Table of contents
- What is spyware?
- How does spyware work?
- What is the purpose of spyware?
- What can spyware do to my computer?
- How does spyware infect my computer?
- Spyware types
- How to protect yourself from spyware
- Conclusion
Spyware is a tricky thing that can lie in wait for you anywhere online.
Recently, Android spyware was disguised as a necessary system update online. After the installation, this “system update" took over the control of the devices to steal sensitive information.
Who knows where else internet spyware can hide?
Spyware is commonly used for identity theft, financial fraud, and unauthorized surveillance. Modern spyware is designed to remain hidden for long periods, quietly collecting sensitive data without triggering obvious warning signs. This makes early awareness and preventive measures essential for everyday internet users.
Now, let's dive into what spyware is and what it does and how to protect your devices against it.
What is spyware?
Spyware is a kind of malware that monitors and tracks your device and internet activity to gather information for third parties. It works underground or attaches to your device's operating system. This way, you hardly even know that they are there.
Spyware is often confused with other types of malware, but it behaves differently:
- Spyware vs viruses: Viruses are designed to damage or disrupt systems, while spyware focuses on silently collecting information.
- Spyware vs ransomware: Ransomware locks or encrypts data for payment, whereas spyware steals data without alerting the user.
- Spyware vs adware: Adware mainly displays unwanted ads, while spyware continuously monitors activity and gathers sensitive data.
How does spyware work?
Spyware silently infiltrates your devices and begins to obtain important information, such as login details, account credentials, and online activities. Internet spyware is secretive, so you don't even know about its existence until it takes over your computer. It just stays put, keeps monitoring and reporting your activities to third parties.
Spyware typically follows a simple but effective process:
- Entry: It enters the device through bundled software, fake updates, malicious links, or infected downloads.
- Installation: The spyware installs itself quietly, often without the user noticing or granting clear permission.
- Monitoring: It runs in the background, tracking activity such as keystrokes, logins, browsing habits, or communications.
- Data transmission: The collected information is sent to third parties without the user’s knowledge.
What is the purpose of spyware?
While spyware is nothing but malicious malware, its purpose is to monitor and steal user data without your consent. When the information is stolen, it sends it to unknown parties looking to make money from your data. These third parties can sell or use your personal information to predict your activities, create a fake online interface or make you susceptible to a scam.
Stolen data collected by spyware is commonly used in several ways:
- Selling personal information to advertisers or data brokers.
- Stealing login credentials for account takeovers.
- Monitoring user behavior to build detailed profiles without consent.
- Supporting phishing attempts or other online scams.
What can spyware do to my computer?
Spyware can take control of your devices and steal your information without you knowing about it. Some of the ways it does this are by recording your keystrokes, hacking your camera or voice calls. It can also change your security settings to give room for more spyware and generate constant pop-ups. When you have too much spyware on your computer, there's hardly any way you will enjoy using it.
Spywares can also slow your devices down. When your devices are breached, the spyware silently attaches to the operating system. Its monitoring and reporting on your activities greatly slows down the speed of your devices too.
In many cases, spyware causes noticeable changes in device behavior, including:
- Slower system performance or frequent freezing.
- Unexpected pop-ups or redirects while browsing.
- New toolbars, extensions, or settings changes you didn’t make.
- Increased data usage without explanation.
- Camera or microphone activating unexpectedly.
- Security software being disabled without permission.
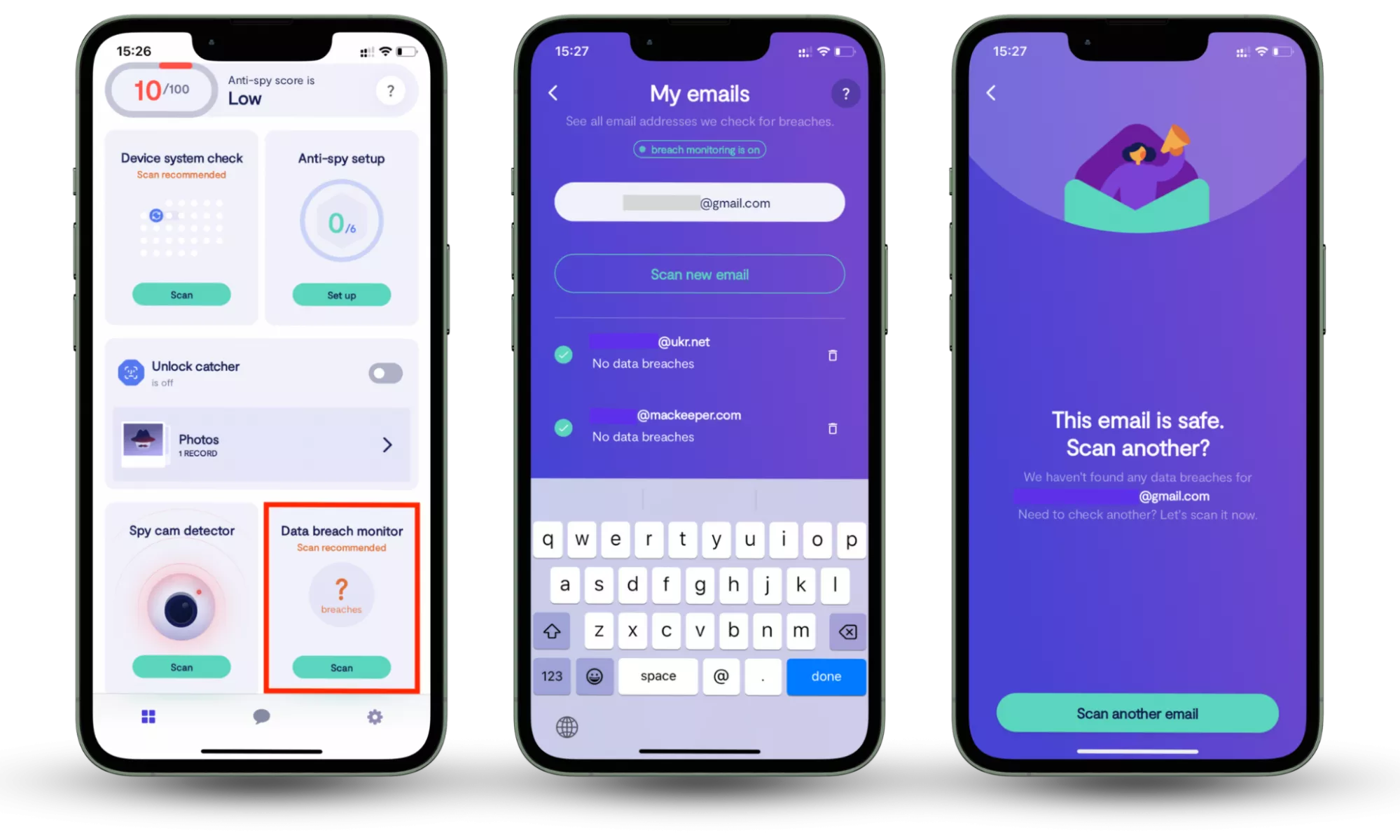
Spyware often aims to steal login details and personal data long before users notice device issues. Using a data breach scan and monitor can help you check whether your online accounts have already been exposed.
Clario Anti Spy’s Data breach monitor scans the email address used during setup to identify known data leaks linked to your accounts. It alerts you if new breaches appear, allowing you to fix affected accounts, mark resolved issues, and add additional email addresses for ongoing monitoring.
How to check whether your information is compromised:
- Download Clario Anti Spy and subscribe.
- Open the app, and, under Data breach monitor, tap Scan.
- Enter your email address.
- When the scan is complete, follow the on-screen guidance to review any data breaches.
- Repeat the process for any other email addresses.
How does spyware infect my computer?
There are different ways for your computer to be infiltrated. The most common ways are:
- Web downloads
There are many software pretending to be something else on the internet, especially if they are from unauthorized sources. Once you download them, this can lead to spyware getting into your computer.
This often includes fake utilities, cracked software, or free tools downloaded from unofficial websites.
- Online Actions
Do you sometimes click on unknown links? Do you ever adjust your browser settings? These are some of the ways you can get spyware on your computer.
Examples include clicking phishing links, changing browser settings on untrusted sites, or installing fake system updates.
- Pop-ups
Not all pop-ups are dangerous but some can be. Clicking and following the instructions on pop-ups may invite unwanted threats onto your device.
These commonly appear as urgent security alerts or prize notifications that pressure users to click immediately.
Spyware types
When discussing the main types of spyware that can infect your gadgets, four will stand out. These spyware examples have been known to deploy unique tactics in tracking and stealing your information.
- Adware
Used mostly for marketing, adware is a type of spyware that tracks your downloads and browser history. It uses the information from these places to predict your interest in different services and products. It then advertises exact or similar services or products, asking you to take action and make a purchase.
While often considered lower risk, adware can still expose users to malicious sites and unwanted data collection.
- Trojan
Trojans often appear to you as one of the softwares you will be keen to download and install. For instance, a trojan may disguise itself as a popular app or security update such as MEMZ. All it needs is for you to download it. Once done, a third party controlling it can access your sensitive information.
Trojans are considered high risk because they can provide attackers with direct access to sensitive personal and financial data.
- Tracking cookies
Tracking cookies work like adware because they serve marketing purposes. They silently invade your downloads and browser history to monitor your preferred products and service activities. They then use this information to give you targeted ads of your previous products or service activities.
These are usually lower risk but can significantly reduce privacy by enabling long-term tracking across websites.
- System monitors
They majorly monitor your activities. If you have them in your gadgets now, there are high chances that they are monitoring your behavior.They gather data like your keystrokes, programs launched, visited websites, chatroom dialogues, emails and many more.
This type poses a high risk as it can capture highly sensitive information such as passwords, messages, and private communications.
How to protect yourself from spyware
As good as the internet is these days, everyone is still susceptible to targeted attacks through different means. But then, this doesn't rule out the fact that you can still protect yourself. Doing the following will help keep you secure from targeted attacks.
- Step 1: Adjust browser security settings
The default security settings of your browser might not be good enough to protect you from spyware. So you need to adjust the settings depending on the browser you use. The main goal is to make your browser block all suspicious pop ups, websites, and plugins to keep you safe.
Pro tip
Enable built-in pop-up blockers and safe browsing features to automatically block known malicious sites.
- Step 2: Always read terms & conditions
What did you hear about terms & conditions? Excessively long, boring and written in technical jargon? But that is where the spyware information that might just save you is included. Software manufacturers usually provide details on how they collect user data in this section, so it is in your best interest to read them.
Pro tip
Pay special attention to sections about data collection, third-party sharing, and permissions.
- Step 3: Avoid pop-ups
If you are on the internet, pop-ups are your permanent, sometimes unwanted, companions. Many of them are enticing and want you to follow through with them. It's in your best interests to avoid clicking on these pop-ups or obey their instructions.
Pro tip
Close suspicious pop-ups using the browser tab or task manager instead of clicking inside the pop-up.
- Step 4: Update your system
Your system's security needs to be maintained regularly, and the way this is done is through the release of system updates. Once you see an advanced version of your browser or system from a trusted source like Google, Microsoft and Apple, be sure to update it.
Pro tip
Only install updates directly from official system settings or trusted vendors like Google, Microsoft, or Apple.
- Step 5: Prevent the download of suspicious apps
Have you ever gone online and seen some apps with enticing ads making promises too good to be true? Or do you simply feel the urge to access a great-looking yet unreviewed app? Don't do it! Apps not gotten through trusted sites should never be downloaded.
Pro tip
Check app reviews and download software only from official app stores or verified websites.
- Step 6: Be careful about emails
Emailing has become a way many third parties use to disguise threats that infiltrate your digital life. If you receive an email from an unknown source telling you to follow a link, be careful. Clicking on these links may land you into more mess than you bargained for.
Pro tip
Verify the sender’s email address carefully and avoid clicking links in unsolicited messages.
Conclusion
Spyware is a real threat to your digital life and your data, but not the only one.
To protect your digital privacy and security, use an all-round solution like Clario Anti Spy. With features like real-time anti-malware protection, and data breach monitor.
That is why it is important to protect your data with reliable software like Clario Anti Spy that will secure your devices from the mentioned threats.


