Table of contents
- What is Coinbase?
- How does Coinbase work?
- 1. Registration and verification
- 2. Buying and selling cryptocurrencies
- 3. Coinbase wallet
- 4. Security measures
- 5. Coinbase Pro
- 6. Regulatory compliance
- Is Coinbase trustworthy?
- Has Coinbase ever been hacked?
- Coinbase pros and cons
- Pros of Coinbase
- Cons of Coinbase
- Is Coinbase secure?
Coinbase is one of the major global cryptocurrency platforms, trading over 240 decentralized cryptocurrencies across 100+ countries using a centralized infrastructure. Its popularity has turned it into a go-to platform. However, as hacking incidents and scams ranging from phishing to complicated Ponzi schemes soar, securing users’ online security and cryptocurrency investments has become a hot topic.
In a 2021 hack, unauthorized third parties exploited a flaw in Coinbase’s SMS account recovery process. This vulnerability gave them access to users’ accounts. To gain access, hackers required email addresses, passwords, linked phone numbers, and access to personal emails.
Although Coinbase implements security measures, only users can protect their accounts from getting hacked. In case of suspicious activity or compromised accounts, Coinbase recommends users lock their accounts.
Coinbase stores user data, app information, and wallet addresses in offline wallets. Offline wallets are much less susceptible to online threats and hacker attacks compared to online wallets. Coinbase stores users’ private keys with AES-256 encryption, known for its high security.
In 2023, over $1 billion was lost to crypto hacks, but understanding Coinbase’s safety features can help safeguard your investments.
What is Coinbase?
What is Coinbase?
Coinbase is a well-established cryptocurrency exchange that enables users to buy, sell, and manage over 240 cryptocurrencies.
Such a selection gives users the advantage of exploring the potential of new and up-and-coming cryptocurrencies on one platform. The company emerged as a trustworthy platform that enables sending and receiving Bitcoin in 2012. Having navigated numerous challenges since its founding, the platform has earned a reputation for being safe, secure, and trustworthy.
Of course, security is at the top of everyone’s list when it comes to the safety of funds. To keep Coinbase safe, the platform has addressed such concerns by implementing robust security measures and utilizing industry-standard encryption protocols to protect sensitive information and 2-tier authentication to provide further security.
How does Coinbase work?
Coinbase connects both buyers and sellers on its platform. In order to keep user funds and Coinbase safe, when a user wants to buy or sell a cryptocurrency, Coinbase matches the order with other users, ensuring secure transactions. Despite boasting features such as two-factor authentication and regulatory compliance, Coinbase’s centralized structure means the platform holds users’ private keys, raising questions over the safety and management of cryptocurrencies.
1. Registration and verification
In order to keep Coinbase trustworthy, any new user will need to register for an account by providing their email address, creating a password, and completing identity verification. This involves submitting personal information and, in some cases, documents to comply with regulatory requirements and enhance safety.
- Be at least 18 years old (proof required).
- Have a government-issued photo ID (passport cards not accepted).
- Have a computer or smartphone with internet connectivity.
- Provide a phone number linked to your smartphone (for SMS text messages).
- Use the latest version of your browser (recommend Chrome) or the newest Coinbase App version.
- If using the Coinbase app, ensure your phone’s operating system is up-to-date.
2. Buying and selling cryptocurrencies
Once the registration process is complete, users can deposit funds into their Coinbase account using various payment methods, including bank transfers, credit/debit cards, or other supported options. This step is crucial for buying cryptocurrencies on the exchange.
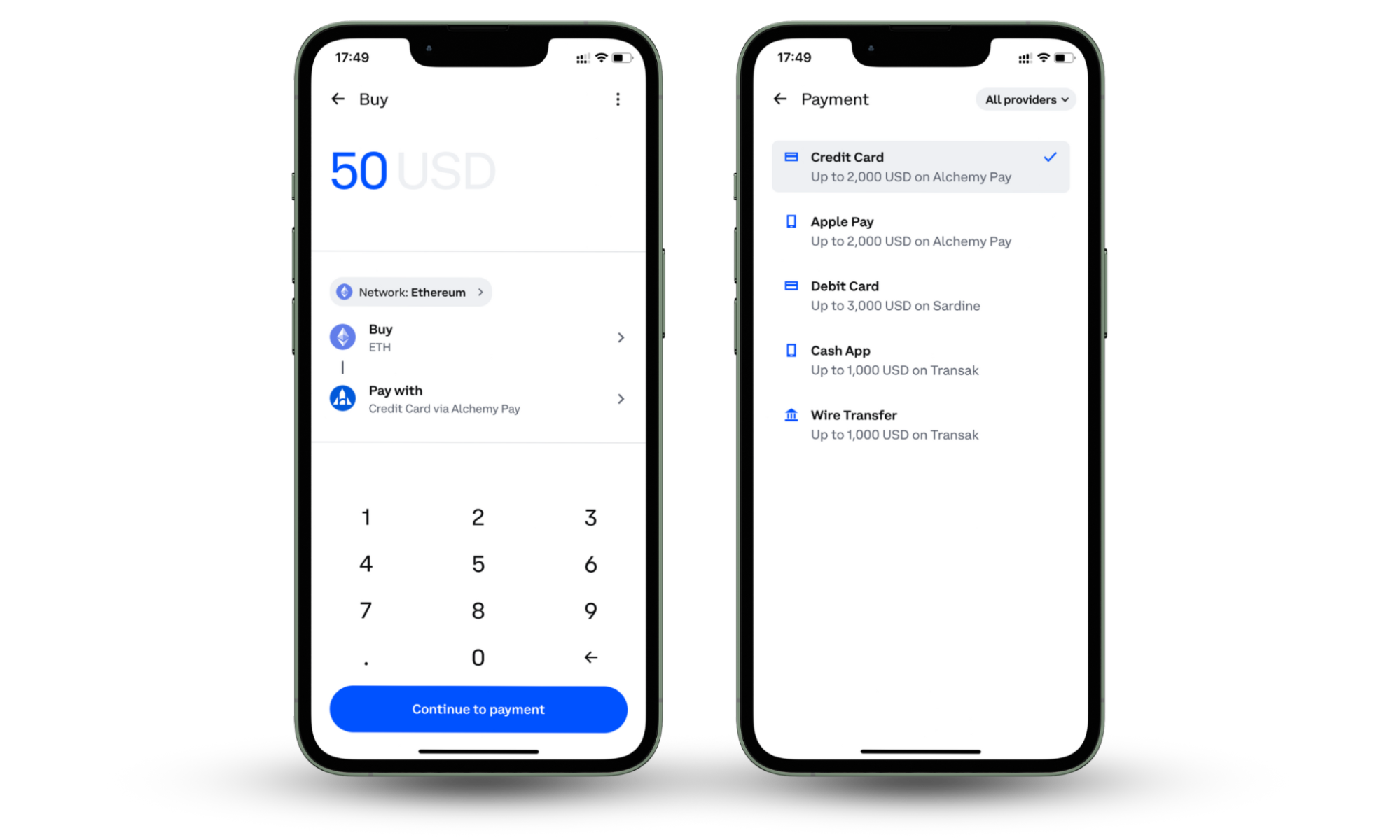
Also, Coinbase rolled out a new tool, Coinbase Pay, to streamline the cryptocurrency loading process into your wallet. Accessible through the Coinbase Wallet extension on Google Chrome, users can initially link their wallet to their Coinbase account.
Users can select the “Add crypto with Coinbase Pay” button to choose the currency, input the amount, and complete the transaction, and their funds become instantly available.
To purchase crypto, ensure your wallet has funds or another cryptocurrency to exchange. Coinbase also allows users to top up their wallets through bank transfers, credit/debit cards, or using Coinbase Pay. This feature streamlines the payment process via the Coinbase Wallet extension on Google Chrome.
Users can link their wallet by selecting “Add crypto with Coinbase Pay,” specifying the currency and amount, completing the transaction, and enjoying instant fund availability. Further details are available on the Coinbase website.
Users can easily sell their cryptocurrencies from any device by simply heading to the “Sell” area of the platform, selecting the amount they’d like to sell, the currency, and the currency to wish they’d like to receive. The final stage in this process involves previewing the sale.
3. Coinbase wallet
Coinbase Wallet is a completely separate story from the Coinbase app. Mainly, it is a self-custody wallet, which means you are in control of your crypto assets. Coinbase Wallet, unlike the Coinbase app, stores private keys on your mobile device, adding security and autonomy. Through this “portal,” users can access the crypto world, over 5,500 assets, and multiple blockchain networks.
The downside with this wallet is network fees, also known as “gas fees.” Such fees occur when making “on-chain” transactions. Coinbashas has no control over these fees, so users should be aware when sending assets or getting involved in DeFi protocols.
4. Security measures
To keep Coinbase legit, the platform has put a lot of emphasis on security measures and the protection of user accounts and assets from any potential breach and scam. Users are encouraged to enable two-factor authentication, use secure devices, and follow the best security measures to safeguard their accounts, devices, and sensitive data from potential threats.
Coinbase, just like any other company or online platform, is at risk of hacker attacks. Suppose cyber attackers can access Coinbase’s inner resources or user information. In that case, there is a potential risk to user accounts, putting their digital assets and personal information in the line of fire. Coinbase uses the InsurAce Protocol, a decentralized multi-chain system, to bolster security further and mitigate such risks.
5. Coinbase Pro
Catering for more advanced traders, Coinbase offers the option called Coinbase Pro, a separate platform with additional features such as advanced charting tools and lower trading fees. Complete integration is provided in the service, ensuring users can seamlessly transfer funds between Coinbase and Coinbase Pro, knowing their assets and personal information are protected.
6. Regulatory compliance
Coinbase adheres to regulatory standards and compliance requirements. This commitment keeps Coinbase safe and helps protect user privacy, personal information, and financial assets, reassuring users that the platform operates within legal frameworks.
Is Coinbase trustworthy?
Although not 100% secure, Coinbase is generally regarded as one of the industry's safest crypto exchanges. What keeps Coinbase secure is the huge emphasis on prioritizing the implementation of advanced security features. This not only ensures the safety of users’ crypto assets but also provides a secure environment and keeps Coinbase legit so users can enjoy the platform’s features to their full extent. As a result, the platform has built up a good reputation for its reliability and trustworthiness.
Below are the security features Coinbase has implemented throughout the years:
- Know Your Customer (KYC). Coinbase requires users to follow identity verification procedures to adhere to Know Your Customer (KYC) laws. This is a multi-step process ensuring the legitimacy of customer identities to prevent fraudulent account creation and usage. Users must provide a passport, a government-issued photo ID, or a national identity card.
- 2-Step Verification. Automatically activated for all users, this feature provides an additional layer of account security.
- Password Protection. Passwords are irreversibly hashed with bcrypt and are stored securely.
- Continuous monitoring. This feature automatically secures login credentials in response to potential risks.
- Proactive Account Monitoring. Coinbase carries out active surveillance for suspicious activities. On top of this, the Coinbase team has created a Dapp blocklist, using a combination of public and private databases to protect users from potentially malicious decentralized applications (Dapps) in the Web3 space. Users can also automatically lock their accounts in case unusual activity is detected.
Dapps (Decentralized Applications)
Applications built on blockchain technology that are distributed across a network of computers, offering users transparency, security, and autonomy.
Web 3
The next evolution of the internet, characterized by decentralized, peer-to-peer interactions, increasing privacy, security, and user control.
- Private Keys and Seed Phrase Security. Private keys and seed phrases, vital for accessing and spending cryptocurrencies, must never be shared. Sharing them compromises wallet security, risking unauthorized access and fund theft. Keep this information confidential for asset protection.
Also, If there is a dangerous app or a potential breach, Coinbase Wallet flags up the issue, warning users before proceeding, further enhancing their crypto experience's overall security.
On top of this, Coinbase Wallet addresses the threat of spam tokens, which are tokens airdropped into users’ wallets, intending to lead them to fake cryptocurrency websites. To address this issue, Coinbase Wallet conceals potentially harmful assets from the home screen.
On the Coinbase website, you will find tips on how to avoid crypto scams. This is part of Coinbase Learn—a dedicated space created to educate users about crypto basics. The platform also offers courses in scam awareness and potential hacking issues they may experience, such as NFT scams that involve phishing or fraudulent activity associated with NFTs for profit.
Additionally, users can report any suspicious tokens that may appear as assets in their wallet, empowering them to actively contribute to the platform’s security measures and maintain the integrity of their cryptocurrency holdings. These robust security measures demonstrate Coinbase’s commitment to providing a secure environment for users exploring the decentralized and dynamic world of Web3.
Tip
Awareness has never been more important as the crypto industry continues to develop at breakneck speed. Learn about crypto scams, avoid fake claims, and secure your crypto!
Has Coinbase ever been hacked?
Yes. Coinbase has faced multiple hacking attempts. Such events highlight that user accounts on the platform are not entirely immune to hacking, emphasizing the need for robust personal security practices.
Such risks emphasize the need for proactive measures that Clario AntiSpy can offer. Keeping your data safe when you surf online and enhancing protective measures no longer need to be an issue. Clario AntiSpy secures users’ devices and online identities from viruses, hacking, ID theft, and real-time spying.
Clario Anti Spy helps you check for risky settings, suspicious access, and permission misuse that could put your accounts at risk.
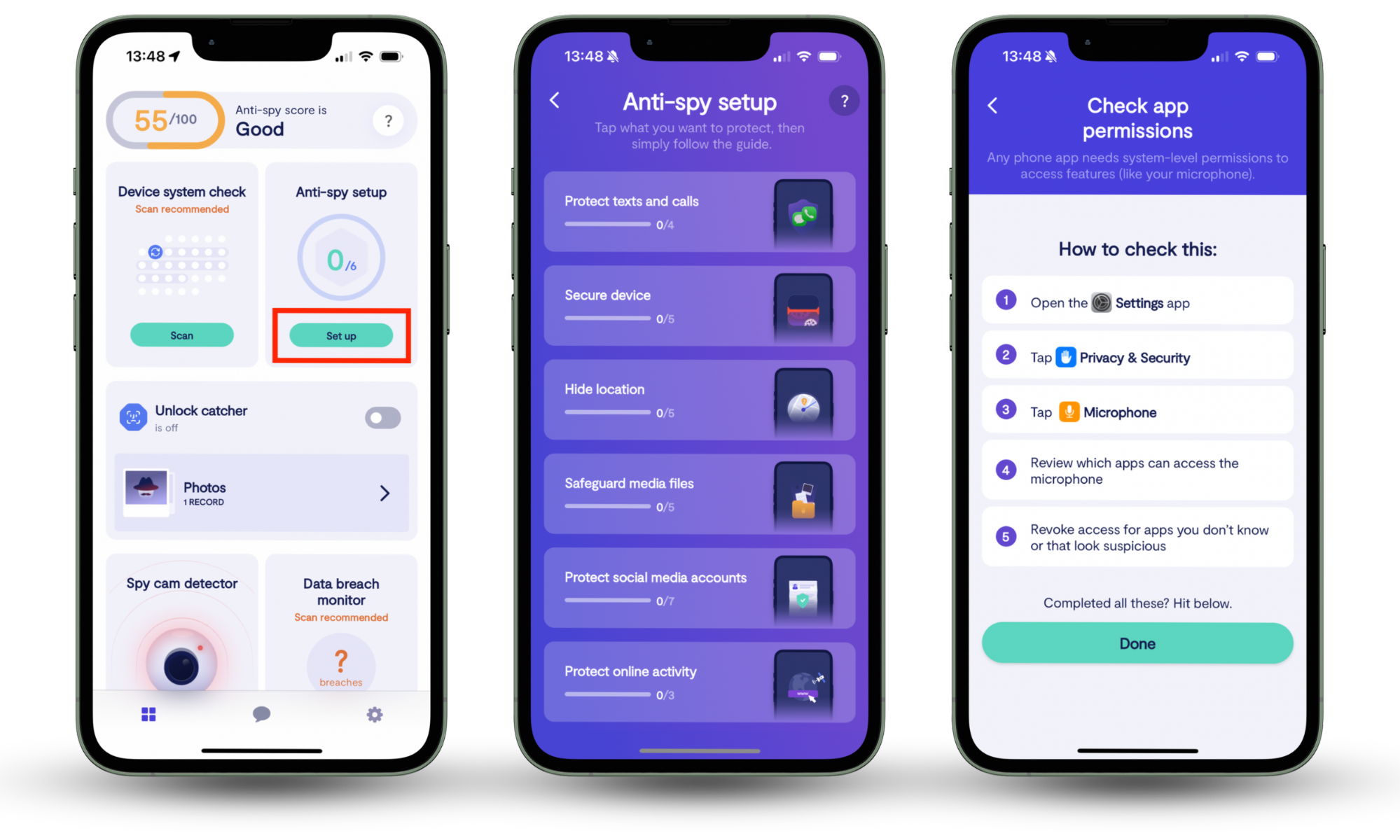
One way it does this is through its anti-spy setup, which guides you through key device checks to improve your security.
Clario’s Anti-spy setup gives you a guided checklist to help spot weak points on your phone. It walks you through essential device checks to make your crypto use safer, from detecting risky changes to tightening key security settings.
Here is how you can use Clario’s Anti-spy setup on your phone:
- Download the Clario Anti Spy app and create your account.
- On the dashboard, tap Anti-spy setup.
- Select the parts of your phone you want to protect, location, or online activity.
- Follow the on-screen checklist to review and apply the recommended security fixes.
1. DDoS Attack (2017)
In 2017, Coinbase encountered a Distributed Denial of Service (DDoS) attack, impacting its online services. The attack overwhelmed Coinbase's servers with traffic, causing temporary disruptions in service.
Crypto exchanges suffer overwhelming traffic attacks quite often. However, they usually target the platform itself rather than its users.
2. SIM Swapping Attack (2018)
A SIM swapping attack on Coinbase took place in 2018. Cybercriminals manipulated mobile carriers to transfer users' phone numbers to new SIM cards. This attack gave the hackers control over account recovery processes, resulting in unauthorized access to accounts, risking loss of funds and identity theft.
3. Credential Stuffing Incident (2019)
In 2019, cybercriminals leveraged automated bots to systematically attempt logins using stolen usernames and passwords. The incident led to unauthorized access to accounts, potential fund theft, and an increased risk of account takeovers.
NB Credential Stuffing
Credential stuffing is a cyberattack where stolen usernames and passwords, often obtained from data breaches, are used to give hackers unauthorized access to user accounts.
4. Phishing Attack (2020)
Hackers were able to deceive Coinbase users through emails and fraudulent websites into revealing login credentials. The attack resulted in compromised user accounts and unauthorized access to funds.
5. Insider Threat Exploitation (2021)
In 2021, Coinbase faced insider threat exploitation, where an internal employee used their position to compromise user data and to carry out unauthorized transactions.
Such hacking attacks underscored that user accounts on the platform are not entirely immune to security risks. Sophisticated hackers, armed with personal information like addresses, passwords, and phone numbers, may gain unauthorized access to individual accounts, even without directly compromising Coinbase’s systems. It highlights the importance of users maintaining robust personal security practices to secure their cryptocurrency assets.
Cryptojacking is also becoming a more common threat in the crypto sphere, often affecting users who are completely unaware that any hacking activity or breach is happening. Recognizing the tell-tale signs of potential hacks and cryptojacking detection are vital to safeguarding your identity and assets.
Coinbase pros and cons
| Pro | Con | |
|---|---|---|
| Easy to use | ✅ | |
| Earning ability | ✅ | |
| Wide variety of currencies | ✅ | |
| Premium subscription service | ✅ | |
| Low fees | ❌ | |
| Hacking attempts | ❌ | |
| Unlimited control over funds | ❌ | |
| Account restrictions | ❌ |
Pros of Coinbase
Like with any platform, there are always lists of pros and cons. Let’s take a look at some of them to get a good understanding of how the platform shapes up.
1. Easy to use for beginners
What sets Coinbase apart from other crypto exchange platforms is its super user-friendly interface, making it the go-to platform for newbies making their first steps into the world of cryptocurrency. The user-friendly design is ideal for guiding you through buying, selling, and trading digital assets hassle-free.
Plus, Coinbase provides guides that walk you through step-by-step. And if you still have any worries, the platform’s educational section will have all the answers to your questions.
2. Earning ability
Coinbase offers users a wide range of earning opportunities that go far beyond trading. Coinbase Learning Reward courses allow users to earn passively while enhancing their knowledge about cryptocurrencies. The platform gives users a rich collection of topics to dive into, including how to best protect crypto assets, comprehensive guides on popular cryptocurrencies, and trading tips. Additionally, users can earn interest on their balances, opening up the possibility for passive income all on the platform.
3. Offers a choice of cryptocurrencies
Coinbase stands out for its pretty impressive selection of cryptocurrencies. So far, the platform boasts a collection of over 240. This massive choice of crypto not only provides users with the opportunity to explore digital assets to their heart’s content but also allows users to develop their strategic and diversified investment strategies.
4. Coinbase One
Coinbase has introduced a premium subscription service. Coinbase One provides exclusive benefits such as zero trading fees, 24/7 priority customer support, $1 million account protection, and a streamlined tax reporting experience with a pre-filled Form 8949. US customers can enjoy a 30-day free trial to experience these enhanced platform features.
Additionally, Coinbase has extended its selection of coins to include stablecoins, including USDC, USDT, and DAI. Eligible USD Coin customers can further benefit from rewards, earning up to a 6.00% Annual Percentage Yield (APY) through the Coinbase app’s incentivized program. These features greatly benefit users and optimize the crypto trading experience on Coinbase.
Stablecoin
Stablecoins are digital currencies pegged to a reserve asset like the U.S. dollar or gold that are designed to reduce volatility and give the cryptocurrencies “stability.”
Cons of Coinbase
Drawbacks with the platform include high transaction fees, concerns over privacy, limited control over private keys, and possible account restrictions.
1. Transaction fees
Coinbase’s fees, especially transaction fees for trading crypto, can be higher than other platforms. For instance, at the time of writing, the platform charges a 0.3% transaction fee. Binance charges a 0.030% fee, whereas Crypto.com charges a 0.075% transaction fee. This impacts cost-effectiveness, particularly for frequent traders. As a result, users may find alternative exchanges with lower fee structures more financially favorable.
2. Privacy concerns
Coinbase has faced criticism for sharing customer information with the IRS. The platform asserts that any disclosure to the IRS is strictly in accordance with legal requirements. Despite implementing measures such as data encryption to protect customer privacy, concerns persist among some users, fuelled by past high-profile hacking attempts.
Unsurprisingly, Coinbase’s mandatory user verification process while complying with regulations raises many privacy issues. This concerns the type of information customers must provide and what could be accessible in the event of possible hacking attempts.
3. Limited control over funds
Another issue discussed in the online community is that Coinbase users sacrifice direct control over private keys, putting their full trust in the platform’s security. This reliance on Coinbase’s measures may raise concerns among those valuing autonomy and control over their digital assets, particularly in the case of successful hacks and the potential loss of funds.
4. Potential for account restrictions
Coinbase’s history of suspending or restricting user accounts from the platform, often due to regulatory compliance, brings about potential inconveniences. Users should be aware of this possibility and consider the impact on accessibility and trading activities.
Despite seeming like a disadvantage, the pro here is Coinbase’s demonstration of vigilance in the face of both hacking threats and fraudulent accounts. The best advice here would be to stay informed, always provide correct information when requested, and implement security measures. Against possible blocks and breaches, these steps are key to navigating these possible challenges.
Is Coinbase secure?
Yes. By prioritizing security and employing advanced measures like biometrics, passwords, and security locks, Coinbase is able to bolster its defense against threats. Nevertheless, this is not a guaranteed solution, and the safety of users’ accounts and assets is still an issue.
It should be highlighted that hacks are an issue in the crypto sphere, and no exchange is completely safe from potential hacking attempts. Therefore, users must stay vigilant, adopt strong personal security practices, and remain informed about potential risks.
Clario’s Anti-spy setup helps you check your phone for spying tools, system weaknesses, or risky access that could compromise your crypto activity. Before you sign in, trade, or store assets, secure the device you use most.
Stay informed and protect your online security. Explore more insights on hacking and stay ahead of potential scams and threats with Clario AntiSpy.


