Table of contents
- What is the Dark Web?
- What is a Dark Web Scan?
- What is Dark Web Monitoring?
- How to Find Out if my Data is on the Dark Web
- What to do if my Information is Detected in a Dark Web Scan
- 1. Change your passwords
- 2. Notify your financial services providers
- 3. Keep an eye on your credit card statements
- 4. Order your credit reports
- 5. Freeze your credit
- Protect Your Personal Information
Are you one of the +4 million Canva users who fell victim to a May 2019 security breach in which user passwords were stolen, decrypted, and shared online?
Perhaps you have fallen victim to a similar incident involving a security breach that landed your personal information on the dark web. It happens all too often, and the consequences are far-reaching.
For this reason, it’s advisable to perform a dark web scan to find out if your personal information is floating around the dark web, so you can act fast if needed. Continue reading to find out how.
What is the Dark Web?
The dark web is a subset of the internet that can go unnoticed by the everyday person. However, it is a real place with real implications.
Those in cybersecurity or privacy-related jobs are more familiar with the dark web. In fact, to them, it’s probably as familiar as the “normal” internet. But for the rest of society that doesn’t deal in those circles, it’s a whole new world.
To understand the dark web, you must first understand the various layers of the internet.
1. The surface web
The internet as you know it—search engines like Google and everything else you can search for and find on it, like this website—is known as the surface web. It’s easily accessible and commonly used for everyday activities.
2. The deep web
The next layer of the internet is the deep web, which consists of data that is used every day but can’t be found on the surface web. The platforms are available there, but not the data they house.
For example, you can access Netflix via a Google search, but you won’t find your login details and account information there.
3. The dark web
Finally, the dark web is the part of the internet that can only be accessed by those who know about it. This sort of secret world of the internet can only be accessed via a private browser known as the Tor Browser.
Just like the surface web, the dark web contains websites and communities. People can search the dark web, connect, trade on it, and so much more. But unlike the deep web, personal data can be shared on the dark web.
For example, the passwords obtained in the Canva breach were shared and probably sold to hackers on the dark web. The password to Canva itself does not carry any value. However, because a lot of people use the same password for many websites, hackers go ahead and try your email and password obtained from Canva on other, more strategic websites, like your password manager, Apple or Google ID, online banking, etc.
Here’s how hackers use leaked personal information:
- Blackmailing victims into sending them money by threatening to share whatever information they’ve obtained online, like intimate pictures
- Buying goods online using your credit card information
- Identity theft to scam others
- Taking out loans and credit cards in your name
Contrary to popular belief, the dark web isn’t all bad.
Legitimate sites, like Facebook, have iterations of their platforms on it. This allows people in countries where those sites aren't allowed to use those platforms.
However, bad actors also use it to share lists obtained through hacks and data breaches.
What is a Dark Web Scan?
Dark web scanning is exactly what it sounds like—it’s the process of scanning the dark web to find out if your information is available there.
Of course, no one would willingly and knowingly put their personal information on the dark web. You'd scan it if you suspect or know that your information was compromised in a breach.
You can use the Have I Been Pwned? website to do this. But it isn’t as effective as a dark web scan.
Because the dark web is such an intricate part of the internet, it’s best to enlist the help of an expert, company, or effective tool that can scan the dark web for you.
Some of the information they can look for includes:
- Social security numbers
- Credit and debit card information
- Medical records
- Website and app passwords and usernames
- Driver’s license information
- Passport information
- Phone numbers
- Fake qualifications
However, that doesn’t mean they’ll cover all the nooks and crannies of the dark web, as that’s impossible to do.
They’ll search leaked lists that are publicly available to users and communities of the dark web.
What is Dark Web Monitoring?
This is the next tier of scanning the dark web.
If a dark web scanner doesn't yield results, a dark web monitoring service can monitor and track your data on the dark web.
These tools use crawlers and scrapers to scan the dark web. Dark web monitoring services alert you if they pick up that your information has been leaked, so you can take action.
How to Find Out if my Data is on the Dark Web
If your data was stolen from a company's records, that company will notify you. This is usually done in the form of an email or a message on its website.
But you can’t depend on companies to contact you, especially because they don’t announce breaches immediately.
And by the time they do, your personal information is already up for sale on the dark web—or worse—being used for unthinkable activities.
Your best bet is to use a cybersecurity service to scan the dark web for data dumps containing your information.
Clario’s data breach monitor is an efficient and reliable tool that can determine if your information has been compromised within moments. The tool is found in the Clario app, which is compatible with Android, iOS, and macOS devices.
Here’s what it does:
- Conducts a dark web scan to determine if your email address is included in a data dump as a result of a data breach
- Notifies you if it is
- Prescribes a way forward, so you can take action by securing your email and protecting your data
Checking the dark web with Clario’s data breach monitor is a straightforward process and doesn’t take long to do.
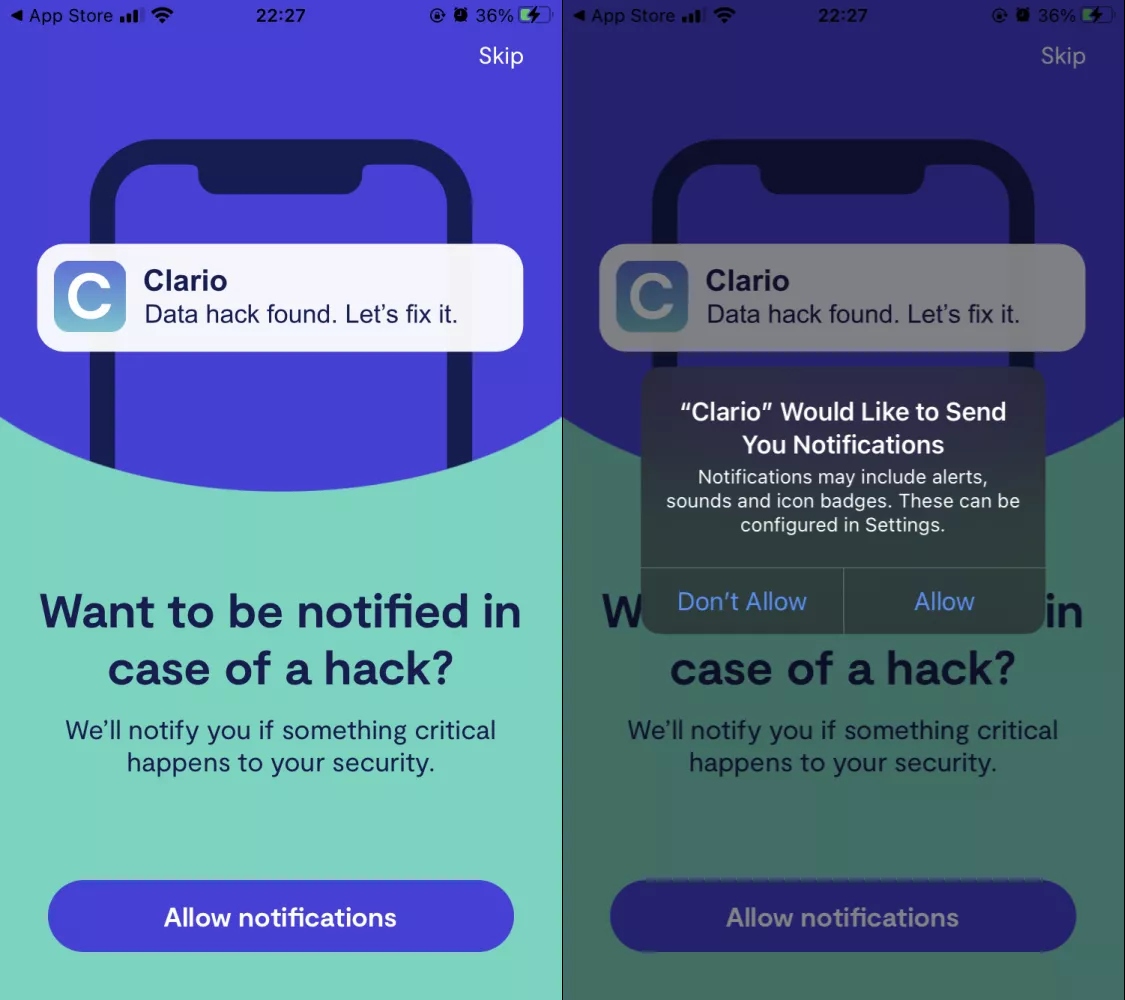
What’s more, when you install the Clario app, you have the option of choosing to be notified should your email address be involved in a known data leak. This helps you to act in real time if your data is ever compromised, thereby limiting any further damage that could be done.
To enable this feature, tap Allow notifications > Allow in the app.
Next, you’ll have to check if your email address has ever been listed as part of a leak as a result of a data breach.
- Open the Clario app on your iPhone or iPad and tap Data breach monitor
- Tap the Add email button, enter your email address, and select the Check button to start your search
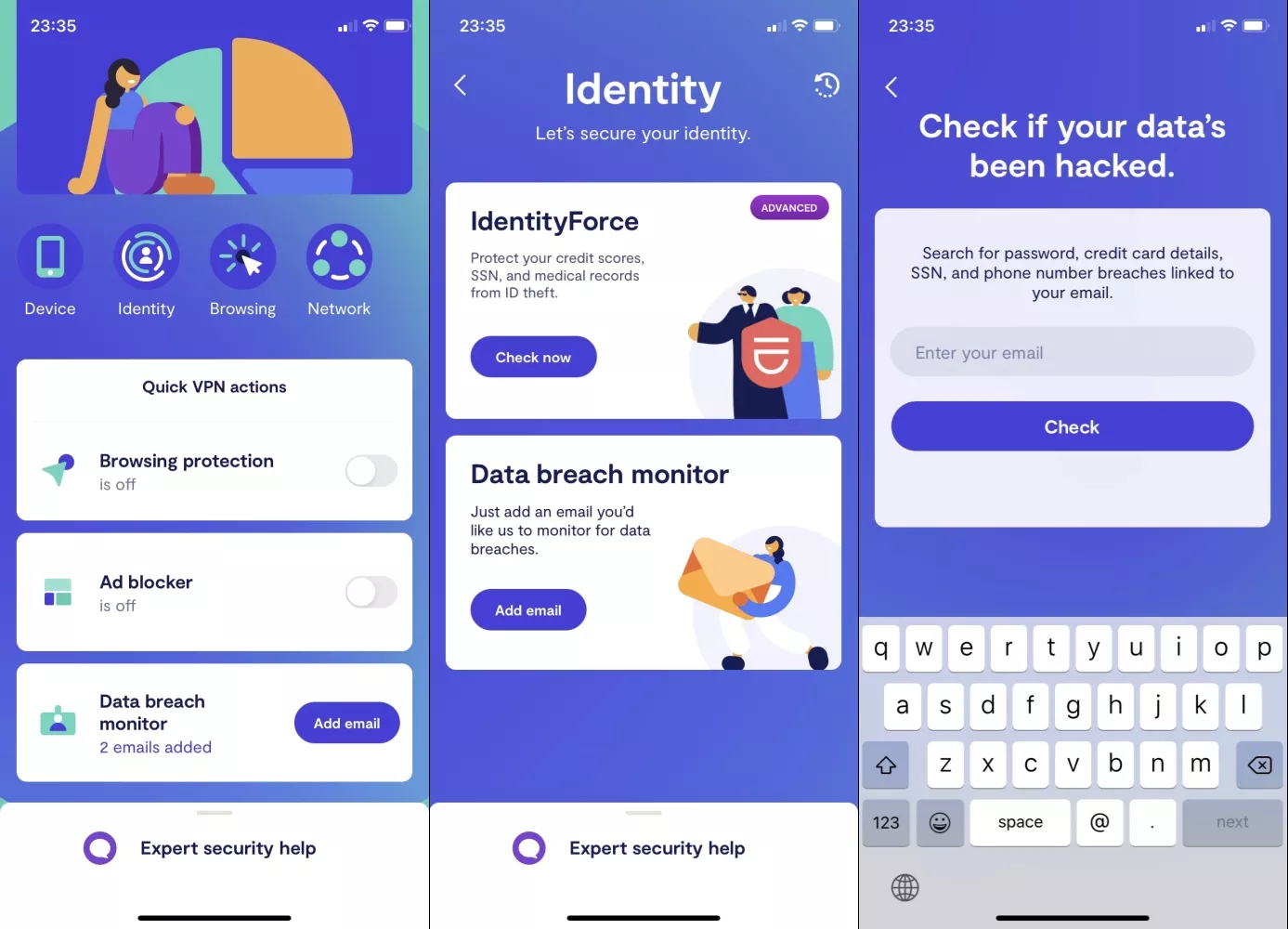
3. If a data breaches is found, it will be shown on the screen. Tap the breach to view more information about it
4. Follow the advice given under What should I do?
5. After you’ve actioned the steps prescribed, select Mark as fixed
6. If there is nothing to fix, simply tap Ignore
What to do if my Information is Detected in a Dark Web Scan
If you find out, through a dark web scan, that your email has been compromised, there are steps you should take to protect yourself on the dark web.
1. Change your passwords
This should be your first course of action after learning that your email address has been compromised.
Start with your email account, be it Gmail or another provider. Change the passwords for any other accounts you have, like…
- Streaming services (Netflix, Spotify, etc.)
- Payment platforms (PayPal, etc.)
- Social media (Instagram, Facebook, Twitter, etc.)
… and more.
Consider changing your Facebook privacy settings and settings for other social media platforms while you’re at it.
2. Notify your financial services providers
Let your financial service providers know what’s happened, so they can be on the lookout for any fraudulent or suspicious activity on your accounts.
If you have a private banker, get in touch with them, so they can help you put the necessary measures in place.
3. Keep an eye on your credit card statements
Next, you want to monitor your credit card statements for any irregularities carefully.
Go through your financial statements with a fine-tooth comb monthly to ensure that even smaller transactions don’t go unnoticed.
If you spot anything suspicious, contact your financial services provider immediately.
4. Order your credit reports
It’s easy for bad actors to get away with credit inquiries, purchases, and applications in your name because you don’t always receive notifications for these. Or, they can add their own contact details instead.
It’s not easy to rectify and restore your credit record, even if you can prove that you’re a victim of identity theft. It can take months, sometimes years.
That’s why you should order, view, or download your credit reports as often as possible. This ensures that you don’t find out about any fraudulent activity in your name when trying to get a bond or buy a car.
5. Freeze your credit
If you ever suspect or know for sure that you’re a victim of identity theft, freeze your credit immediately while you launch an investigation and get to the bottom of it.
Continue to monitor your finances over the next year or so to ensure you’re out of the woods.
Bad actors can take their time using your information for unsavory and illegal activities, and sometimes act when they think you’ve let your guard down.
Protect Your Personal Information
You can never completely prevent your data from being stolen. However, you can play your part by conducting regular dark web scans, so you can act fast if it is.
It’s also important to note that you can’t remove your information from the dark web. You can, however, protect yourself by changing your passwords.