Table of contents
- What is cyber espionage?
- Tactics and techniques used in cyber espionage
- Who are the targets of cyber espionage?
- How to detect signs of cyber espionage
- How to protect yourself against cyber espionage
- Conclusion
What is cyber espionage?
Cyber espionage means a cybercrime in which hackers obtain sensitive information from digital devices, such as computers, phones, and network servers. These attacks, often carried out by state-sponsored individuals or organized groups, usually target key people, corporations, or government agencies and can pose a significant threat to national security, economic stability, and individual privacy.
If you asked me what cybercrime is, I usually think of common cyberattacks involving computer viruses and ransomware that bad actors use for financial gain. However, unlike these threats, which typically target individuals or organizations en masse, cyber espionage focuses specifically on those who possess state secrets, military plans, trade secrets, and other confidential material.
Modern cyber espionage started in the 1990s, with some of the earliest operations being China’s “Moonlight Maze” infiltration of US government and defense systems from 1996 to 1999. Another early cyber espionage example is “Titan Rain,” a second Chinese attack on US systems in the early 2000s.
In the Moonlight Maze attacks, hackers used a combination of custom scripts, toolkits, and hacked servers to monitor and extract valuable data. By the time the Titan Rain attacks were executed, more modern methods of infiltration, including phishing, vulnerability exploits, and keyloggers, had been deployed.
Tactics and techniques used in cyber espionage
Those carrying out cyber espionage rely on Advanced Persistent Threats (APTs) to remotely access secure systems. APTs can include various tactics and techniques, such as custom malware and spyware, zero-day software exploits, phishing attacks, and social engineering on key individuals.
Let’s take a closer look at common tactics that go into an APT to understand them better:
- Custom malware and spyware: APTs rely on sophisticated malware and spyware that are unknown to antivirus programs and aim to avoid detection for long periods of time. Once running on a target device, these tools gather information, monitor users, and gain access to secure networks.
- Zero-day software exploits: Zero-day vulnerabilities are flaws in software, such as an operating system or app, that its developer is unaware of. By exploiting these vulnerabilities using tailored attacks, cyber spies can breach the software and gain access to a computer system.
- Phishing attacks: One of the most common tricks cybercriminals use today is phishing, which involves impersonating trusted organizations or recognizable people, such as Apple and Microsoft, to obtain sensitive information. Cyber espionage also uses these tactics to fool targets into providing sensitive credentials.
- Social engineering: Somewhat similar to phishing, social engineering is a more in-depth technique. Rather than hoping to trick victims with a random email that looks like it came from a reputable company, social engineering instead calls on more sophisticated manipulation tactics. For example, hackers may establish trust with a victim over time, perhaps by befriending them, and then gradually convince them to disclose valuable info.
If you’ve ever wondered how the government spies on us, it probably won’t surprise you to learn that many law enforcement and federal agencies employ similar methods to gain access to suspect devices. That’s why we always advise readers to be aware of these activities and protect against them.
Who are the targets of cyber espionage?
The primary targets of cyber espionage are normally high-profile individuals and organizations that possess valuable material. This includes any information that might give one entity—such as a government, a corporation, or a research institution—a competitive or strategic advantage over others.
For example, some nations use cyber espionage against others to learn military capabilities and tactical plans. A corporation might use similar tricks against a major rival to steal intellectual property and trade secrets. Academic and research institutions are targets as they possess valuable insights across a wide range of fields that could provide a competitive advantage.
Of course, it’s not just large organizations and governments that have to protect against cyber espionage. We’ve also heard of celebrities, politicians, and other public figures falling victim to cybercriminals who use espionage to obtain information and material they can sell or trade. When we look into what hacking means, we find that almost anyone with a digital device is a target.
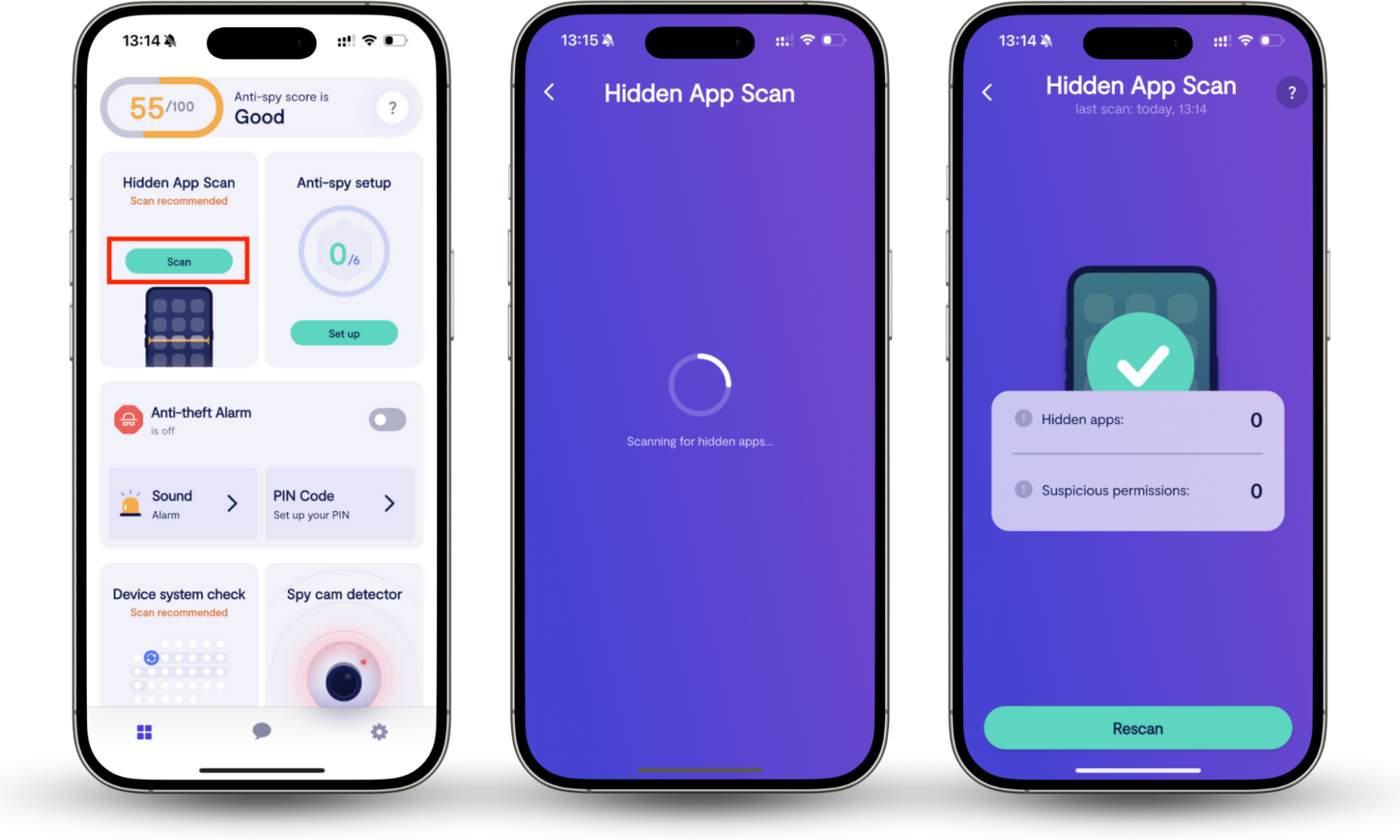
Are you worried cyber attackers could target your devices? When it comes to keeping Android and iOS devices free from spyware, we believe the best solution is Clario Anti Spy. Its hidden app scan identifies apps using suspicious permissions—a telltale sign that they are spying on you. It also helps you find potential surveillance tools that attempt to go unnoticed.
How to use Clario Anti Spy’s Hidden app scan:
- Download Clario Anti Spy.
- Open Anti Spy, then tap the Scan button under Hidden app scan.
- Once the process is complete, you’ll see whether any hidden apps are present on your iPhone. We recommend removing apps you didn’t install yourself.
How to detect signs of cyber espionage
You don’t need to be a government official, a well-known celebrity, or the CEO of a Fortune 500 company to fall victim to cyber espionage, so we believe it’s important to be aware of the signs indicating your system is under surveillance. Here’s what we always look out for:
- Check for unauthorized device access: If any of your devices allow you to view recent login attempts, we recommend checking these frequently for unauthorized access. This includes unsuccessful login attempts where someone has tried to guess your password and successful attempts when you weren’t using the device.
- Monitor for unusual network activity: Most devices allow you to monitor network activity using built-in tools—such as Activity Monitor on Mac—or third-party programs. We advise readers to use these frequently to see not only the volume of data their device sends and receives but also the programs and processes using the network. Large amounts of data being sent from their machine and network access from unrecognized apps are cause for concern.
- Keep an eye on system behavior: You should be mindful of not only unusual network activity. We’ve found that an unexplained drop in system performance, increased battery drain, and frequent increases in device temperature all indicate that something is pushing your device hard. If it’s not a program that you’re using yourself, you’re likely experiencing a spyware infection.
As cyber threats are so common today, we highly recommend that all customers familiarize themselves with how to know if someone is spying on your laptop. Once you’re aware of the symptoms of a security threat, you can more quickly identify them and take the necessary steps to block and remove infections.
How to protect yourself against cyber espionage
Strong security measures are essential for protecting yourself against cyber espionage, whether you’re looking after an entire organization with a fleet of systems or just your personal devices. These are the steps for minimizing the risk of attack:
- Use device security: We recommend that any device containing sensitive data (likely every device you use) also run appropriate security software to protect it. This includes a strong antivirus for Mac and Windows computers, and an app like Clario Anti Spy on Android and iOS.
- Keep software up to date: Update your devices whenever new software releases are available to ensure they have the latest security patches and protections.
- Enable two-factor authentication (2FA): Almost all online accounts offer some form of 2FA these days, and you should enable it wherever it’s available. 2FA ensures that even if someone else obtains an account password, they won’t be able to log in without a unique code.
- Activate network security: It is surprising how many people still don’t use passwords on their Wi-Fi networks. Activate the best protection offered by your router—usually WPA2 or WPA3—to prevent unauthorized access by hackers who can exploit devices on your network.
- Enforce regular security training: If you’re responsible for an organization’s IT, introduce regular cybersecurity training. We’ve found that half of the battle to protect enterprise devices is ensuring that all employees know today’s security risks and how to avoid them.
Conclusion
While cyber espionage is most commonly associated with government agencies, military organizations, and large corporations, the scary truth is that all our devices hold sensitive information that attackers can use to their advantage. While those working for these entities are certainly more valuable targets, everyone should take steps to protect their devices and their data from cybercriminals.
The most effective way to keep your smartphone free from spyware and invasive apps is to use Clario Anti Spy. Its Hidden app scan weeds out all apps that are accessing permissions that likely don’t need and uncovers potential risks that are difficult to find manually.


