Table of contents
- What are biometrics?
- Biometric identification
- Biometric authentication
- How does biometric security work?
- What is biometric security used for?
- Single sign-on (SSO) and healthcare
- Banking
- Smartphone security
- Types of biometrics for security and authentication
- Facial recognition
- Optical recognition
- Vein recognition
- Voice recognition
- Handwriting recognition
- Is biometric security safe?
- Advantages of biometric security
- Disadvantages of biometric security
- How to protect biometric data?
- How organizations should protect biometric data
- How you should protect your biometric data
- Is biometric security here to stay?
- Conclusion
Computer and smartphone users in 2021: “Who needs biometric security? We’ve gotten so good at creating unique and strong passwords!”
Hackers, exposing 8.4 billion passwords in 2021: “Yeah, don’t worry about it, you’re totally fine!”
Google’s 2021 Changing Tech Behaviors & Online Safety report says searches for “password strength test” went up by 300% in 2020. The world’s largest email service provider has even published a seemingly innocent blog post, announcing it will soon require two-step verification from many of its users.
According to Verizon’s 2021 Data Breach Investigations Report (DBIR), 80% of breaches occur because of compromised or weak passwords. Someone out there knows exactly how your brain works, so unraveling the mystery of “JohnDoe123” only takes a minute.
Although these figures come from 2020 and 2021 reports, more recent industry research continues to show that weak or stolen passwords remain one of the most common causes of account compromise worldwide in 2026.
Are you a regular reader of Clario’s digital wellness blog? Then you must feel safe knowing how to create a strong password and why it is essential.
But imagine you could create a unique password you didn’t have to remember, one that would always be with you and could never be stolen? Many believe biometric security can provide all of this to make our accounts more secure than ever before. So let’s get down to it.
What are biometrics?
Definition
Biometrics is the use of a person’s unique physical or behavioral traits — such as fingerprints, facial features, or voice — to identify them or confirm that they are really who they claim to be.
Biometrics refers to metrics or measurements related to human features or characteristics. They can be broken down into two types:
- Physiological measurements: Fingerprints, hand shape, vein pattern, iris or retina shape, or face shape.
- Behavioral measurements: Voice, handwriting or signature dynamics, keystroke dynamics, gait, or gestures.
Biometrics can be used to answer two slightly different questions about a person:
- Who are you? (biometric identification)
- Are you who you say you are? (biometric authentication)
Can you see the difference? Here’s a deeper explanation.
Biometric identification
Biometric identification compares a person’s biometrics with those in a database to find a match and positively identify an individual.
A good example of this is how law enforcement keeps DNA in its database, then compares it to the DNA of any unidentified suspects to answer a key question: “Who left this DNA at the crime scene?”
Biometric authentication
Biometric authentication is a process of comparing an individual’s biometric data to the validated authentic data stored in a database to answer another key question: “Are you really who you say you are?”
For example, if you set up a fingerprint login on your smartphone, your device will ask you to capture and store your fingerprint pattern. Each time you log in using fingerprint authentication, your device will check your fingerprint pattern against the saved data and verify your identity.
In practice, biometric authentication is generally considered safer for everyday consumer devices than biometric identification. Authentication systems only compare your biometric data against your own stored template, rather than searching through large databases of other people’s data. This reduces privacy risks and limits the impact if a system is compromised.
The table below highlights the key differences between biometric identification and biometric authentication, showing how they are used, how data is compared, and why authentication is generally preferred for everyday consumer security.
| Aspect | Biometric Identification | Biometric Authentication |
| Primary purpose | Determines who a person is | Verifies whether a person is who they claim to be |
| Data comparison | Compared against many records in a database | Compared only against the user’s stored template |
| Typical use cases | Law enforcement, border control, large databases | Smartphones, laptops, banking apps |
| Privacy impact | Higher, due to large-scale data searches | Lower, due to one-to-one matching |
| Common risk | Mass data exposure if database is breached | Limited exposure tied to individual accounts |
How does biometric security work?
So, could biometrics and, in particular, biometric authentication, actually replace traditional passwords and transform how we access our accounts and devices? After all, we have passwords for everything these days.
The first thing we need to understand is what's involved in a biometric system.
A biometric security system is made up of three components:
- A sensor — to read your biometrics
- A computer — to store your biometrics
- Software — to connect the computer with the sensor
Sounds relatively simple.
At a high level, biometric authentication usually follows a simple process:
- The sensor captures a biometric input, such as a fingerprint or facial scan.
- Software extracts unique features from that input.
- These features are converted into a secure biometric template.
- The system compares the new template to the one stored during enrollment.
- Access is granted or denied based on how closely the templates match.
And it kind of is!
The use of biometrics has ramped up for many reasons — increased public acceptance, improved technological accuracy, and greater affordability of sensors, computers, and software.
Technology once used only by the military or law enforcement is now cropping up in all aspects of our everyday lives.
What is biometric security used for?
If you haven’t already, you’ll soon notice biometric security systems appearing more and more as you go about your daily business. Typical use cases range from unlocking your smartphones or laptops for regular browsing or work to authentication in banking or retail apps.
Here are some examples of where you’ll see biometrics in use today.
Single sign-on (SSO) and healthcare
Single sign-on (SSO) is an authentication service allowing a user to log in with a single ID and password to any of several related but separate software systems.
For example, your Google username and password can log you into your Gmail, and also to YouTube, Google Drive, Google Calendar, and so on.
That’s one powerful login ID.
SSO is also widely used in healthcare services to allow healthcare providers to access multiple systems quickly and easily. However, healthcare is also among the most vulnerable industries when it comes to data breaches — data breaches in healthcare spiked 55% in 2020. There’s particular urgency in the healthcare sector to utilise biometric SSO, taking advantage of the speed and security it offers.
While this figure reflects a specific period, in 2025, healthcare organizations remain a frequent target for cyberattacks due to the sensitivity and value of medical data.
Banking
Banking customers are tired of worrying about identity theft and having to prove their identity every single time they want to access their account.
Therefore, demand for banks offering biometric security technology is on the rise.
And banks are responding.
Many banks with mobile apps use biometrics for user authentication. The types of biometrics used include fingerprint scanning alongside facial and voice recognition.
Some banks use a combination of these biometrics to add an extra layer of security in the form of multi-factor authentication.
Smartphone security
Both Android and iOS devices have added biometric security features over recent years.
In 2011, the Motorola Atrix was the first consumer smartphone to feature integrated fingerprint scanning. It was far from perfect, but since then, the technology has come on in leaps and bounds and is now a feature of almost every modern smartphone.
But it doesn’t stop at fingerprint scanning.
In 2017, Apple’s iPhone X showcased a new biometric authentication feature — Face ID.
Since then, in 2026, smartphone manufacturers have continued to refine biometric authentication by keeping biometric processing on-device and reducing reliance on centralized servers.
This facial recognition feature works by projecting a pattern of more than 30,000 infrared dots onto the user’s face, then reading the pattern to create a facial map of the user.
This allows the device to read the user’s face, confirm their identity and authorize them to log in.
In 2021, Apple is taking it one step further by combining its Face ID tech with a client-server side Passkey algorithm for even more secure authentication.
Samsung has its own take on facial recognition technology in its Intelligent Scan feature. This combines iris scan and facial recognition to provide biometric multi-factor authentication.
Types of biometrics for security and authentication
As we’ve learned above, biometric security doesn’t end with fingerprint scanners. Humans have all sorts of unique characteristics. These features make for ideal security tools.
Here are some different types of biometrics you might see replacing your passwords in the near future.
Facial recognition
Facial recognition works when an image of your face is captured on camera. Special software then reads various measurements and points of your face, such as the distance between your eyes, to create your facial signature.
Face recognition is a feature modern Apple smartphones use to unlock their devices. According to Apple, the chances of a face other than your own unlocking your phone is about one in a million!
The Covid-19 pandemic has a different take on the subject, robbing facial recognition engines of [the bottom] half of the data. Apparently, the Cupertino giant’s tech is so solid that iPhones and iPads can be trained to recognize their masked owners with a few tricks involving a half-folded mask.
Optical recognition
Did you know that the human iris holds more than 200 points of reference while a fingerprint holds just 60-70?
The iris is a muscle in your eye which opens and closes your pupil to control the amount of light entering. If you look very closely in the mirror, you’ll see that the patterns in your right iris are completely different to your left. And you certainly won’t find another human with the same iris pattern as yours.
This makes iris recognition an excellent way to verify your identity. Your iris patterns are scanned and recorded — and later used to authenticate you.
Believe it or not, this type of optical recognition has been used for user authentication in smartphones as far back as 2015, with the Lumia 950 and Lumia 950 XL.
Vein recognition
Vein recognition, simple and secure, is also growing in popularity. Some versions of this technology have been introduced to industries, while others are still in the research phase.
It works by scanning your finger. But this time, rather than scanning your fingerprint ridges, the device actually scans through your finger to detect your vein pattern.
Many researchers consider this tech the future of more secure, touchless authentication. While you may leave your fingerprints on items you touch (which can be lifted and replicated), there’s no way you can leave your vein pattern behind!
The technology can also scan veins in your palm, as seen in LG’s G8 ThinQ smartphone. This option seems to be getting a lot of attention from Apple: the company has recently filed a patent that could allow their smartwatches to better detect hand movements and assist in authentication.
Voice recognition
Biometrics aren’t just limited to your physical features. Voice or “voiceprint” biometrics technology is developing rapidly. Some financial institutions already use it, for example, to authenticate users carrying out transactions via telephone.
It works like this. A voice sample is recorded, usually with the user reciting some text or phrases, so the sample can be analyzed digitally for tone and frequencies. Then the system compares the user’s spoken passphrase to this stored digital voiceprint. Some voice recognition technology requires a fixed passphrase, while others can recognize the voiceprint even through unfamiliar, non-fixed passphrases.
Handwriting recognition
Another non-physical form of biometric security is handwriting recognition.
This captures a person’s handwriting behavior rather than the final handwritten output. Dynamic signature verification technology confirms the user’s identity by analyzing the shape, speed, stroke, pen pressure, and timing information during the act of signing.
These unique handwriting behaviors are extremely difficult to recreate by anyone other than you, which makes them a highly effective way of verifying a user’s identity.
Is biometric security safe?
While this technology is undeniably exciting and may seem like the answer to all our cybersecurity problems, it’s important to understand that it does not guarantee security.
While it might require a bit more effort to crack than a weak password, biometric security can still be breached.
Cybercriminals have successfully lifted fingerprints left behind on surfaces to make impressions and breach biometric security systems.
The security of the database holding your biometric information is also key. In order to verify your identity, the first step is to scan your unique biometrics, whether it’s your fingerprint, vein pattern, or your voiceprint, then save it to a database.
But what happens if your biometric data is compromised?
How will you change your password?
Unfortunately, this is a very real concern, and a breach has already happened.
In 2015, the US Office of Personnel Management reported the theft of 5.6 million fingerprints in a damaging cybersecurity incident.
The Guardian exposed a massive leak of over 23 gigabytes of data with records of about 28 million facial recognition tokens, fingerprints, passwords, and other security-related information in 2019. UK banks, police, and defense firms were among the customers of the company whose data had been compromised.
These incidents are often cited because they highlight a long-term risk: once biometric data is exposed, it cannot simply be changed like a password.
So, biometric security isn’t bulletproof. It comes with its pros and cons. Here’s a brief rundown.
Advantages of biometric security
- Improved security. Biometric authentication, while not perfect, is much more difficult to hack than traditional logins and passwords.
- No more memorizing passwords. The need to memorize passwords tempts people into setting weak ones. Biometrics cancels the need to remember anything.
- No more forgetting passwords. By their very nature, strong passwords aren’t usually memorable. Forgetting your password can be frustrating and time-consuming.
- Speed. Modern phones equipped with fingerprint scanners can identify their users in milliseconds, significantly faster than inputting any password or pin.
- Identification on the go. The great thing about biometrics is that the data is always on you, wherever you go. You can’t accidentally leave it at home or on the train!
Disadvantages of biometric security
- Environment. The environment can impact how well the technology functions. For example, in cold weather, the chance of error when authenticating a user is higher. Excess moisture can also prevent sensors from working properly.
- Errors. There’s always a chance that the technology might return an error. When a biometric security device accepts an unauthorized user, it’s called a False Acceptance. When it rejects an authorized person, it’s a False Rejection. Both have been known to happen.
- Requires hardware and integration. Not only does the biometric system rely on the trio of a sensor, computer, and software, it also requires a programmer’s know-how to manage the system. It’s fair to say that a biometric system is more complex than a lot of other security alternatives.
- Scanning challenges. Certain scenarios, such as wearing glasses when trying to scan your iris, can cause scanning difficulties and slow down what should be a convenient and quick process.
- Cost. While biometric security systems are cheaper than ever, they are still more costly than more traditional security devices.
- Can’t be reset once compromised. To use biometric authentication, you need to allow your unique biometrics to be held in the government or organizational database. What happens if this database is breached? Unlike a password, you can’t change your biometrics.
- Physical disabilities and population coverage. Biometric security will not work for everybody. For instance, someone may have lost body parts such as fingers or eyes and will be unfairly excluded from the system.
- Unhygienic. Some biometric systems will require a large number of people to come in contact with the same scanners, which can raise hygiene concerns. This is especially relevant in the post-pandemic reality.
How to protect biometric data?
While most of the responsibility to protect your biometric data falls on the organizations gathering it, you also have a personal responsibility to respect and protect it.
Here are some principles that businesses and individuals should follow to protect this valuable information from cybercriminals.
How organizations should protect biometric data
- Use anti-spoofing technology to protect against unauthorized users tricking the system, such as using rubber masks to breach facial recognition.
- Keep all software and systems up-to-date.
- Use strong internal passwords.
- Use multi-factor authentication.
- Use strong cybersecurity software and processes.
How you should protect your biometric data
- Respect your biometrics and only share it with highly trusted organizations.
- Check if the necessary cybersecurity controls are in place with any organization you share your data with.
- Only share where necessary. For instance, consider whether enabling Facebook’s facial recognition is an absolute must.
- Maintain strong passwords to block easy routes for hackers to steal your biometrics.
- Use a trusted cybersecurity software to keep your digital life secure.
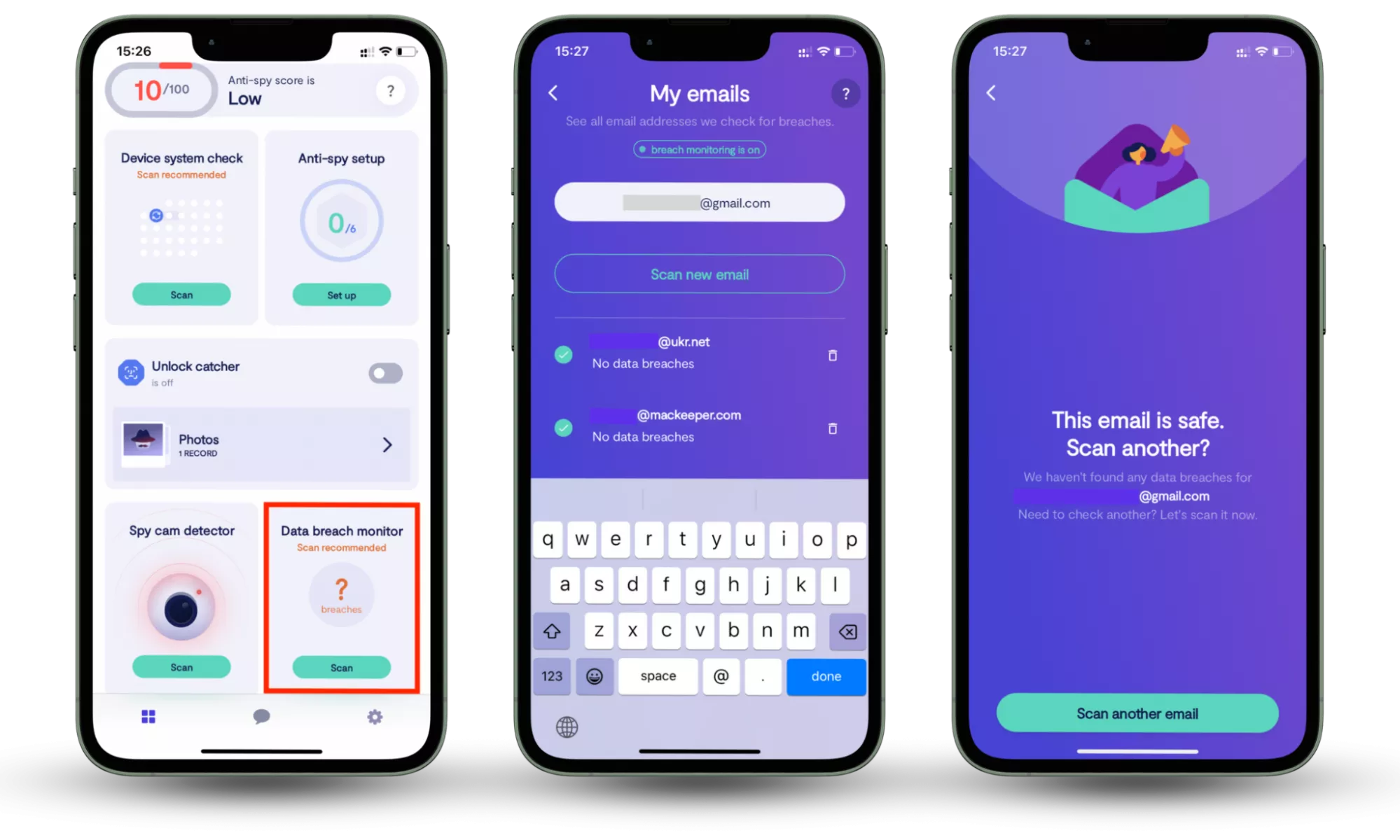
One practical way to reduce the risk of biometric misuse is to monitor whether your online accounts have already been exposed in data breaches. Tools like Clario Anti Spy’s Data breach monitor scan the email addresses you use for online accounts and alert you if they appear in known breaches. This allows you to fix compromised accounts outside the app, track which issues have been resolved, and continuously monitor new breaches, helping to limit opportunities for attackers to exploit leaked credentials alongside biometric data.
How to check whether your information is compromised:
- Download Clario Anti Spy and subscribe.
- Open the app, and, under Data breach monitor, tap Scan.
- Enter your email address.
- When the scan is complete, follow the on-screen guidance to review any data breaches.
- Repeat the process for any other email addresses.
Is biometric security here to stay?
While the biometric security technology is relatively young and might have its disadvantages, it’s certainly not going anywhere. In the future, we’ll be seeing better implementations with more reliability, speed, and convenience.
Although some examples and statistics reference earlier years, the security principles discussed in this article continue to apply as biometric technologies and attack methods evolve.
It has proven to be a more secure way of protecting accounts than traditional logins and passwords. Healthcare and finance, the two industries that need it most, steadily demonstrate their trust in it.
While this authentication technique has countless benefits, biometric security does not cover all aspects of digital safety. There are numerous other ways for cybercriminals to penetrate your system or take advantage of your gullibility, including ransomware or social engineering.
Conclusion
Biometric security has become a reliable alternative to traditional passwords, offering greater convenience and stronger protection in many everyday scenarios. However, biometrics work best as part of a broader security strategy, not as a single line of defense. If personal data or login credentials are already exposed, even strong authentication methods can be undermined.
That’s why ongoing awareness matters. Tools like Clario Anti Spy help close this gap by monitoring whether your email addresses appear in known data breaches and alerting you when information is exposed. By identifying compromised accounts early and fixing them in time, users can reduce the risk of attackers exploiting leaked data alongside biometric authentication.
Read more:


