Table of contents
- What is voicemail hacking?
- Are you at risk of hacking by listening to voicemail?
- How to stay safe after listening to suspicious voicemail
- 1. Avoid calling back unknown numbers
- 2. Verify legitimacy of message
- 3. Be wary of requests for personal information
- 4. Enable multi-factor authentication (MFA)
- 5. Update your voicemail PIN
- 6. Monitor your accounts for unusual activity
- Conclusion
What is voicemail hacking?
Voicemail hacking is someone illegally accessing your voicemail to listen to your messages. Hackers often exploit weak PINs, use social engineering tactics, or manipulate network settings to access your voicemail. Once inside, they can listen to your messages, change settings, or use the access for identity theft and phishing scams. Knowing this risk is part of learning how to stop someone from listening to your phone calls and voicemails.
Most often, a scammer will call into your voicemail system, looking for mailboxes that use the default security PIN. Because many people never change their PIN code, a hacker can try a common code like “1234” until they gain access to a mailbox.
Did you know you can check whether your phone has been hacked using codes? Check out these phone hack check codes to see if you’re at risk.
Are you at risk of hacking by listening to voicemail?
Simply listening to a voicemail cannot transmit malicious code or directly lead to hacking. However, security risks arise when hackers exploit voicemail vulnerabilities. These risks often stem from default PINs, caller ID spoofing, and tactics like phishing or vishing (otherwise known as voice phishing). Older systems and unencrypted networks are particularly vulnerable.
How to stay safe after listening to suspicious voicemail
To stay safe from voicemails, you need to be proactive. If you receive a suspicious voicemail, avoid responding or sharing personal information. Verify the caller's identity through official channels, report the call, and update your voicemail security with a strong PIN. Stay informed about scams and use caller ID services to block potential threats effectively.
Here’s what to do if you listen to a suspicious voicemail:
1. Avoid calling back unknown numbers
What numbers should you avoid answering? Firstly, always be cautious before contacting unfamiliar numbers, and never return calls to numbers you think are suspicious. Scammers often use callback tactics to lure you into sharing sensitive information or incur high charges from premium-rate numbers.
These calls might appear urgent or official, but calling back can expose you to phishing attempts.
2. Verify legitimacy of message
Cross-check a voicemail’s content by directly contacting the sender through verified and official channels, like calling the business's publicly listed customer service number. Hackers frequently pretend to be banks, government agencies, or service providers to deceive you into acting quickly, which can lead to security breaches.
3. Be wary of requests for personal information
Never share personal or financial information based on a voicemail. Scammers exploit these messages as part of social engineering schemes, trying to scare you into acting without thinking. Legitimate companies won’t request sensitive information like passwords or credit card numbers through voicemails.
4. Enable multi-factor authentication (MFA)
Enabling multi-factor authentication (MFA) adds a powerful layer of security. MFA requires an additional verification step beyond the usual PIN, with a second code sent to your smartphone or email. This extra measure ensures that even if a hacker obtains your PIN, they wouldn’t be able to access your voicemail without access to your phone or email account.
You might be wondering, is it possible to hack a phone with MFA enabled? The answer is yes, unfortunately. But it’s much, much harder to do so.
5. Update your voicemail PIN
If you suspect scammers are targeting your voicemail, update your PIN to a complex, unique code. Avoid easy-to-guess combinations like "1234" or your birth year. Change your PIN every few months to reduce the risk of unauthorized access and strengthen your voicemail’s security.
6. Monitor your accounts for unusual activity
Keep an eye out for signs of unusual activity on your accounts, including unexpected logins, transactions, or messages. Hackers might exploit your voicemail’s vulnerabilities to collect details for phishing or breaching accounts. Detecting these suspicious activities early means you can change your passwords, secure your accounts, and avoid further damage.
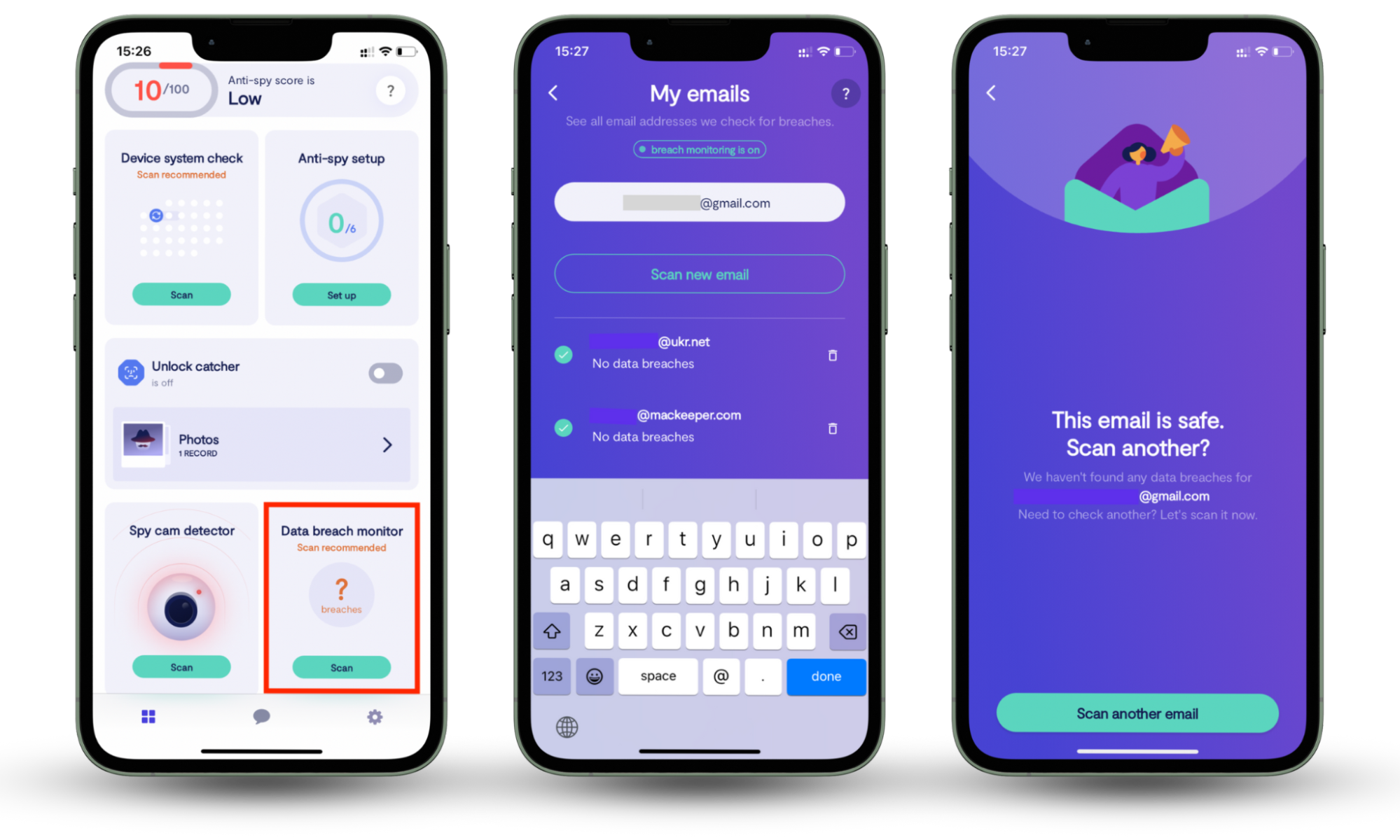
Clario Anti Spy’s Data breach monitor can help you monitor your accounts to catch suspicious activity. It constantly scans your email addresses and online accounts to see which ones have been compromised or are accessible to spies.
To use Clario Anti Spy’s data breach monitor:
- Download Clario Anti Spy and create an account.
- Under Data breach monitor, press Scan.
- Press Scan new email, then enter your email address. Clario Anti Spy will inform you whether your account has been compromised and walk you through how to secure it.
Conclusion
Voicemail scams are a real threat, but you can protect yourself by verifying sources and strengthening security. Stay ahead of hackers with Clario Anti Spy’s data breach monitor, which alerts you to potential threats. Download Clario Anti Spy now to secure your digital privacy and peace of mind.


