Table of contents
- How hackers use images to infiltrate your phone
- 1. Exploit vulnerabilities in image files
- 2. How malicious code can be embedded in images
- 3. Other common image-related threats
- How to protect your phone from picture-based hacks
- 1. Precautions to take when receiving images
- 2. Updating software and using security features
- 3. Recognizing phishing and avoiding suspicious links
- Conclusion
How hackers use images to infiltrate your phone
Cybercriminals can use images to infiltrate your phone in a few different ways. The most sophisticated—and rarest—method involves hiding malicious code inside the image's raw data, which can trigger when the file is opened. More common techniques involve disguising malware as fake image files or embedding photos with links that lead to phishing sites.
1. Exploit vulnerabilities in image files
Hackers often take advantage of bugs in the way mobile system software processes images. By creating malicious images that exploit these flaws, they can run unauthorized code on your device. For example, in 2019, a serious flaw in Android's handling of PNG files let attackers insert harmful code that could take full control of the device once the image was opened.
2. How malicious code can be embedded in images
A process called "steganography" allows attackers to hide malicious code inside photos. One example is Stegosploit, which is an exploit involving hidden JavaScript code in the pixel data of an image. When the image loads in a browser, the hidden script runs automatically and launches malware or steals sensitive information.
Another method someone can use to hack your phone is by texting you a picture, which involves editing an image's EXIF metadata, which stores details like camera settings. Hackers can insert malicious scripts into these fields, which may execute when the photo is processed.
3. Other common image-related threats
Besides embedding malicious code, there are several other image-based tactics to compromise devices and steal information. These include:
- Malicious links via MMS: Attackers can send MMS messages with photos that contain embedded links to phishing sites or malware downloads. These images are usually attention-grabbing and designed to trick the user into tapping. By the way, can you get hacked by responding to a text?
- Fake image attachments in messaging apps: Users might receive image files over instant messengers or emails that look harmless but are actually disguised executables (e.g., photo.jpg.apk). Opening these files can sideload spyware and allow hackers access to the device.
- Infected images on social media: Bad actors also target social media platforms by posting images that redirect users to malicious websites or start unwanted downloads. For instance, the Dorkbot malware spread via social media channels by luring users into tapping on infected images.
Clario Anti Spy is an anti-spyware solution designed to protect both iOS and Android phones from cyber criminals. Its Device system check feature easily detects hidden jailbreaks, device rooting, or system software vulnerabilities that could expose the device to image-based attacks and other threats.
Here's how to run a Device system check with Clario Anti Spy:
- Download Clario Anti Spy and subscribe to create an account.
- Tap Scan under Device system check.
- Wait for the scan to complete, then follow any on-screen instructions to handle potential threats.
- If you need help, tap the Messages icon to connect to a security expert 24/7.
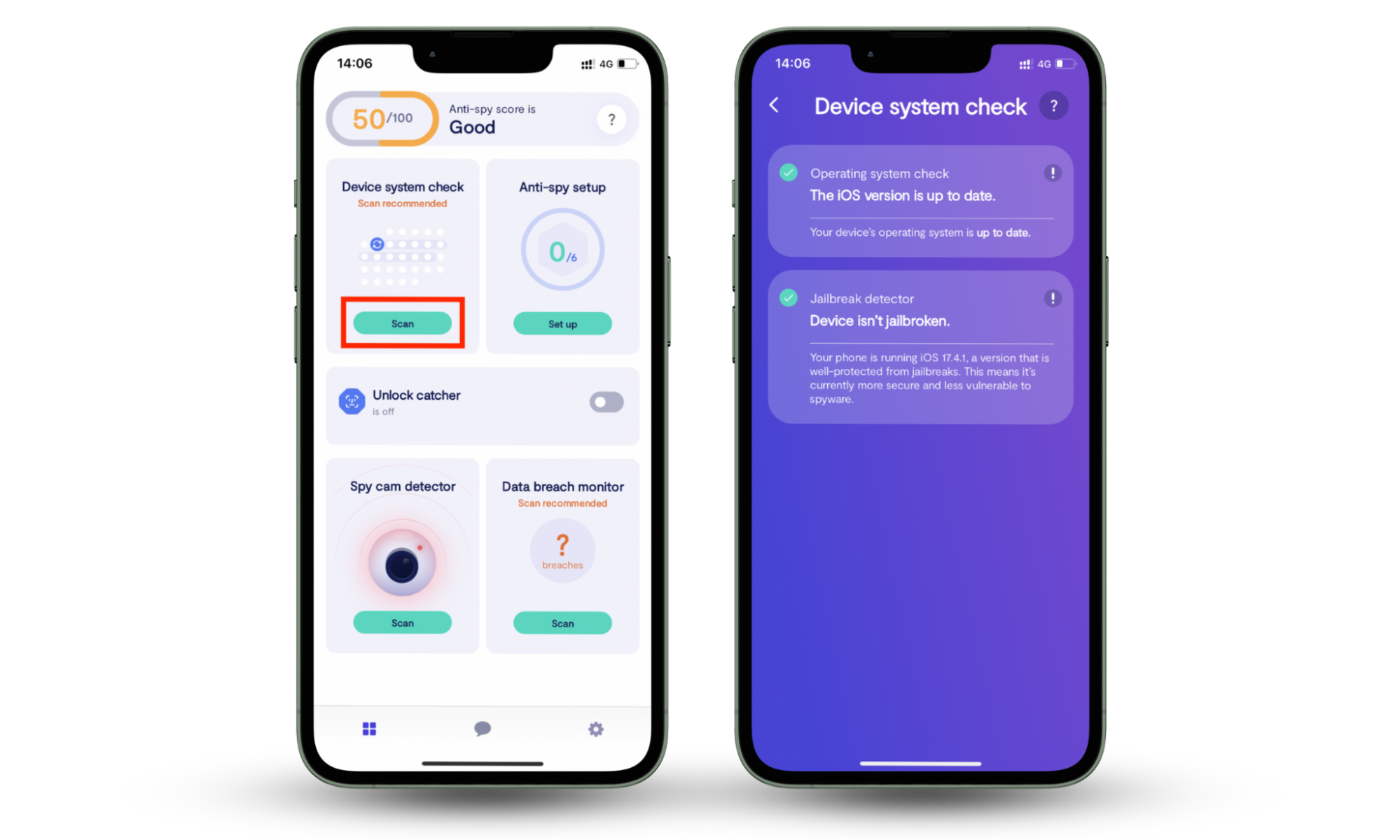
You also gain access to several other tools to keep your phone secure. For instance, the Anti-spy setup walks you through everything you need to tighten your privacy settings, the Data breach monitor alerts you if your email or passwords have been leaked, and Spyware scan detects privacy-invasive Android apps.
How to protect your phone from picture-based hacks
You can protect your phone from image-based threats by being cautious when receiving images, keeping your system software and apps up to date, and making use of available security features.
1. Precautions to take when receiving images
- Be cautious with unknown senders: Always avoid tapping on photos you receive from people you don't know over MMS, email, or chat apps. These image files could be used to deliver malware. If you accidentally tap on a sketchy-looking image, a mobile hack checking number can tell you if your phone is hacked.
- Verify unexpected messages: Got an image from someone you know but it somehow feels off? Their account may have been compromised, so double-check with them through a different channel before opening it.
2. Updating software and using security features
- Keep your software up to date: Install new iOS, Android, and app updates as soon as they become available. Apple, Google, and app developers release regular patches to fix security vulnerabilities that hackers could exploit.
- Use Google Play Protect: On Android, you can take advantage of Google Play Protect (go to Play Store > Profile > Play Protect) to scan for malicious apps.
- Review app permissions: Routinely check which permissions your apps have (Settings > Privacy & Security on iOS or Settings > Apps > Permissions on Android). Make sure they only access what's necessary—nothing more.
- Invest in an anti-spyware solution: For extra precaution, use Clario Anti Spy to detect system software vulnerabilities and hidden threats.
3. Recognizing phishing and avoiding suspicious links
- Watch for signs of phishing: Stay alert for messages that create a sense of urgency, use generic greetings, or ask for personal information. These are classic red flags of phishing scams.
- Avoid suspicious links and downloads: Never click on links or download attachments from unfamiliar senders. These could lead to malicious websites or trigger malware downloads.
- Don't blindly trust legitimately-looking messages: If a message claims to be from a known company but looks suspicious, use official channels to confirm it's legitimate.
Think you've already been hacked? Update the passwords for your online accounts immediately. Then, check our guides on how to remove a hacker from your phone and how to find who hacked your phone.
Conclusion
Yes, someone can hack your phone by texting you a photo—especially if the image contains hidden malicious code and your device has unpatched vulnerabilities. That said, these attacks are rare and usually rely on a specific set of conditions to work.
The good news? You can greatly reduce your risk by staying cautious with unknown files, keeping your software up to date, and practicing good cybersecurity habits. Clario Anti Spy can also add an extra layer of protection to help keep your device safe and spyware-free.


