Table of contents
- What is a white hat hacker?
- What are some other types of hackers?
- Key differences between white, black, and grey hat hackers
- Black hat hackers
- Grey hat hackers
- Red hat hackers
- How to become a white hat hacker?
- White hat hacker certification
- White hat hacker background
- Famous white hat hackers
- Conclusion
What is a white hat hacker?
A white hat hacker is hired to break into computer networks with the aim of finding loopholes or flaws in cybersecurity systems that other hackers could potentially misuse.
Insight
White hat hackers work with explicit permission from the organization they are testing. Their activities are typically authorized through legal agreements such as penetration testing contracts or bug bounty program rules, which define what systems can be tested, what methods are allowed, and how findings must be reported.
A cyberattack is simulated so it is similar to how a malicious hacker would behave. This way all the vulnerabilities are identified and then fixed.
Unlike real cyberattacks, these simulations are conducted in a controlled environment to avoid service disruptions, data loss, or privacy violations while still accurately reflecting real-world attack techniques.
Here’s everything white hat hackers are expected to do when hired by an organization:
- Identify threats from Open Ports
In the absence of a proper cybersecurity system, open ports can let hackers easily enter your system. White hat hackers scan these ports via third-party tools and recommend measures to make them safe against breaches.
This typically involves scanning systems to identify unnecessary or misconfigured ports that expose services to the internet and increase the risk of unauthorized access.
- Analyse patch installations
Threat actors can easily exploit patch installations. The white hats analyse them closely to minimize the threat.
White hat hackers check whether security patches are missing, outdated, or incorrectly applied, as unpatched software is one of the most common ways attackers gain access to systems.
- Employ social engineering
They often put social engineering methods in place to collect certain information. This way, they identify the steps hackers could take to access your system, then protect you against them.
These tests may include simulated phishing emails or phone calls designed to assess employee awareness, without collecting real credentials or sensitive personal data.
- Evaluate honeypots and firewall systems
White hat hackers also identify the weak points of the honeypot systems you have already set up. They try to find methods to evade firewalls, IDS, IPS, or honeypots so that they can put measures in place to prevent anyone else from doing the same.
The objective is to determine whether these security controls correctly detect suspicious behavior or can be bypassed using known evasion techniques.
- Protect networks
They try to recognize network-related security loopholes by performing network sniffing and hijacking your web servers.
This helps uncover issues such as insecure network protocols, exposed services, or insufficient traffic monitoring that could allow attackers to move within the network.
What are some other types of hackers?
Hackers can be good, evil, and everything in between. Let’s look at the different types they can be classified as, depending on the side they take.
Hackers are commonly classified based on intent, authorization, and legal status. While their technical skills may overlap, the key difference lies in how and why those skills are used.
Key differences between white, black, and grey hat hackers
- White hat hackers: Authorized by the system owner, operate legally, and focus on identifying and fixing security weaknesses.
- Black hat hackers: Act without permission, violate laws, and exploit vulnerabilities for personal, financial, or malicious gain.
- Grey hat hackers: Access systems without authorization but claim ethical motives, such as exposing flaws, even though their actions are still illegal in most jurisdictions.
Black hat hackers
A black hat hacker breaks into computer systems, steals important data, and manipulates or destroys entire systems. At times, they write malware that helps them break into these systems. The law ranks them as criminals who conduct hacking for evil reasons — usually to harm their victims.
Black hat hackers often target mobile devices, exploiting vulnerabilities in your mobile systems to steal personal data, gain unauthorized access to your device, and install harmful malware. They generally focus on vulnerabilities in popular operating systems like Android and iOS, compromise applications you use daily, and exploit network weaknesses to break through your security defenses.
As a result, you may end up with malware, viruses, and other harmful software downloaded on your phone without your knowledge, causing disruptions in device function, spying on you, or stealing your credentials for malicious purposes. To prevent this from happening, strengthen your mobile device's safety with Clario Anti Spy. It is a cybersecurity app we created to ensure a protected user experience in the online space.
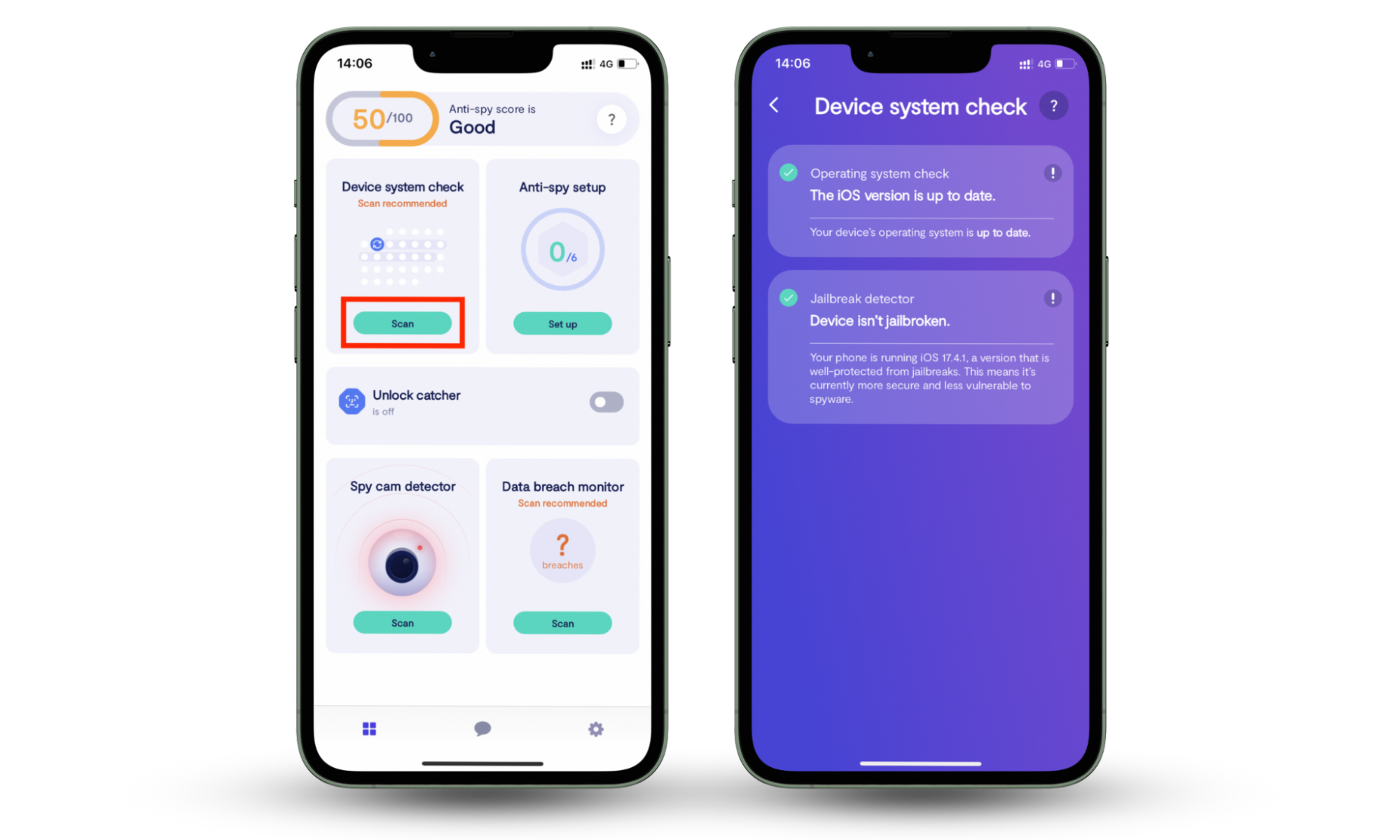
If you're an iOS user, try our robust feature Device system check. It will analyze your iOS for the most dangerous vulnerability— jailbreak. When an iPhone is jailbroken, it is easy for hackers to install harmful software and compromise your device’s safety. So, use Device system check to make sure your system is intact. It will also check if your iOS is running on the latest updates and security fixes.
Here’s how to use Clario Anti Spy’s Device system check on iPhone:
- Download Clario Anti Spy and set up an account.
- Go to the Device system check feature and tap Scan.
- The results of the scan will be shown under the Operating system check field and Jailbreak detector field.
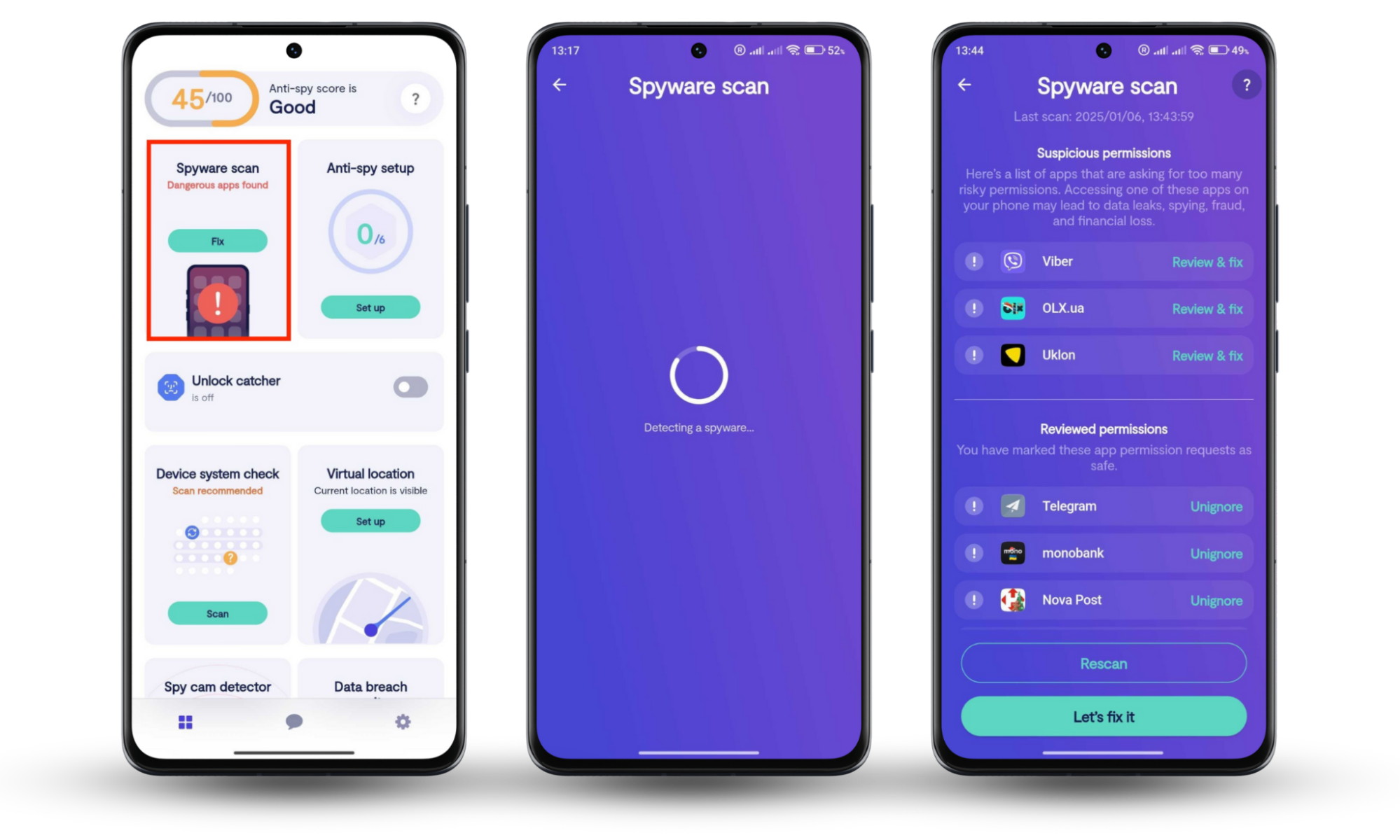
For Android users, we’ve created a Hidden app scan. With its help, you can thoroughly scan your mobile device, checking if any spying apps, like spyware or parental control software, have sneaked into your system. The feature will also take a closer look at app permissions, helping you spot suspicious ones.
Here’s how to use Clario Anti Spy’s Hidden app scanon Android:
- Download Clario Anti Spy and create an account.
- Locate the Hidden app scan feature and tap Fix.
- Wait for the results of the scan and tap Let’s fix it if issues are found.
Grey hat hackers
The grey ones lie somewhere in between good and evil. They hack into the computer systems of large corporations, inform them of the breach, then demand a certain amount of money to undo the damage and prevent future violations. Organizations sometimes don’t cooperate, and this situation turns into blackmailing and eventually black hat hacking. While grey hat hackers may hide their actions behind noble goals, their actions are still unethical and prohibited by the law.
Red hat hackers
These are the positive characters of the Linux world, but the way they operate is slightly different. You can call them the vigilantes of cyberspace who directly fight black hat hackers by destroying their systems, and in extreme cases, making their devices inoperable. A red hat hacker usually does this by planting different viruses or through Denial of Service attacks.
How to become a white hat hacker?
Becoming a white hat hacker requires a specific set of expertise, which could be backed by a few certifications making things official. You could obtain a certificate from the EC Council, or other similar institutes. Other than that, all that matters is how capable you are and how much effort you put into your work.
White hat hacker certification
- Certified Network Defender (CND)
This certification involves almost everything related to networks — right from the basics to intermediate and advanced levels. The major topics you get to understand and practice include network protocols, firewalls, traffic signatures, vulnerability scanning, private networks, etc.
- Certified Ethical Hacker (CEH)
The second certificate after a CND is the CEH program. The difficulty level is slightly higher here and you get to study the same concepts in a lot more detail. The things covered include network scanning, cryptography attacks, sniffing, SQL injections, internet of things, mobile applications, operating systems, footprinting, etc. Most of the skills required for white hat hacking are covered by now.
- EC-Council Certified Security Analyst (ECSA)
This certificate includes content related to penetration testing, which can be understood as a faux attack against your cybersecurity system to find out all the faults that can be used against you. To be an ECSA, you will need to master your pen-testing skills for wireless environments, networks, web apps, cloud software, databases, and social engineering systems. Besides, you will learn advanced level scans, security auditing and creating formal test reports.
- Licensed Penetration Tester (LPT) Master
This certification takes your penetration testing concepts to an advanced level. You get to apply advanced hacking methods such as privilege escalation, multi-level pivoting, SSH tunnelling, SQL injections, etc. To pass the exam, you will also need to handle exploitation related to various operating systems and host-based apps.
White hat hacker background
Having an IT-related degree helps a lot in white hat hacker training, but isn’t necessary. Ideally, you should study for a formal college degree, but shorter certifications and diplomas also give you the training and skills you need to start hacking.
- Basic scripting or programming knowledge to automate testing tasks
- Strong understanding of cybersecurity ethics and legal boundaries
- Ability to document findings clearly and explain risks to non-technical stakeholders
Other fields of study that give you an edge in becoming a white hat hacker are Computer Science, Information Security, or even Maths.
Some organizations also prefer to hire employees who have military experience, especially in the intelligence department. This could also have to do with military people already having security clearances.
Famous white hat hackers
Here are some of the most prominent white hat hackers from across the world:
- Tim Berners-Lee was the brilliant inventor and white-hat hacker who introduced URLs, HTML, and HTTP. During his time at Oxford, he was restricted from using the computer facilities as he was caught hacking into their system. Afterwards, he used his skills to create great, life-changing things such as the World Wide Web.
- Steve Wozniak is one of the founding partners of Apple, and worked very closely with Steve Jobs from the very first days of the tech giant. Wozniak and Jobs together developed the infamous ‘blue boxes’ which could hack into phone systems and allow users to make long-distance calls without any charge. This was during their college days, and eventually, both of them moved on to achieve amazing things later on.
- Kevin Mitnick started his career as a black hat hacker and hacked into some of the most influential companies in the world. He got into legal trouble and spent a few years in prison, after which he left black hat hacking and became a consultant. He also went on to write some important books on hacking later on.
- Tsutomu Shimomura is another cybersecurity expert who was responsible for Mitnick’s eventual arrest. He worked closely with the FBI and helped them track and locate black hat hackers who were on top of their game at the time. Shimomura was very good at it and helped arrest a lot of infamous hackers.
- Jeff Moss is an American hacker who helped start the first Black Hat Security Conferences. He also worked with the U.S. Department of Homeland Security as an adviser on cybersecurity-related issues.
Conclusion
With the development of new technologies every day, the threats and demand for protection are also snowballing. Larger organizations with a lot of sensitive data are already hiring white hat hackers to help them fight against such threats.
If you’re an individual mobile user and wish to strengthen the security of your mobile device, use Clario Anti Spy. This is a cybersecurity app with robust features for both iPhone and Android users. Use Device system check to check for jailbreaks (iPhone’s biggest threat so far) and Hidden app scan to check for malicious apps on Android. Keep your digital life safe!
Read More:


