Table of contents
- What is SpyNote?
- How SpyNote spreads: infection vectors and distribution
- SpyNote’s capabilities and functions
- Who does SpyNote target?
- How to detect SpyNote on your device
- How to protect yourself against SpyNote
- Conclusion
What is SpyNote?
SpyNote is a mobile malware that spies explicitly on Android devices. It’s a Remote Access Trojan (RAT), giving hackers full control over your phone from anywhere. First seen in 2020, this class of malware is now one of the most common types online.
What does malware mean? In short, it’s a type of malicious software that infects your device to do harm. If you’re still lost, find out the difference between malware and viruses.
Once installed, it turns your phone into a powerful surveillance tool. It can access your camera and microphone, capturing private moments. It can also steal your files and record every action you take, from typing messages to logging into accounts.
Recently, a client contacted Clario Anti Spy, suspecting his phone was compromised after his spouse seemed unusually aware of his private conversations and location.
Our tech support team specializes in helping users through sensitive privacy situations like this, providing expert guidance when digital security feels violated.
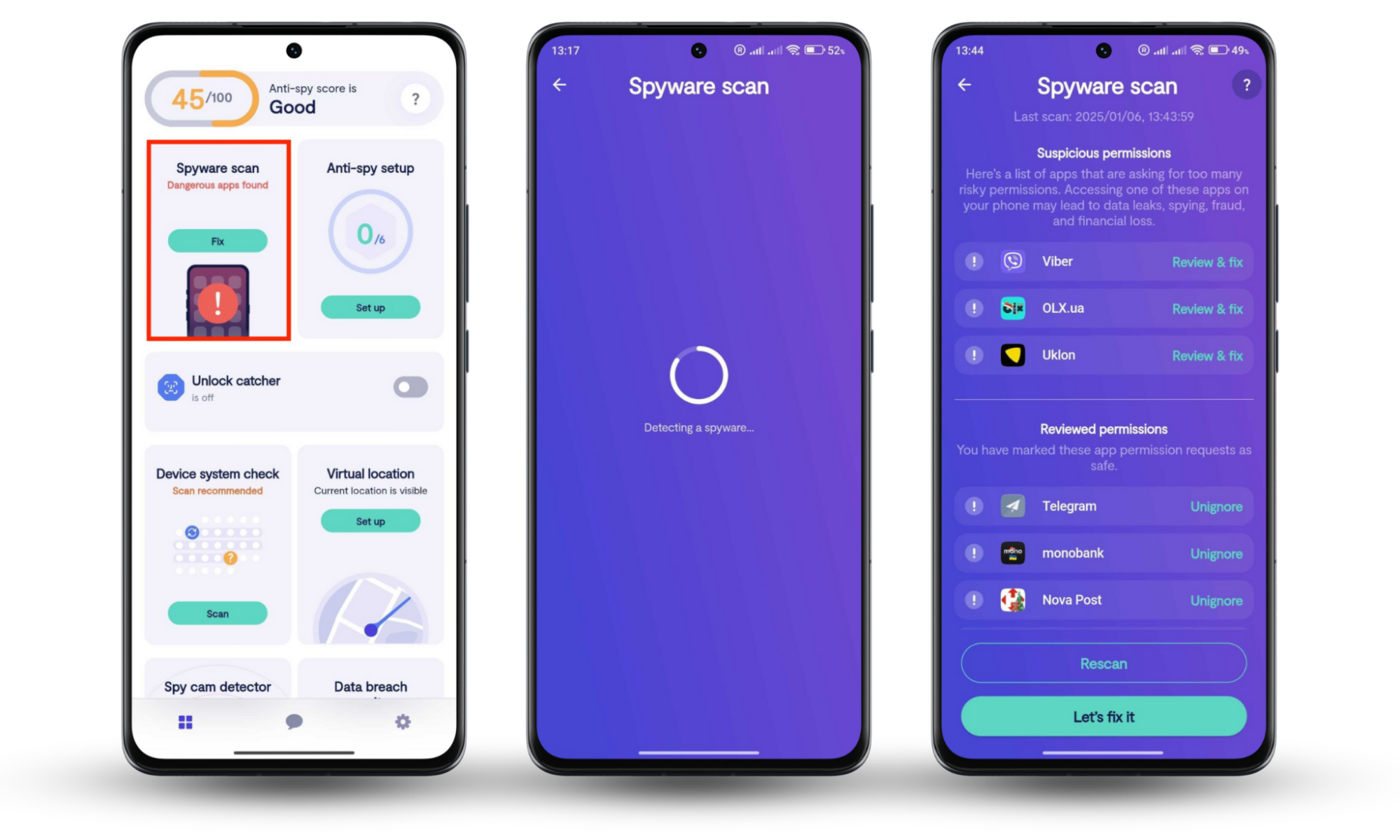
Our Spyware scan feature found suspicious apps he didn’t recognize, so support agent Fane guided him through removing these threats and securing his location permissions, restoring his privacy and peace of mind. If you suspect someone might be spying on you using SpyNote or other tracking tools, scan your phone yourself using Clario Anti Spy’s Spyware scan.
Use Clario Anti Spy’s Spyware scan (for Android) to find SpyNote:
- Download Clario Anti Spy from the Google Play Store and set up an account.
- Under Spyware scan, press Scan.
- Follow the instructions and wait for Clario Anti Spy to check your device for signs of spying apps. Press Review & Fix to update your phone’s permissions if it finds anything suspicious.
How SpyNote spreads: infection vectors and distribution
SpyNote uses social engineering to trick you into installing it through phishing, fake apps, and fraudulent APK files. Cybercriminals constantly change their methods, but keep an eye out for these:
- SMS phishing (smishing): Most SpyNote infections start with malicious text messages. These create urgency, like fake package deliveries or security warnings, to make you click a link and install the app from outside the official Google Play Store.
- Fake security apps: Attackers create convincing fake security apps. In 2024, researchers’ analysis found that SpyNote masqueraded as “Avast Mobile Security for Android” to deceive users.
- Fraudulent Google Play websites: SpyNote attackers set up fake websites that mimic the Google Play Store. These look nearly identical to the official site, complete with fake reviews and ratings, to trick you into downloading fake applications.
- Sideloaded APK files: Criminals also spread SpyNote through direct APK downloads from malware-infected sites and third-party app stores. These files claim to be cracked premium apps, but actually are SpyNote.
The key to SpyNote’s success is social engineering. Urgent, fake scenarios can make even cautious people vulnerable. If you’ve fallen victim, here’s how to remove malware from Android.
SpyNote’s capabilities and functions
Once SpyNote’s malware code infects your Android, it becomes a comprehensive surveillance tool. Here’s what SpyNote’s malware can do:
- Camera and microphone access: The malware remotely activates your device’s camera and microphone, capturing images and recording audio. It can take screenshots of everything on your screen using Android’s built-in features.
- Call recording: SpyNote records incoming phone calls as .wav files and sends them to the attacker’s device. It also monitors your call logs and can intercept communications.
- File theft and keylogging: The malware accesses your device’s storage to steal files. It performs comprehensive keylogging to capture passwords, messages, and other sensitive data.
- Screen monitoring: SpyNote captures constant screenshots to give cybercriminals real-time access to everything you do on your device.
- GPS location tracking: SpyNote can track location data and let attackers monitor your movements. They can build a profile of your daily routines and track any places you frequently visit.
- Contact harvesting: The malware steals your contact list, giving hackers access to your personal and professional networks. The hackers can then target your contacts with phishing and social engineering attacks.
- App monitoring: It tracks which applications you use, how often you use them, and your activity within specific apps, creating a detailed profile of your digital behavior.
- Device control functions: SpyNote even gives attackers full control over your device. They can remotely execute commands, install more malware, or use your device as part of a botnet.
Even worse, the information hackers collect automatically transfers to the attacker’s servers, where they can sell it or use it for identity theft and financial fraud.
Who does SpyNote target?
SpyNote’s Android malware targets a wide range of victims, including normal people, journalists, activists, corporate employees, and government officials. Recently, attackers have begun to increasingly target financial institutions and cryptocurrency companies.
Since the malware is so versatile, it’s easy for opportunistic cybercriminals and stalkers to try to attack people at random. But at the same time, sophisticated attackers can use it for high-value targets like companies and governments.
How to detect SpyNote on your device
SpyNote hides itself to avoid detection and uses “diehard services” on your Android phone that automatically restart if you try to shut them down.
Look for these warning signs to identify SpyNote on your device:
- Battery drain and performance issues: Your phone battery dies faster than usual, runs hot, or is sluggish because of SpyNote’s constant background activities.
- Unusual data usage: Because the malware uploads your calls, screenshots, and files to remote servers, you’ll notice sudden spikes in mobile data consumption.
- Unexpected permissions requests: The app will ask for access to your microphone or camera without clear reasons, suggesting that it’s trying to track you through greater accessibility.
- Slow app switching: SpyNote sometimes prevents users from getting to the app through the Settings menu. It’ll make your device unresponsive when you try to uninstall the app.
- Persistent services: You might notice mysterious programs running in your device settings. If you force them to stop, they restart immediately.
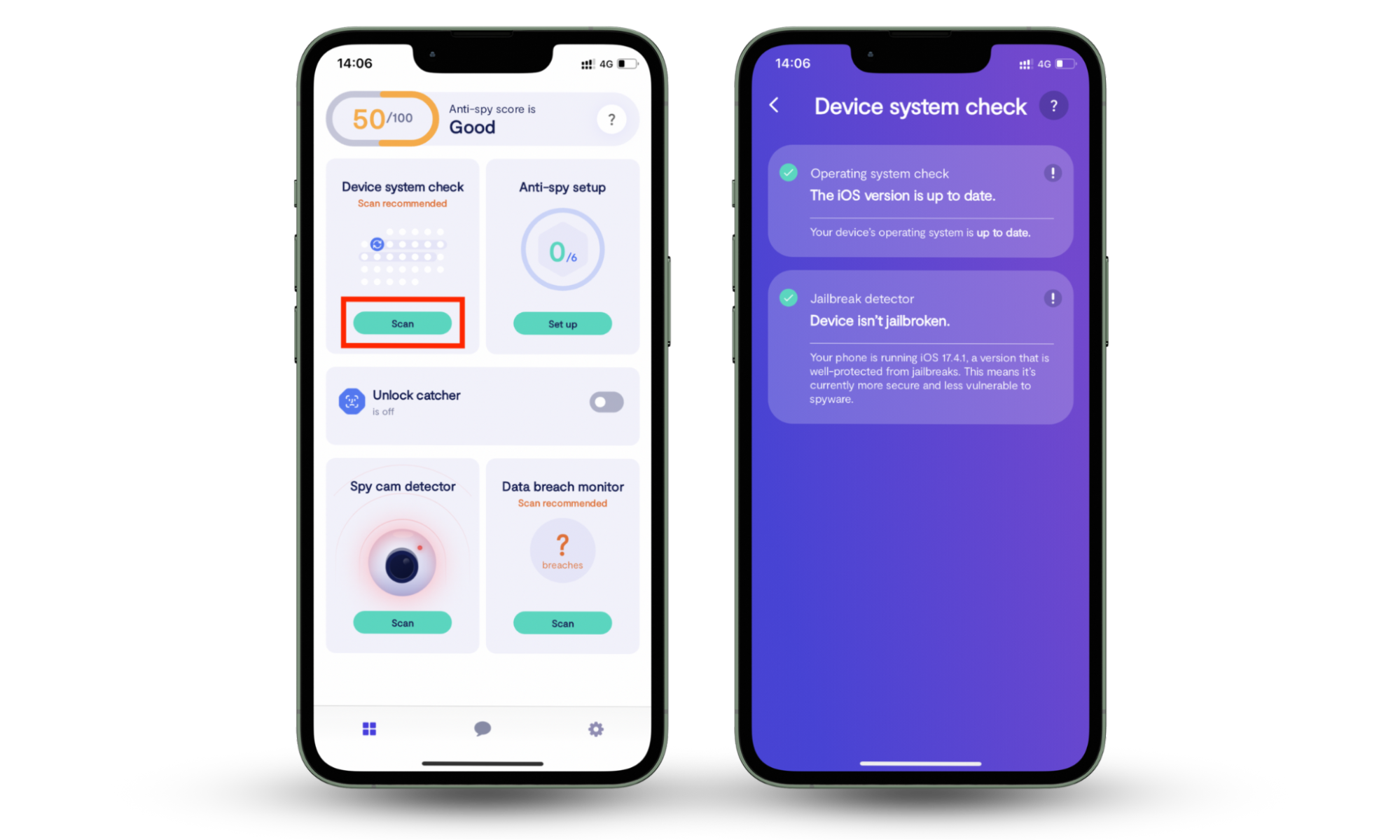
If you notice any of these symptoms, run a full scan using Clario Anti Spy’s Spyware scan. If you have iOS devices and you’re worried that malware has infected them too, use Clario Anti Spy’s Device system check to find out:
- Open Clario Anti Spy and find the Device system check option.
- Press Scan and wait for Clario Anti Spy to check your device for vulnerabilities and problems that can lead to an infection. Then, follow the instructions on screen to secure your device once and for all.
How to protect yourself against SpyNote
To defend against SpyNote, avoid installing unknown APKs and never install apps from third-party sources. You should also use a mobile antivirus like Clario Anti Spy, review your permissions regularly, and keep your operating system up to date.
Here’s how to protect yourself from SpyNote in more detail:
- Avoid unknown files: Never download apps from third-party websites, file-sharing platforms, or links in SMS messages. Stick to the official Google Play Store for all app installations.
- Disable unknown sources: Go to your security settings and disable Install unknown apps permissions for all browsers and messaging apps to prevent sideloading malicious apps.
- Use mobile security software: Install reputable antispyware solutions like Clario Anti Spy that can detect and block SpyNote before it infects your device. Run regular scans to catch hidden threats.
- Keep your system updated: Install Android security patches and system updates as soon as you can. They fix vulnerabilities that malware like SpyNote exploits to gain device access.
- Enable Google Play Protect: Google’s built-in malware scanner will scan apps that you download for threats. Enable it in the Google Play Store settings.
It’s also crucial that you know what a phishing attack looks like. Keep your eye out and avoid urgent links claiming package deliveries, security alerts, or banking notifications. Instead, contact the company through official channels.
Conclusion
SpyNote turns your Android into a surveillance tool that monitors everything you do. Now that you know how it spreads, you can avoid the SMS links and fake apps that deliver this dangerous malware.
Remember, basic security settings aren’t always enough protection against threats like SpyNote. Clario Anti Spy’s Spyware scan for Android detects and removes hidden malware before it compromises your privacy. Use Device system check for iOS to find signs your phone has been targeted so you can take action immediately.


