Table of contents
- Types of man-in-the-middle attacks
- Rogue access point
- ARP spoofing
- DNS spoofing
- MITM attack phases
- Interception
- Decryption
- Examples of man-in-the-middle attacks
- Example 1: Accessing data through a fake website
- Example 2: Accessing funds through a fake chat service
- Detecting a man-in-the-middle attack
- 4 Ways to prevent MITM attacks
- Use secure connections
- Use a Virtual Private Network (VPN)
- Enable multi-factor authentication
- Educate yourself and your employees
Man-in-the-middle attacks occur when a hacker intercepts data passed along between two parties, e.g. you and a website or you and an app. The goal is to steal sensitive data, like passwords, credentials, banking details, etc., by impersonating either of the parties. They can also pass viruses and malware onto their victim’s devices.
The attacker generally falsifies a connection between the individual and the source in which they are looking for information. The “man-in-the-middle” can then observe the data a user passes through and even pass along their own data, like malware. A hacker uses this attack to steal sensitive user data and proprietary corporate information.
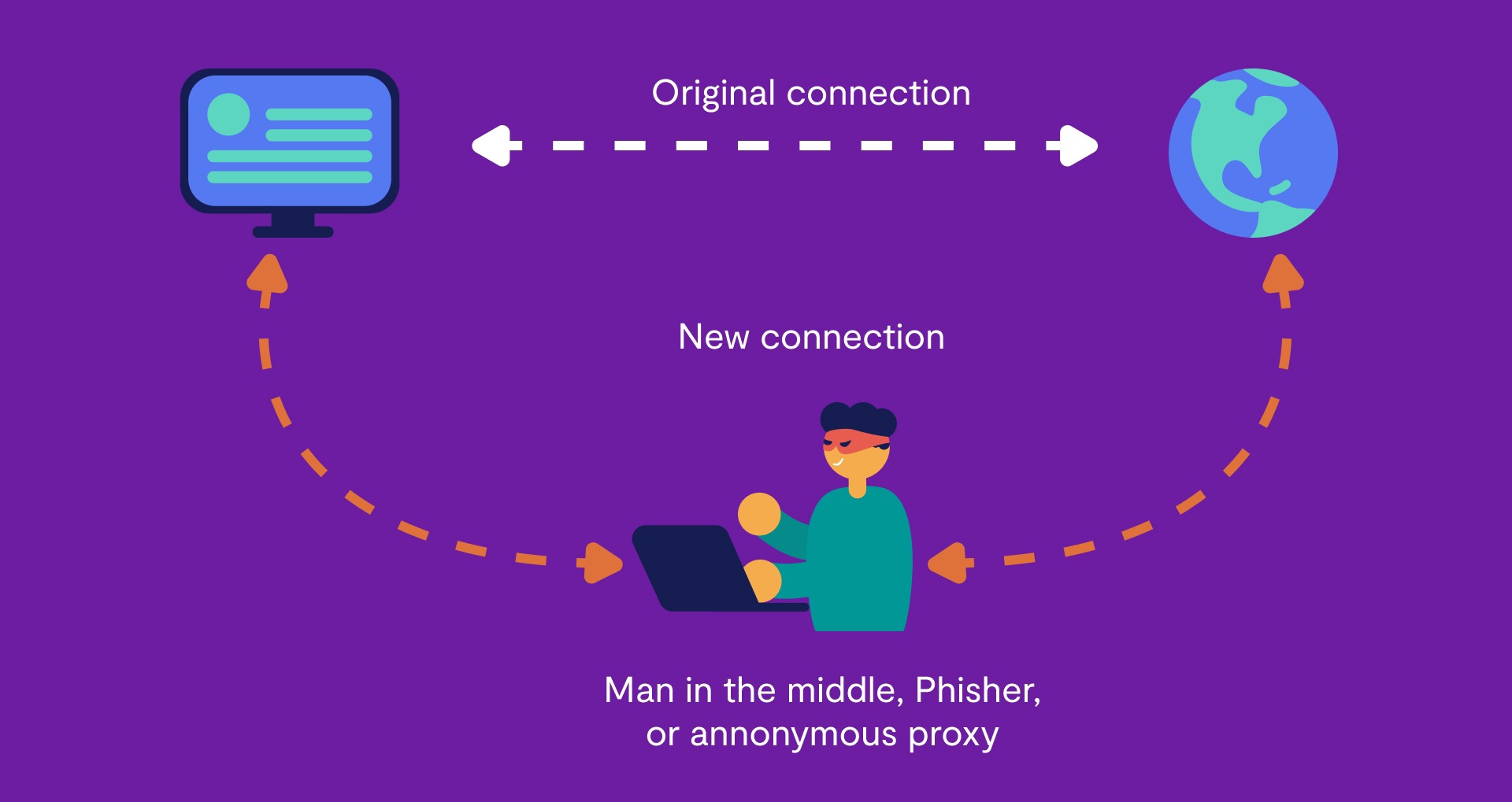
Types of man-in-the-middle attacks
There are multiple ways a hacker can set up opportunities for MITM attacks.
Rogue access point
Many devices connect automatically to Wi-Fi connections that produce the strongest signal. However, hackers can set up their own Wi-Fi access points to trick devices into joining it. This scam access point provides the hacker access to all of a user’s network traffic, meaning they can see the websites you visit and what information you are sharing. As a result, the hacker can steal sensitive information, like important logins, credit card data, and more.
A hacker doesn’t need to be on a trusted network to do this; they just need to be close enough to the victim’s device.
ARP spoofing
ARP (Address Resolution Protocol) is a procedure that connects an ever-changing IP address to a fixed physical machine address, also referred to as the media access control (MAC) address. This is how an internet router or local access network (LAN) makes sure it connects securely to your device.
ARP spoofing occurs when a hacker broadcasts false ARP messages to connect their MAC address to a legitimate server within the local network, allowing them to act as the host to which you are connecting. It is at this point that they can carry out a MITM attack.
Now that the hacker is acting as the host, they can see all communications you are sending out, the websites you are visiting, and the login information you use. The hacker can then access the sensitive information they need to steal from you or your company and even pass malware back to your devices.
Browse online safely
Learn how VPN works to protect your online activity
DNS spoofing
Domain Name Server (DNS) spoofing occurs when DNS records are altered and used to redirect online traffic to a malicious website that closely resembles the original website. Once victims reach the false website, the website will prompt them to log in, allowing the hackers to steal their information and install viruses on their computers.
MITM attack phases
Hackers generally go through two phases to carry out a successful man-in-the-middle attack: interception and decryption.
Interception
Hackers will first intercept the victim's traffic and pass it through the hacker's network before it reaches its intended destination. This interception commonly occurs through Wi-Fi connections, but as we've outlined above, there are multiple ways for a hacker to launch a MITM attack.
Decryption
Once traffic has been successfully intercepted, the second phase is to decrypt that data without alerting the user or the application.
Some ways that a hacker might decrypt two-way encrypted traffic are:
- HTTPS spoofing: Hackers will send a false certificate to the victim’s browser when the first connection request is made.
- SSL BEAST (browser exploit against SSL/TLS): This targets a vulnerability in the SSL, allowing the hacker to infect the victim’s computer with malicious JavaScript that intercepts encrypted data and compromises the website or app to decrypt the data.
- SSL hijacking: During this attack, the hacker passes forged authentication keys to the user and application, setting up what appears to be a secure connection.
- SSL stripping: This removes the secure certificate from a website so the hacker can send victims to an unencrypted version of the website, allowing the attacker to see the user’s entire session.
Examples of man-in-the-middle attacks
As you’ve seen so far, there are many ways that a hacker can execute a MITM attack. Here we’ll go over a couple of examples that you might come across in the real world:
Example 1: Accessing data through a fake website
How does the hacker do this? Let’s go over the steps:
- The attacker watches a network for insecure communications.
- When a user logs into a website, the attacker accesses their information and redirects them to a fake website that looks like the real one they were trying to access.
- The user unknowingly provides data to the fake website, allowing the hacker to collect and use this data on the real website to access sensitive information.
This example can occur in many ways, from accessing sensitive corporate information to gaining information for identity theft.
Example 2: Accessing funds through a fake chat service
MITM attacks are more than just fake websites and intercepting Wi-Fi connections. Hackers can also use these methods to set up false chat services. Let’s look at this example:
- A hacker creates a fake online chat service that mimics the victim’s bank.
- Let’s say the hacker used methods from the first example to collect data on the victim. They could then start a chat with the victim using that data to appear legit.
- In the conversation with the victim, the hacker collects enough information to go to the actual bank website and access the victim’s accounts and funds.
This example could also be used for customer support or IT-related chats to collect information to access other kinds of sensitive data. Users should enable two-factor authentication on all banking apps to help prevent losses like this.
Detecting a man-in-the-middle attack
It can be challenging to detect a MITM attack. If you aren’t actively taking measures to track and watch for the attack, it can go unnoticed until it’s too late. Detecting an attack like this usually involves implementing tamper protection and consistently checking for proper page authentication. But even then, the additional forensic analysis may be necessary afterward.
It’s better to try to prevent MITM attacks in the first place than to try to detect them as they are happening.
4 Ways to prevent MITM attacks
Follow these suggestions to protect your information from man-in-the-middle attacks.
Use secure connections
Ensure you are only accessing secure websites–those with HTTPS to indicate secure encryption. Also, make sure you are only accessing secure Wi-Fi and internet connections. Those are generally the first place attackers look for opportunities.
Use a Virtual Private Network (VPN)
A VPN is a great way to protect your online information because it encrypts your data. If a hacker finds a way to access your network, all of your data is encrypted, so they can’t see what information you’re sending or the websites you are accessing. A VPN also provides additional protection if you connect to public Wi-Fi networks.
Clario offers an unlimited VPN that allows you to access content from around the world and protect your data whether you are using your home network or public Wi-Fi.
To use Clario’s VPN:
To protect your outcoming traffic, which carries valuable information, from being out in the open for grabbing, encrypt it by using VPN. Follow these simple steps:
3. Go to your Clario app dashboard and toggle Browsing protection on
4. Choose the location you want to connect to the internet from
5. Done! Your data is encrypted.
6. You can also go to Network and toggle on the Auto VPN to stay safe on public Wi-Fi.
Enable multi-factor authentication
As we mentioned earlier, two-factor authentication is a great way to prevent hackers from stealing funds and other information hidden behind a login. Even in a hacker tricks you into handing over login information through a MITM attack, you can still add some safeguards with multi-factor authentication. When you enable multi-factor authentication on your private accounts, this adds another layer of security beyond your password. So, even if a hacker gets your password, they wouldn’t be able to get into your account unless they had access to your secondary authentication layers, like a text verification code or phone call.
Educate yourself and your employees
Whether you are an individual or a business, it’s essential to be aware of the different ways that hackers will try to access information so you can protect yourself and your data.
Businesses have become particularly vulnerable to cyber-attacks. Therefore, it’s important to educate your staff and employees on the dangers of MITM attacks and to help them implement best practices for good cyber security.
Have a plan to regularly provide information about cyber security to keep these things top of mind for your staff and remind them to keep up with these best practices.