Table of contents
- How phone cloning works
- 1. Cloning using cloud backups
- 2. SIM card cloning
- 3. Cloning using local backups
- 4. Spyware
- 5. Viewing synced cloud data
- 6. SIM swapping
- How to unclone your phone
- 1. Scan phone for spyware
- 2. Update your passwords
- 3. Use two-factor authentication
- 4. Secure cloud accounts
- 5. Contact your mobile carrier
- How to prevent phone cloning
- Conclusion
How phone cloning works
Phone cloning happens in a few different ways. To unclone a phone, you’ll need to know which method was used. Someone might make a copy of your phone using cloud or local backups. They might clone your SIM card or run a SIM swapping scam. Alternatively, they could clone your phone using spyware.
When we talk about cloning a phone, we don’t usually mean that someone has created a complete copy of your device. Instead, it means that a hacker has gained access to some of your data—or that they can use your phone number.
Exactly what they can see depends on the method of cloning. Once you know how someone has cloned your device, you can take steps to reverse phone cloning and take back control.
1. Cloning using cloud backups
Using cloud backups is one of the easiest ways for cloners to copy your phone. If you have backups enabled, your phone regularly saves data to the cloud. If someone accesses your iCloud or Google account, they can restore an old backup to their own device.
When someone clones your phone using a cloud backup, they’ll have a copy of your data from the day of the backup. This might include photos and videos, text messages and iMessages, call history, location history, saved passwords, and browsing data. It’s potentially enough information to make purchases, commit identity theft, or even blackmail you over private images and videos.
The hacker won’t have access to newer information, unless your phone continues to automatically save data to the cloud. They also won’t have access to your phone number or SIM card, so they can’t intercept your calls or texts, or make calls or texts posing as you.
You’re at risk from cloning using cloud backups if:
- You reuse passwords between accounts
- You’ve been the victim of a password leak
- You don’t have two-factor authentication (2FA) set up
You might notice someone has cloned your phone using a cloud backup if you’ve received an unexpected login notification from iCloud, for a cloned iPhone, or your Google Account. Alternatively, you might notice unknown purchases if someone has accessed your bank details, or even receive messages from the hacker threatening to blackmail you.
2. SIM card cloning
SIM card cloning is rare nowadays. It was more common in the past, but cell providers have improved their security systems.
In a SIM card cloning scam, a hacker creates a physical copy of your SIM card. This deactivates your original SIM, and the new SIM can be used to make and receive calls and texts.
Signs of SIM card cloning include:
- Complete loss of cell service
- No incoming calls or texts
- No ability to make calls or send texts
- Unexpected charges on your bill
If someone clones your SIM card, they can’t see your photos, apps, emails, or anything else stored on your device. They can only access incoming calls and texts, including 2FA texts, and make calls and texts posing as you. Learn more about how to check SIM cloning and find out if you’re a victim.
3. Cloning using local backups
If you back up your phone to a computer or external storage device, someone could access it. With a spare phone, hackers can download the backup and have a cloned copy of your data.
Like cloning from a cloud backup, this creates a copy of your phone from the day it was backed up. The cloned phone might contain images, videos, messages, and emails, but it won’t have real-time access to your calls and messages, and the hacker can’t call or text someone pretending to be you.
This method requires someone to have access to your physical backup. You’re most at risk if someone else is regularly unattended around your computer or external hard drive.
4. Spyware
Spyware can let a hacker monitor or mirror your phone in real time. They might have access to your calls, messages, emails, apps, and browsing history. However, they can’t make calls or send texts posing as you.
If someone is spying on your phone in real time, they could see your passwords, financial information, and even private images and conversations. You might be at risk of identity theft or blackmail.
Signs of spyware on your phone might include:
- Fast battery drain
- Unexpected freezing or slow performance
- High temperature
- Unknown apps
- Your camera or microphone being unexpectedly activated
Someone with physical access to your phone might install spyware—perhaps an abusive partner or controlling parent. It could also have been installed remotely.
5. Viewing synced cloud data
We’ve already explained that someone can download a backup of your phone’s data onto another device. However, hackers don’t need to clone your phone—they can simply view your data online. Your pictures, call history, and messages might all be easily available to them.
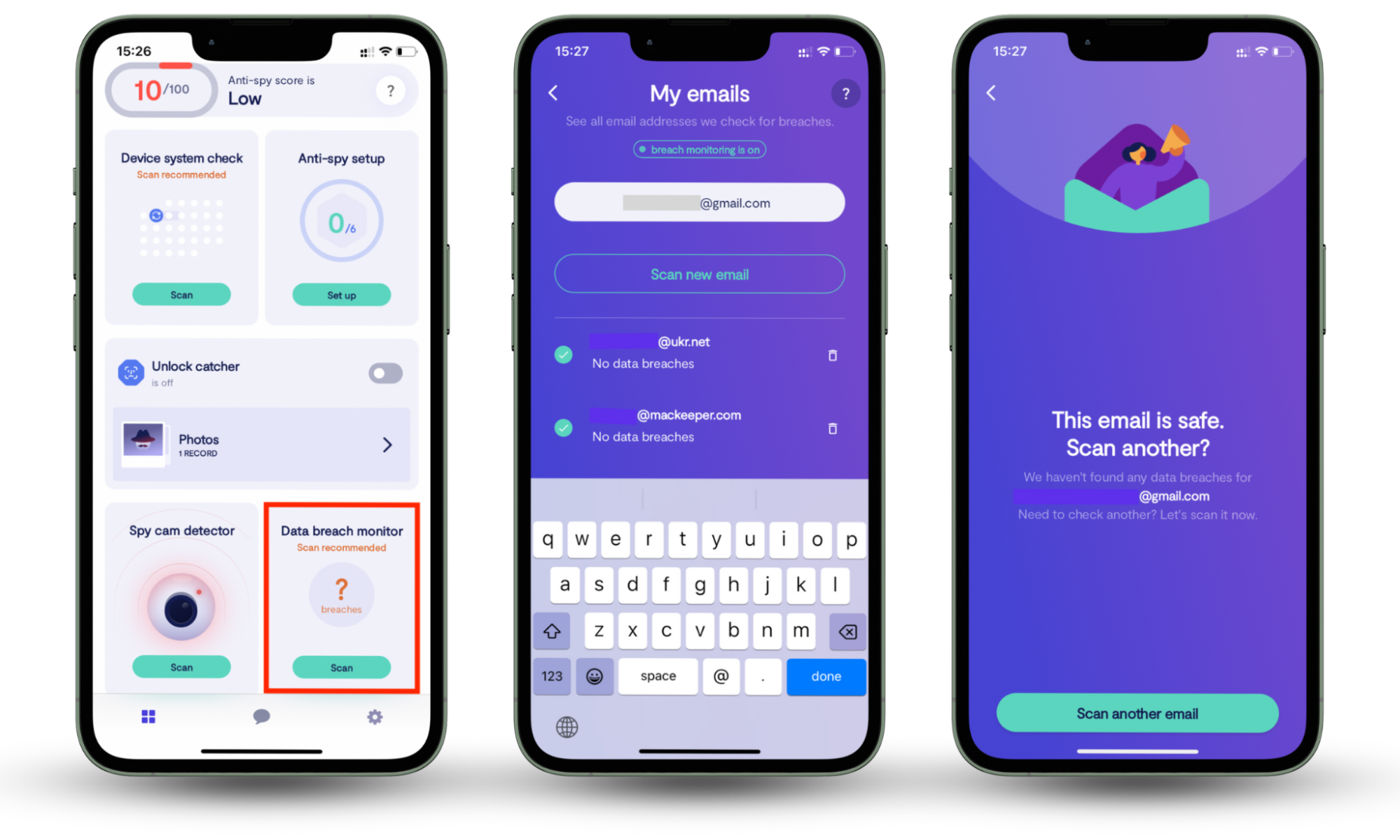
If you reuse passwords, you’re at risk of someone accessing your online accounts. If your details have been compromised in a data breach, anyone could have your password. Fortunately, Clario Anti Spy’s Data breach monitor can scan databases of known password leaks for your details, so you can change the affected passwords and stay safe.
How to check for data breaches:
- Download Clario Anti Spy and set up a subscription.
- Under Data breach monitor, tap Scan.
- Enter your email address and follow the on-screen instructions to find out whether your details have been compromised.
6. SIM swapping
SIM swapping can look like SIM cloning—but the hacker doesn’t make a physical copy of your SIM card. Instead, they contact your cell provider, impersonating you, and request another copy of your SIM.
They need some of your personal information to do this. You’re most at risk from SIM swapping if you’ve shared private details online or recently been a victim of a phishing scam.
With SIM swapping, as with SIM cloning, your phone can be cloned without you knowing. However, you might notice that your phone has no cell reception and you can’t make or receive calls.
How to unclone your phone
To unclone a phone, start by scanning your device for spyware and other suspicious apps. Update your passwords and enable two-factor authentication (2FA) where possible. If you use cloud services, check your security there too. Most importantly, contact your mobile provider for assistance.
The methods you take to protect yourself will depend on how your phone was cloned. For example, if someone has installed spyware on your device, you’ll need to remove it yourself. However, if you’re the victim of a SIM swapping scam, you should contact your cell carrier immediately, because they’ll need to deactivate the cloned SIM card.
How do you know if your phone is cloned? You might not be sure whether you need to stop phone cloning or if there’s another problem with your device. If your phone is cloned, you might notice that you’re no longer receiving calls or messages, you’ve got unexpected charges on your bill, or you don’t have cell reception.
Seeing any of those problems? Let’s talk about how to reverse phone cloning.
1. Scan phone for spyware
If you suspect spyware on your device, act fast. Someone with real time access to your phone could be accessing your private information right now.
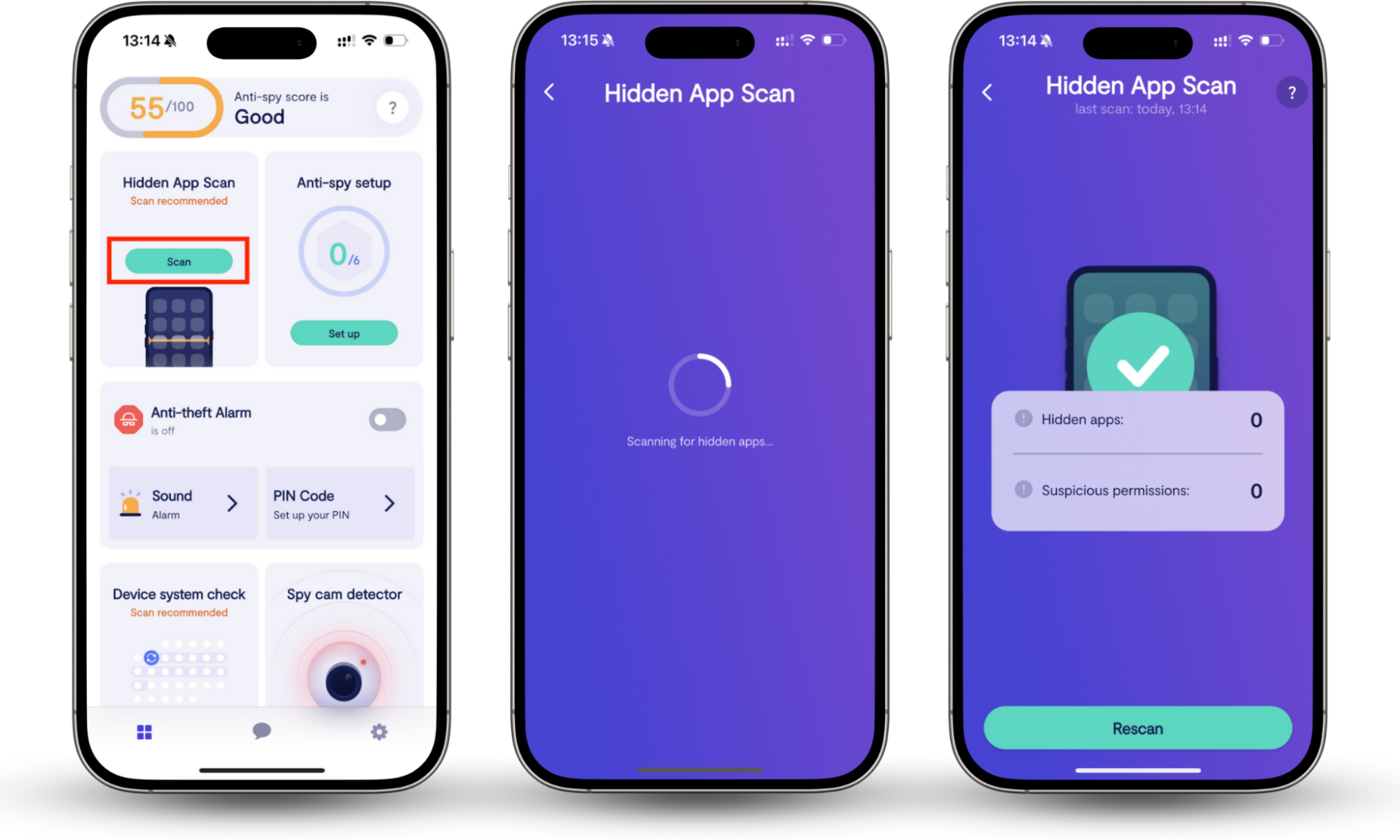
Clario Anti Spy’s Hidden app scan can check for suspicious apps with just a few taps. It can help you find hidden software running in the background and apps with suspicious permissions—maybe software that looks innocent is regularly accessing your camera, messages, or location data.
Recently, a customer contacted the Clario team about an app they didn’t remember downloading. The Hidden app scan discovered that this unknown app had access to the customer’s gallery, contacts, and even their location! It seemed suspicious, so Lila, one of the Clario experts, advised the customer to uninstall it immediately and then change any vital online passwords and privacy settings, just in case.
How to check for suspicious apps on your phone:
- Download Clario Anti Spy and sign up for a subscription.
- Under Hidden App Scan, tap Scan.
- When the scan is complete, review the list of hidden apps and suspicious permissions.
2. Update your passwords
Reusing passwords puts you at risk. To stop phone cloning, change your important passwords and use a unique password for each account.
Expert tip
If you suspect someone is monitoring your phone with spyware, use another device to change your passwords.
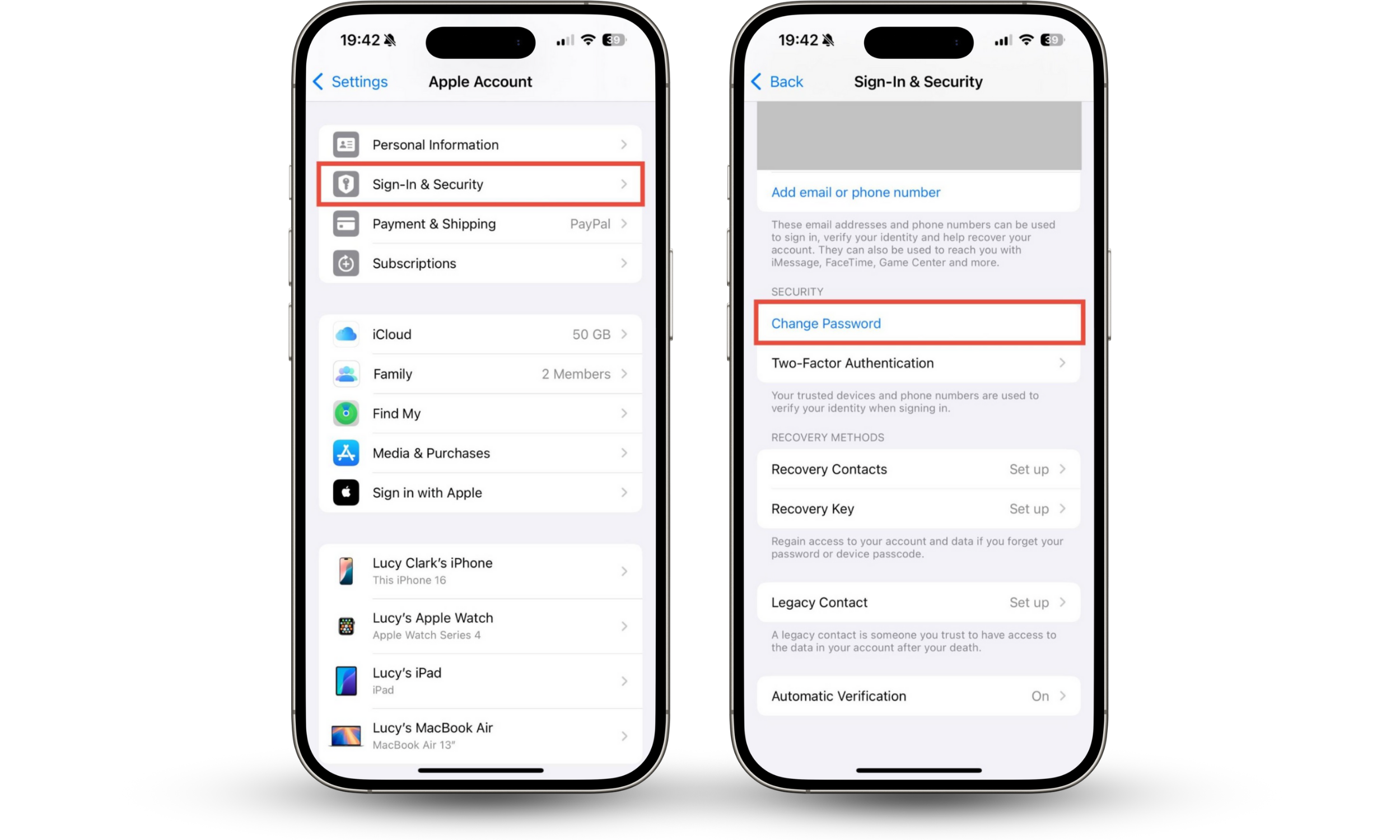
How to change your iCloud password:
- Using your iPhone or iPad, go to Settings > Apple Account > Sign-In & Security.
- Tap Change Password and follow the on-screen instructions to change your password.
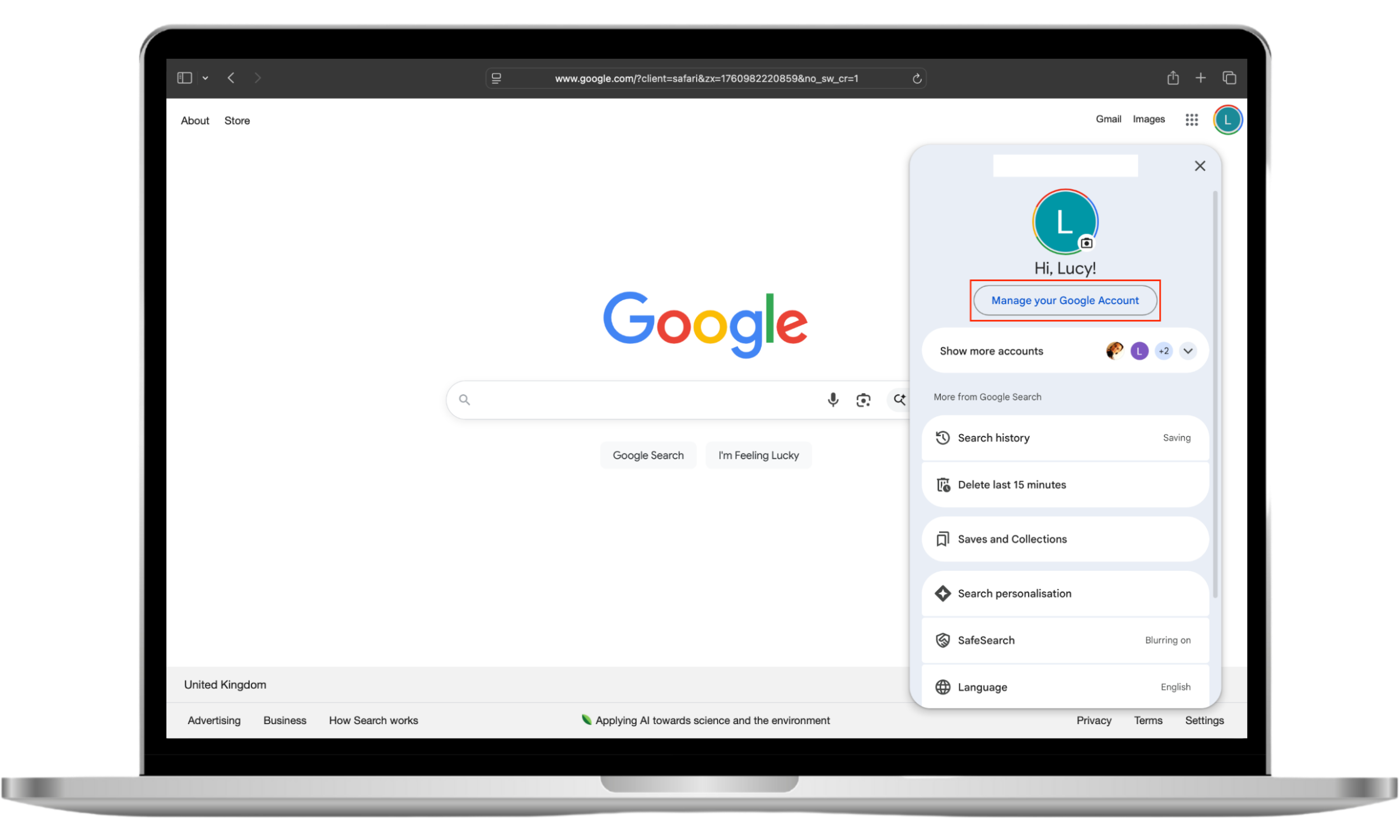
How to change your Google Account password:
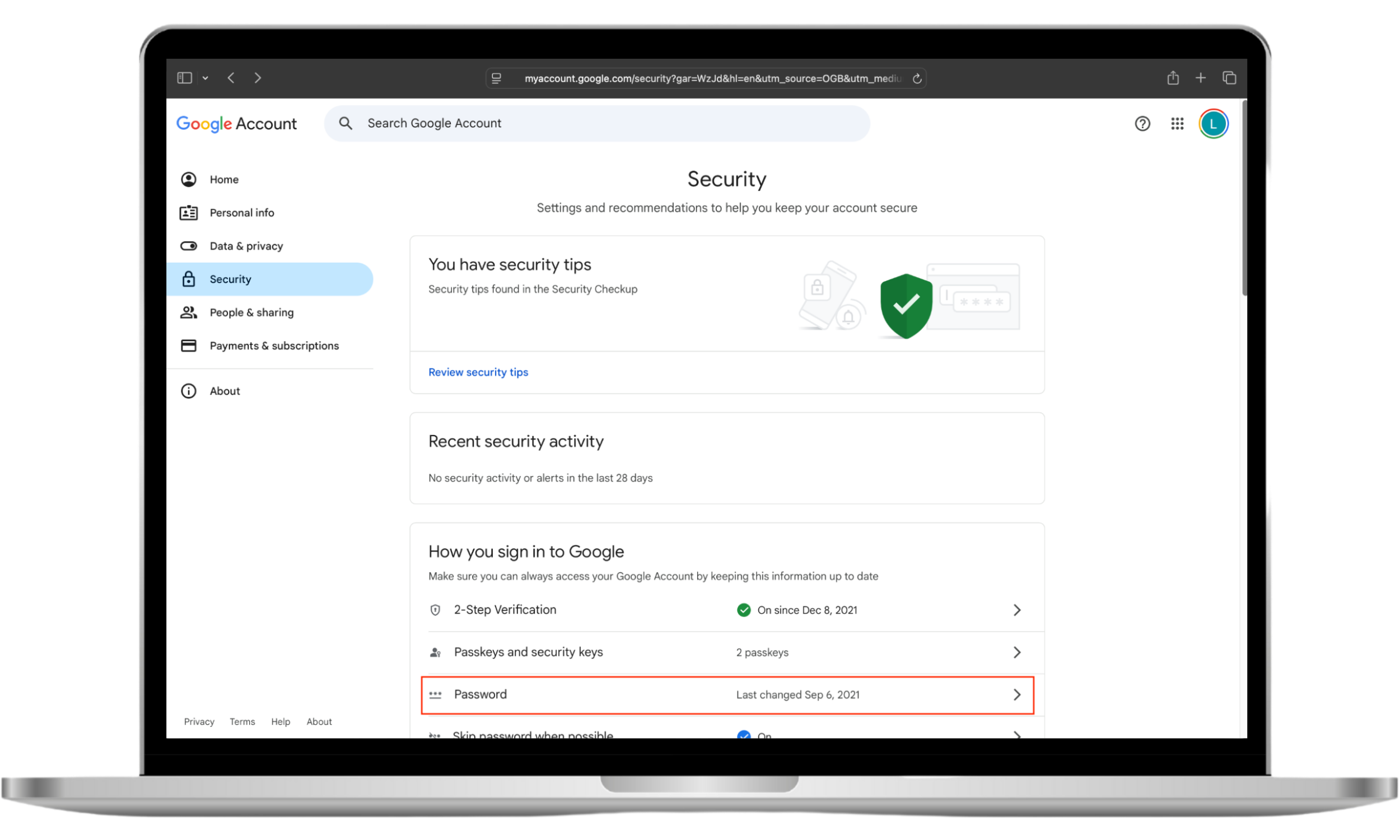
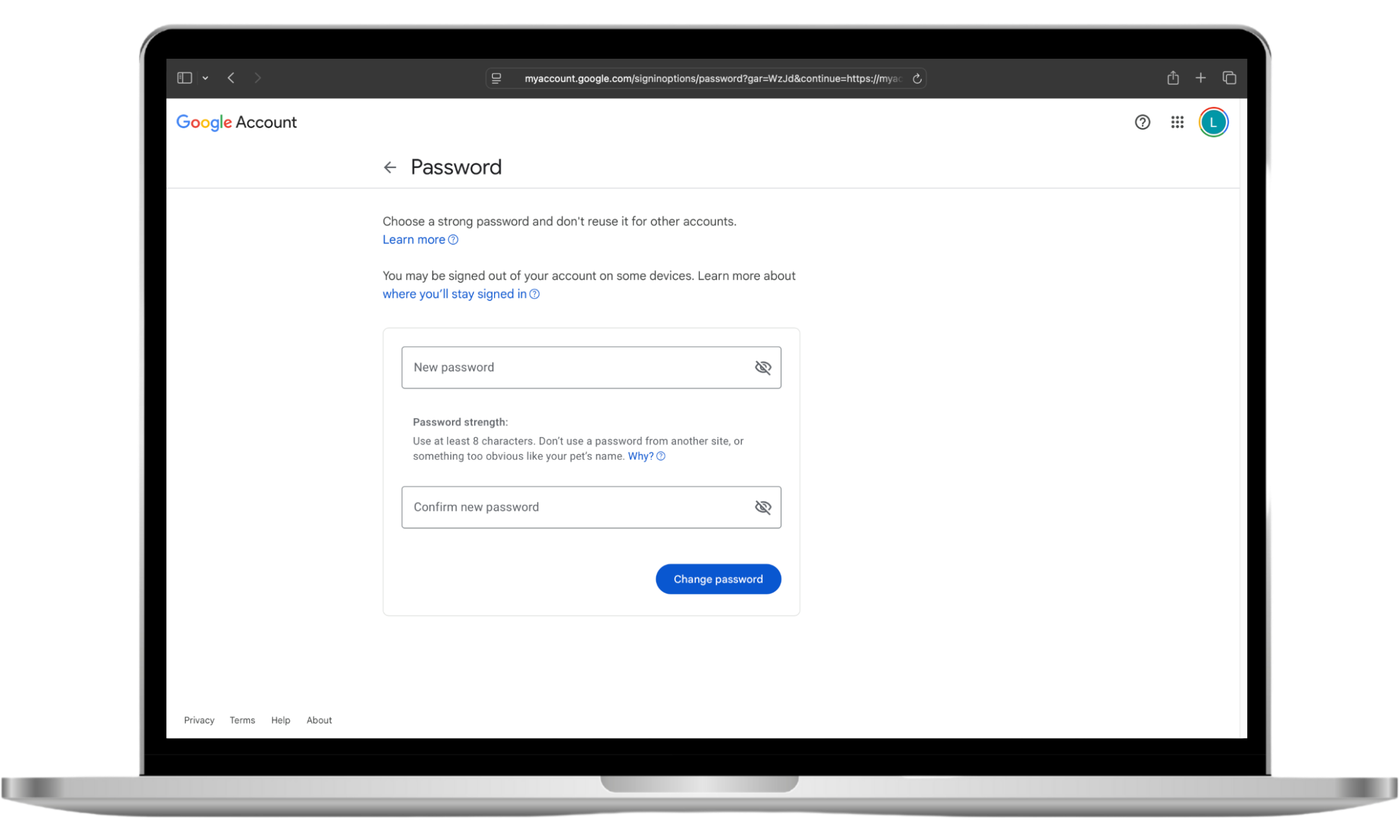
- Go to the Google homepage, click on your profile picture in the top right corner, and then click Manage your Google Account.
- Choose Security, and click Password.
- You may need to enter your password (or use a biometric alternative, such as Touch ID). Choose a new password and click Change password.
3. Use two-factor authentication
Two-factor authentication (2FA) adds a second layer of verification to the login process. In addition to your password, you might need biometric authentication, or a code from a text message, email, or authenticator app. Enabling 2FA won’t reverse phone cloning, but it can stop a hacker accessing your accounts again.
Lots of online accounts will let you set up 2FA. You should enable it for your Google and Apple Accounts, and any online banking accounts, at a minimum.
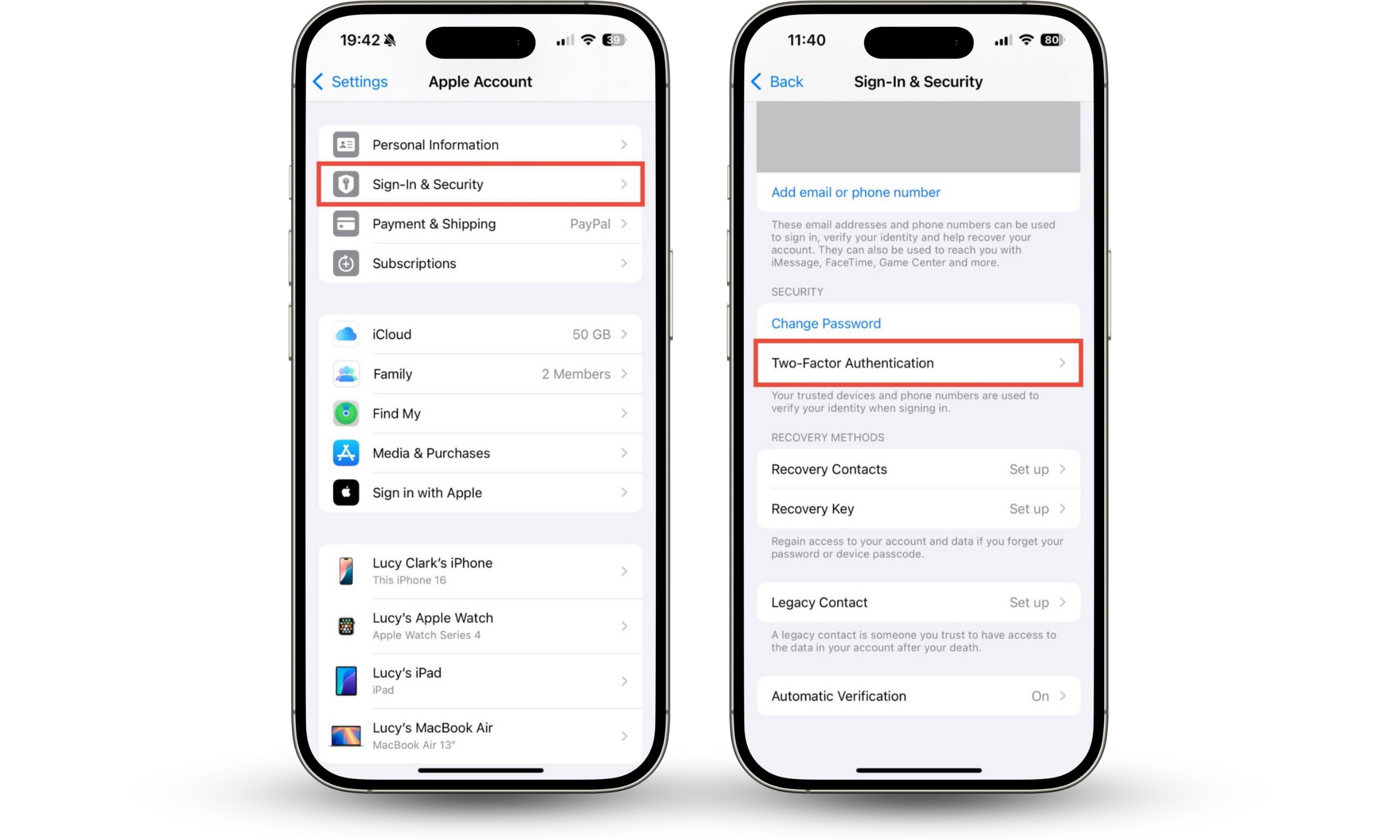
How to set up 2FA for your Apple Account:
- On your iPhone or iPad, go to Settings > Apple Account > Sign-In & Security.
- Choose Two-Factor Authentication, and follow the on-screen instructions to set up 2FA.
How to set up 2FA for your Google Account:
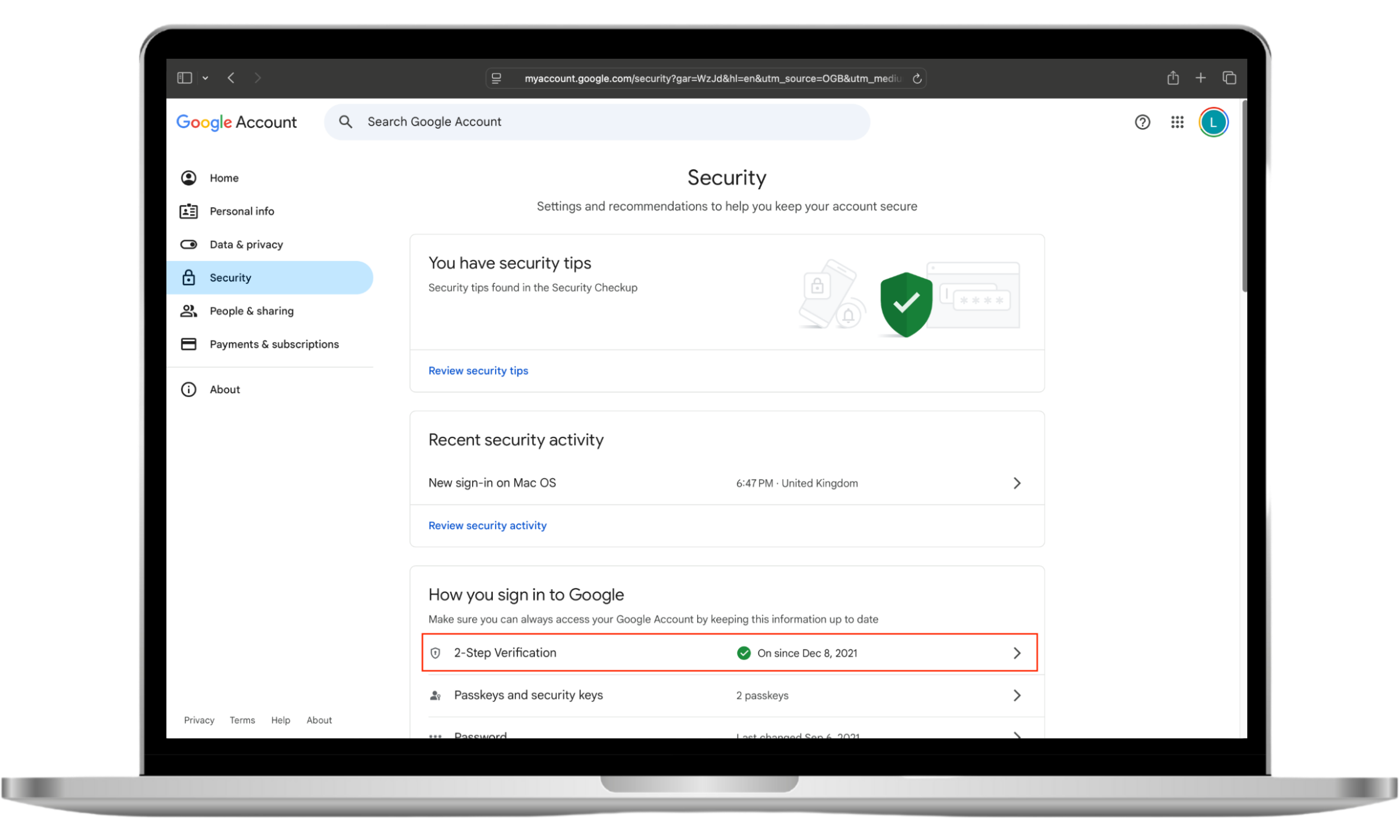
- Go to Google’s homepage and choose Manage your Google Account.
- Choose Security > 2-Step Verification. You may need to enter your password. Then select your chosen 2FA method and follow the on-screen instructions to set it up.
Expert tip
I recommend not using SMS messages for 2FA. As we’ve seen, hackers can intercept text messages. Use the Google Authenticator app instead.
4. Secure cloud accounts
If someone has access to your iCloud or Google accounts, you’ll need to secure them immediately. You can do this by removing any unknown devices from these accounts. This should remove the cloned phone, and they’ll no longer have access to your data.
How to remove devices from your iCloud account:
- On your iPhone or iPad, go to Settings > Apple Account.
- Check the list of devices. If you don’t recognize one, tap on it and choose Remove from Account.
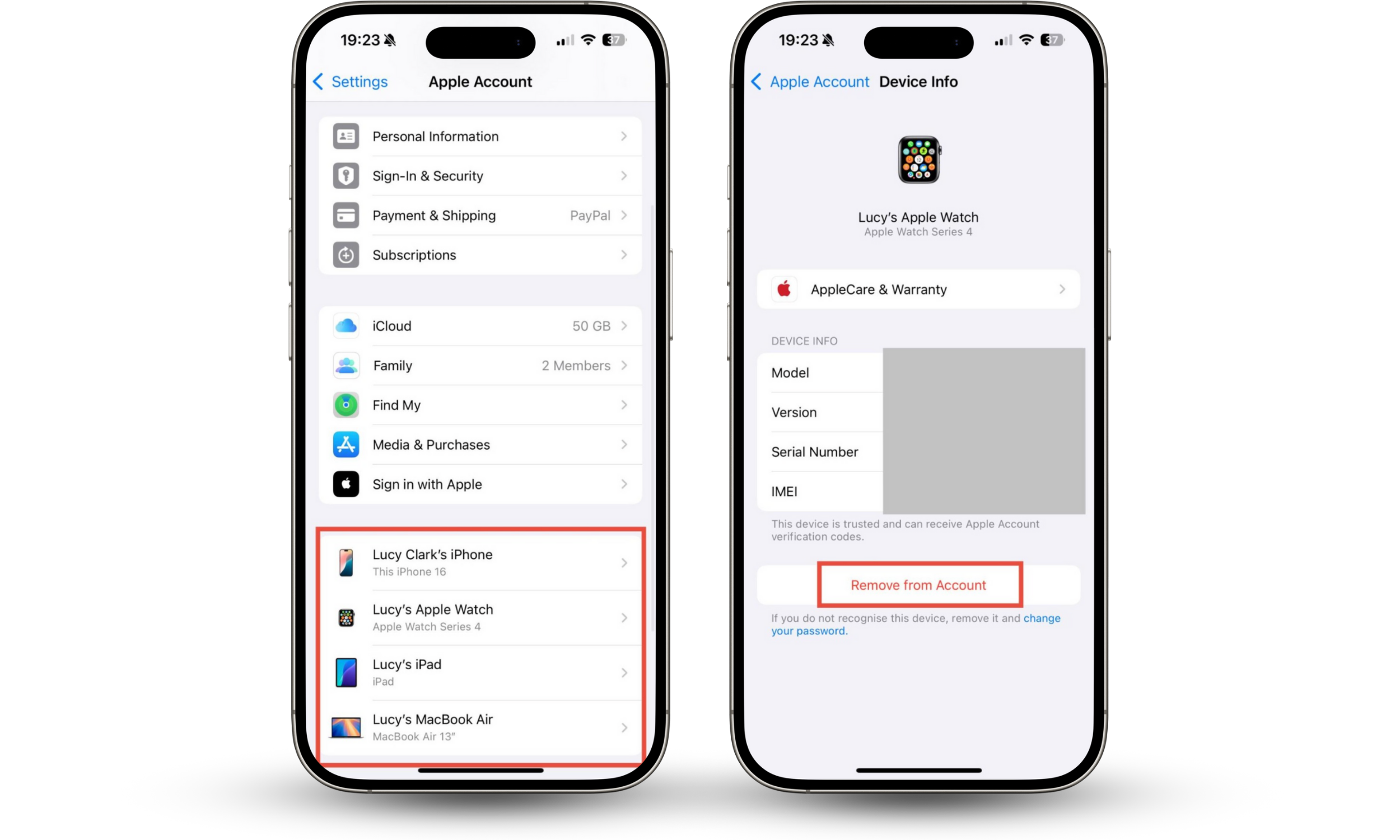
How to remove devices from your Google account:
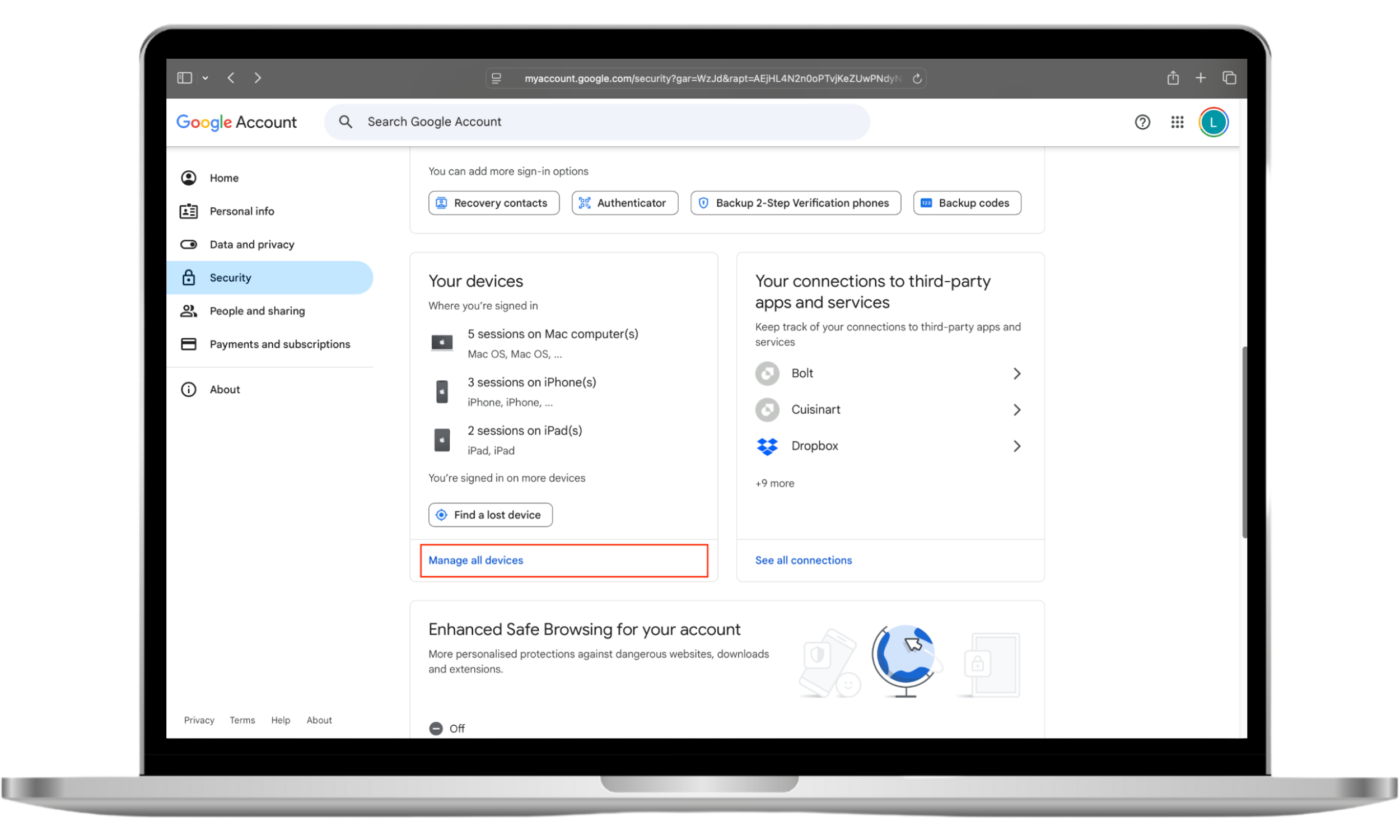
- Go to Google’s homepage and choose Manage your Google Account.
- Click Security, then scroll down to Your devices. Click Manage all devices.
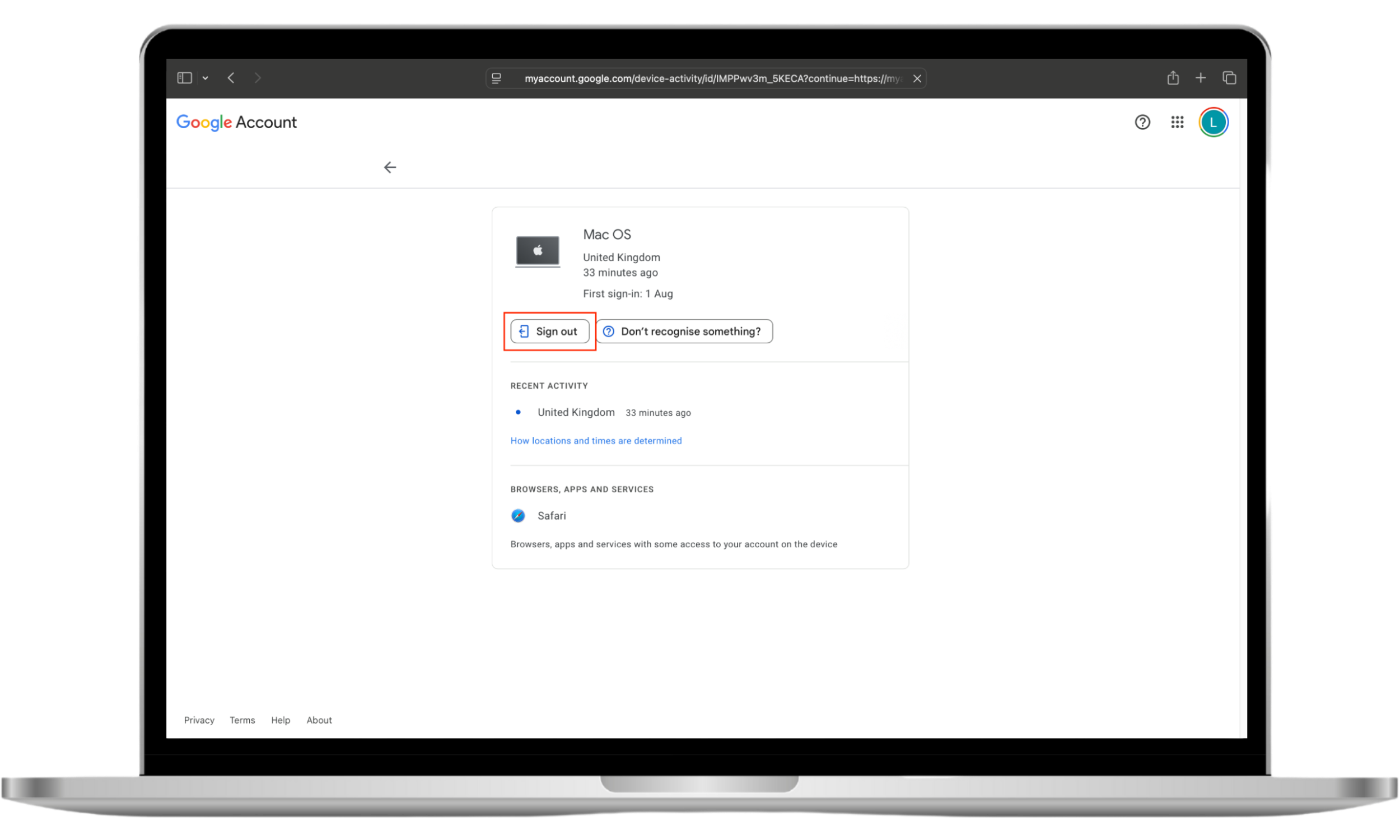
- Look through the devices listed. If you don’t recognize one, click on it and choose Sign out.
5. Contact your mobile carrier
If you’ve fallen victim to SIM cloning or SIM swapping, you’ll need to contact your cell provider to undo the phone cloning. Call them from a different phone, as SIM cloning and SIM swapping both mean you won’t have any service.
When you call your mobile carrier, explain that you’ve lost all cell service, and you think that you’re a victim of a SIM swap scam. Your carrier can either reactivate your original SIM card or send you a new SIM, depending on their policy, to fix the problem.
They may also offer advice on how to report phone cloning to local law enforcement. Ask them if you can set up a PIN or passcode so that no one else can request a new SIM card for your account in the future.
How to prevent phone cloning
To stop phone cloning in future, use unique passwords and 2FA where possible. This can prevent phone cloning through cloud services. If possible, set up a PIN or passcode with your cell provider so no one else can request a SIM card. Know the signs of phone cloning and take action as soon as you suspect it. Don’t put yourself at risk of malware—avoid jailbreaking your phone and using public Wi-Fi.
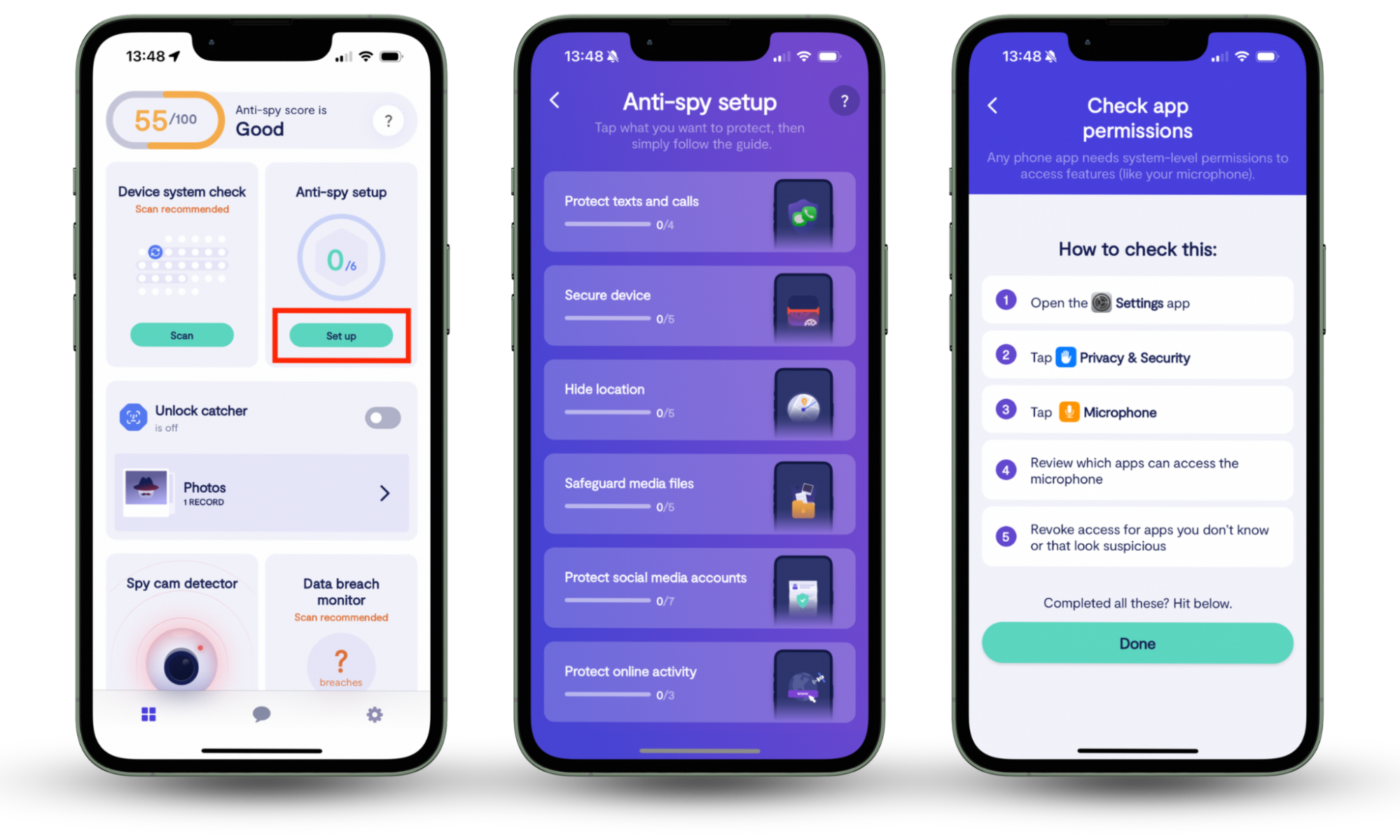
There are often ways to improve your phone’s security. We might like to think that we stay safe online, but, in reality, we all occasionally reuse passwords, share our location, and open unfamiliar emails. Clario’s Anti-spy setup can help you check your phone’s security levels and walk you through how to keep yourself safe in the future.
How to improve your phone’s security:
- Download Clario Anti Spy and subscribe.
- Under Anti-spy setup, tap Set up.
- Follow the on-screen instructions, and tap Done when you’ve finished.
Conclusion
To reverse phone cloning, find out how your phone has been cloned. Someone may have accessed your backups, installed spyware on your device, cloned your SIM card, or requested a new SIM card in a SIM swap scam.
Firstly, if you’re the victim of SIM swapping or SIM cloning, contact your cell provider for support—they can undo phone cloning. If someone has accessed your cloud backups, change your passwords, enable 2FA, and remove any unknown devices from your accounts. If someone accessed your data via spyware, run a scan to find and remove the malicious software—this should stop phone cloning. Use Clario Anti Spy’s Hidden app scan to check for suspicious apps quickly.
Going forward, ensure that you stay on top of your online security. Choose unique passwords, enable 2FA where possible, and use Clario’s Anti-spy setup to improve your phone’s privacy and security settings.


