Table of contents
- What is encryption?
- How encryption protects data
- When should encryption be used?
- Everyday examples of data encryption
- Why is data encryption important?
- Can encryption be hacked?
- Is encryption safe?
- How to protect yourself where encryption doesn’t
- Conclusion
Google encrypts 95% of the traffic. What does it mean? What is encryption?
What is encryption?
Encryption is the process of making data unreadable to an unauthorized party. This is achieved by turning original data into seemingly random data using a cryptographic key. Later, this original data can be deciphered by an authorized party using the key.
There are two main types of encryption: symmetric and asymmetric. Symmetric encryption involves a single cryptographic key for both encryption and decryption. In contrast, asymmetric encryption requires two keys to encode and decode information.
How encryption protects data
At its most basic level, encryption provides data confidentiality. But it also performs other functions to ensure you can trust encrypted and decrypted data.
- Confidentiality - encodes and hides the message
- Authentication - verifies the message’s origin
- Integrity - proves the message’s contents haven’t been changed since sending
- Non-repudiation - ensures a message sender can’t deny sending the message
To provide confidentiality, information is encrypted using formulas called encryption algorithms, or ciphers. One part of the algorithm must have a variable called a key.This makes the algorithm’s output unique, thereby turning your data into unreadable code.
If your encrypted information is intercepted by an unauthorized user, they have to either guess the encryption algorithm used to encrypt the data or the keys used as variables. Naturally, it’s a tough challenge, and this is what makes encryption such an effective security tool.
It doesn't matter how strong your encryption is—if your accounts credentials get leaked, your data is still at risk. That's where Clario Anti Spy comes in. It's an anti-spyware solution for iPhone and Android that includes a Data breach monitor to alert you if your online accounts are involved in a data breach.
Here's how to activate the Data breach monitor in Clario Anti Spy:
- Download Clario Anti Spy and subscribe to create an account.
- Tap Scan under Data breach monitor.
- Wait for the scan to complete. If your email is found in a data breach, change your passwords immediately starting with critical accounts like banking and email. You'll also get alerts if your email shows up in any future breaches.
- If you need help, tap the Messages icon on the main screen to connect with a security expert.
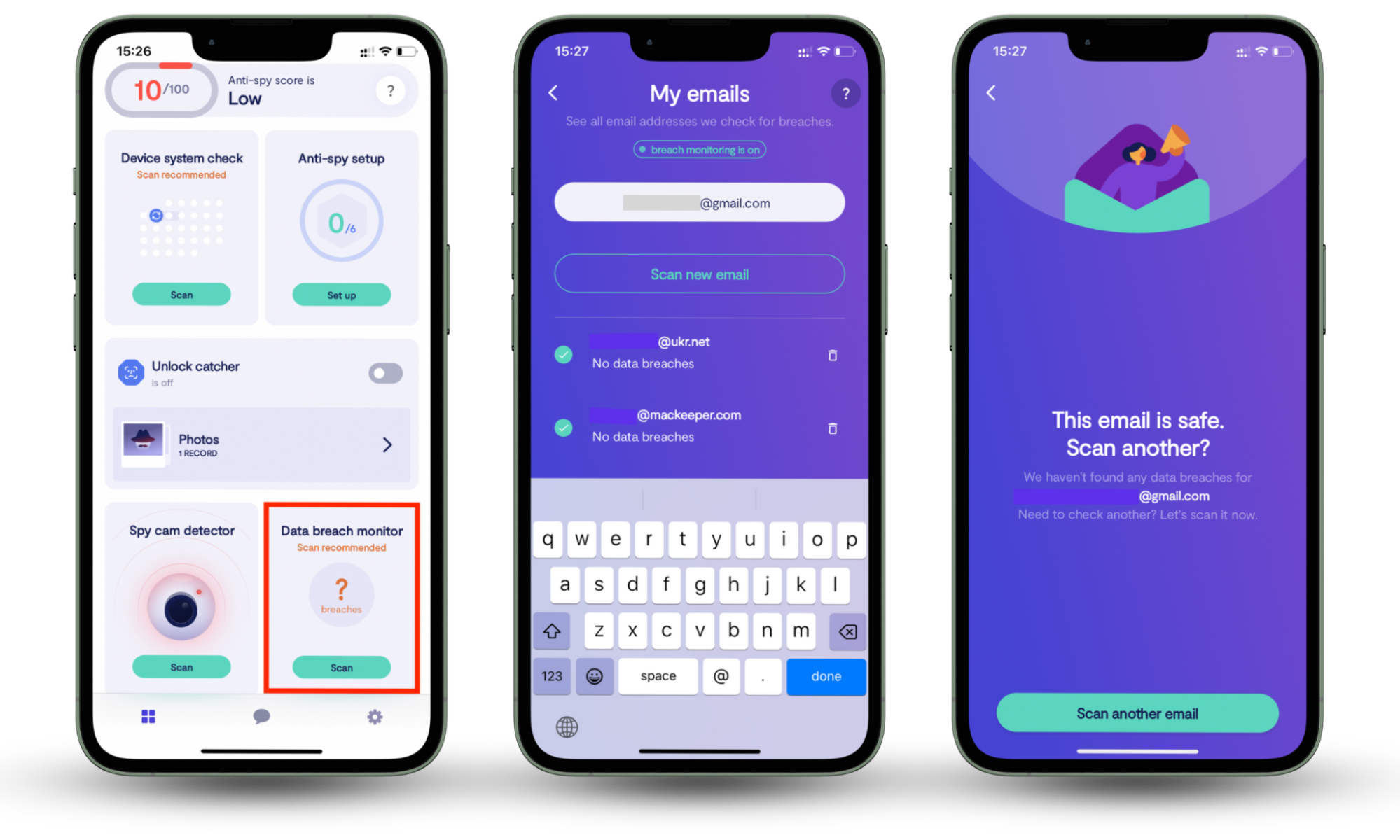
Clario Anti Spy also includes other powerful tools. For example, Device system check helps you detect security risks like hidden jailbreaks or device rooting, while Anti-spy setup walks you through securing your online accounts, web browsing, and social media for better overall privacy.
When should encryption be used?
There are two scenarios when data should be encrypted:
1. When data is ‘at rest’
Any time data is stored, it should be encrypted to ensure security. For instance, this could be on a removable storage drive or your computer’s hard drive. Responsible organizations will encrypt any data they store.
2. When data is ‘in transit’
Any time you send data from one place to another, there is a risk of interception by an unauthorized user. By encrypting data, you can minimize the adverse consequences of interception by scammers.
Everyday examples of data encryption
One of the earliest forms of encryption is known as ‘symbol replacement’, which was widely used by the militaries in Ancient Greece and Rome. The Caesar Cipher was a system where each letter in the original message or ‘plaintext’ was replaced by a letter situated a certain number of positions later in the alphabet. You might recall playing similar code-cracking games as a kid.
Of course, today, data encryption is far more advanced. Its use is also incredibly widespread and is likely protecting your data right now without you even being aware of it.
Some examples of common uses of encryption are:
- ATMs - every time you use an ATM the information is protected by encryption
- Online payments - your payment details are protected by encryption
- Encrypted web traffic - many websites encrypt your web usage by default. If you’re using a website with ‘https’ (the ‘s’ stands for ‘secure’) at the beginning of the address, your data is encrypted
- Messaging apps - messenger apps such as WhatsApp have enabled end-to-end encryption. If cybercriminals breach WhatsApp, they won’t be able to decrypt your messages
- Digital rights management systems - prevent the unauthorized use or reproduction of copyrighted content and protect software against reverse engineering
- Data ‘at rest’ - responsible organizations always encrypt data they store
While organizations usually encrypt vast quantities of any data they store, you might also want to encrypt the files and folders on your Mac. Our guide on data encryption for Mac will get you started.
Why is data encryption important?
Data encryption is an essential privacy safeguard. If someone gains unauthorized access to your encrypted data, they will not be able to read it or use it for malicious purposes. As such, data encryption functions as the final line of defense against cybercrime.
Encryption is important for data security because it can greatly reduce data breach damage. Given that no system is 100% secure, companies operating in healthcare, finance, education, and other critical industries are mandated to encrypt their data. For instance, the Health Insurance Portability and Accountability Act (HIPAA) requires healthcare providers to implement data encryption to protect patients’ health information.
Can encryption be hacked?
In short, yes. While decrypting an encrypted message would require considerable computational resources and skills, it’s still possible. However, given the resources required, it is very rare.
Is encryption safe?
Yes, encryption is incredibly safe. Most encryption standards offer a level of safety unmatched by other cybersecurity safeguards. Due to the technology’s incredible reliability, the AES 256 encryption standard is approved by the US National Security Agency (NSA). The overwhelming popularity of WhatsApp messenger, which since its creation in 2016 has delivered over 100 trillion encrypted messages, is another testament to the safety of encryption.
How to protect yourself where encryption doesn’t
Data encryption is a powerful tool in your security mix, but it’s important that you do have a mix and other tools to keep you secure. Don’t rely solely on data encryption, or any single measure alone to keep your data protected.
To protect your data, update your Mac regularly, adopt strong passwords, enable 2FA, avoid suspicious links, and use a VPN. A reliable VPN hides your online identity and serves as a second layer of encryption. Make sure the VPN you choose has a high user rating and a solid track record of respecting user privacy. Avoid free VPN services, as they can collect and sell your data.
Conclusion
Encryption is a great way to protect your data, but it's not fool-proof and it can be hacked. That's why it's important to take your security into your own hands. Using a VPN adds an extra layer of protection, and Clario Anti Spy takes it further with tools like the Data breach monitor to help keep your online accounts safe.


