Table of contents
- What is remote access control?
- Remote access security risks
- Remote access scams
- Full control over your computer
- Lack of understanding of what’s happening on the session
- How to prevent risks and give remote access safely
- Only allow remote access to those you trust
- Ask questions
- Ensure the company takes responsibility
- Back up your system regularly
- End a suspicious remote access session
- Use a security app
- Wrapping Up
Remote access is a way of accessing a Mac from a separate location to your home or office. As such, it’s a double-edged sword: it can save you time and effort when on the move, but it can also expose you and your personal data to multiple cybersecurity risks.
Let’s dive deeper into the topic to understand remote access security threats and learn the best ways to protect your digital identity.
What is remote access control?
Remote access is the ability to connect to another Mac and operate it as your own. This comes in handy when you need to access files on your device when you’re not with it. Remote access control can also be used to let other people access your Mac for troubleshooting.
The term remote access is often confused with similar technologies that provide very different levels of control and security exposure.
| Access type | What the user can do | Level of control | Typical use cases |
| Remote access | Fully control the device as if physically present | Full system control | IT support, remote work, accessing files and apps |
| Remote desktop / Screen sharing | View the screen and control specific actions | Limited or session-based control | Guided troubleshooting, collaboration |
| File-only access | Access and transfer files only | No system or app control | Retrieving documents without system access |
To access your Mac remotely, a reliable internet connection is needed. Furthermore, your devices should be configured to facilitate the remote connection, which is usually established via Remote Login.
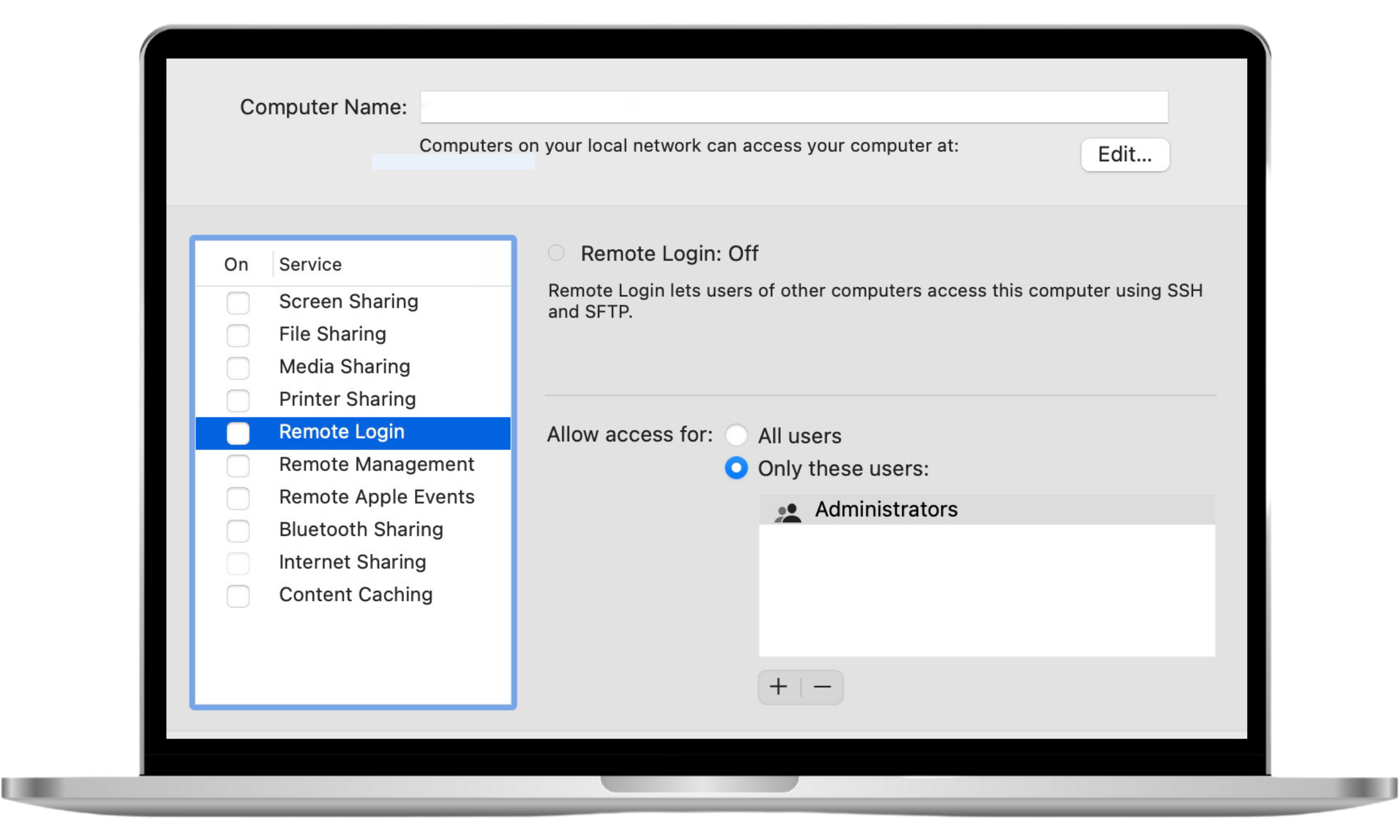
Remote access security risks
The remote connection is quite safe: macOS has an inbuilt remote desktop client allowing an encrypted connection between devices. Remote access risks stem not from the connection itself, but rather from those who misuse it for the following purposes:
Remote access scams
Cybercriminals use social engineering tactics to gain access to people’s devices. For example, they sometimes pose as telecommunication company representatives to convince victims that their computer needs an urgent fix via a remote connection. If access is granted, the criminals then install malware or ransomware to steal or encrypt the victim’s data.
Full control over your computer
When you grant somebody remote access to your computer, in effect, you are physically handing over your machine to them - the person will be able to do almost anything with your system. This is quite concerning, especially if there’s a hacker now in charge of your device.
Lack of understanding of what’s happening on the session
Even if you have an option to end a remote session at any time, a good question is when should you do it? What is the red flag sign to tell you when you should halt the connection? You need to possess some basic tech knowledge to realize remote access is being misused.
How to prevent risks and give remote access safely
Only allow remote access to those you trust
👀 If you get a call from an unknown person requesting remote access to your Mac, it’s most likely a scam.
☝️ Remember: reputable companies do not offer unsolicited repair services. Never allow unknown individuals to fix your Mac remotely, especially if you haven’t requested it first.
Ask questions
🧐 Don’t hesitate to ask someone why they need to access your computer and what they are going to do with it. If you are suspicious, ask for an alternative solution.
For example:
- What exactly will you do on my Mac during this session?
- Do I need to stay and watch while you’re connected?
- Can this be fixed without remote access?
👩💻 Good tech support explains how you can fix the issue yourself. The bad one or scammers will always insist on connecting to your Mac remotely.
Ensure the company takes responsibility
🕵️♂️️️️️️ Sometimes even the right actions can produce unexpected results. Make sure the company whose representative accesses your computer assumes full responsibility for their actions if something goes wrong.
Back up your system regularly
🤫 System restoration from a backup is your safety net in case something goes wrong during a legit remote connection session. And it is absolutely indispensable if you fall into a scammer’s trap. By backing up your Mac regularly, you minimize the risk of complete data loss.

End a suspicious remote access session
🙄 If something seems fishy about a remote access session, stop it at once. The red flag to look out for is any attempt to obtain your credit card information, login credentials, social security number, any SMS confirmation codes, or any other sensitive information.
Use a security app
Letting someone access your Mac remotely can be helpful, but it comes with risks. It’s a good idea to check your system settings and make sure nothing on your Mac is giving away more than it should.
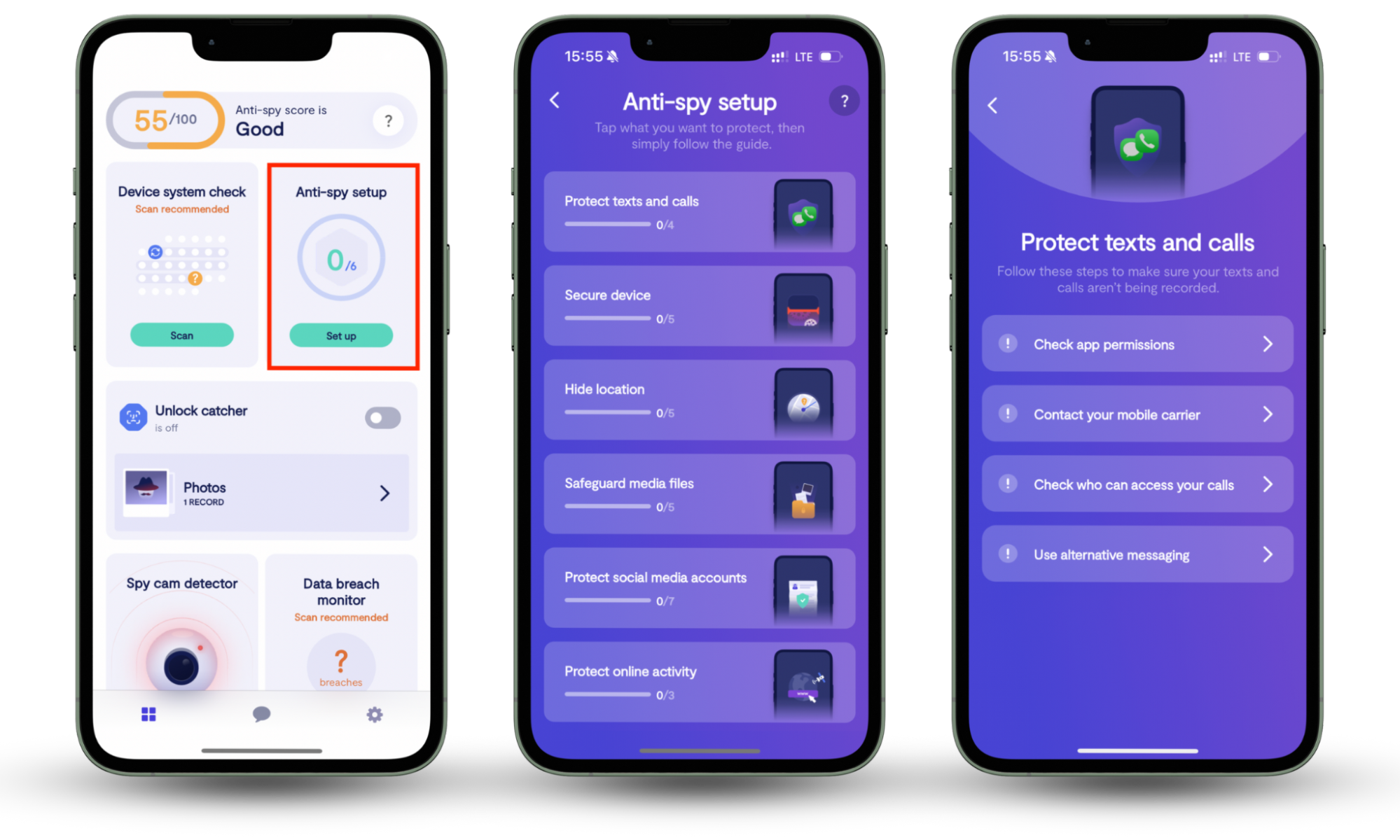
That said, your phone matters, too. A lot of remote access hacks start there. Clario’s Anti-spy setup walks you through your device’s security configurations, app permissions, and tracking settings to make sure it isn’t exposed during or after a session.
Follow these steps to use the Anti-spy setup feature:
- Download Clario Anti Spy, and create an account.
- Tap Anti-spy setup.
- Go through the checklist on your screen.
- Make the changes it suggests to better protect your phone.
Wrapping Up
To sum up, allowing somebody to access your Mac remotely can be both useful and risky. Therefore, you should be absolutely certain that a person accessing it is trustworthy.
Explore our blog for more practical cybersecurity tips. If you’re setting up remote access on your Mac, take a moment to check your phone too. It’s often the first place attackers look for a way in. Clario Anti Spy’s Anti-spy setup helps you review your mobile privacy settings so nothing on your phone leaves your Mac exposed.
Read more:


