Table of contents
- How secure is Apple Pay?
- 1. Biometric authentication
- 2. Tokenization mechanism
- What are Apple Pay’s vulnerabilities?
- 1. Phishing and fraud
- 2. Apple ID compromise
- 3. Risks of weak passwords
- 4. Relay attacks
- 5. Jailbreak device
- 6. Data interception
- How to protect Apple Pay from hackers
- Conclusion
How secure is Apple Pay?
Apple Pay is protected with multiple layers of security, including biometric authentication, tokenization, and hardware-level encryption. These features prevent bad actors from pulling your card details or making unauthorized payments. However, there are still risks to watch out for, such as phishing scams, online fraud, weak Apple ID security, and jailbroken devices.
1. Biometric authentication
Apple Pay only works after you confirm a payment with Face ID, Touch ID, or the device passcode. All of your biometric data stays locked inside your iPhone's Secure Enclave (an isolated hardware component) and never gets uploaded anywhere. Even if someone steals your phone, they cannot approve payments without passing that authentication step.
2. Tokenization mechanism
With Apple Pay, your credit card is swapped with a Device Account Number (or token) and stored locally in another isolated area called the Secure Element. This token is encrypted at the hardware level, and every transaction requires biometric authentication to use it. If your iPhone goes missing, you can disable the token through Find My without cancelling the actual card.
Despite Apple Pay's strong security, you can still get caught out by other attack methods if your iPhone is compromised. Jailbroken devices, for example, are much easier for attackers to exploit.
This is where Clario Anti Spy can help. Its Device system check quickly verifies that your phone isn't jailbroken and that you're running the latest, most secure version of iOS.
Here's how to run a Device system check with Clario Anti Spy:
- Download Clario Anti Spy and subscribe to create an account.
- Tap Scan under Device system check.
- Follow the on-screen instructions if anything suspicious shows up.
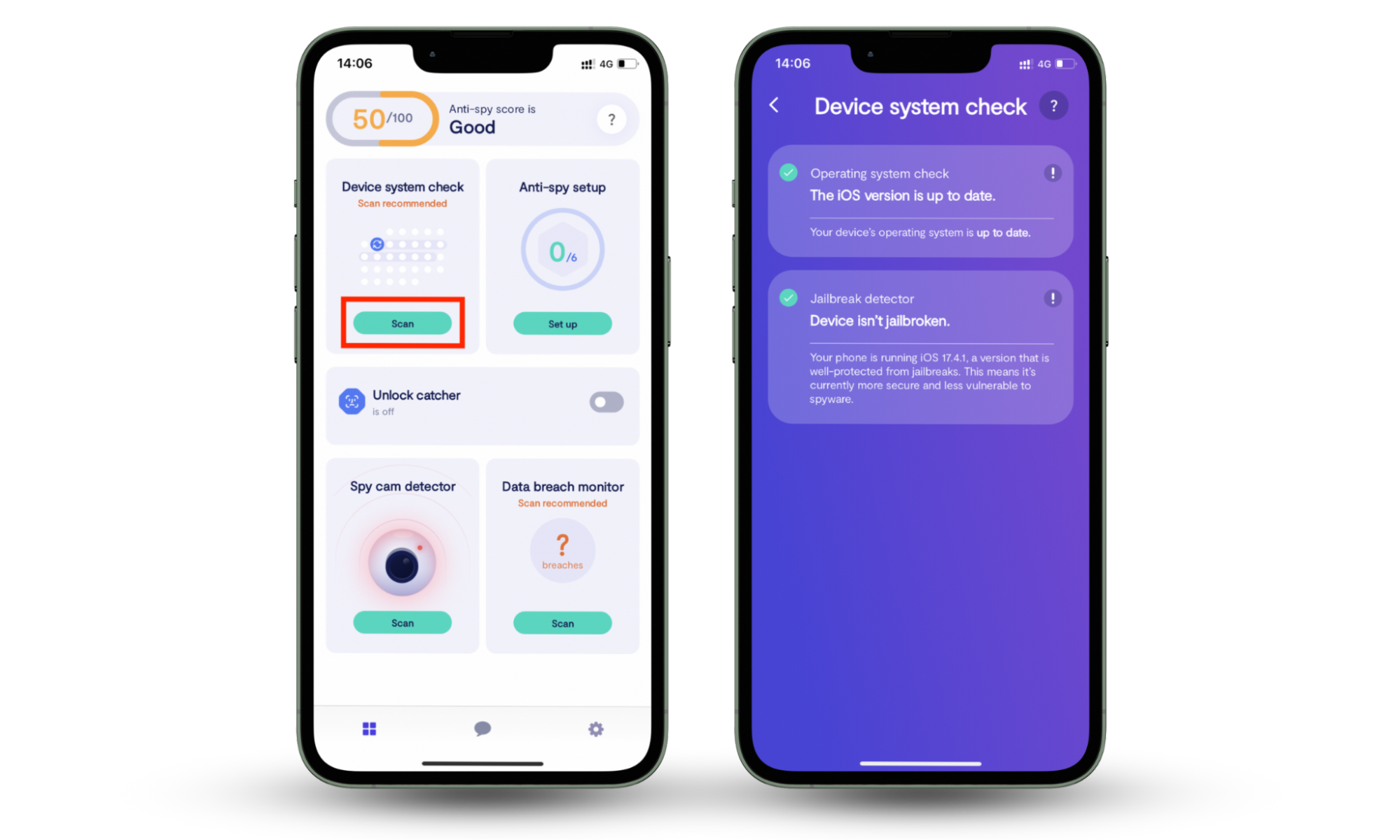
If the Device system check is all clear, it's still worth exploring other features in the app—e.g., Anti-spy setup, Data breach monitor, and Hidden app scan. These help lock down your settings, keep your online accounts safe, and make sure there's no spyware hiding on the device.
You can also tap the Messages icon to chat with a Clario expert 24/7 if you run into any trouble. They handle everything from suspicious apps to data leaks. Here's what one expert had to say about a customer who was worried about their personal data:
"A client reached out with concerns regarding the potential exposure of his personal information and requested our assistance in verifying whether any of his data had been compromised or was circulating on the dark web. In response, we provided step-by-step guidance on how to integrate his email addresses into our Data Breach Monitoring system, along with detailed instructions on reviewing breach reports and mitigating any associated risks. The client was particularly anxious to ensure that none of his sensitive information—especially financial or personally identifiable data—was being exploited without his knowledge.
Following a comprehensive scan, several breaches were detected involving the client's data. Alarmingly, the exposed information included critical personal identifiers such as credit card details and his Social Security Number (SSN). Given the severity of the findings, we promptly recommended a series of actions: contacting his financial institution to cancel the affected card and issue a replacement, initiating a credit freeze across all major credit bureaus to prevent unauthorized access, and considering the placement of a fraud alert to enhance vigilance around any future credit inquiries.
The client expressed sincere appreciation for the timely support and actionable recommendations, and confirmed his intention to leave a positive review of our services."
What are Apple Pay’s vulnerabilities?
Apple Pay is secure on its own, but the systems around it can still be exploited. Most problems come from human error, such as weak Apple ID passwords, falling for phishing scams, or using a jailbroken or compromised device. Attackers can also attempt relay attacks or take advantage of insecure public Wi-Fi networks to intercept your data.
1. Phishing and fraud
Scammers often send fake Apple emails or texts claiming there is an issue with your Apple ID or payment details. The goal is to push you into revealing sensitive information, such as credit card numbers or verification codes.
There are also other types of fraud. For example, a scammer might send you a payment "accidentally" through Apple Pay using a stolen credit card, then ask you to refund the money through a different payment method. Check our list of Apple scams for more examples of what you should watch out for.
2. Apple ID compromise
If someone gains access to your Apple ID, they can't simply sign in on a new device and start using Apple Pay without going through re-verification steps. However, they can still dig through your account. For example, if you have saved credit card numbers, screenshots, or documents, an attacker could use that information to verify your identity or even impersonate you.
3. Risks of weak passwords
Short or easy-to-guess passwords can be cracked through brute force or leaked in data breaches. If you reuse the same password on multiple sites, bad actors can test those stolen credentials on your Apple ID as well. To avoid this, always use strong, unique passwords and keep two-factor authentication turned on.
Good to know
The Data breach monitor in Clario Anti Spy can help you identify leaked passwords and alert you if your account details get compromised.
4. Relay attacks
Relay attacks are a vulnerability that security researchers discovered in 2021. The idea is that someone could grab the NFC signal from your device and pass it along to a payment terminal somewhere else. This is incredibly hard to pull off in reality, but it's still a good reminder that no system is completely foolproof.
5. Jailbreak device
Jailbreaking removes Apple's built-in security protections, and that creates a lot of room for trouble. It opens your device to malicious apps and dangerous system tweaks that would normally be blocked. These things can interfere with Secure Element communication, log what you type, or exploit other system vulnerabilities.
Once an iPhone is jailbroken, Apple Pay becomes less secure because the device can no longer guarantee that your payments or data are protected.
6. Data interception
Public Wi-Fi is extremely insecure and can expose you to data interception. For example, a bad actor on the same network can redirect you to a fake Apple Pay page when you're about to make a payment. The hacker could then get your credit card and CVV numbers by asking you to fill them in under the guise of "verification."
How to protect Apple Pay from hackers
Keeping Apple Pay secure mostly depends on how well you protect your device and Apple ID. Make sure to use a strong, unique password, turn on two-factor authentication, and keep your iPhone up-to-date. Also, avoid risky public Wi-Fi, never jailbreak your device, and disable Apple Pay through Find My iPhone if your phone goes missing.
Here's how to prevent someone from hacking your Apple Pay:
- Keep iOS up to date so that you are protected from known security flaws.
- Use a strong Apple ID password and turn on two-factor authentication.
- Stay alert for phishing scams and other online fraud.
- Never jailbreak your device, as this exposes you to many types of attacks.
- Use cellular data or a VPN over public Wi-Fi to reduce the risk of data interception.
- Mark your iPhone as lost in Find My to disable Apple Pay if the device goes missing.
- Set up a fraud alert if you think your personal information is at risk.
Conclusion
Can Apple Pay be hacked? With biometrics, tokenization, and hardware-level encryption all working together, direct hacks are extremely unlikely. The real risks usually come from weak passwords, phishing attempts, or using a device that is already compromised. If you follow basic security practices, you should be all good.
If you have concerns about your iPhone's security, you can always download Clario Anti Spy and run a quick Device system check to make sure everything's clean and up to date.


