Table of contents
- How can someone get your phone number?
- What can hackers do with your phone number?
- 1. Forward your text messages and calls
- 2. Identity theft
- 3. SIM swap scam
- 4. Send you text scams and malware
- 5. Doxing
- 6. Target you with phishing attacks
- 7. Blackmail you using your sensitive data
- 8. Spam you with calls
- 9. Target you with phone scams using spoofed caller ID numbers
- 10. Prey on your family and contacts by spoofing your number
- How to protect your phone number against hackers
- 1. Use two-factor or multi-factor authentication (2FA/MFA)
- 2. Lock your SIM
- 3. Avoid clicking links from unknown senders
- 4. Ignore and block unknown callers
- 5. Never call back number from unsolicited text
- 6. Get fraud monitoring
- 7. Install antivirus software
- 8. Shred old documents
- Conclusion
How can someone get your phone number?
These days, it’s almost impossible to restrict your phone number to your closest friends and relatives. You’re forced to give it up to gain access to all kinds of products and services, which gives scammers so many opportunities to get hold of it. Here are the most common ways someone can get your number:
- Public records: Phone numbers are typically tied to public records, such as voter registrations and court records, and they are easily accessible with a quick Google search.
- People databases: There are many online databases that collect and sell our contact details to anyone who wants them, such as RocketReach, Whitepages, and ZoomInfo.
- Social media: Some people add their cell phone numbers to their social media profiles on Facebook, LinkedIn, Instagram, and more—particularly when promoting a service or business—without realizing that anyone can see it if they don’t lock down their privacy settings.
- Online forms: Whenever you fill out an online form that asks for your phone number, it’s handed over to a third party that can do whatever it chooses, and in many cases, our information is sold to advertisers and data brokers.
- Competitions and giveaways: Online competitions and giveaways almost always ask you to submit personal information, including your phone number. Although genuine competitions do exist, many are set up by scammers to steal data.
- Data breaches: One of the biggest causes of personal information leaks is data breaches. The average person has submitted their info to dozens and dozens of companies, and it’s inevitable that at least one of them will suffer a data breach eventually.
What can hackers do with your phone number?
Once they have your hands on it, what can hackers do with your phone number? Well, in addition to contacting you to conduct social engineering attacks to gather more information, they can quietly use your number to impersonate you, gain access to online accounts, and more.
Here are 11 ways scammers can use your phone number to exploit you for their own gain:
- Forward your text messages and calls
- Identity theft
- SIM swap scam
- Send you text scams and malware
- Doxing
- Target you with phishing attacks
- Blackmail you using your sensitive data
- Spam you with calls
- Target you with phishing attacks
- Prey on your family and contacts
- Spoof your number
If you’re trying to figure out can someone track you with your phone number, the answer is yet, but it’s not an easy feat. Instead, most scammers prefer to use easier exploits like those above. Let’s take a look at them in more detail.
1. Forward your text messages and calls
After obtaining your cell phone number, a hacker can attempt to forward all your calls and text messages to themselves. They’ll contact your carrier, claiming to be you, and ask to have all incoming communications rerouted to another number. They can then intercept everything that was en route to you.
Although this isn’t the easiest scam, it’s one of the most beneficial when it works. With access to your incoming calls and texts, a hacker can start breaking into your online accounts by having the password reset links sent to them by text—and they’ll receive all your two-factor authentication (2FA) codes as well.
2. Identity theft
With more than 365,000 incidents of identity theft in the US during the first quarter of the year alone, it’s likely 2025 will see a record number of ID theft victims. And your phone number is a scammer's gateway to all the information they need to impersonate you for financial gain.
By searching for your phone number in online databases, scammers will quickly find associated addresses, emails, social media, and other online accounts. Sophisticated hackers will also use social engineering attacks to trick you into handing over more, like your Social Security number and date of birth.
3. SIM swap scam
The SIM swap scam involves using the porting service offered by carriers to steal your phone number. Instead of simply forwarding your calls and texts, scammers will trick your carrier into sending them a replacement SIM card. If you’re wondering can someone clone your phone number, this is how they do it.
Once they have hijacked your SIM card, an attacker can intercept incoming calls and texts and send messages that appear to be from you. In the UK, Cifas found that SIM swap scams surged by more than 1,000% in 2024, and that trend is expected to continue throughout this year.
4. Send you text scams and malware
Text scams and malware have become some of the most common cybersecurity risks, and once attackers have your number, they’ll bombard you with messages in the hope that you’ll fall for at least one of them. They will employ a wide range of tricks, from asking you to confirm bogus payments to exciting job offers.
The main purpose of the messages is to trick you into handing over other sensitive information, such as an address they can use to steal your identity or payment details. Alternatively, they will send links that can infect your phone with malware, allowing them to download all the data they wish.
5. Doxing
Doxing or doxxing is when scammers post all the information they’ve collected on you online, allowing others to harass you or use the details for their own attacks. The info often ends up on the dark web where it’s significantly more difficult for the average person to find and remove.
6. Target you with phishing attacks
Phishing attacks are another form of text scam in which fraudsters claim to be reputable companies or organizations. They’ll send you messages that look like they’re genuine, typically asking you to confirm your password or submit information to protect your account.
More confident scammers will also conduct phishing attacks by phone. For example, they might call pretending to be a representative from your bank, claiming that someone is trying to access your account. They’ll say they want to protect your funds but can only help if you confirm your card details.
7. Blackmail you using your sensitive data
Some hackers will blackmail you to get what they want. First, they’ll use your phone number to obtain sensitive data or other content—such as private photos and videos—and then they’ll threaten to share everything publicly if you don’t agree to their demands, usually to send the hackers money.
8. Spam you with calls
Annoyingly, phone numbers are regularly sold to marketers, and some marketing firms constantly scour the web to find leaked numbers for free. If they get hold of yours, you’ll quickly find yourself bombarded by spam calls and texts trying to sell you products, offer you jobs, and more.
According to YouMail, a whopping 52.8 billion spam robocalls reached US citizens throughout 2024. That’s actually a decrease of 4.2% compared to 2023, but it’s still an average of 4.4 billion calls a month.
9. Target you with phone scams using spoofed caller ID numbers
More sophisticated fraudsters use fake or spoofed caller IDs to trick you into thinking they’re legitimate companies, organizations, or government agencies like the IRS. This makes you feel like you can trust them but don’t—they’re only interested in obtaining more information or stealing your money.
10. Prey on your family and contacts by spoofing your number
Some scammers won’t use your number to exploit you; they’ll prey on your friends and family instead. After taking over your number, they’ll text your contacts pretending to be you with the sole purpose of obtaining money from someone who believes they’re helping you out.
The scammer will claim they’re in urgent need of cash. They might say they’ve broken down somewhere and need a ride or that they’re in a store buying groceries, and their card got declined. The hope is that one of your friends will fall for the sob story and send money, thinking that they’re saving you.
How to protect your phone number against hackers
You can’t stop third parties from selling or leaking your phone number, but you can secure your phone number from hackers by following these steps:
- Use two-factor or multi-factor authentication (2FA/MFA)
- Lock your SIM
- Avoid clicking links from unknown senders
- Ignore and block unknown callers
- Never call back number from unsolicited text
- Get fraud monitoring
- Install antivirus software
- Shred old documents
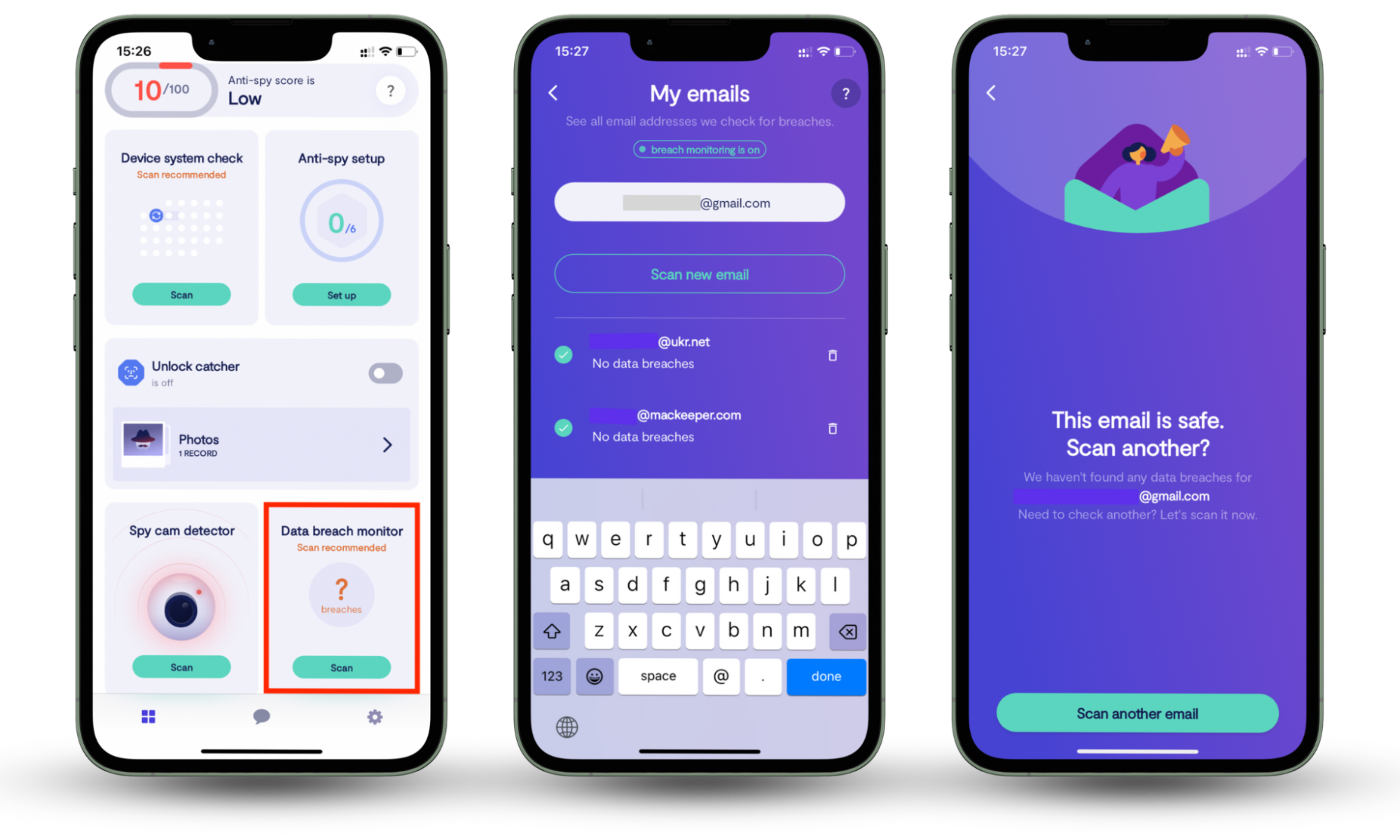
One of the best ways to tackle dangers like identity theft and credit fraud is by using Clario Anti Spy’s Data breach monitor on Android and iOS. It alerts you immediately if any of your email addresses appear in a data breach so you can take steps to protect yourself right away. Here’s how to use it:
- Download and install Clario Anti Spy for Android or iPhone.
- Under the Data breach monitor, tap Scan.
- Check to see if any of your emails are part of a data breach.
1. Use two-factor or multi-factor authentication (2FA/MFA)
Two-factor or multi-factor authentication (2FA/MFA) adds an additional layer of security to your online accounts, making it more difficult for someone else to log in—even if they know your username and password. We recommend enabling this feature wherever it’s available.
2. Lock your SIM
Most phones allow you to set a SIM lock or SIM PIN inside the carrier settings menu. This prevents someone from using your SIM card inside another device should they get hold of it.
3. Avoid clicking links from unknown senders
Many scams require you to click a link inside a text message, which takes you to a website that steals your details or infects your device with malware. Guard against them by not opening links from unknown and untrusted senders.
4. Ignore and block unknown callers
Scammers often call you to conduct social engineering or phishing attacks, and you can easily avoid them by not answering the phone to unknown callers. Better yet, use the blocking features built into all modern smartphones to prevent future calls from numbers you don’t recognize.
5. Never call back number from unsolicited text
If you get an unsolicited text message asking you to call a random number, it’s best to ignore it. Scammers use this tactic to try and persuade you to give up personal information, or to trick you into calling premium rate numbers that lead to large bills.
6. Get fraud monitoring
Fraud monitoring services will notify you whenever suspicious activity appears on your credit report. This means that if a scammer attempts to take out loans, credit cards, and other financing using your identity, you’ll know about it as soon as it happens.
7. Install antivirus software
Hackers will try anything to get you to download malware and viruses—including sending you malicious links via text message. If you want to know how to find out who hacked your phone, it’s not easy—but you can use antivirus software on your devices to remove and block threats before they can do any damage.
8. Shred old documents
Old credit card statements, bills, and other documents containing personal details are incredibly valuable to someone looking to steal your identity. Shred old documents as soon as they’re no longer needed to prevent sensitive information from making its way into the wrong hands.
Conclusion
Your phone number is a gateway to fraudsters who want to scam you and steal your identity. They can use it to find out more about you, bombard you with spam and malicious links, and to trick your friends into handing over cash. But using the tips above, you can protect yourself against common hacks and scams.
To receive alerts as soon as your email addresses appear in a data breach, try Clario Anti Spy’s Data breach monitor on Android and iOS. It trawls the web to find leaks associated with all the emails you use so that you can take preventative steps before you become a victim of ID theft.


