Table of contents
- Understanding IMSI Catchers
- How IMSI Catcher works
- Overview of IMSI Catcher attack
- 1. Communication interception
- 2. Location tracking attacks
- 3. LTE CSS connection methods
- 4. Denial of service and downgrading
- Can you detect iMSI catcher
- Conclusion
Understanding IMSI Catchers
The basic IMSI catcher definition is that it's a fake base station used to intercept mobile phone signals to steal information. They're often used in surveillance or sting operations to track someone's location and see who they're talking to. Because they are sneaky and hard to detect, IMSI catchers pose a serious risk to personal privacy and security.
IMSI catchers are often used by law enforcement (learn how the police can track a phone number), but they can also be abused by hackers, stalkers, or authoritarian regimes.
How IMSI Catcher works
IMSI catchers work by taking advantage of the trust mobile phones place in nearby cell towers. These devices mimic real towers and broadcast a stronger signal, hoodwinking nearby phones to automatically connect to them.
Once connected, IMSI catchers can collect sensitive data including:
- IMSI (International Mobile Subscriber Identity): A unique number tied to your SIM card.
- IMEI (International Mobile Equipment Identity): Your phone's hardware identifier ID.
- Metadata: Information like call logs, message timestamps, and phone numbers.
There are two main ways IMSI catchers operate:
- Passive listening: The device silently gathers information like IMSI numbers and your location.
- Active manipulation: More advanced versions can intercept calls and texts, inject fake messages, block calls, or downgrade your connection to 2G so that encryption is weak or missing.
Unless you're a high-profile individual, worried about being targeted, or participating in protests where IMSI catchers are used by law enforcement, you're probably not at risk from these devices. But that doesn’t mean your privacy is safe—more common threats like hidden cameras and wireless spying tools are still a major concern.
That’s where Clario Anti Spy comes in. It’s an anti-spyware app designed to help protect your privacy, and includes a Spy cam detector that can notify you if there’s a hidden camera or wireless gadget nearby monitoring you without permission.
Here’s how to use the Spy cam detector feature in Clario Anti Spy:
- Download Clario Anti Spy and subscribe to create your account.
- Tap Scan under Spy cam detector.
- Wait for the scan to complete.
- If something shows up under the Suspicious Devices section, tap it and follow the on-screen steps to identify the device.
- If you need help, tap the Messages icon on the main screen to chat with a security expert 24/7.
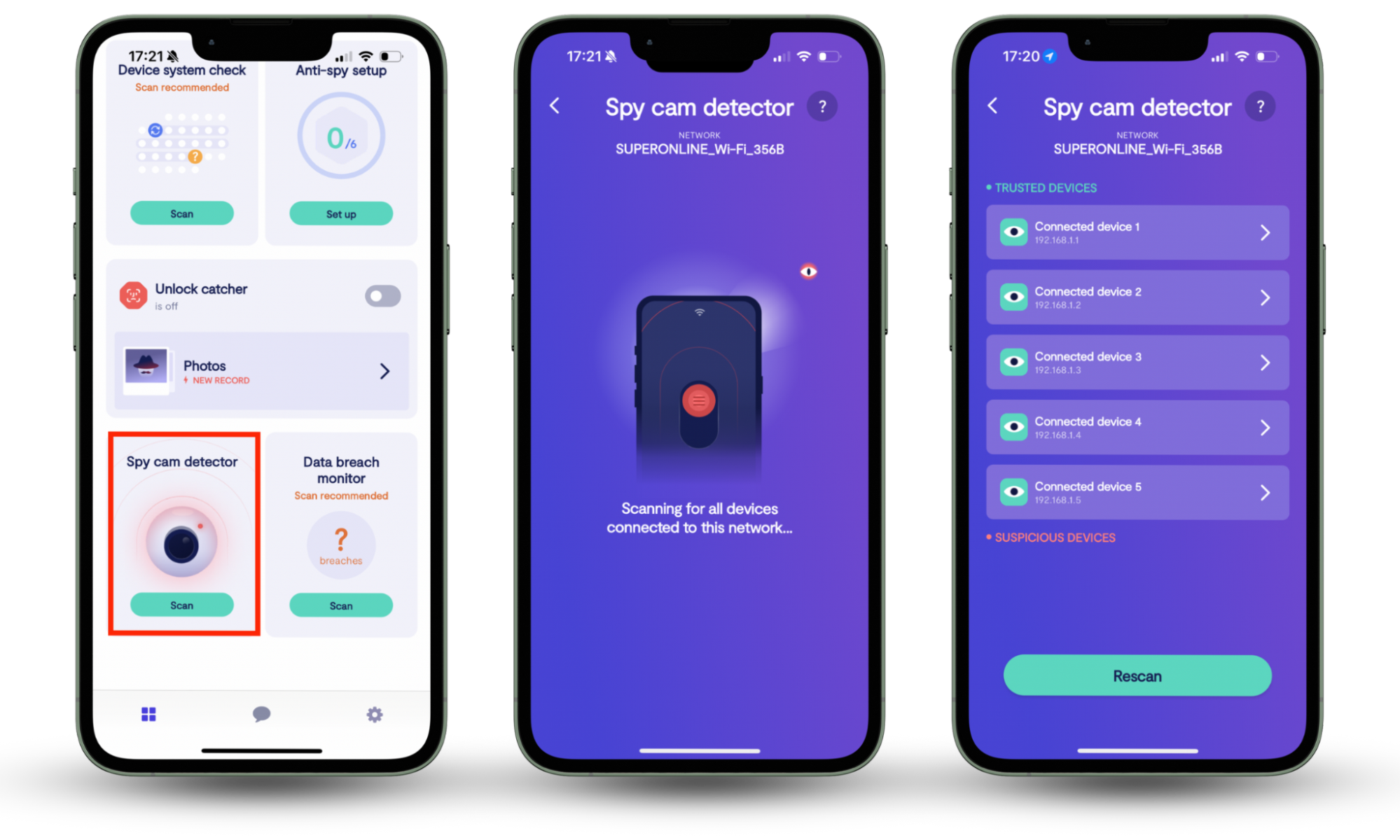
Other privacy tools built into Clario Anti Spy include the Anti-spy setup, which walks you through the basics of strengthening your privacy settings, and the Device system check, which detects if your phone has been jailbroken or has hidden root access. There's also a Data breach monitor that alerts you if your personal information is exposed in a breach, and an Unlock catcher records anyone trying to unlock your phone.
Overview of IMSI Catcher attack
What does an IMSI catcher attack mean? Once a phone connects to a fake base station, law enforcement (does the FBI track your phone?) or the bad actors behind the attack can intercept data, track your location, or mess with your network access. Common tactics include forcing a 2G connection, stealing device IDs, and logging calls and texts. The scariest part is how hard it is to detect IMSI catchers—most victims never realize anything's wrong.
1. Communication interception
When a phone connects to an IMSI catcher, attackers can monitor or manipulate your communications. This usually involves forcing your device to fall back to using 2G, which comes with serious security flaws. Here's why that's a problem:
- 2G networks use outdated encryption—on none at all—making it easy for attackers to eavesdrop.
- They can intercept SMS messages, log call metadata (like who you contacted and when), and in some cases, listen in on voice calls.
- Some advanced IMSI catchers can even inject or alter messages, turning them into phishing attempts or tools for spreading misinformation.
2. Location tracking attacks
IMSI catchers can also be used to track a phone's real-time location. Here's how it works:
- When your phone connects, the IMSI catcher can measure the signal strength and use triangulation (with one or more antennas) to estimate your location.
- Some attackers use silent SMS—invisible text messages that trigger a response from your phone without you knowing. This helps confirm your phone's location.
- Both law enforcement and bad actors can move the IMSI catcher around to follow your movements, even if you're not making calls or using mobile data.
3. LTE CSS connection methods
Modern IMSI catchers aren't limited to old-school 2G networks—they can also exploit weaknesses in LTE and 4G networks. Here's how:
- CSFB (Circuit Switched Fallback): When you make a voice call over LTE, your phone may briefly switch to 2G or 3G to complete the call. Attackers use this moment to downgrade encryption and intercept your data.
- Silent SMS: These are invisible messages that force your phone to ping its location.
- LTE control plane exploits: Some advanced IMSI catchers abuse LTE control messages to trick phones into responding to fake paging or handover commands. While LTE uses encryption, attackers exploit protocol switching and unencrypted metadata exchanges to gain access.
4. Denial of service and downgrading
IMSI catchers can do more than just spy on your phone. They can also disrupt your connection and make it less secure. For instance, this could involve:
- Denial of Service (DoS): Attackers can block your phone from connecting to real towers, cutting you off from calls, texts and mobile data completely.
- Forced downgrade: Even if you're on 4G or 5G, the IMSI catcher can force your phone to switch to 2G or 3G, which use weaker or no encryption. This makes it much easier to intercept your voice and text communications.
- Connection manipulation: Some IMSI catchers can repeatedly kick devices off the network to drain your battery or force your phone to connect to a specific tower for easier tracking.
These types of attacks can even block emergency calls or prevent important messages from getting through, making them dangerous in high-risk situations.
Can you detect iMSI catcher
IMSI catchers are extremely hard to detect. They mimic real cell towers and don't trigger any system alerts, which means your phone has no way of telling it's connected to a fake tower. These devices are designed to blend in seamlessly with legitimate infrastructure, making detection nearly impossible without advanced tools.
That said, there are a few warning signs you can watch for:
- Sudden signal drops or unexpected switches to 2G
- Texts or calls are not going through
- Trouble making encrypted calls or using mobile data securely
- Fast battery drain triggered by repeated disconnections and reconnections to the cellular network
- Strange delays or echoes during calls
There are Android apps like SnoopSnitch and Cell Spy Catcher that can detect fake base stations, but their accuracy is limited, and they aren't fully reliable. More effective detection methods—such as hardware-based tools or network anomaly scanners—are usually only available to researchers or law enforcement.
Cloned SIM cards are another serious privacy issue. Make sure that you also know if someone is using your SIM card.
Conclusion
IMSI catchers are one of the most silent and dangerous threats to mobile privacy. By imitating legitimate cell towers, they can intercept calls, track your location, and collect sensitive data—all without your knowledge. That said, unless you have strong reason to believe you're being spied on, this isn't something you need to stress about daily. For everyday protection, installing Clario Anti Spy can give you peace of mind from more common threats like monitoring tools, online threats, and hidden cameras.


