Table of contents
- What to do immediately after a data breach
- What actually happens after a data breach (most people don’t realize this)
- Stolen data is resold, not used once
- Attacks are often delayed on purpose
- One leaked account can unlock others
- Follow-up scams feel more convincing
- What companies must do after a data breach
- What the law requires companies to do
- What users actually need after a breach
- What you should do after a data breach
- First 24 hours after a data breach
- What to do in the following 7 days
- Long-term protection after a breach
- Common mistakes to avoid after a data breach (checklist)
- Clicking “security alert” emails or messages
- Changing only one password
- Ignoring secondary or old accounts
- Assuming no immediate financial loss means no risk
- Skipping follow-up monitoring
- FAQ
- Can a data breach affect me even if nothing happens right away?
- Should I change passwords even if the company says the breach was “limited”?
- What is the biggest risk after a data breach?
- How do I know if my email or password has been leaked?
- Is antivirus software enough after a data breach?
- Conclusion
Getting a data breach notification can feel alarming — especially when it’s unclear whether your personal information is actually at risk or what to do next. Research and incident reports tracked by organizations such as the FBI’s Internet Crime Complaint Center (IC3) show that a large share of identity theft and account takeovers occur weeks or months after a breach, not immediately. This delay happens because stolen data is often reused later for phishing, credential-stuffing, and targeted scams, when people are less alert.
This guide explains exactly what to do after a data breach, based on real-world breach patterns. You’ll learn how to verify alerts, secure your accounts, and reduce the hidden risks that commonly appear days or weeks after the initial incident, following guidance aligned with official recommendations from the U.S. Federal Trade Commission.
What to do immediately after a data breach
When a data breach is confirmed, speed matters more than complexity. You don’t need to be technical, but you do need to act in the right order. The steps below focus on reducing the most common post-breach risks: account takeovers, phishing attacks, and reused credentials being exploited across other services.
- Follow this checklist as soon as you receive a legitimate breach notification.
- Verify the breach notification is legitimate using the company’s official website
- Secure affected accounts by changing passwords and enabling multi-factor authentication (MFA)
- Check whether the same password is used on other services and update those accounts
- Watch for follow-up phishing emails, scam calls, or fake “security alerts”
- Freeze your credit if financial or identity data was exposed
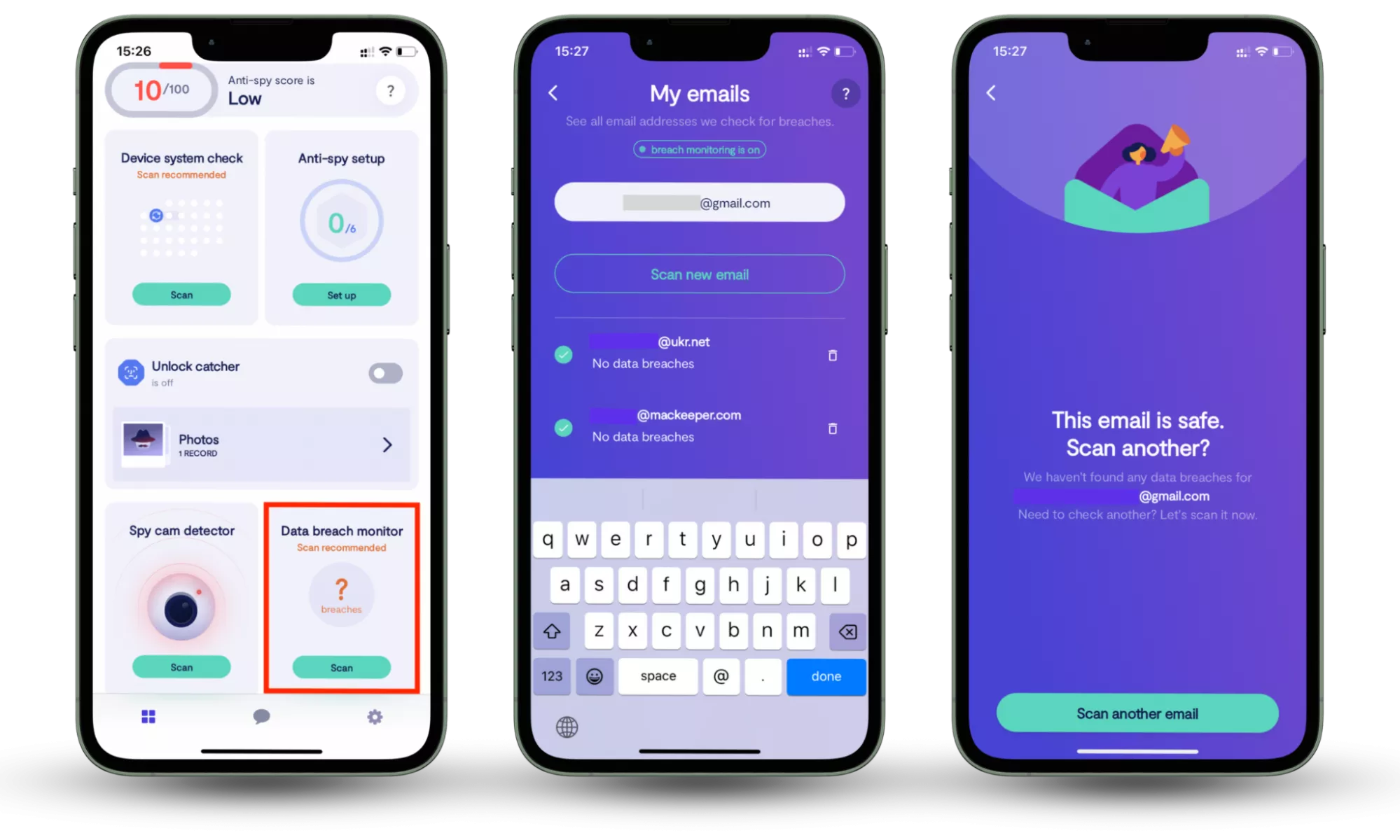
- Use the Data breach monitor in Clario Anti Spy
Clario Anti Spy includes a Data breach monitor that continuously checks whether your personal data, such as email addresses and passwords, has appeared in known data leaks. This allows users to react quickly, secure affected accounts, and avoid delayed attacks that often follow major breaches.
One customer contacted our support team after receiving a breach notification from an online service he hadn’t used in years. He wasn’t sure whether his data was still relevant or at risk.
Using Clario Anti Spy’s Data breach monitor, we identified that the same email and password combination had already appeared in multiple leaked databases. Our support team guided him through changing passwords on all linked accounts, enabling MFA, and monitoring for suspicious login attempts. Within days, he avoided several unauthorized access attempts tied to reused credentials.
How to check whether your information is involved in a data breach:
- Download Clario Anti Spy.
- Open the app, and, under Data breach monitor, tap Scan.
- Enter your email address.
- When the scan is complete, follow the on-screen guidance to review any data breaches.
What actually happens after a data breach (most people don’t realize this)
For many people, a data breach feels like a single event — a notification arrives, passwords are changed, and life moves on. In reality, a breach is often just the starting point. The most serious consequences usually happen later, when stolen data is quietly reused in ways that aren’t immediately obvious.
Stolen data is resold, not used once
After a breach, personal data is rarely used by just one attacker. Email addresses, passwords, phone numbers, and other details are typically bundled and resold on underground marketplaces, sometimes multiple times. Each resale increases the chance that your data ends up in the hands of someone looking for a new way to exploit it.
Attacks are often delayed on purpose
Many cybercriminals don’t act immediately. Instead, they wait days or weeks before attempting access. This delay makes the activity harder to connect to the original breach and increases the chances that users will have dropped their guard. As a result, suspicious logins or scam messages may appear long after the breach seems “resolved.”
One leaked account can unlock others
If the same password is reused across services, attackers will attempt account chaining by testing leaked credentials on email, banking, shopping, and social media platforms. Gaining access to one account often provides clues or recovery options that make breaching others easier.
Follow-up scams feel more convincing
Once attackers have real data, they can launch highly targeted social engineering attacks. Phishing emails may reference actual services you use, partial account details, or recent breach news. These follow-ups feel legitimate because they are built on real information, not guesswork.
Understanding these patterns is critical. A data breach isn’t just about what was stolen — it’s about how that information is reused over time, and why fast, informed action makes a real difference.
What companies must do after a data breach
When a data breach occurs, companies are required to follow specific legal steps. However, legal compliance alone is not enough to protect users. There is often a gap between what regulations mandate and what affected customers actually need to stay safe.
What the law requires companies to do
Most data protection laws require companies to act quickly and transparently after a breach. While exact obligations vary by region, companies are typically expected to:
- Notify affected users within a defined timeframe once a breach is confirmed
- Disclose what types of data were exposed, such as emails, passwords, or financial details
- Explain how the breach occurred, if known
- Report the incident to relevant regulatory authorities when required
What users actually need after a breach
From a user’s perspective, compliance isn’t enough. People need clear, practical guidance that helps them act immediately. After a breach, companies should also:
- Clearly state whether passwords, login tokens, or recovery data were exposed
- Explain what users should do first, in plain language
- Warn about follow-up phishing or scam attempts related to the breach
- Offer concrete security steps, such as enabling MFA or monitoring account activity
When companies fail to provide this level of detail, users are left vulnerable — not because they weren’t notified, but because they weren’t guided.
What you should do after a data breach
Responding to a data breach isn’t about doing everything at once — it’s about doing the right things at the right time. The steps below are organized by urgency, helping you reduce immediate risk first and prevent delayed attacks that often follow weeks later.
First 24 hours after a data breach
The first day is critical. Most account takeovers happen when leaked credentials are tested quickly or when users react to fake “security alerts.”
- Confirm the breach is real by visiting the company’s official website directly, not by clicking email links
- Change the password for the affected account immediately
- Enable multi-factor authentication (MFA) if it’s available
- Log out of all active sessions to block access using stolen login tokens
- Secure your email account first if it shares the same password — email access allows attackers to reset other accounts
What to do in the following 7 days
Once immediate access risks are reduced, focus on exposure and follow-up attacks, which often begin days later.
- Check whether the same password was reused on other services and update those accounts
- Review account activity logs for unfamiliar logins or changes
- Stay alert for phishing emails, scam calls, or messages referencing the breach
- Monitor whether your personal data appears in additional leaks
Tools such as Clario Anti Spy’s Data breach monitor can help by continuously checking whether your email addresses or passwords appear in known leaked databases, allowing you to act before accounts are abused.
Long-term protection after a breach
Even after accounts are secured, long-term precautions reduce the chance of future misuse.
- Use unique passwords for important accounts, especially email and financial services
- Keep multi-factor authentication enabled wherever possible
- Be cautious with unexpected “security” messages, even months after a breach
- Consider freezing your credit if identity or financial data was exposed
Taking these steps helps secure your accounts, reduce follow-up risks, and minimize the chances of falling victim to data breaches in the future.
Why data breaches are more dangerous weeks later
Data breaches often cause delayed harm, as attackers commonly wait weeks before exploiting leaked data when users are less alert. After breach announcements, phishing and scam attempts typically increase because messages referencing real incidents appear more trustworthy and urgent.
Common mistakes to avoid after a data breach (checklist)
People often make data breach mistakes by clicking fake security alerts, changing only one password, ignoring secondary accounts, or assuming they are safe if no money is stolen immediately. Use this checklist to make sure your response to a data breach doesn’t accidentally increase your risk.
Clicking “security alert” emails or messages
Avoid clicking links in emails or texts claiming to help you “secure” your account after a breach. Attackers often impersonate companies involved in real breaches to steal login details through fake security pages.
Changing only one password
Do not assume that securing a single account is enough. If you reused the same password elsewhere, attackers can test it across multiple services using automated login attempts.
Ignoring secondary or old accounts
Check all accounts connected to the same email address, including older or rarely used services. These accounts are commonly targeted because suspicious activity is less likely to be noticed.
Assuming no immediate financial loss means no risk
Do not stop monitoring just because no money was stolen. Identity misuse, phishing attacks, and account takeovers often occur weeks or months after the original breach.
Skipping follow-up monitoring
Failing to monitor account activity and data exposure after the initial response leaves room for delayed attacks. Ongoing monitoring helps catch problems before real damage occurs.
| ✅ Do this | ❌ Don’t do this |
| Visit the company’s official website directly to verify the breach | Click links in “security alert” emails or text messages |
| Change passwords for the affected account and any accounts using the same password | Change only one password and assume the issue is resolved |
| Enable multi-factor authentication (MFA) wherever possible | Rely solely on password changes for protection |
| Review all accounts linked to the same email address, including older or inactive ones | Ignore secondary or rarely used accounts |
| Monitor account activity and watch for phishing attempts after the breach | Assume you’re safe because no money was stolen immediately |
| Continue monitoring for weeks after the breach | Stop checking once the initial response is complete |
FAQ
Can a data breach affect me even if nothing happens right away?
Yes. In many cases, stolen data is misused weeks or months later. Attackers often wait before launching phishing campaigns or attempting account takeovers using leaked credentials.
Should I change passwords even if the company says the breach was “limited”?
Yes. If your login details were involved, changing passwords immediately is recommended — especially if you reused the same password on other services.
What is the biggest risk after a data breach?
The biggest risk is credential reuse. Attackers commonly test leaked email-password combinations across multiple platforms to gain access to other accounts.
How do I know if my email or password has been leaked?
Clario Anti Spy’s Data breach monitor can alert you if your personal information appears in known leaked databases.
Is antivirus software enough after a data breach?
Not on its own. While antivirus software helps protect devices, post-breach protection also requires securing accounts, monitoring identity exposure, and staying alert to phishing attempts.
Conclusion
A data breach doesn’t always cause immediate harm, but the risk often increases over time as stolen data is reused for phishing and account takeovers. Acting quickly, securing all related accounts, and avoiding common post-breach mistakes significantly reduces long-term damage. Use Clario Anti-Spy’s Data breach monitor, which helps identify leaked emails or passwords early, allowing users to respond before follow-up attacks occur.


