Table of contents
- Why online scams are more effective today than ever
- How to tell if you’re being scammed
- Types of scams
- Phishing
- Identity theft
- Credit card fraud
- Nigerian scam
- Online dating scam
- AI voice & deepfake scams
- QR code scams (Quishing)
- Business email compromise (BEC)
- Crypto investment & wallet scams
- What to do and how to recover if you’ve been scammed
- How to avoid scams in the future
- Use Anti Spy tool
- How to silence unknown callers on your phone
- Conclusion
Online scams are almost as old as the web itself. As the internet has evolved, the scope and complexity of scams have evolved with it, posing a risk to anyone online. The increased convergence of internet, phone and cloud services has only served to amplify the threat, providing bad actors with multiple avenues of attack.
To make matters worse, scammers are experts at taking advantage of tragic events to unveil all-new scams, preying on people’s fears and vulnerabilities. For example, as the COVID-19 pandemic raged on, the FTC reported a 45% increase in identity theft and fraud cases in 2020. The cases numbered some 4.8 million, up from 3.3 million in 2019.
More recent data confirms that online scams continue to grow at an alarming rate. According to reports from U.S. consumer protection agencies, fraud losses now exceed $10 billion annually, with impersonation scams, investment fraud, and online shopping scams accounting for the largest share of reported losses. This trend shows that scams did not peak during the pandemic but have continued to evolve in scale and sophistication.
If you haven’t already been the victim of a scam, chances are it’s just a matter of time. Knowing the kinds of scams out there and what to do in response is important to protect your information, reputation, and resources.
Pro tip
A dedicated security app can be an important first line of defense against scams and fraud. Clario Anti Spy provides real-time security monitoring of your devices. If your personal details are compromised, such as in a data breach, it instantly alerts, helps you re-secure your accounts and shuts down any potential pathway for scams. Download Clario Anti Spy today to stay safe from scams.
Why online scams are more effective today than ever
Modern scams succeed because attackers combine psychological manipulation with advanced technology. Data breaches, social media exposure, and AI-generated content allow scammers to personalize messages at scale, making them appear more legitimate than ever. At the same time, people increasingly rely on digital services for banking, communication, and work, expanding the number of potential attack surfaces scammers can exploit.
How to tell if you’re being scammed
Regardless of the type of scam, many scammers employ similar methods to achieve their goal. Often, they resort to high-pressure sales tactics in an effort to get you to make a quick decision. As part of this strategy, many scammers will present an opportunity as a limited-time offer.
More often than not, this sounds too good to be true. They promise great riches and rewards, with little to no real risk — clearly not how things can be in real life.
Cybersecurity analysts consistently observe that scams promising guaranteed rewards or unusually high returns rely on urgency to bypass rational decision-making. When an offer emphasizes speed over verification, it is often designed to prevent victims from spotting inconsistencies or researching the sender.
The vast majority of scams also involve money transfers, using a check or wire transfer. Some, such as Craigslist scams, may involve sending a fake PayPal email in an attempt to get you to send money.
Another big warning sign is a lack of detailed contact information, or conflicting information. Either way, it will result in a vague, incomplete picture, perfect for a scammer who doesn’t want to get caught.
The table below highlights common scam warning signs compared to how legitimate organizations typically operate.
| 🚩 Scam behavior | 🟢 Legitimate behavior |
| Creates a sense of urgency or pressure to act immediately | Allows time to review, verify, or seek a second opinion |
| Requests payment via gift cards, wire transfers, or cryptocurrency | Uses standard, traceable payment methods |
| Avoids providing verifiable contact information | Provides official contact details and customer support channels |
| Messages contain vague or inconsistent details | Communication is clear, specific, and consistent |
| Asks for sensitive information unexpectedly | Does not request passwords or full financial details |
| Discourages independent verification | Encourages contacting the organization directly through official channels |
Based on real-world breach response patterns, scammers frequently avoid providing verifiable contact details because anonymity allows them to abandon accounts quickly once a scheme is exposed.
Types of scams
While by no means exhaustive, here are a few of the most common types of online fraud and scams to watch out for.
Phishing
Phishing scams are one of the most common types of scams. They involve using social engineering to con individuals into giving away important, sensitive information, such as passwords and banking details.
Identity theft
Identity theft is one of the most terrifying types of scams. The scammer uses a person’s identity to open lines of credit, take out loans and generally wreak havoc on a person’s credit score and reputation.
Credit card fraud
Credit card fraud involves using a malicious website masquerading as a legitimate one to convince someone to pay for something using a credit card. Unfortunately, the site is designed to harvest credit card numbers from unsuspecting victims.
Nigerian scam
Also known as the 419 scam, this scam takes the form of a message claiming to have been sent on behalf of a Nigerian prince. It involves asking for an investment with the promise of a return many times larger.
Online dating scam
The rise of online dating apps and services have helped modernize one of the oldest scams in the book. A scammer poses as a boyfriend or girlfriend, wooing the target and getting them to lower their guard. Once the time is right, the scammer asks the victim for money, gifts or help paying bills.
AI voice & deepfake scams
AI-powered scams use cloned voices, fake videos, or realistic text messages to impersonate trusted individuals such as family members, executives, or company representatives. These scams are especially effective because they exploit trust and urgency, often demanding immediate action or payment.
QR code scams (Quishing)
QR code scams involve malicious codes placed on parking meters, restaurant menus, emails, or flyers. Scanning the code redirects victims to phishing websites designed to steal login credentials or payment information.
Business email compromise (BEC)
Business Email Compromise scams target employees by impersonating executives or vendors. Victims are pressured into making wire transfers, updating banking details, or sharing sensitive company information.
Crypto investment & wallet scams
Cryptocurrency scams often promise high or guaranteed returns and may involve fake trading platforms or wallet-draining links. Once funds are transferred, recovery is usually impossible.
Cybersecurity insight
Modern scams are rarely random. Scammers increasingly rely on breached databases, public social media profiles, and automated tools to tailor messages to specific victims. If a message references personal details such as your workplace, recent purchases, or contacts, this should not be taken as proof of legitimacy—it is often a sign that your data has already been exposed.
What to do and how to recover if you’ve been scammed
There are a number of steps you should take if you think you’ve been scammed. They can help you recover money and mitigate the damage, but the specific steps depend on the particular scam you’re a victim of.
- If you were tricked into giving a scammer your credit card or banking information, and money has been stolen from your bank account, the first step is to contact your financial institution and put a hold on any payments. The FTC recommends immediately calling the card issuer and reporting the charge as fraudulent. The faster you act, the more likely you are to get your money back or, at the very least, minimize how much the scammers make off with.
- The same goes for virtually any kind of financial transaction. Whether it be a gift card, wire transfer, cryptocurrency or any other payment method, contact the company that issued the payment and report it as fraudulent.
- Things are a little trickier if you’re the victim of identity theft. Swift action is critical to minimize the damage someone can do with your information. Immediately go to IdentifyTheft.gov, file a report and put a recovery plan into action.
- Similarly, if a scammer has gained access to your passwords, it’s important to change them as soon as possible, choosing something that is secure and hard to guess.
- If a scammer has gained access to, or stolen your phone, you should immediately contact your wireless provider to stop anyone from accessing your account. You may also want to use iOS or Android’s built-in tools to remotely wipe the device, thereby preventing the scammer from continuing to gather data from it.
Pro tip
If you suspect malware or unauthorized access on any device, run a full security scan and review app permissions immediately. Remove unknown software, enable multi-factor authentication on critical accounts, and monitor login activity for unusual behavior over the following weeks.
- Report any scams or fraud to the FTC. Reporting fraud helps the FTC build a case and increases the likelihood of bringing a scammer to justice.
Some individuals have started taking their revenge on scammers, scambaiting them in an attempt to waste their time. Is this something you should do? What are the risks? Read our blog to find out what you need to know about getting back at scammers.
How to avoid scams in the future
One of the most successful tools scammers have is pressure. They will often try to pressure you into making a decision before you have time to think about what they’re asking. This may include demanding a very specific action, such as some type of payment that can only be made a certain way.
Therefore, one of the most important things you can do is to take a moment and think about what the person wants.
Were you expecting this call or email? Is this an organization or business you normally interact with? What is the person asking you to do? Are they insisting some action only be done a certain way?
Even if you’ve received a phone call or email from an organization you normally do business with, don’t click any links or do anything while on the phone call. Instead call the organization back using a published phone number and verify the legitimacy of the communication you received.
Use Anti Spy tool
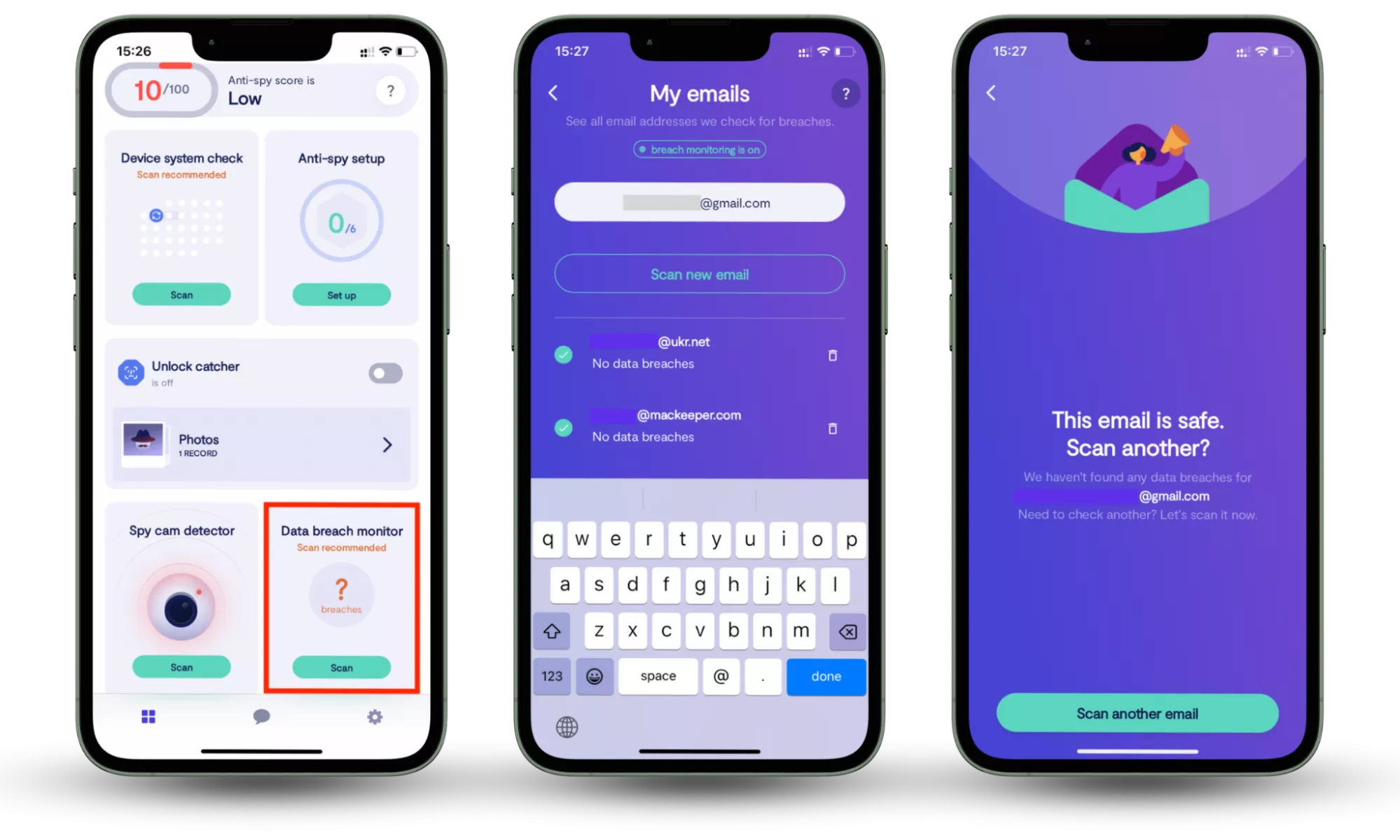
Based on real-world breach response patterns, many scams originate from previously leaked emails and passwords rather than random targeting. When personal data appears in a data breach, scammers often use it to craft convincing phishing messages or impersonation attempts. Tools such as Clario Anti Spy’s Data Breach Monitor continuously check whether your personal information has been exposed online and alert you early, giving you time to secure accounts before scammers can exploit the data.
How to check whether your information has been exposed in a data breach:
- Install Clario Anti Spy and activate the Data Breach Monitor feature.
- Click Scan under Data Breach Monitor.
- Enter the email address you want to check.
- Review the results and follow the in-app guidance.
- Repeat the scan for other email addresses you actively use.
How to silence unknown callers on your phone
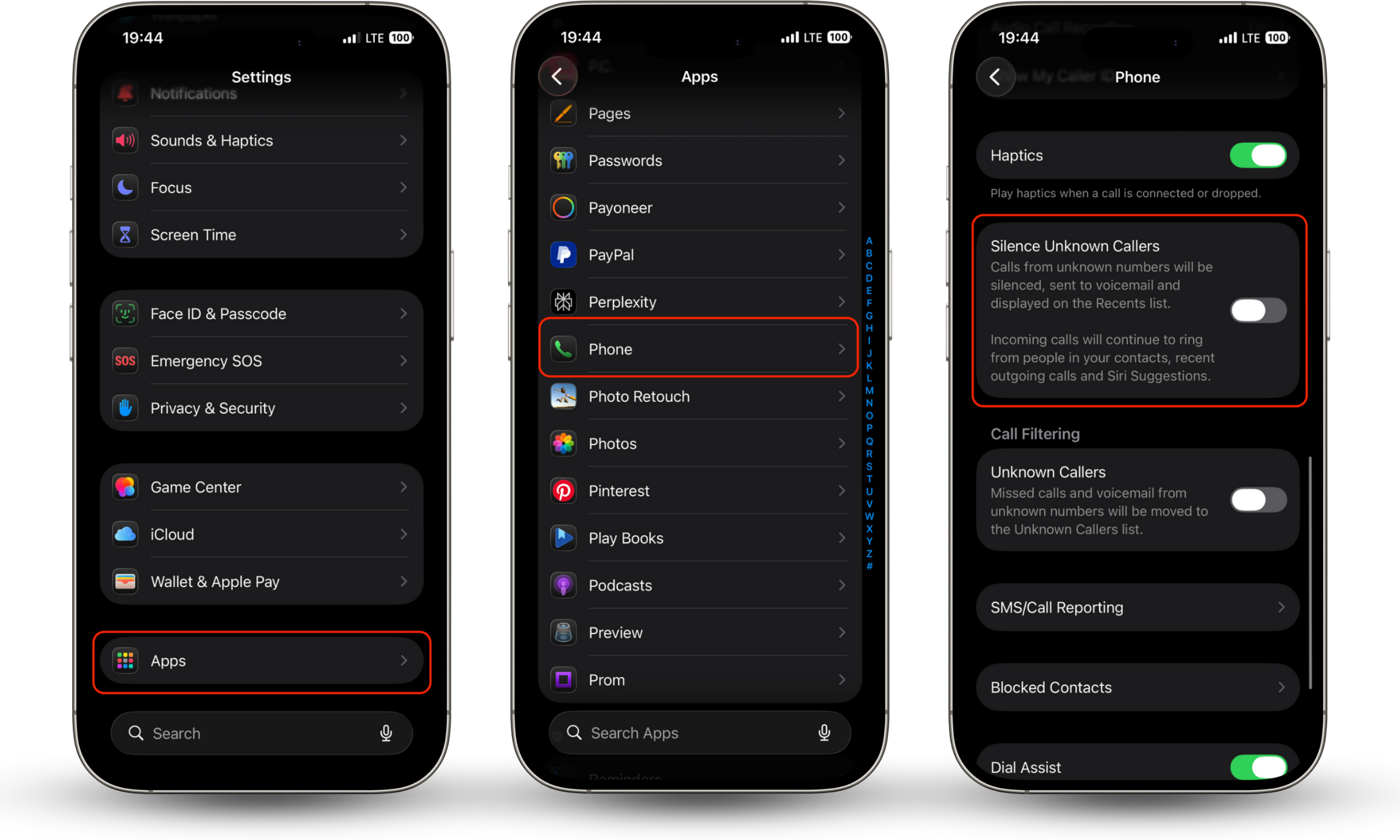
You can also change your iPhone or Android settings to only allow phone calls from individuals in your address book. While it is true that any calls from individuals outside your address book will go to voicemail, it will then allow you to evaluate these calls without any pressure.
On iPhone:
- Open Settings > go to Apps > search for Phone.
- Select Silence Unknown Callers.
- Turn the feature on to automatically send calls from unknown numbers to voicemail.
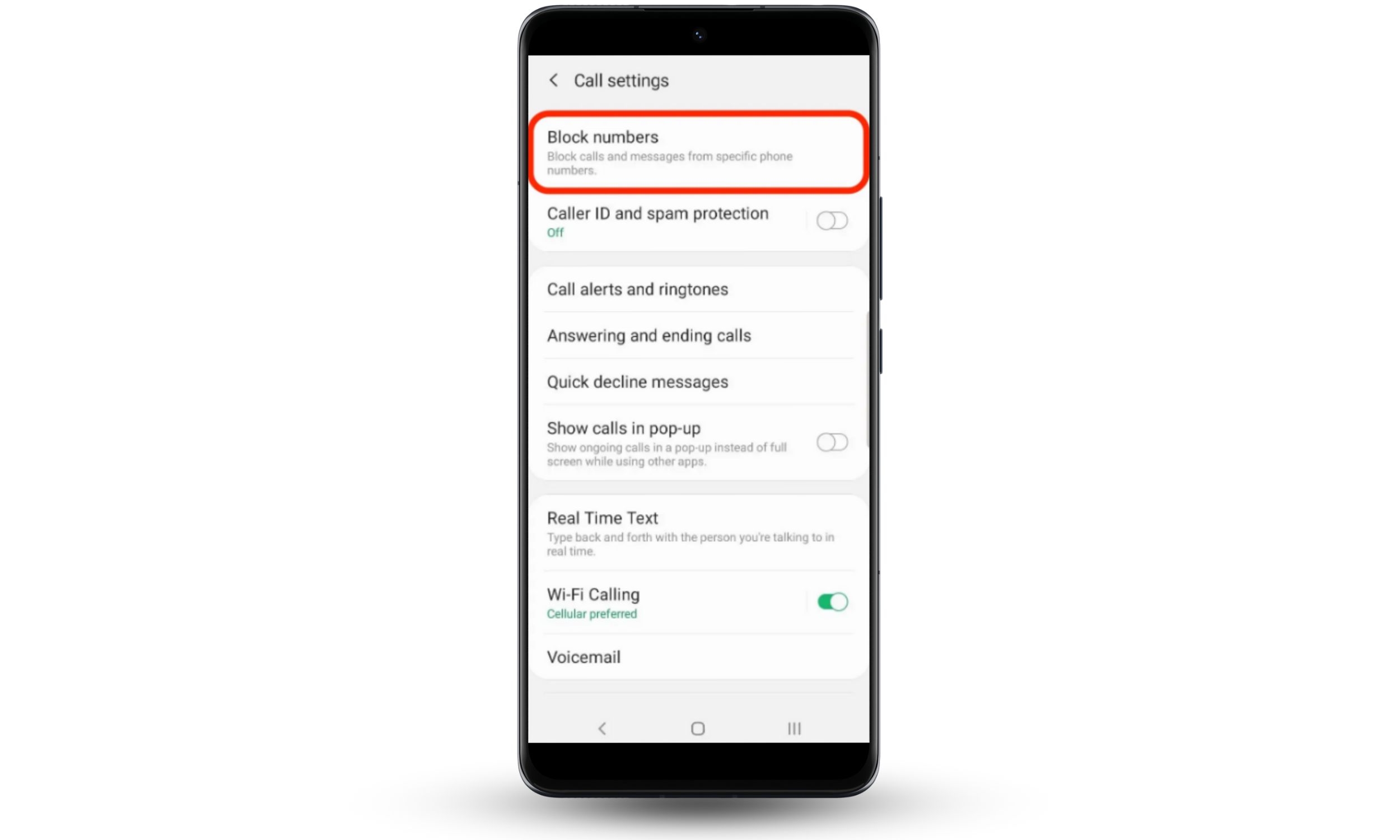
On Android (steps may vary by device):
- Open the Phone app and go to Settings.
- Look for Call blocking, Spam protection, or Unknown call silencing.
- Enable options that block or silence calls from numbers not in your contacts.
Security analysts consistently find that reducing real-time interaction with unknown callers lowers the success rate of pressure-based phone scams.
Conclusion
Being the victim of fraud or a scam can be a frustrating and terrifying experience. However, like with many things, to be forewarned is to be forearmed. Understanding the kinds of threats, and the appropriate responses, can go a long way toward protecting you from scams, mitigating the damage and recovering any money should you fall victim to one.
As with many online threats, speed is of the essence. The faster you take action, the less damage you are likely to suffer as a result of an online scam.
For added protection, install Clario Anti Spy to protect your identity, secure your data, protect your banking and transactions, and notify you the instant something suspicious happens. If something does go wrong, 24/7 human support provides the assistance you need to mitigate the damage and get back on track.
Read more:


