Table of contents
- What are SIM cards?
- Can someone hack and use your SIM card?
- 1. SIM cloning
- 2. SIM swapping
- 3. Simjacker
- How to check if your SIM card is hacked
- 1. Calls and text messages are not received
- 2. Strange activity on your accounts
- 3. You lose access to online accounts
- 4. You receive messages asking to reboot the device
- 5. Recent requests for confidential information
- 6. The device appears elsewhere on location trackers
- 7. You’ve recently serviced or mailed your device
- How to protect the SIM card from hacking
- Conclusion
- FAQ
- 1. What do I do if my SIM card is hacked?
- 2. If my phone is hacked should I get a new SIM card?
What are SIM cards?
A Subscriber Identity Module (SIM) card is a small smart card you insert into your phone. You need a SIM card to connect to the cellular network and make calls or send messages.
A SIM card contains information about your subscriber identity, cellular network credentials, and personal contacts. Cellular network providers (like T-Mobile) sell them.
Can someone hack and use your SIM card?
Yes, someone else can steal or use your SIM card. If they can access your SIM card in person, they can easily insert it into their own phone and make calls, send messages, or access your mobile data. If your SIM is stolen, call your provider and deactivate it.
Tip
Since someone can steal your SIM card, you may be wondering, what is more secure, home Wi-Fi or cellular data? Well, the answer is usually cellular data, and public Wi-Fi is the least safe option.
Hackers can also hijack your SIM card remotely using three different methods:
1. SIM cloning
SIM cloning is when a hacker creates a duplicate copy of a SIM card. They can access your mobile data and personal information by transferring the International Mobile Subscriber Identity (IMSI) and Authentication Key (Ki) from your SIM card to a blank card.
SIM cloning is illegal because it involves gaining unauthorized access to someone’s personal information and communication. It can also lead to identity theft. But even though it’s illegal and providers have security measures to prevent it, SIM cloning can still occur. If you notice strange behavior on your phone, it’s important to check if your SIM is cloned.
2. SIM swapping
SIM swapping, also known as SIM hijacking, is a trick cybercriminals use to transfer your mobile number to a SIM card they control. After they’ve swapped out your SIM card, they can access your calls and messages and potentially take over online accounts linked to your phone number.
Cybercriminals often carry out SIM swapping by tricking a customer support representative at your cell carrier. Using social engineering tactics, they pretend to be you and claim to have a new SIM card to which they want to transfer your data.
3. Simjacker
Simjacker is a sophisticated exploit that lets skilled hackers remotely control your SIM card. The exploit targets a technology called S&T Browser, which mobile network operators use to provide services to their subscribers.
The hacker will send specialized SMS messages to your device. These messages make your SIM card perform malicious activities, like tracking your location or sending fake messages. Here’s how to stop someone from accessing your phone remotely.
How to check if your SIM card is hacked
Here are 7 ways to check if someone is using your SIM card:
- Calls and text messages are not received
- Strange activity on your accounts
- You lose access to online accounts
- You receive messages asking to reboot the device
- Recent requests for confidential information
- The device appears elsewhere on location trackers
- You’ve recently serviced or mailed your device
1. Calls and text messages are not received
If you suddenly cannot receive calls and text messages, your SIM card may have been hacked. If someone has swapped or cloned your SIM card, they may be receiving your calls and SMS messages instead of you.
Hacking your SIM card can also prevent you from sending texts or making calls. Double-check whether you’re still able to send and receive calls. If not, call your service provider to report the issue and secure your account.
2. Strange activity on your accounts
You can tell if a SIM card is cloned if there’s strange or unauthorized activity on your online accounts. Weird activity on your accounts is one of the signs of a cloned SIM card. Here’s why:
- Your phone number is linked to your accounts: Many online accounts, including social media and banking accounts, link to your phone number. If hackers can access your number, they can request password rests and block you from accessing your accounts.
- Two-factor authentication (2FA): When you use 2FA, you receive a verification code when you sign into your accounts. If someone has stolen your SIM card, they can intercept the code and gain access to your accounts.
If this happens, contact your network operator to cancel your SIM and request a new one. Then, change all of your online passwords to unique, strong phrases. Finally, change your 2FA settings to send an email rather than text so the hacker is locked out for good.
3. You lose access to online accounts
If you lose access to your account, a hacker may have used your phone number to lock you out. This happens in the same way as we explained above—with your phone number, the hacker can easily sign into your account, request a password change, and then prevent you from regaining access.
4. You receive messages asking to reboot the device
Even if a hacker has successfully cloned or swapped your SIM card, they won’t be able to activate it until your SIM card goes offline. That’s why messages asking to switch off your device are one of the signs of hacked SIM cards.
To complete this last step, the hacker will send a text message to your number asking you to reboot the device. They’ll impersonate your phone service provider to try to convince you to follow their instructions. Once the device turns off, they can activate their SIM card and take control of your phone number.
If you receive a message asking you to reboot your device, do NOT turn it off. Call your network operator to report the issue and seek guidance on what to do next.
5. Recent requests for confidential information
Requests for confidential information are known as phishing attempts. This is where a scammer will try to trick you into handing over passwords, verification codes, or personal information to steal your identity or hijack your accounts.
If you’ve recently received a request like this and handed over personal information, your SIM may have been hacked. The scammer may have called your mobile network operator and impersonated you, asking them to send out a new card in your name.
A good way to find out if you’ve installed malicious software because of a phishing attack is by using an anti-spyware solution like Clario Anti Spy.
6. The device appears elsewhere on location trackers
Some cell network providers can triangulate the location of SIM cards on their networks. But this also means you can find out if your SIM card has been hacked. If you call your provider and ask them to track your SIM card, and they tell you the SIM’s location is elsewhere than where you are, it means someone has cloned your SIM.
If you were also wondering whether someone could find your address from your phone number, it is possible. That’s why it’s important to keep your phone number as private as possible and your SIM card secure.
Note
Hackers aren't the only ones who can track your phone. If you’ve ever questioned, can the FBI track your phone? The answer is yes. Advertisers, the government, and even law enforcement agencies like the FBI can track your phone using various techniques.
7. You’ve recently serviced or mailed your device
The easiest way for someone to hijack your SIM card is by physically tampering with your device. If you’ve recently mailed your phone somewhere, it may have been intercepted and cloned.
Likewise, if you’ve had it serviced, there’s a chance that someone untrustworthy gained access to your phone and cloned your SIM card.
How to protect the SIM card from hacking
Here are a few tricks to protect your SIM card from scammers and hackers:
- Never tell anyone your passwords, login details, or personal information
- Don’t open or reply to unsolicited messages, calls, or emails
- Don’t click on suspicious links—they often contain malware
- Avoid linking your phone number to your online accounts
- Keep an eye on your phone while you’re out and about
- Lock your SIM card—you can do this in your Android or iPhone settings
- Use a two-factor or multi-factor authentication (MFA) app
- Consider using a cybersecurity solution like Clario Anti Spy
Clario Anti Spy can monitor the web for your personal information and ensure your operating system is secure and up-to-date. It can also run regular deep scans to uncover and remove any spyware lurking on your device, protecting it from hacking at all times.
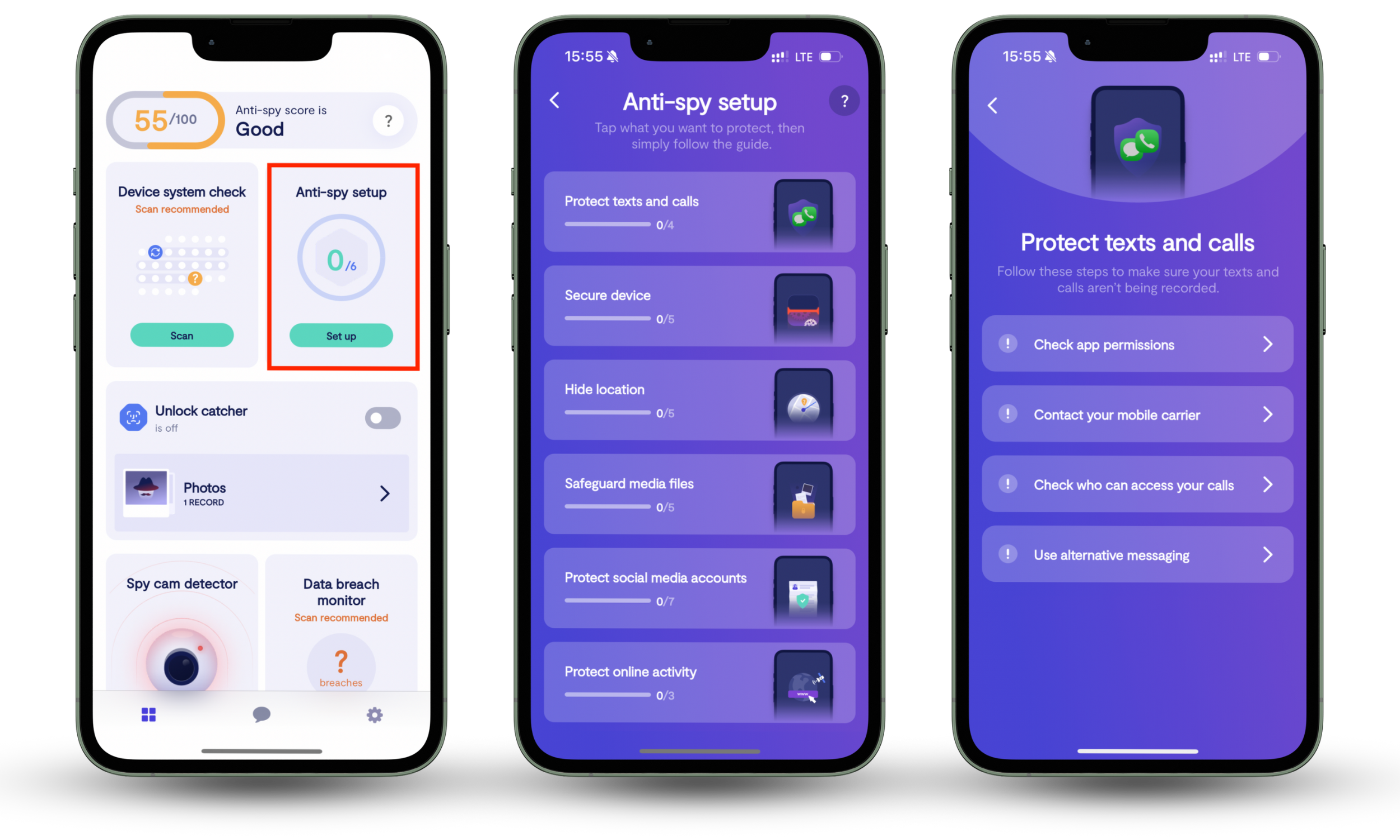
Here’s how to use Clario Anti Spy’s Anti-spy setup:
- Download Clario Anti Spy and create an account.
- On the home screen, look for Anti-spy setup. Press Set up when you find it.
- You’ll now see a list of actions you can take to make your device less vulnerable. Go through each action step-by-step until you’ve completed the process and secured your phone.
Conclusion
It’s important to regularly check if someone is using your SIM card to prevent unauthorized access to your personal information and data. One effective way to secure your mobile devices is to use Clario Anti Spy, a powerful tool designed to detect and remove spyware from your devices. Take control of your privacy by downloading Clario Anti Spy and safeguarding your personal data from prying eyes.
FAQ
1. What do I do if my SIM card is hacked?
If you know your SIM card is hacked, there are several steps you need to take immediately:
- Contact your mobile service provider to report the hack and secure your SIM
- Change your passwords to secure, unique phrases
- Enable two-factor authentication with a new number or email address
- Monitor your accounts
2. If my phone is hacked should I get a new SIM card?
It depends. If you think the hacker cloned your SIM card as part of the attack, then you should get a new SIM card. We recommend calling your mobile service provider to ask for guidance on what steps to take. They may recommend swapping out your SIM card as a precautionary way to stop the hacker from accessing it.


