Table of contents
- Why Two-Factor authentication (2FA) is essential for account security
- What is 2FA and multi-factor authentication (MFA)?
- How to set up 2FA
- How to setup 2FA for Instagram
- How to setup 2FA for Apple ID
- How to set up 2FA for WhatsApp
- How to use 2FA to prevent a security breach
- What are the most popular 2FA methods?
- What are the least secure 2FA methods?
- What are the most secure 2FA methods?
- How to log in to an account after losing a phone?
- Stay Ahead of Account Compromise
Why Two-Factor authentication (2FA) is essential for account security
Two-factor authentication (2FA) is essential because passwords alone are routinely exposed through data breaches, phishing, and credential reuse attacks. By requiring a second verification factor, 2FA blocks unauthorized access even when a password has been compromised. This additional layer significantly reduces account takeover risk and protects sensitive data tied to email, banking, and social platforms.
No matter how strong your password is, it won’t do you any good if stolen by cybercriminals. Enabling two-factor authentication (2FA) will ensure no one can access your email or any other account with the password alone.
Passwords are most often stolen through phishing websites, malware, data breaches, and automated credential stuffing attacks that reuse leaked login details across multiple platforms. Because many users reuse passwords, one exposed login can quickly lead to multiple compromised accounts.
According to Microsoft, 2FA reduces the likelihood of an account breach by a whopping 99.9%. Despite the security advantages of 2FA, its adoption rates are woefully low. For example, only 2.3% of Twitter users have enabled this additional security function.
Luckily, you don’t have to be a tech expert to protect your accounts with multi-factor authentication (MFA). Here, you can learn what 2FA is and how to set it up in our article.
Important to know
2FA significantly improves security, but not all second factors offer equal protection. SMS-based codes are more vulnerable than app-based authentication or hardware security keys. Choosing a stronger method further reduces the likelihood of successful phishing or interception attacks.
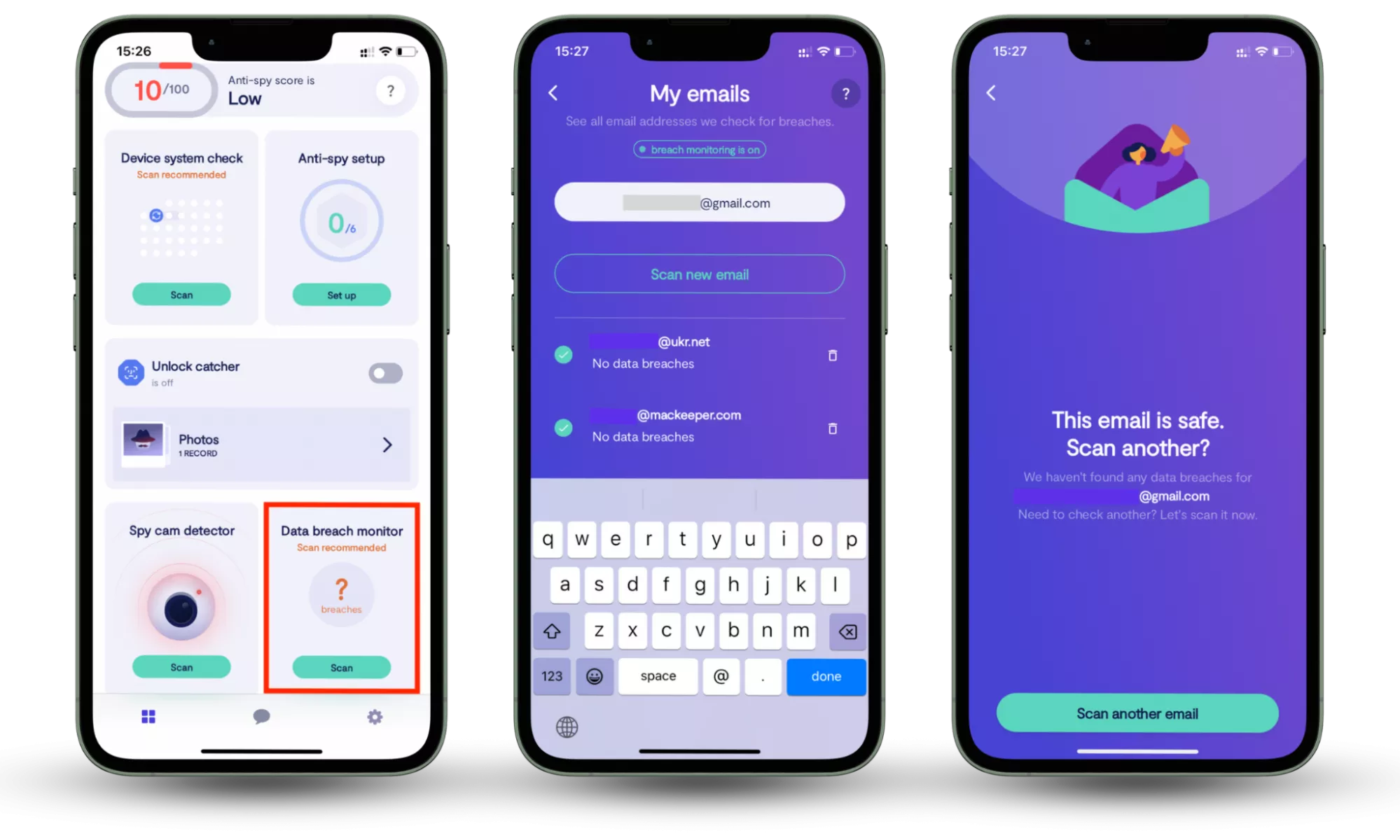
Even with 2FA enabled, it’s important to know if your credentials have already been exposed in a data breach. Clario Anti Spy includes a built-in Data breach monitor that scans your email address against known breach databases and alerts you if your data appears in a leak.
How to check whether your information is compromised:
- Download Clario Anti Spy and subscribe.
- Open the app, and, under Data breach monitor, tap Scan.
- Enter your email address.
- When the scan is complete, follow the on-screen guidance to review any data breaches.
- Repeat the process for any other email addresses.
What is 2FA and multi-factor authentication (MFA)?
Multi-factor authentication (MFA) is a login verification method requiring several verification factors to access an account. MFA with two levels of protection is referred to as two-factor authentication or 2FA. To access an account protected by 2FA, a user has to submit their login and password as well as a verification code sent to their device.
MFA requires three components:
| Authentication factor | What it means | Examples |
| Something you know | Information only you should know | Password, PIN, passphrase |
| Something you have | A physical device or token in your possession | Phone receiving a login prompt, authenticator app code (TOTP), hardware security key |
| Something you are | A biometric trait used for identity verification | Fingerprint, Face ID, retina or voice recognition stored on the device |
A combination of any two of these three factors is called 2FA. To access an account protected by 2FA, you need a password you know and a code sent to a phone you have.
How to set up 2FA
Setting up 2FA usually means turning on an extra sign-in step in your account’s security settings and choosing a verification method. Most services support SMS codes, authenticator apps, or device prompts. For stronger protection, prefer an authenticator app or security key when available. The exact clicks vary by platform, but the setup flow is typically: enable 2FA, register a method, then confirm with a one-time code.
To set up 2FA, you need a phone to verify your identity using a code provided via text message or an authentication app.
Before you start:
- Make sure you can access the email address tied to the account
- Update your phone number if the service uses SMS as a fallback
- If available, install an authenticator app and plan to use it instead of SMS
- Save backup codes (if offered) somewhere offline you can reach later
How to setup 2FA for Instagram
To enable two-factor authentication on Instagram, you need to access your account’s Security settings and choose a verification method, such as a text message or an authentication app. Once activated, Instagram will require a second verification step each time someone attempts to log in from a new device.
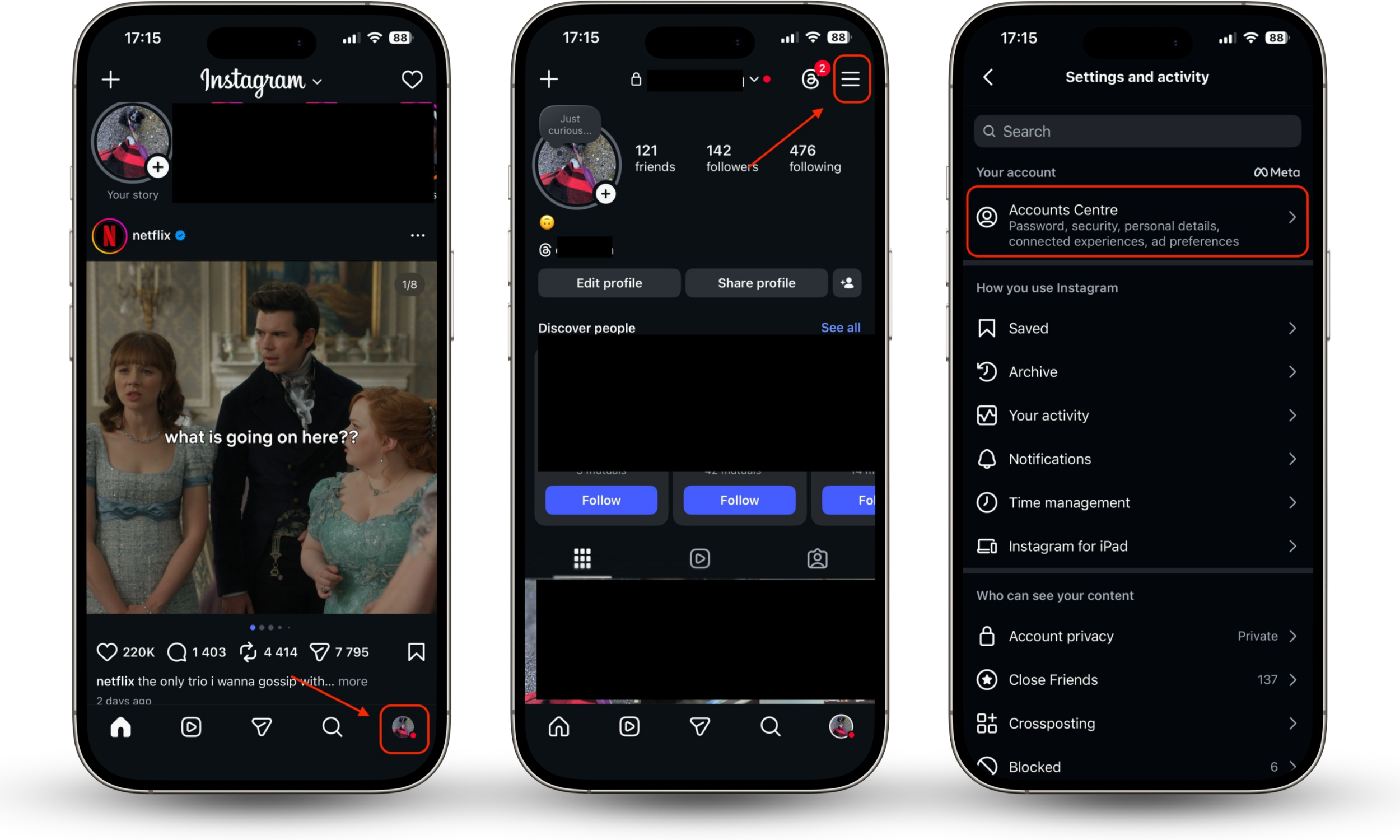
Here’s how to activate 2FA for Instagram:
- Tap a user sign or your profile picture at the bottom right.
- Click on the 3 lines at the top right.
- Tap on Accounts Centre.
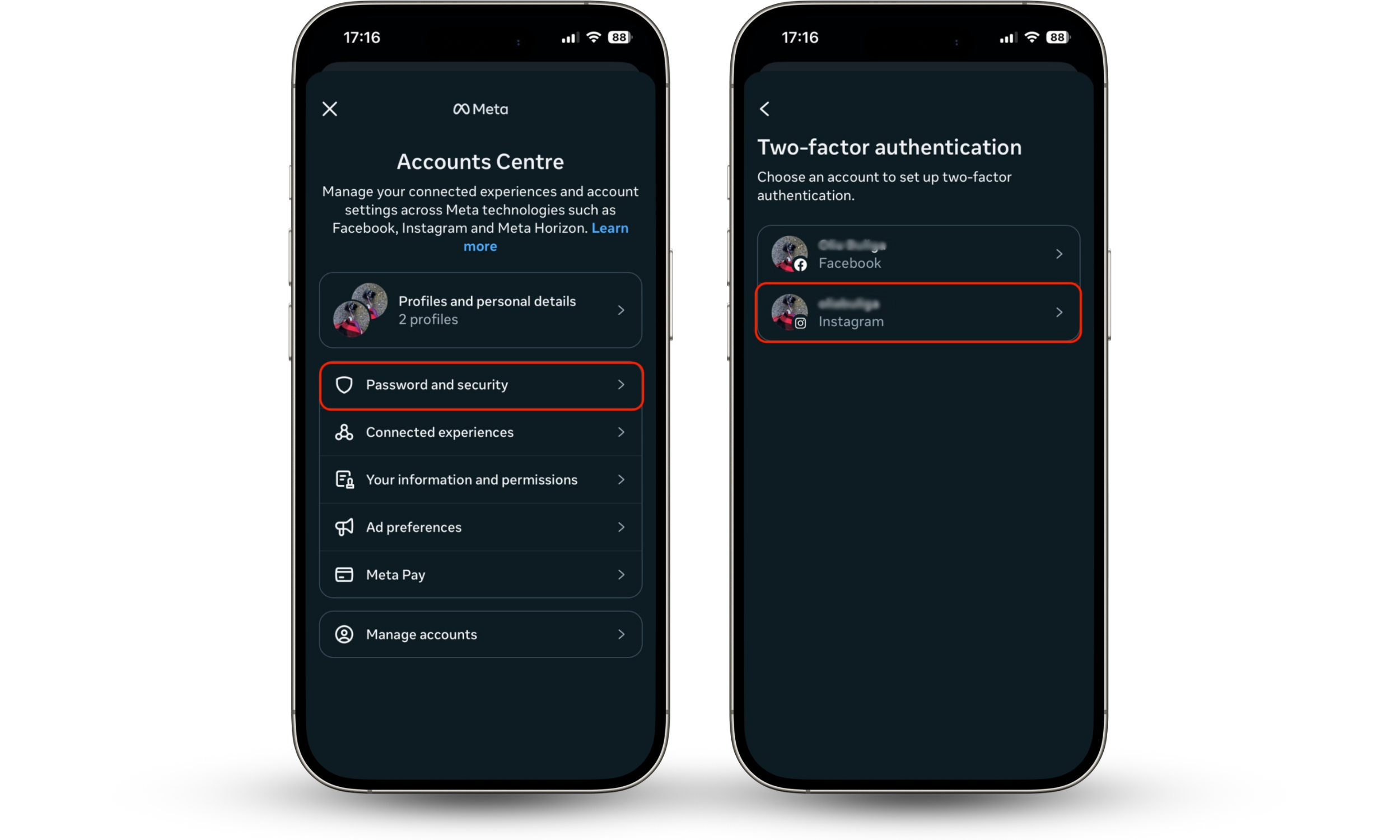
- Select Password and security.
- Select the Instagram profile.
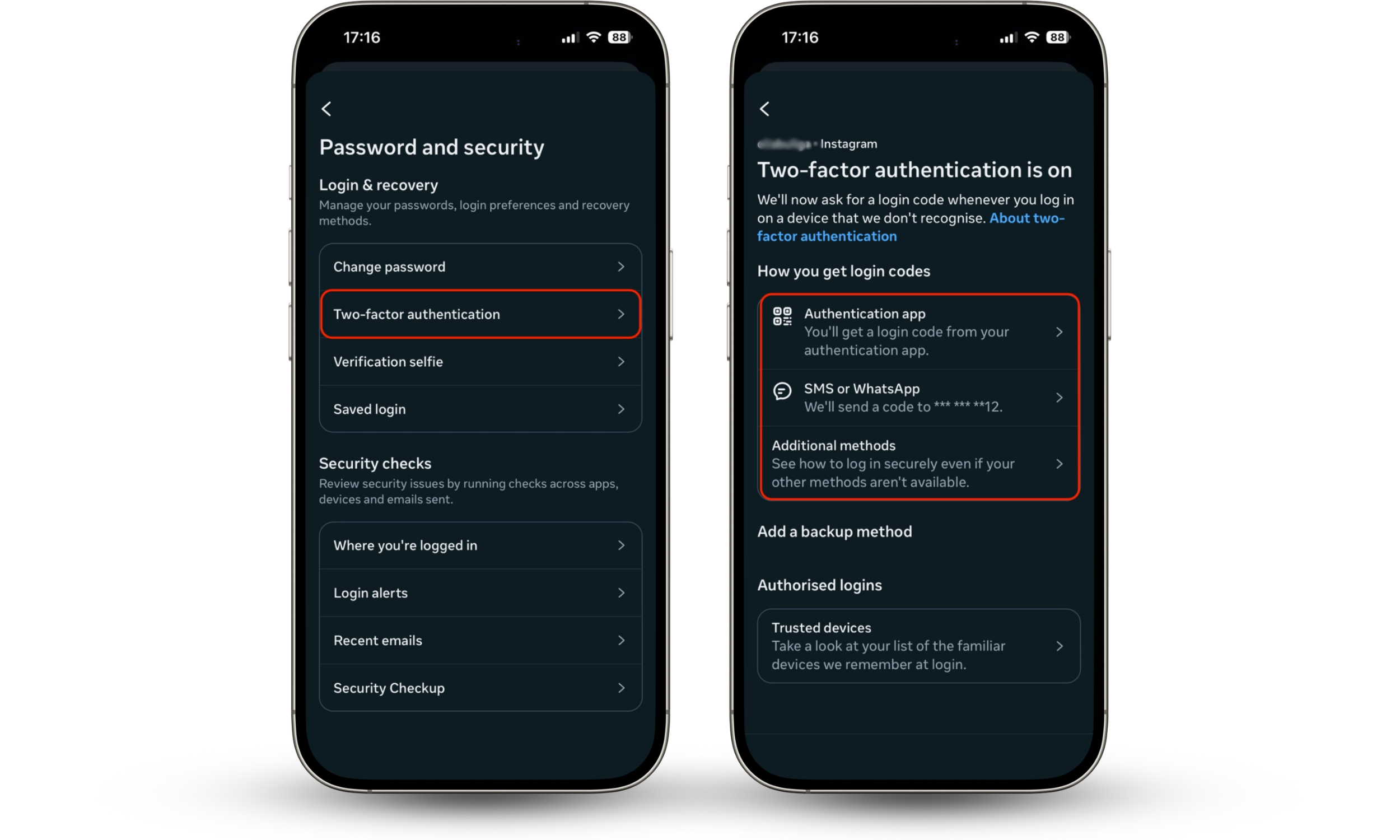
- Then go to Two-factor authentication.
- Choose the type of 2FA: authentication app or SMS.
How to setup 2FA for Apple ID
To enable two-factor authentication for your Apple ID, open your device’s account security settings and activate the 2FA option. Once enabled, Apple will require both your password and a verification code sent to a trusted device or phone number when signing in on a new device or browser.
Here’s how to set up 2FA for your Apple ID:
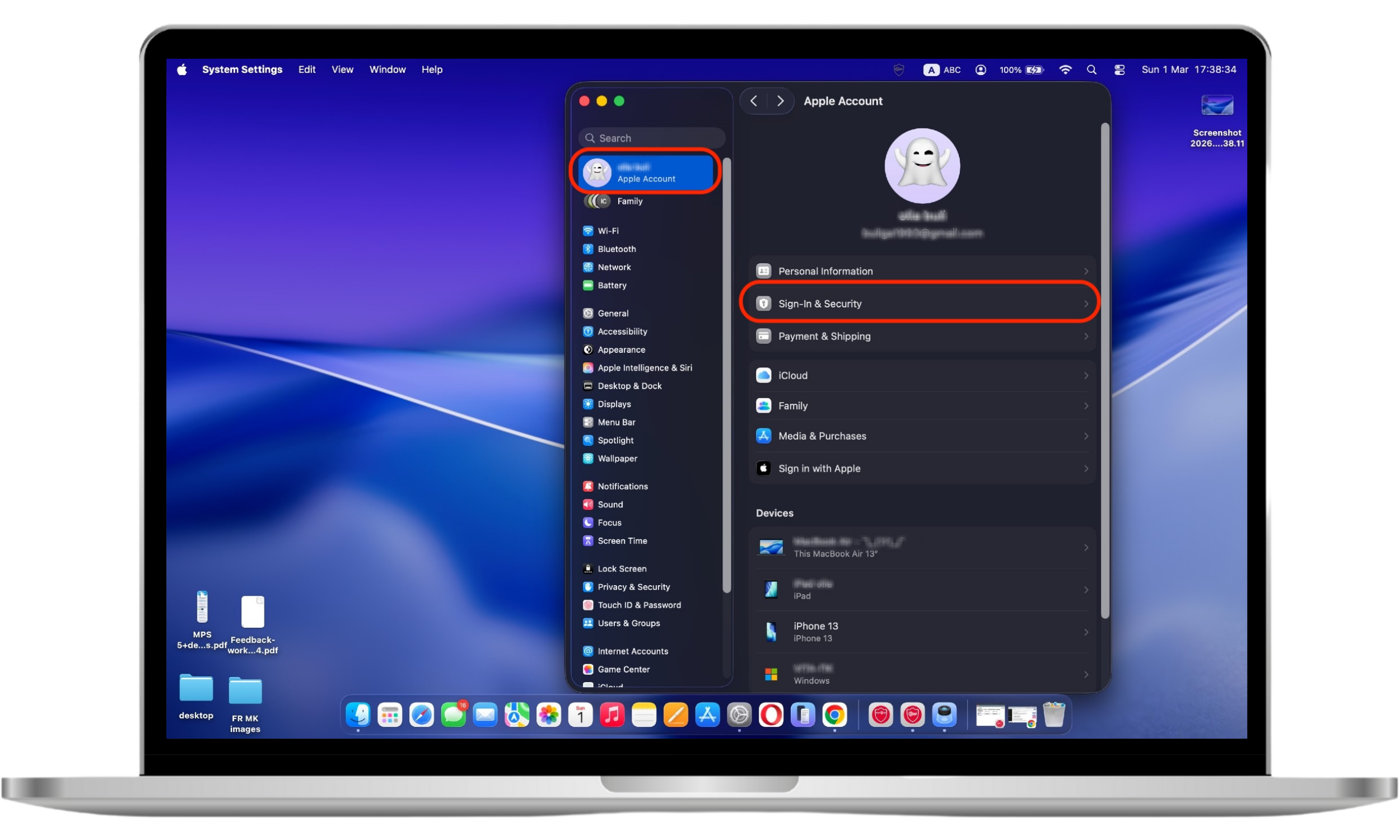
- In the Apple menu, click System Settings.
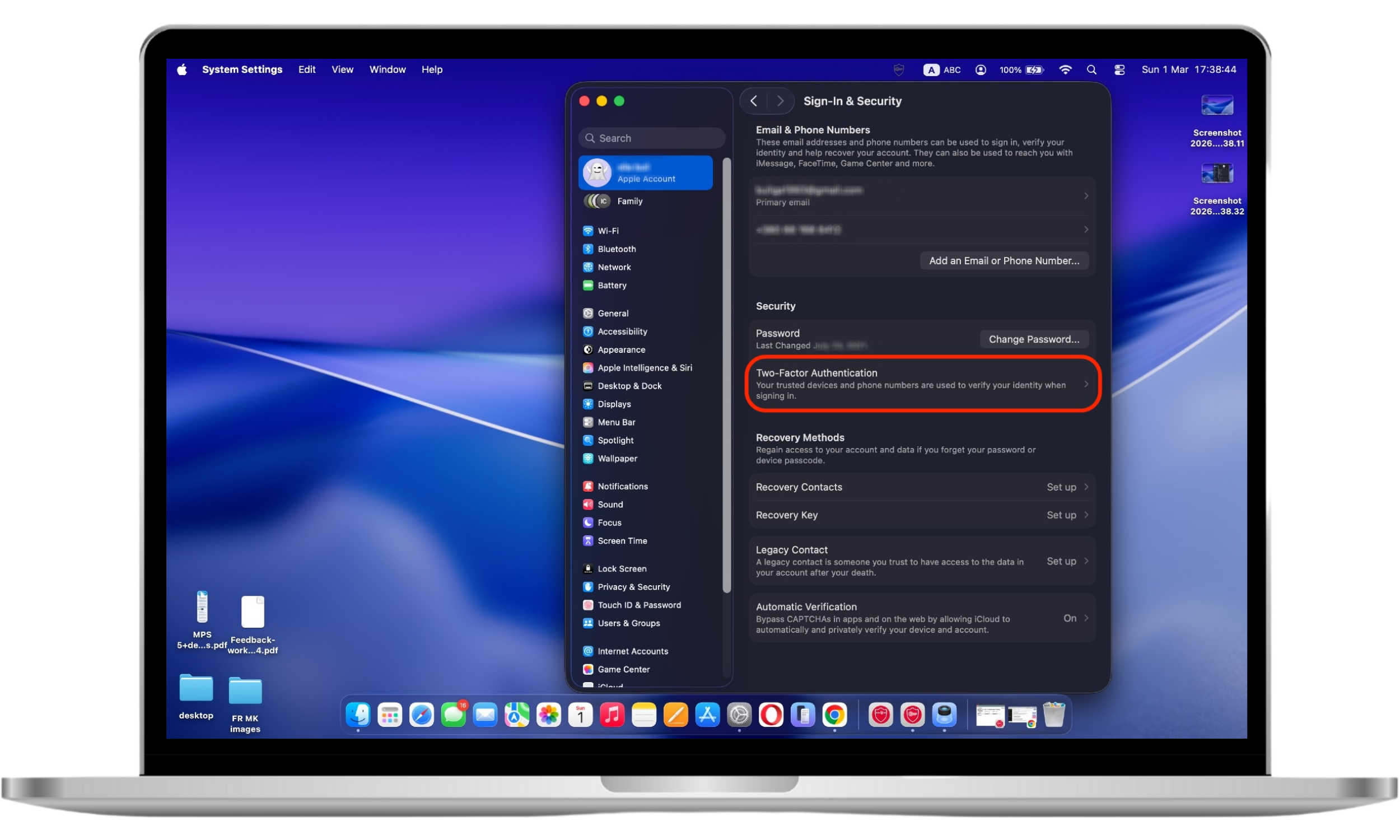
- In the Apple ID section, click Sign-in & security.
- Select Two-Factor Authentication.
- Add a trusted phone number or security keys.
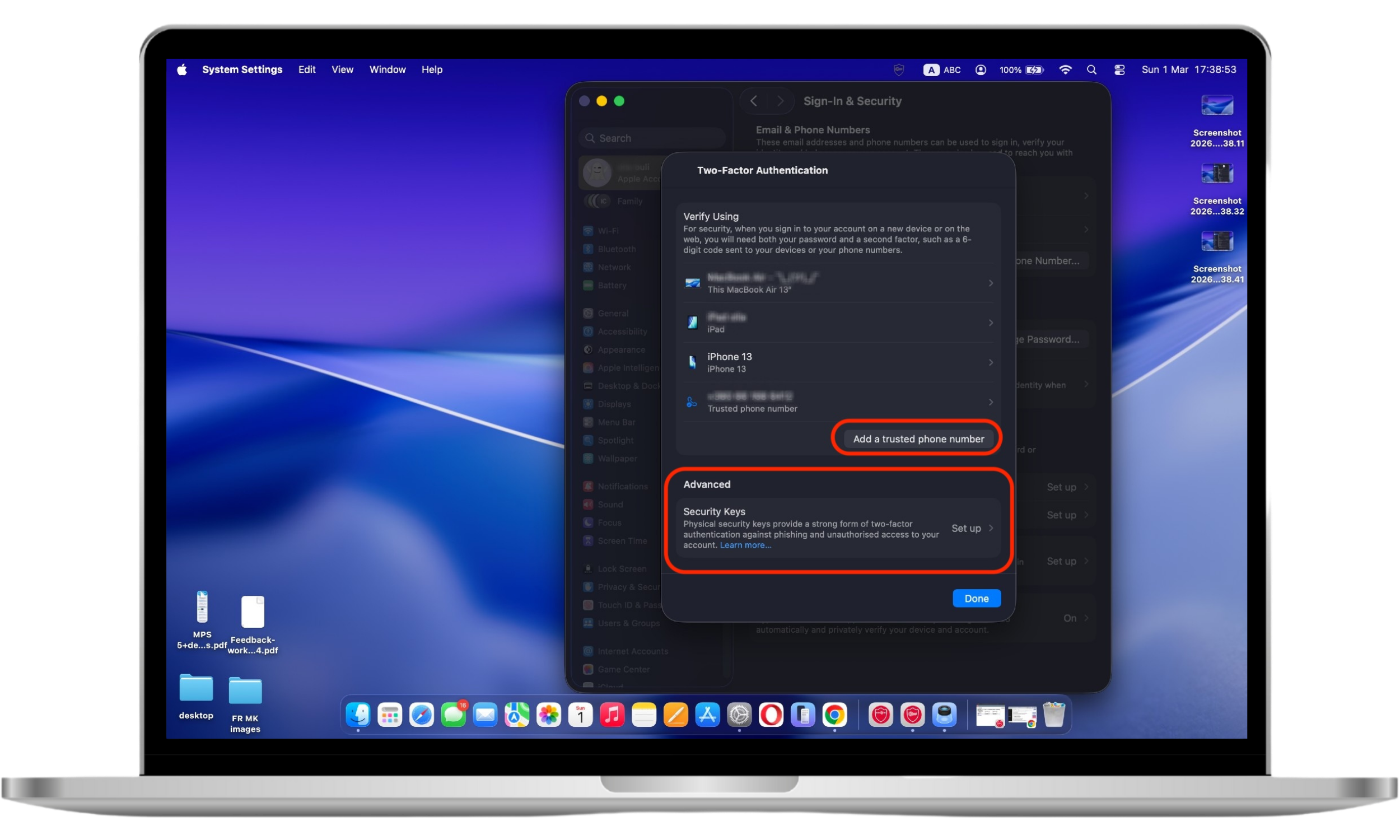
Now, to log in to your Apple ID account you need a password and code.
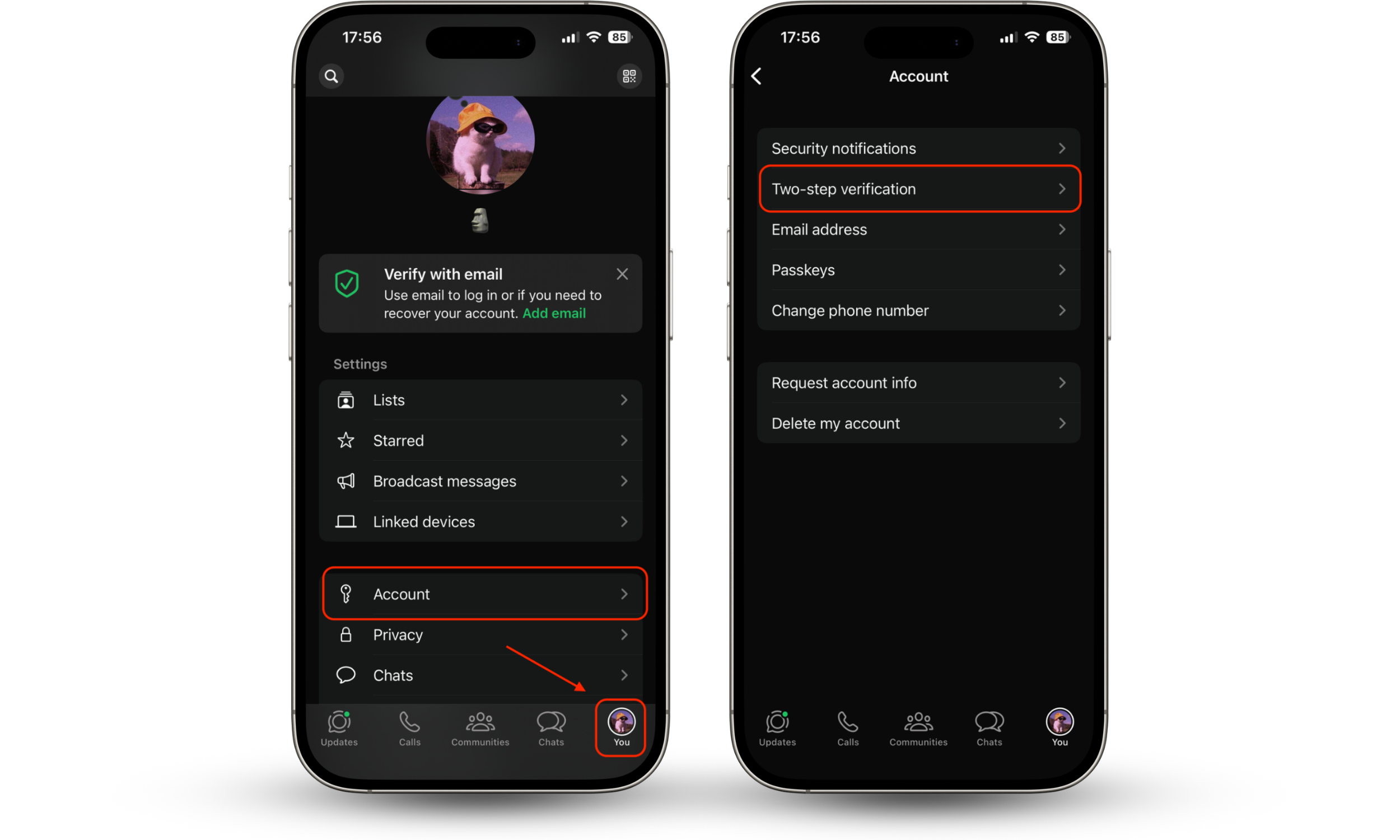
How to set up 2FA for WhatsApp
To enable two-step verification on WhatsApp, you need to activate it in the app’s account settings and create a six-digit PIN. Once enabled, WhatsApp will require this PIN periodically and when registering your phone number on a new device, adding an extra layer of protection against SIM swapping and unauthorized account access.
Here’s how to set up 2FA for your WhatsApp:
- Open WhatsApp and tap on your profile picture at the bottom.
- Tap Account.
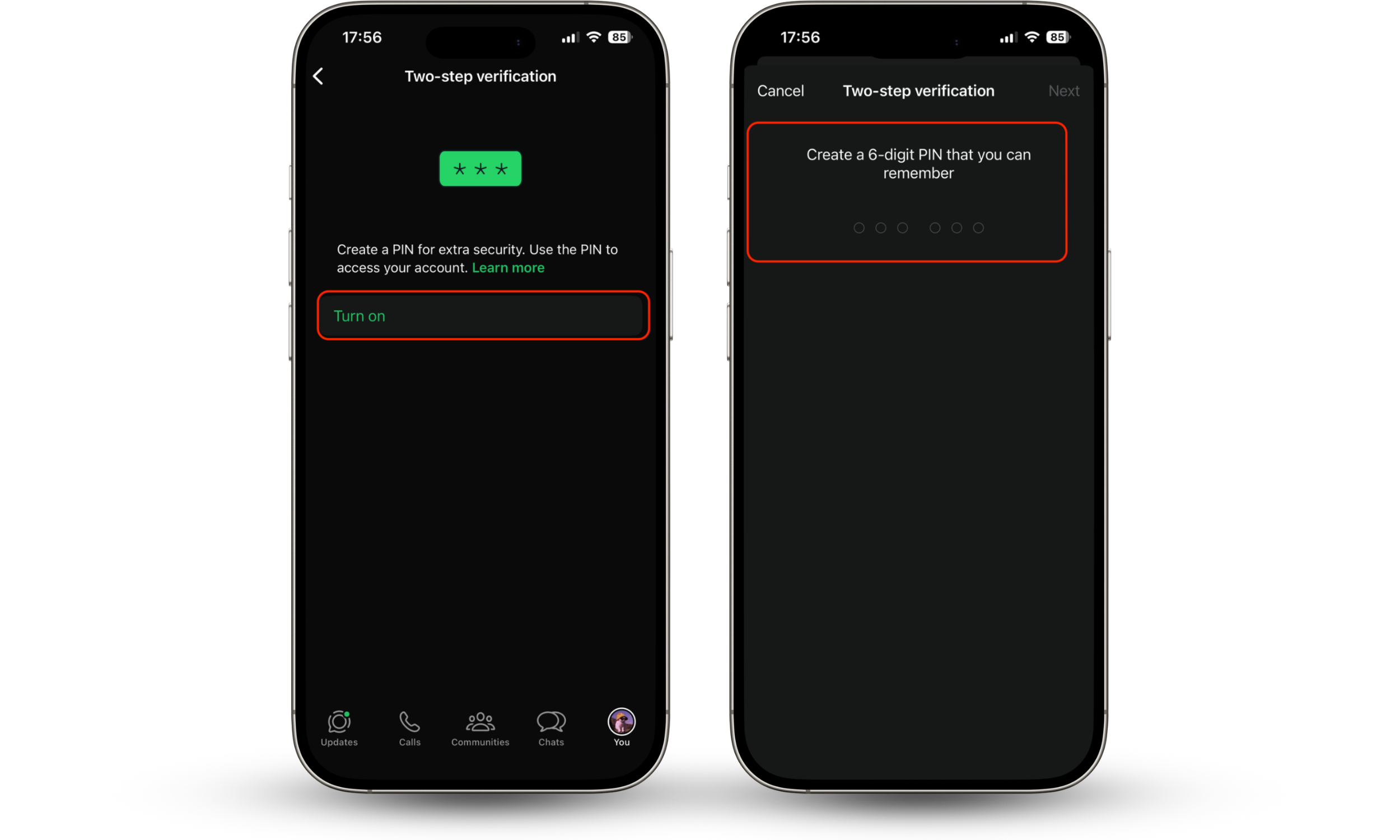
- Select Two-step verification.
- Tap Turn on.
- Create and confirm your six-digit PIN.
- Add and confirm a recovery email address.
How to use 2FA to prevent a security breach
2FA can substantially reduce the likelihood of a security breach. Why? Well, while it’s possible to guess or steal your password, it’s much harder to obtain your phone and use it for authentication.
To avoid a security breach make sure to protect the following types of accounts with 2FA:
- A password manager
- Social media profiles
- Bank accounts
Start with protecting your email account as this is the entrance to the fortress of your digital security. And unfortunately, both personal and business email accounts are regularly attacked by cybercriminals.
If cybercriminals get access to your email, they can access all the other accounts linked to it. To break into these accounts, cybercriminals can simply click the Forgot Your Password button and follow the Reset password link provided via email.
What are the most popular 2FA methods?
Most 2FA methods pair a password with a second step that proves you control a trusted device or authenticator. Common options include SMS one-time codes, authenticator apps that generate time-based codes (often called TOTP), and push prompts where you approve a sign-in on another device. “Passwordless” sign-in also exists and typically replaces the password with a device-based approval method rather than removing security checks.
The most popular 2FA method is the combination of a password and the second factor - your phone or a one-time password (OTP) that is valid for up to 60 seconds.
Passwordless authentication is also becoming increasingly popular. To access an account, you just have to enter your login on one device, then click a push notification on another one.
What are the least secure 2FA methods?
Some 2FA methods are easier to intercept or trick users into approving. SMS codes are vulnerable to SIM swapping (when an attacker convinces a carrier to move your number to their SIM) and can be exposed through malware or message interception. Because SMS relies on the phone number routing system, it is generally considered weaker than app-based codes or hardware-backed methods.
SMS verification is the least secure 2FA method because it’s extremely easy to intercept text messages. Hacking tools capable of intercepting messages cost just a few hundred dollars. In addition, texts can be read via malicious applications, which can be installed on your phone.
Expert note
SMS 2FA is still usually better than using only a password, but it’s not ideal for high-value accounts. If your service supports an authenticator app or security key, switching reduces exposure to SIM swapping and message interception.
What are the most secure 2FA methods?
Security keys are the most reliable means of 2FA. The keys, inserted in a USB port, connect with your phone or computer through Bluetooth and generate a special random key combination. To date, this type of authentication is deemed the most secure.
How to log in to an account after losing a phone?
Phone loss is a common 2FA failure point, so recovery planning matters. Most services offer one or more fallback options: printable backup codes, a second trusted device, a backup phone number, or a formal account recovery flow. The safest approach is to set up at least two recovery methods in advance so you can regain access without disabling 2FA.
It depends on the service, and that’s when things can get complicated. For instance, Google Authenticator doesn't sync between multiple devices. So, if you lose your phone, you have to somehow restore all your passwords and associate them with your accounts all over again.
Google and Facebook give you lists of 10-12 backup codes you can print out and keep in a safe place. After losing a phone, you can verify your identity using a backup code.
In the same way, Google and Apple allow you to register a backup phone. Make sure to submit a phone number of a trusted person to have an alternative authentication method
Stay Ahead of Account Compromise
Even with 2FA enabled, leaked credentials can still circulate online without your knowledge. Clario Anti Spy’s Data Breach Monitor scans your email for exposed accounts and alerts you if your data appears in a breach. Continuous monitoring helps you quickly reset affected passwords and secure accounts before attackers can misuse them.


