Table of contents
- Why follow cybersecurity experts?
- Top cybersecurity experts
- 1. Bob Sullivan: ID Theft and consumer protection expert
- 2. Mikko Hypponen: Keeping businesses safe from global cyber threats
- 3. Bill Brenner: Cybersecurity for the modern enterprise
- 4. Jack Rhysider: Cybercrime investigations & data breaches
- 5. Lesley Carhart: Threat analysis & digital security
- 6. Brian Krebs: Cybercrime investigations & data breaches
- 7. Charlie Miller: Automotive security & vulnerabilities
- 8. Josephine Wolff: Cybersecurity policy & digital safety
- 9. Troy Hunt: Personal cybersecurity & data privacy
- 10. Shira Rubinoff: Cybersecurity & blockchain security
- Conclusion
Why follow cybersecurity experts?
In today’s ever-changing digital world, cybersecurity is more critical than ever. According to the Verizon Data Breach Investigations Report, over 40% of data breaches are caused by hacking, with phishing and credential stuffing being among the most common attack methods. With new threats emerging daily, it’s essential to stay informed by following leading experts in the field. These professionals provide not only the latest insights on vulnerabilities and risks but also share actionable advice on how to safeguard your data and privacy.
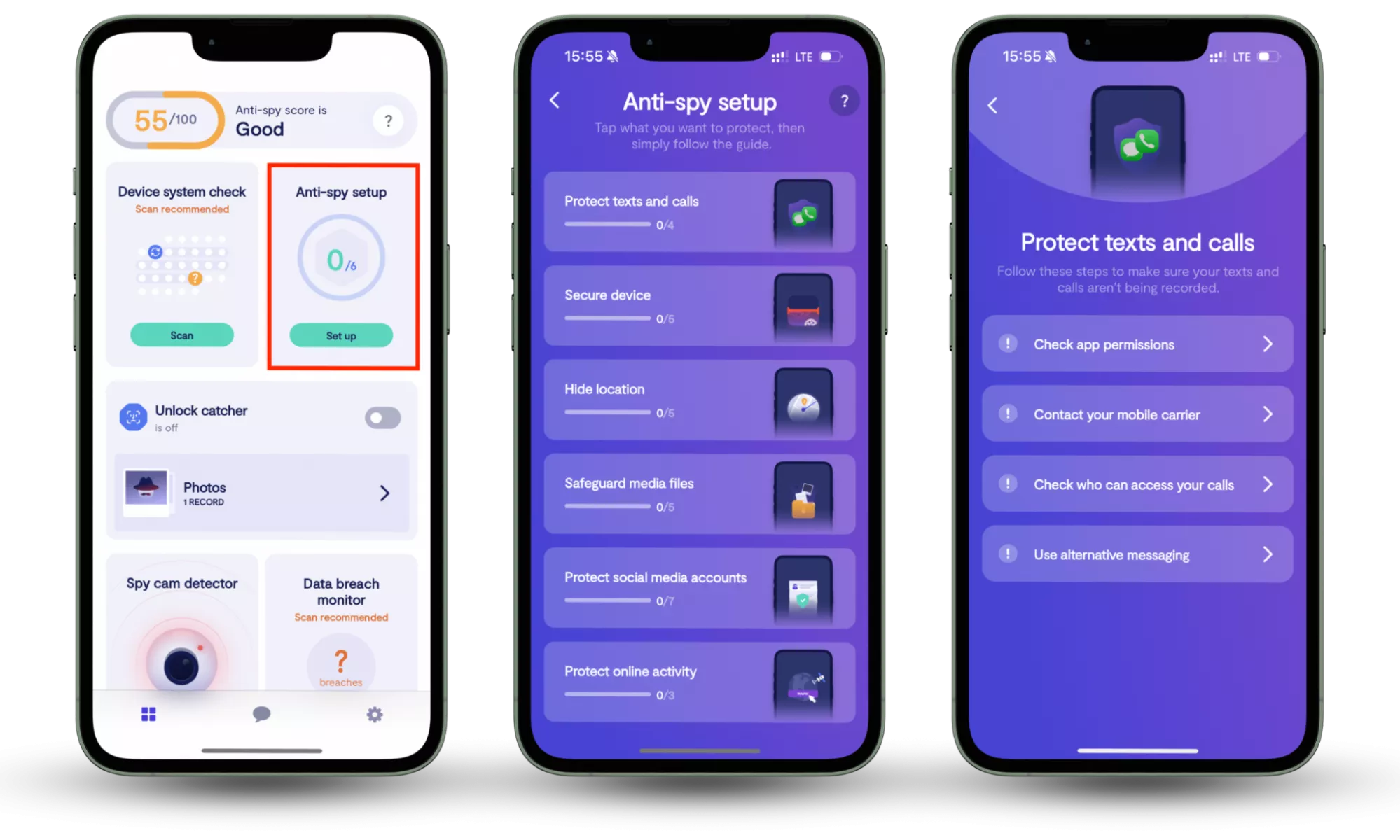
However, even with expert advice, many individuals and businesses still face security challenges due to invisible threats like spyware and unauthorized access. That’s where Clario Anti Spy comes in, providing advanced protection from the rising tide of spyware, tracking tools, and unwanted surveillance. With a simple, intuitive setup.
Recently, we had a conversation with one of our customers, a busy professional who became increasingly concerned about her online security after hearing about the rise in cyberattacks and spyware incidents. She had noticed strange behavior on her phone, such as slow performance, battery drainage, and increased pop-up ads. This raised red flags, and she started to worry that her personal data might be compromised. Having heard about spyware infecting mobile devices, she didn’t know how to protect herself from such threats.
Feeling uneasy about the situation, she decided to take action. After contacting us, we quickly ran a scan using Clario Anti Spy’s Anti-spy setup. Within minutes, our cybersecurity experts detected several hidden apps running on her phone without her knowledge. To her shock, our customer discovered that many of these apps had unauthorized access to sensitive parts of her phone, including her camera, microphone, and personal data.
To run Clario Anti Spy's Anti-spy setup on your phone, follow these steps:
- Download Clario Anti Spy, create an account, and sign in.
- Under Anti-spy setup, select Set up.
- Follow the guide to secure your device and prevent Netflix from being able to spy on you.
Top cybersecurity experts
Cybersecurity is a vast field, and each expert has their unique area of expertise. Whether you’re interested in consumer protection, corporate security, or understanding the latest cyber threats, there is an expert for every aspect of digital safety. Here are some of the top cybersecurity leaders and what they specialize in:
1. Bob Sullivan: ID Theft and consumer protection expert
Why follow him?
Bob Sullivan is an investigative journalist and author renowned for his work on identity theft and consumer protection. With nearly two decades of experience, he has exposed scams, fraud, and vulnerabilities in the consumer tech space. His insights help individuals understand the risks to their personal data and how to protect themselves from identity theft.
Practical advice on staying safe:
- Monitor your credit regularly: Use free credit monitoring services to track any suspicious activity.
- Set up fraud alerts: Contact your bank and credit bureaus to set up fraud alerts and prevent unauthorized credit inquiries.
- Use multi-factor authentication (MFA): Enable MFA wherever possible to add an extra layer of security to your accounts.
- Beware of phishing scams: Always verify the source of emails or messages before clicking links or sharing sensitive information.
2. Mikko Hypponen: Keeping businesses safe from global cyber threats
Why follow him?
Mikko Hypponen is the Chief Research Officer at F-Secure and a globally recognized cybersecurity expert. His extensive experience in researching and mitigating global cyber threats, such as ransomware and cyber espionage, has made him a leading voice in the field. Mikko's work focuses on protecting businesses from large-scale cyberattacks and predicting emerging risks.
Practical advice on preventing ransomware and cyberattacks:
- Update software and systems regularly: Ensure all software, including operating systems and antivirus, is up to date to prevent exploitation of known vulnerabilities.
- Backup your data: Maintain regular backups of critical files to mitigate the impact of ransomware attacks.
- Educate your employees: Train employees to recognize phishing attempts and to follow safe practices when dealing with emails or attachments from unknown sources.
- Conduct regular security audits: Evaluate your cybersecurity systems regularly to identify vulnerabilities and patch them before they can be exploited.
3. Bill Brenner: Cybersecurity for the modern enterprise
Why follow him?
Bill Brenner is a cybersecurity expert with extensive experience working at the Institute for Applied Network Security (IANS). His deep insights into corporate security and risk management help businesses build more resilient defenses against cyberattacks.
Practical advice on enterprise cybersecurity:
- Implement continuous threat monitoring: Use advanced threat detection systems to monitor network activity 24/7 and catch breaches early.
- Develop an incident response plan: Prepare a clear incident response plan for your team, detailing steps to take in the event of a breach.
- Layer your security: Use a multi-layered security approach, including firewalls, encryption, and intrusion detection systems to protect sensitive company data.
- Regularly test your security systems: Conduct penetration testing and vulnerability assessments to evaluate the effectiveness of your defenses.
4. Jack Rhysider: Cybercrime investigations & data breaches
Why follow him?
Jack Rhysider is the host of Darknet Diaries, a popular podcast that explores the hidden side of the internet, including hacking, cybercrime, and data breaches. Jack interviews cybersecurity experts, hackers, and insiders, offering listeners an in-depth look at the world of cybercrime.
Practical advice on avoiding cybercrime and data breaches:
- Stay vigilant about data leaks: Regularly check if your personal or business data has been exposed using tools like Have I Been Pwned.
- Be careful with IoT devices: Ensure that all connected devices in your home or workplace are securely configured and regularly updated to prevent them from being exploited.
- Understand dark web activity: Stay informed about the dark web’s activities by listening to expert podcasts or reading reports on new trends in cybercrime.
- Limit personal information sharing: Be cautious about sharing personal information on social media or untrusted websites.
5. Lesley Carhart: Threat analysis & digital security
Why follow her?
Lesley Carhart is one of the top female professionals in the cybersecurity sector and a highly respected threat analyst at Dragos, Inc., specializing in industrial control systems and critical infrastructure protection. She has spent over a decade analyzing digital threats and has become a key voice for cybersecurity in both private and government sectors.
Practical advice on threat detection and response:
- Conduct threat intelligence gathering: Leverage open-source threat intelligence tools to stay informed about emerging vulnerabilities and active attacks.
- Harden your security configurations: Regularly audit and harden your network configurations to prevent common attack vectors such as misconfigured firewalls or weak access controls.
- Implement security monitoring systems: Deploy advanced security monitoring systems like SIEM (Security Information and Event Management) to identify unusual patterns in your network traffic and mitigate potential threats.
- Focus on incident response readiness: Ensure your team is trained to respond quickly and effectively to security incidents by running regular incident response simulations.
6. Brian Krebs: Cybercrime investigations & data breaches
Why follow him?
Brian Krebs is a leading investigative journalist known for his work on cybercrime and data breaches. His blog, KrebsOnSecurity, is a trusted source of information on the latest cyberattacks, malware, and security vulnerabilities. Brian’s reporting helps businesses and individuals stay informed about the latest threats in the cybersecurity landscape.
Practical advice on protecting yourself from cybercrime:
- Use strong passwords and unique credentials: Avoid reusing passwords across accounts and use complex, long passwords to protect your accounts.
- Monitor your financial accounts: Keep an eye on your bank statements and credit card activity for unauthorized transactions.
- Implement security software: Use a reputable antivirus program and a firewall to protect your devices from malware and unauthorized access.
- Know your rights: Understand what actions to take if your data is compromised, including how to file a complaint with regulatory bodies like the FTC.
7. Charlie Miller: Automotive security & vulnerabilities
Why follow him?
Charlie Miller is a cybersecurity researcher famous for his work in automotive security. His research on remote car hacking led to the recall of over a million vehicles and significantly impacted the automotive industry’s approach to cybersecurity.
Practical advice on securing connected vehicles:
- Secure IoT devices in vehicles: Ensure that all connected features of your vehicle, such as keyless entry or infotainment systems, are securely configured.
- Software updates: Regularly update the software of connected cars to patch vulnerabilities that could be exploited by attackers.
- Know the vulnerabilities in your vehicle: Research your vehicle's security features and stay informed about potential weaknesses that could be exploited.
- Limit access to vehicle systems: Be cautious about who has access to your car’s onboard computer systems, especially in the case of remote services.
8. Josephine Wolff: Cybersecurity policy & digital safety
Why follow her?
Josephine Wolff is a cybersecurity researcher and academic known for her work on cybersecurity policy and the social and political implications of cybercrime. She has authored numerous articles for The New York Times, Wired, and other major outlets, focusing on how cybercrime affects society at large.
Practical advice on cybersecurity policy and digital safety:
- Advocate for stronger cybersecurity regulations: Engage in policy discussions about strengthening regulations around data privacy and security in the digital age.
- Understand cybersecurity’s social impact: Learn about the socio-political effects of cybercrime and how policies can mitigate its impact on society.
- Educate on data protection: Spread awareness about the importance of protecting personal and business data to minimize risks of exposure.
- Follow legal and ethical guidelines: Stay informed about the legal implications of data breaches and follow ethical practices when handling sensitive information.
9. Troy Hunt: Personal cybersecurity & data privacy
Why follow him?
Troy Hunt is the creator of Have I Been Pwned (HIBP), a website that allows users to check whether their accounts have been involved in data breaches. Troy is a leading expert on personal cybersecurity and privacy.
Practical advice on protecting your personal data:
- Check data breaches regularly: Use tools like Have I Been Pwned to check whether your email addresses or other personal data have been compromised in any breach.
- Use strong, unique passwords: Make sure your passwords are long, unique, and stored in a password manager to keep them secure.
- Enable multi-factor authentication (MFA): Always enable MFA on accounts that support it to add an additional layer of security.
- Be aware of data privacy: Understand what data you’re sharing online and how it may be used or misused by third parties.
10. Shira Rubinoff: Cybersecurity & blockchain security
Why follow her?
Shira Rubinoff is a thought leader in cybersecurity, specializing in blockchain security and the role of women in tech. As the president of Prime Tech Partners, Shira has worked with major corporations to improve their cybersecurity strategies.
Practical advice on blockchain security and digital safety:
- Understand blockchain security: Learn about the security risks associated with blockchain technologies and how to protect your crypto assets.
- Secure your digital identity: Use secure authentication methods and regularly update your security settings to protect your digital identity in the blockchain space.
- Promote diversity in tech: Support initiatives that foster diversity in the cybersecurity industry, especially for women and underrepresented groups.
- Educate on security: Encourage others to prioritize cybersecurity and take proactive measures to protect their online presence.
By staying up-to-date with their work, you can stay one step ahead of cybercriminals and ensure your personal and professional digital environments remain secure. The rise in cyberattacks and data breaches means that cybersecurity is no longer optional; it’s a necessity to protect both your personal and business assets.
Conclusion
Cybersecurity is an ongoing challenge in today’s digital landscape, with threats like data breaches and spyware targeting us every day. While expert advice helps us stay informed, many individuals continue to face challenges with invisible threats like spyware and unauthorized surveillance. That’s where Clario Anti Spy comes in, offering a straightforward solution to protect your mobile device. By combining expert insights with the right tools, you can protect your privacy, stay ahead of cybercriminals, and navigate the increasingly complex world of digital security with confidence.


