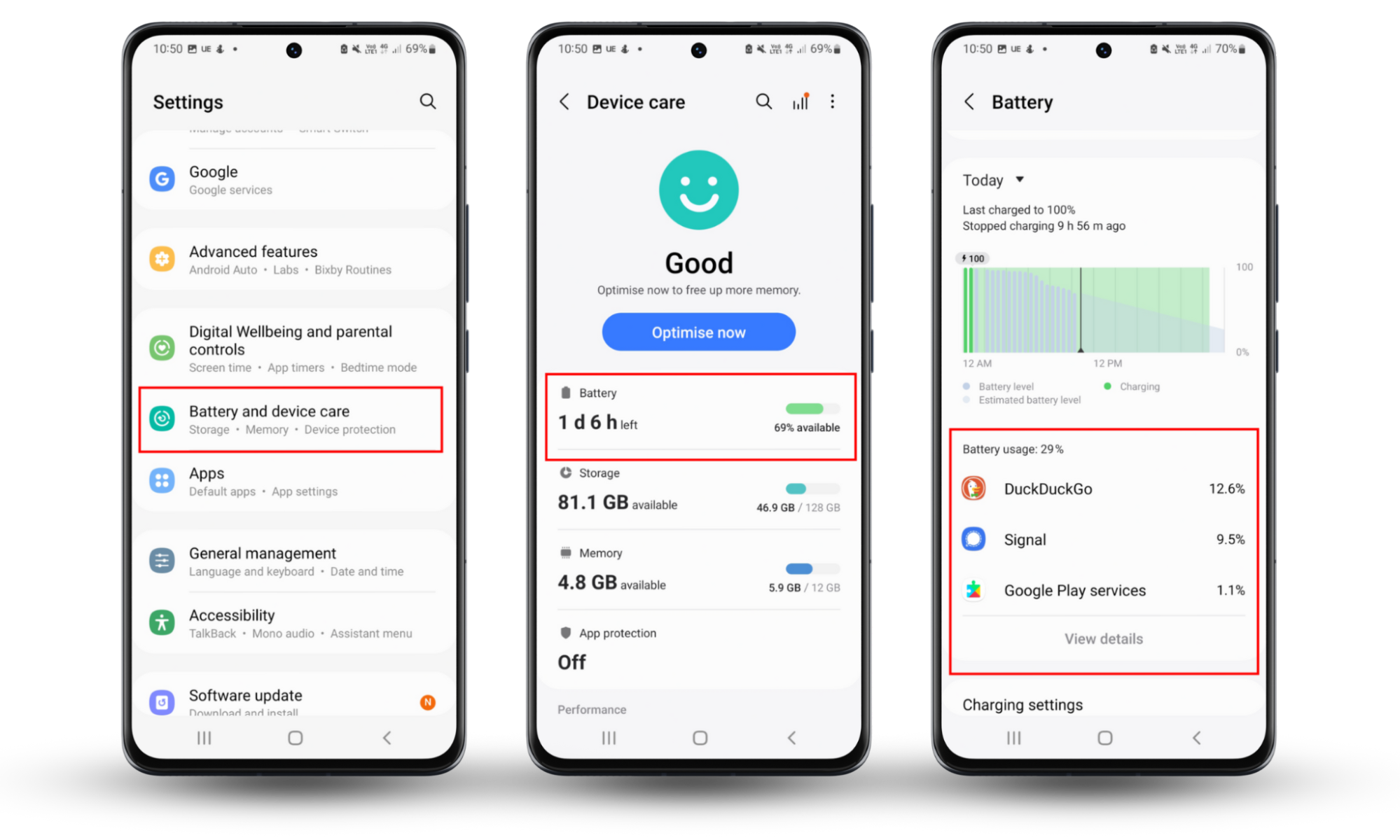
To check for battery performance spikes and what apps are draining your Android device, follow these steps:
- Go to Settings.
- Tap Battery and device care > Device care.
- Check for battery use spikes and apps you do not recognize.
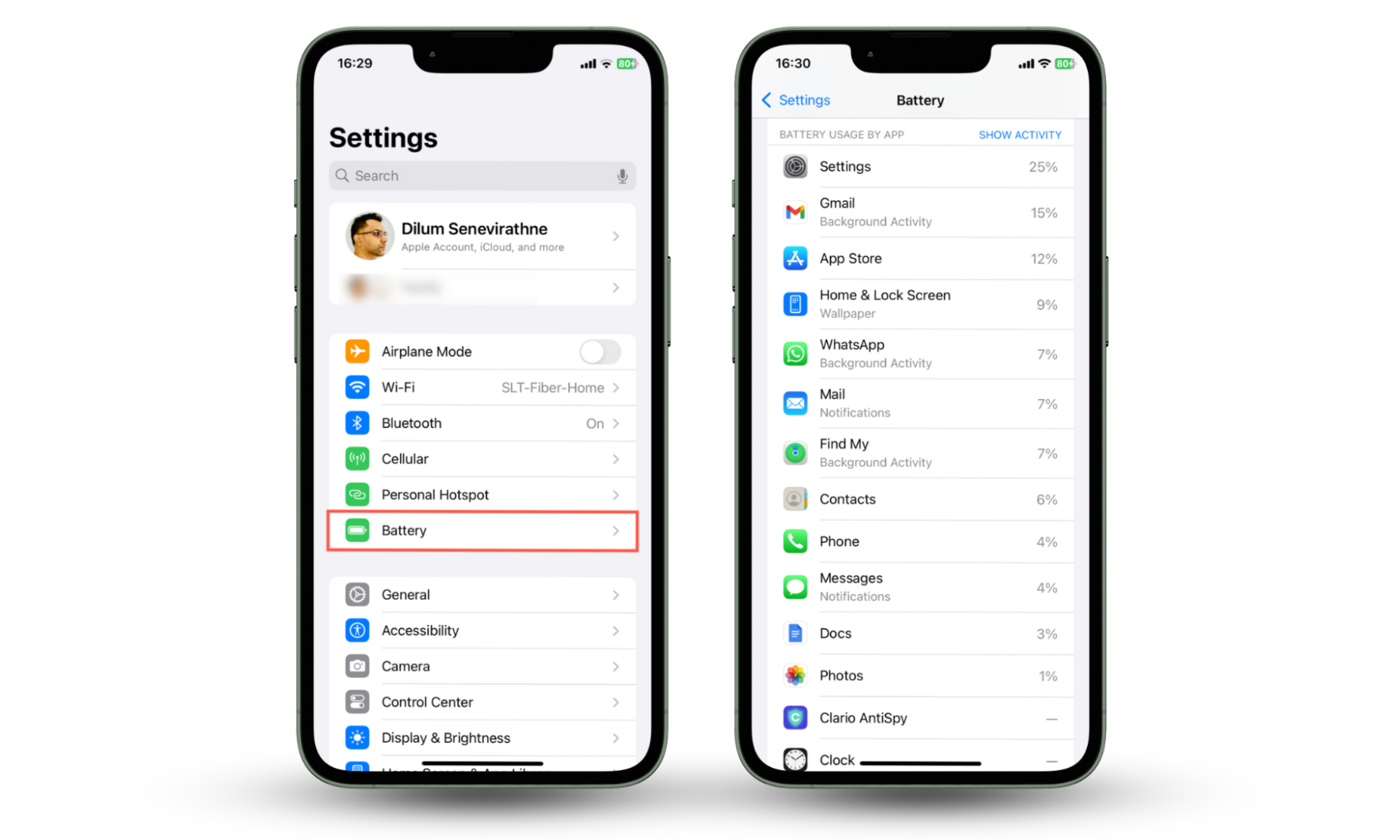
To check for battery performance spikes and what apps are draining your iPhone, follow these steps:
- Go to Settings.
- Tap Battery.
- Check for unusual battery use spikes and apps you do not recognize.
5. Install security software
To guard against possible cloning efforts, consider adding anti-spyware software to your device. Clario Anti Spy was created to protect your messages, location, contact list, photos, videos, etc., from unauthorized access. It runs on Android and iOS and offers an anti-spy setup, hidden app scan, 24/7 human assistance, and much more.
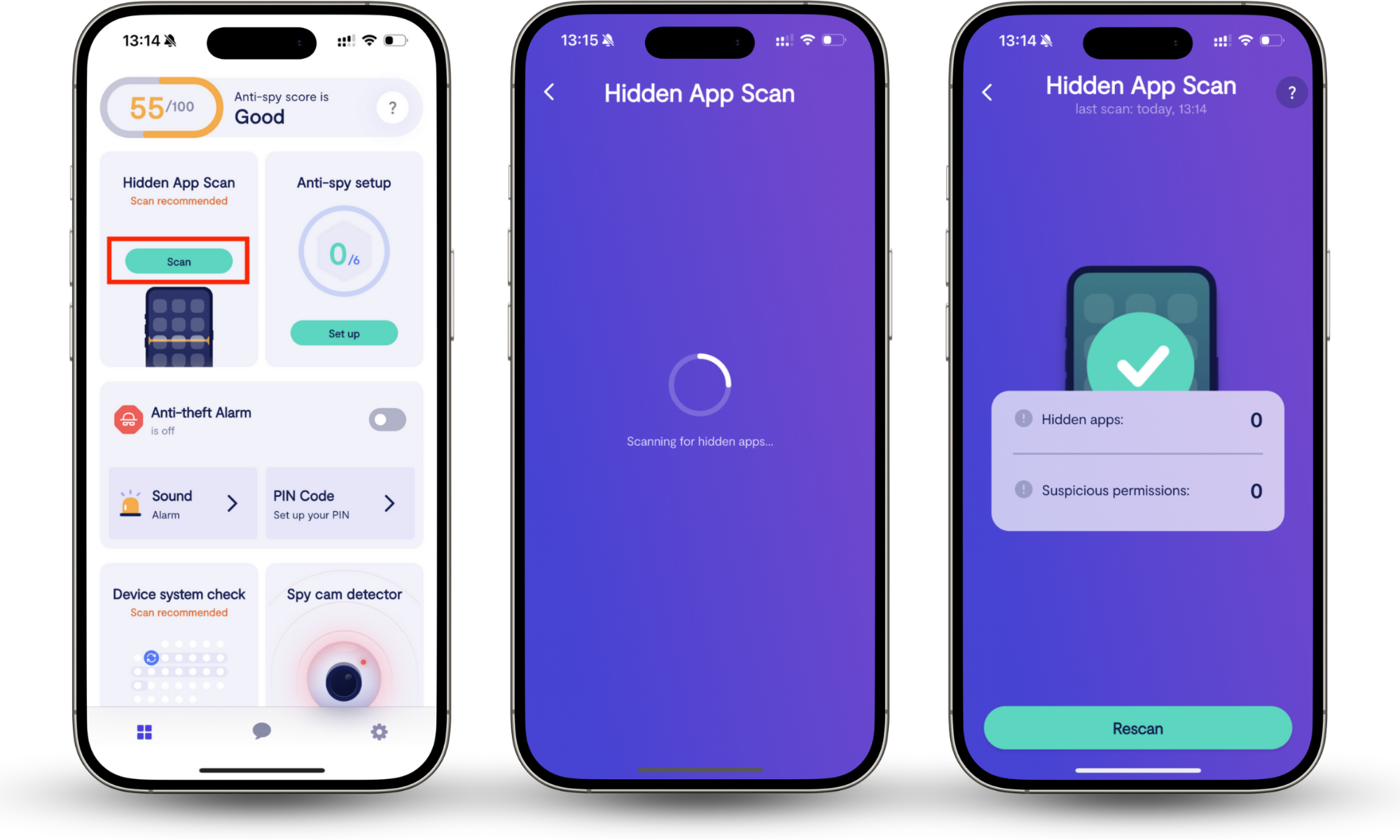
Use Clario Anti Spy’s Hidden app scan to detect spying apps on your phone. Hidden app scan searches your device for malicious or disguised apps that could collect your data and help attackers clone your phone. It also checks which apps have risky permissions, such as camera, microphone, or location access, that don’t match their function.
Follow these steps to run Clario Anti Spy’s Hidden app scan:
- Download Clario Anti Spy and sign up.
- Open the app and select Hidden app scan.
- Tap Scan to check for suspicious or hidden apps.
- Review the list of suspicious app and permissions.
- Follow the recommendations to remove or restrict any threats.
6. Keep your device up to date
Ensure regular software updates to patch vulnerabilities and keep your device secure against the latest threats.
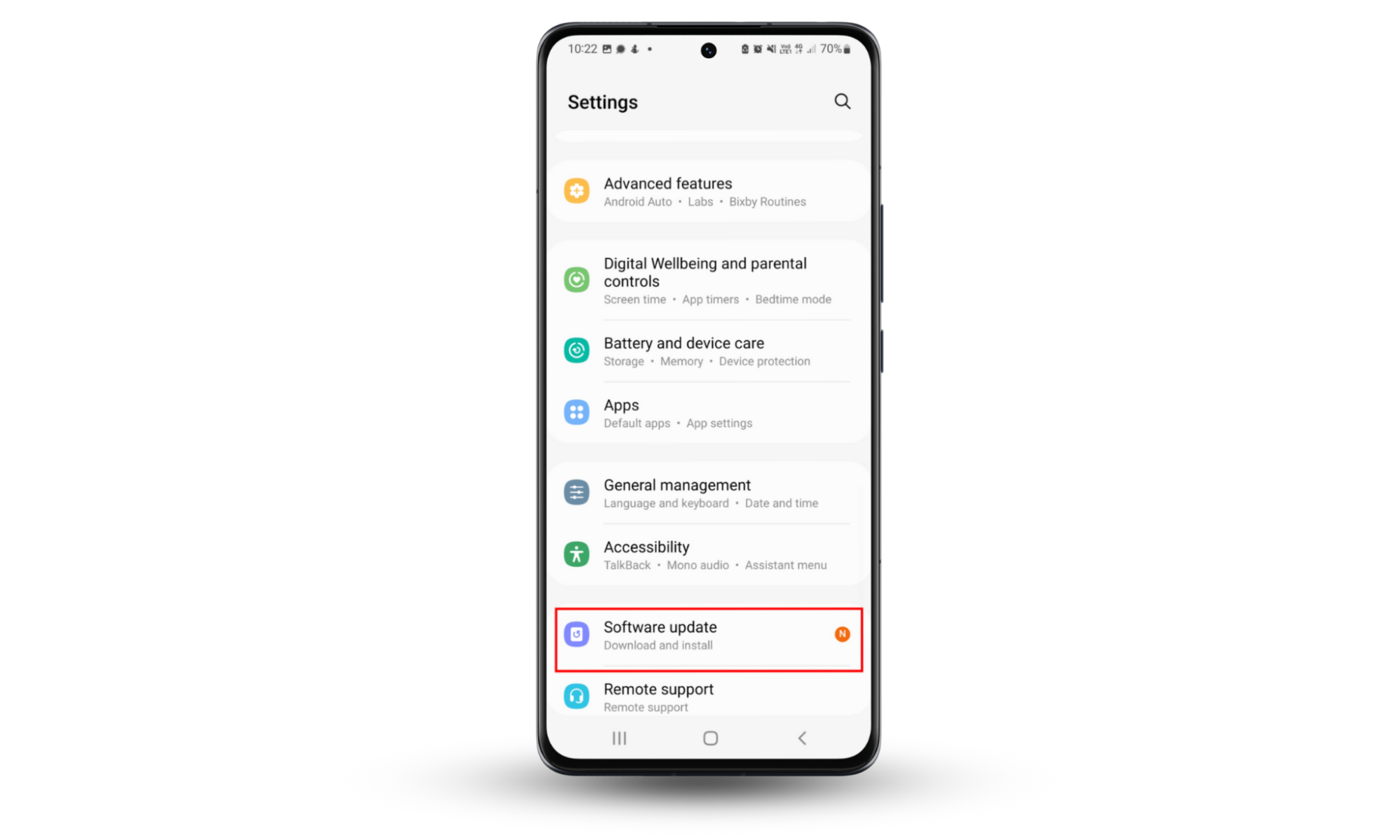
Here’s how to update software on an Android device:
- Go to Settings.
- Tap Software Update and install any available update.
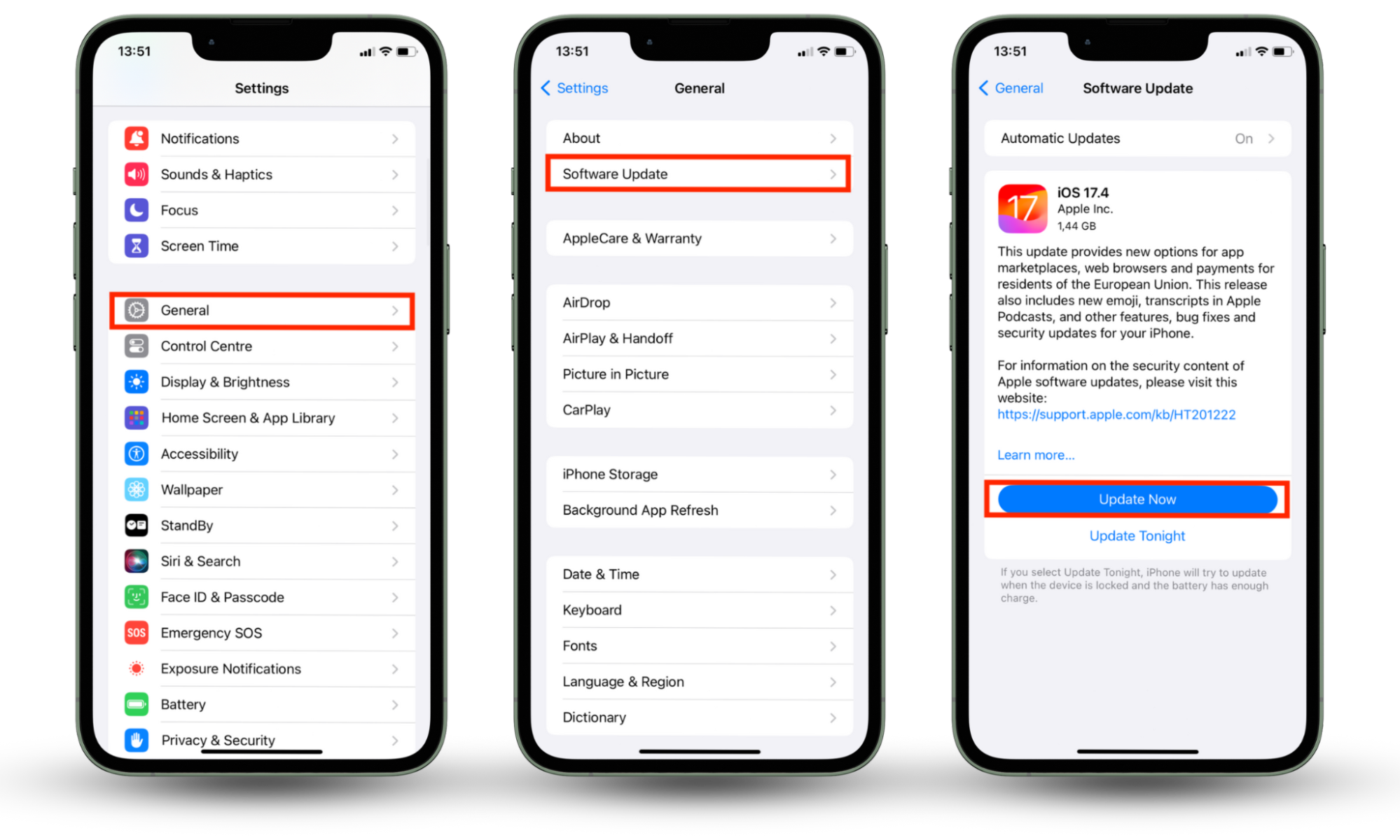
Here’s how to update software on your iPhone and turn on Automatic Updates:
- Go to Settings, and tap General.
- Tap Software Update.
- Click Update Now.
- After the update is done, go back to the Software update page and tap Automatic Updates.
- Set on Automaticly Install and Automaticly Download.
Conclusion
So, can someone clone your phone without you knowing? Unfortunately, the answer is yes. Though rarely, phone cloning still happens and can have negative implications for your privacy and security. But how to know if your phone is being tracked? Download Clario Anti Spy to safeguard your digital life. Your phone is an extension of yourself—protect it accordingly.


