Table of contents
- Business email compromise vs. phishing
- BEC vs. phishing vs. vendor fraud
- Anatomy of BEC
- How BEC works
- Types of BEC
- Who does BEC target?
- Why is protection from BEC so important now?
- What to do if you suspect a BEC incident
- The most famous BEC scams
- Google and Facebook
- Scoular
- Ubiquiti
- How to prevent BEC
- Conclusion
Business email compromise vs. phishing
The difference between business email compromise vs. phishing is that the attacker already has the credentials or a believable way to pretend to be another company representative, contractor, vendor, or client. This way, they can persuade legitimate employees to perform actions that would benefit the hacker. The usual outcome of a business email attack is the loss of money or confidential information. According to Verizon's 2024 Data Breach Investigations Report, financially motivated attacks continue to be the most common ones, so business email compromise is also gaining popularity.
| Aspect | Business email compromise (BEC) | Phishing |
| Targeting | Highly targeted, specific employees or departments | Mass or semi-targeted campaigns |
| Sender appearance | Impersonates executives, vendors, or partners | Often generic or unfamiliar senders |
| Use of malicious links | Often no links or attachments | Commonly includes links or attachments |
| Primary goal | Financial fraud or data theft | Credential theft or malware delivery |
| Detection difficulty | Very high due to contextual legitimacy | Lower, often caught by filters |
| Typical emotional trigger | Urgency, authority, trust | Fear, curiosity, rewards |
BEC vs. phishing vs. vendor fraud
Unlike traditional phishing, business email compromise does not rely on mass emails or obvious malicious links. BEC attacks are highly targeted and often reference real invoices, internal processes, or existing vendor relationships. Vendor fraud, a common BEC subtype, focuses on subtly changing payment details rather than requesting a new action. This makes BEC significantly harder to detect using standard email filters or basic user awareness.
Anatomy of BEC
An attempt at business email compromise usually consists of a message sent from a hacked or a falsified account of a person in a powerful position within a company. The transfer of money or data then takes place, and the attacker vanishes. Lately, BEC has become such a serious and widespread problem that even the Australian Cyber Police provided recommendations on how to avoid and protect yourself against BEC.
One of the most typical signs of business email compromise, which it shares with most other phishing scams, is the urgency and non-typical nature of the request. Without the time factor, the recipient of the treacherous email is most likely to question what's required of them. However, the attackers usually exploit human psychology, using fear, threats, or pleading to get what they need. The victims are put under such circumstances that the presumed consequences of not complying with the request outweigh the possible consequences of fulfilling it.
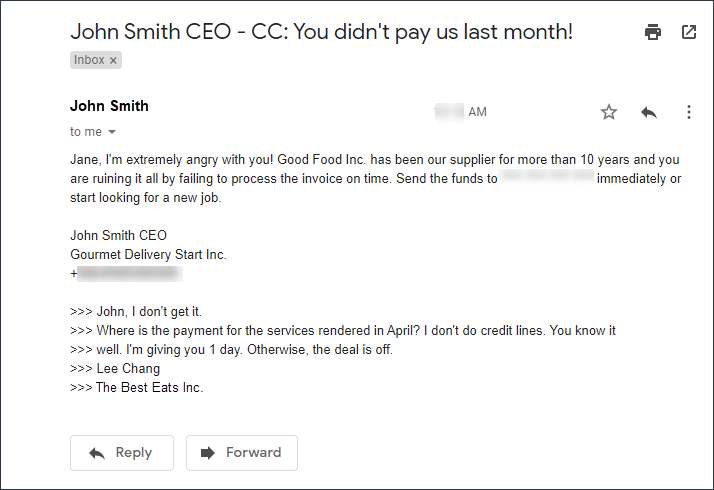
How BEC works
To compromise the initial gateway email or to trick the receivers of the BEC email, the attackers will use one of the following methods:
- Spoofing of websites, email, or even instant messenger accounts
- Spear phishing to target select employees or
- Malware running within the organization's infrastructure
At first, the attacker gets access to a business email account belonging to a top manager (hence the "CEO attack" nickname). Next, they reach their goals by manipulating the employees. Phishing plays a big role in this. In business email compromise cases, the average time it takes a person to fall for a phishing scam is under 60 seconds.
This rapid response is increasingly driven by AI-assisted attacks, where emails are written to closely match a real executive’s tone, vocabulary, and communication habits. When combined with mobile email usage and high-pressure work moments, this makes fraudulent requests appear both legitimate and urgent, reducing the likelihood of verification.
Behavioral security insight
Most successful BEC attacks exploit workflow pressure rather than technical weaknesses. Attackers intentionally time their messages during travel, payroll deadlines, or financial closings, when employees are less likely to verify requests. Teaching teams to pause and confirm unusual instructions is often more effective than adding another technical control.
An anti-spyware solution like Clario Anti Spy can go a long way toward safeguarding you from malicious BEC and phishing attacks. Its Anti-spy setup walks you through the steps needed to stay secure online. And if you need assistance, you can connect with a security expert 24/7.
Here's how to use Clario Anti Spy to protect yourself online:
- Download Clario Anti Spy and subscribe to create an account.
- Tap Set up under Anti-spy setup.
- Follow the on-screen suggestions to secure your device.
- Tap the Messages icon on the main screen for expert assistance for anything security-related.
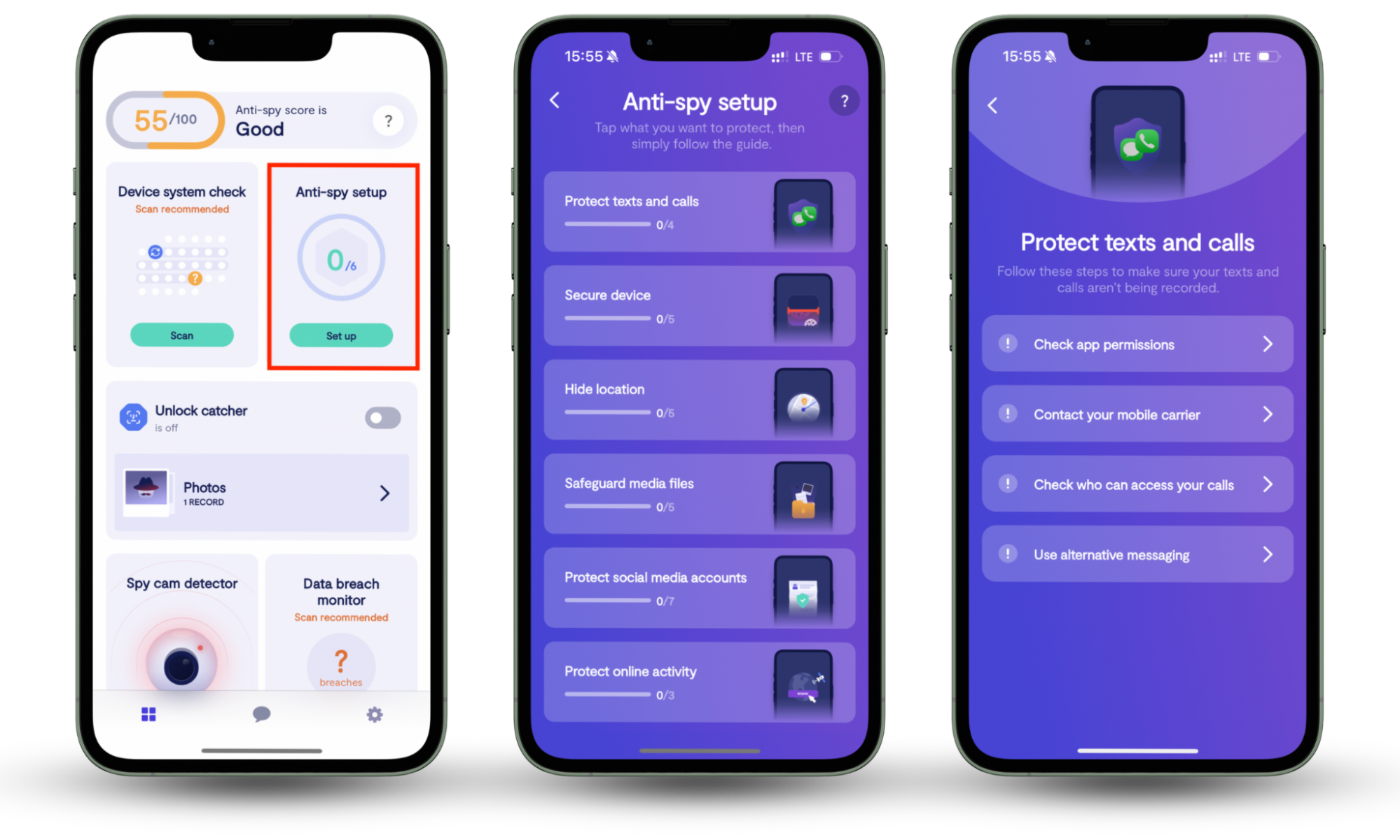
Clario Anti Spy protects your device in multiple other ways. It scans for hidden jailbreaks, detects outdated system software versions, and alerts you to data breaches associated with your accounts. On Android, it also includes a spyware scanner to ensure your device stays free from malicious software.
Types of BEC
A business email compromise scam where the attacker gains access to an email within the business infrastructure (hence causing email system compromise) is also called email account compromise. Most often, during the BEC, the attacker only impersonates somebody and pretends to be sending the messages through a legitimate gateway — using tactics like domain spoofing or display name spoofing.
The most common types of BEC are:
- Fake CEO (Fake boss) — the money, property, or sensitive info/permissions are stolen by somebody pretending to be a C-level manager of the attacked company.
- Fake invoice scam — money is lost to a fake legitimate-looking invoice.
- Wire transfer fraud — similar to a fake invoice scam, but the wire transfer is requested to a 'drop' account from which it is immediately transferred further until the money is untraceable.
- Fake lawyer — attackers impersonate a legal representative of the company or its business partner to lay their hands on sensitive legal information.
- Fake HR — an attacker that impersonates HR staff gets access to personal employee information.
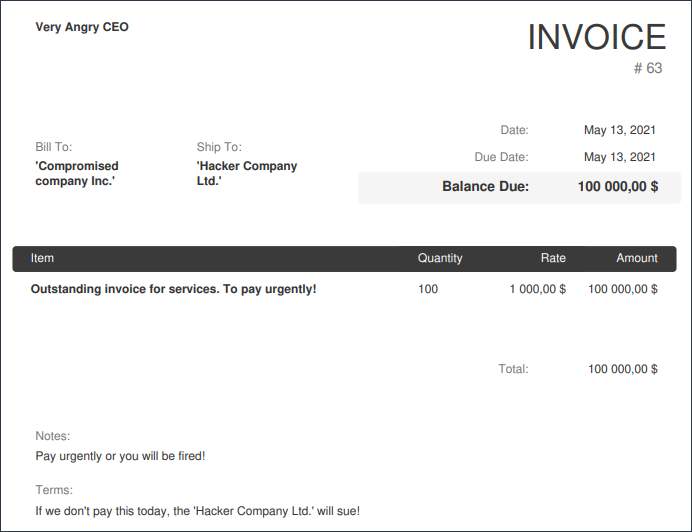
In BEC, a hacked business email may be used for targeting other employees, suppliers, or clients. This will usually be a manager or a business partner (for example, a supplier) asking for a specific action.
Who does BEC target?
The most likely targets of a BEC are:
- Companies with a large number of employees and complicated business processes.
- Research and development companies whose trade secrets, discoveries, or inventions are of great interest to their competitors.
- Companies that deal with large sums of money regularly so a "lost" invoice for several hundred thousand dollars won't seem out of place.
- Companies whose top management is away on a business trip, so out-of-place after-hours requests made from unknown phone numbers or email accounts won't seem unusual.
The one common denominator here is that the companies have something of interest for hackers, and the fraud won't be easily recognized.
Why is protection from BEC so important now?
Unfortunately, the transition to remote working during the global pandemic helped increase the numbers in business email compromise statistics. Many of us have switched to the working-from-home model, and we're using our personal devices for working purposes (and the other way around, too). This, plus the absence of the physical office's security infrastructure, obviously puts us at much greater risk.
According to the FBI's Internet Crime Complaint Center (IC3), Business Email Compromise was the second-costliest type of cybercrime in 2023, with 21,489 complaints resulting in reported losses of approximately $2.9 billion. The average loss per BEC incident has also risen, with the average cost per complaint increasing from $74,723 in 2019 to $137,132 in 2023.
What to do if you suspect a BEC incident
If you suspect a business email compromise, immediately stop any ongoing transactions and notify your IT or security team. Contact your bank or payment provider as soon as possible, as early reporting increases the chances of fund recovery. Reset compromised credentials and review email forwarding rules, which attackers often modify to stay hidden. Prompt action can significantly limit financial and data damage.
The most famous BEC scams
Due to the nature of the scam — as it deals with hacking humans as opposed to systems — business email compromise examples include companies of all sizes and from all industries. From 2019 to 2024, 84.7% of surveyed firms experienced cyberattacks.
Google and Facebook
The early days of BEC also saw one of the biggest and the most ambitious attacks — the one against Facebook and Google, which led to $121 million in losses between 2013 and 2015. The person behind these attacks, Evaldas Rimasauskas, got a 5-year prison sentence for this fraud in 2019.
Scoular
This has been one of the most significant BEC cases ever. An employee of the Scoular company transferred $17.2 million to a Shanghai bank account following the request in a fake email that pretended to come from the company's CEO.
Ubiquiti
$46.7 million was lost by a company called Ubiquiti due to business fraud. The attackers used BEC and pretended to be an external company that successfully demanded and received money from Ubiquiti's financial department.
How to prevent BEC
These are the steps you should take to prevent business email compromise:
- Realize that your company is just as vulnerable to such an attack as any other.
- Set workplace rules on using two-step verification for suspicious correspondence.
- Set email rules for flagging external emails.
- Require two-factor authentication in your IT infrastructure.
- Normalize confirmation requests and double-checks for unusual orders.
- Set at least a basic business email compromise policy and provide training for all new hires.
For financial and legal requests, introduce mandatory secondary verification through a separate communication channel, such as a phone call or secure messenger. Even if an email appears to come from a trusted executive or vendor, payment or data changes should never rely on email alone.
Unless the breach has been really deep and ongoing for a long time, a business email compromise attack alone won't bypass such security measures. Remember, the cost of business email compromise is always higher than the time and effort spent providing preventive training.
If BEC prevention seems complicated but you would like to make your infrastructure more secure and your employees or colleagues more cautious, you should consider asking trusted security experts for help. With Clario Anti Spy you can consult our experts 24/7 if you have any doubts over the authenticity of any email.
When it comes to your company's security, it's better to err on the side of caution than regret your carelessness later. Keep your guards up and question anything suspicious that ends up in your email.
Conclusion
Business email compromise is no longer a rare or sophisticated edge case — it’s a daily risk driven by trust, urgency, and increasingly convincing impersonation tactics. As BEC attacks evolve alongside remote work and personal-device usage, relying on awareness alone is no longer enough. Combining clear internal processes, employee vigilance, and device-level protection is key to reducing risk. Tools like Clario Anti Spy help close critical security gaps by detecting account breaches, suspicious activity, and system weaknesses before they can be exploited. When it comes to BEC, prevention, verification, and timely expert support can make the difference between a close call and a costly mistake.
Read more:


