Table of contents
- What is a Keylogger?
- How to detect a keylogger?
- On Windows
- Clean Windows Registry
- On Mac
- How to remove a keylogger from Windows
- Uninstall programs
- Clear temporary files
- Reset your PC
- How to remove a keylogger from Mac
- Why are keyloggers dangerous?
- How do keyloggers infect your device?
- How to bypass an active keylogger
- Do mobile devices get keyloggers?
- Protect yourself from keyloggers
What is a Keylogger?
A keylogger is a form of spyware used by hackers and criminals to record each keystroke you make. That means everything you type into your laptop is saved and sent to the person on the other end — including your passwords, emails, searches, and private information.
The sole purpose of a keylogger is to record your keystrokes on a keyboard or taps on a smartphone or tablet. Keyloggers are able to bypass anonymous browsers as they are installed directly onto your devices.
How to detect a keylogger?
When using your device, there are multiple signs to look out for that may help you identify if a keylogger is affecting your device.
- A slow/buffering browser.
- Delayed response to mouse movements or keystrokes.
- A disappearing cursor.
Instead of guessing whether your device is just acting slow, or if you do, in fact, have a keylogger tracking your movements — we will highlight the best ways you can find them so you can become an expert keylogger checker.
On Windows
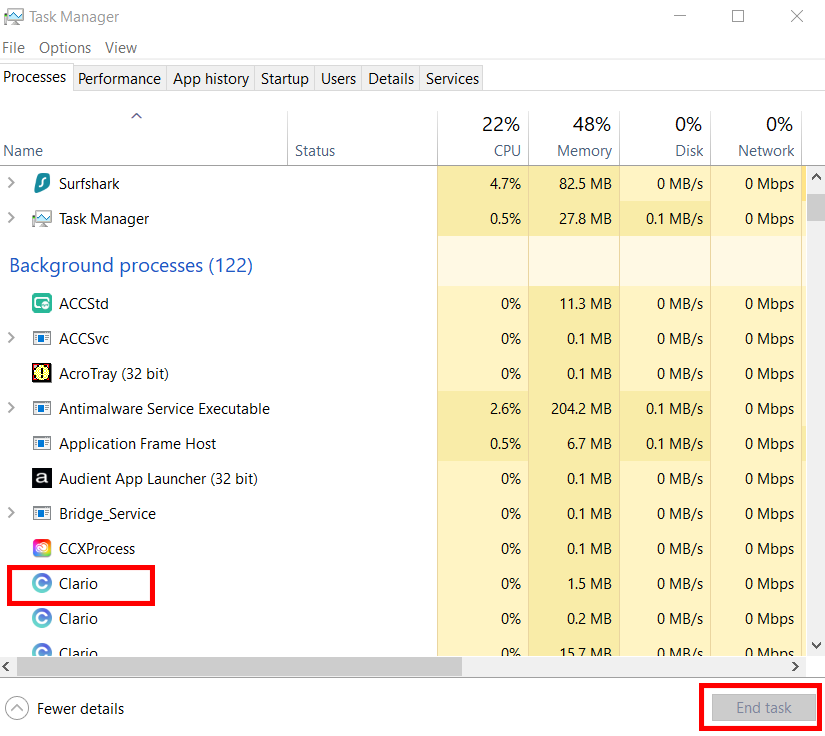
Check the Task Manager
The Task Manager can quickly identify an unknown process in the background and allow you to end the task fast. Follow these simple steps to check your Task Manager for a keylogger:
- Right-click the Windows button and left-click Task Manager
- Click the drop-down arrow More Details to open the full list of processes
- Check what programs are running in the background, and if you notice any unusual programs you don’t remember installing, a quick google search can identify whether it is harmful. After determining if it is needed or not, simply press End task.
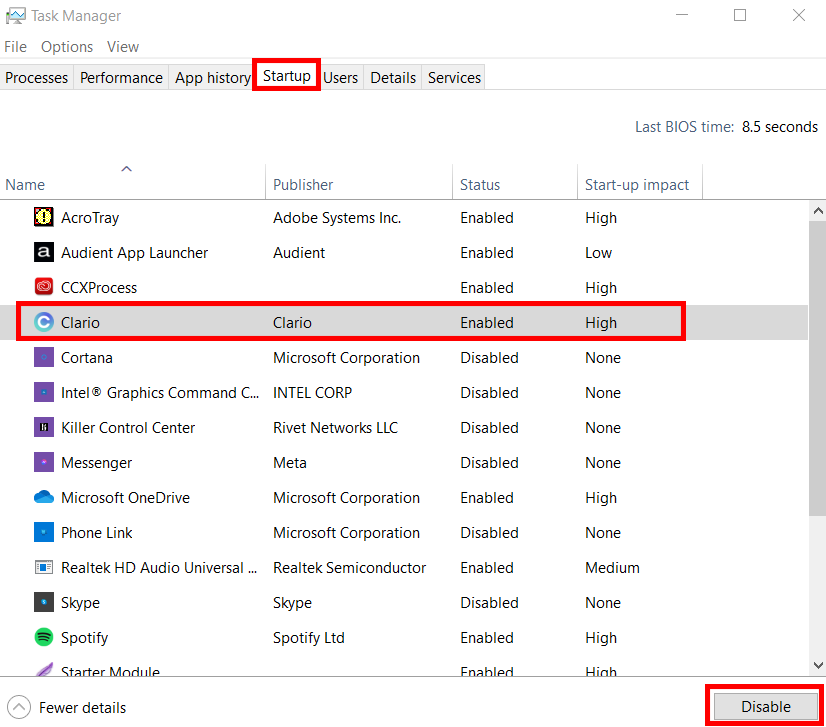
4. Moving over to the Startup tab will bring up the programs which launch on the startup of your device.
5. Again, if you see a program you don’t recognize, look them up online and see if they are dangerous to your device and press Disable.
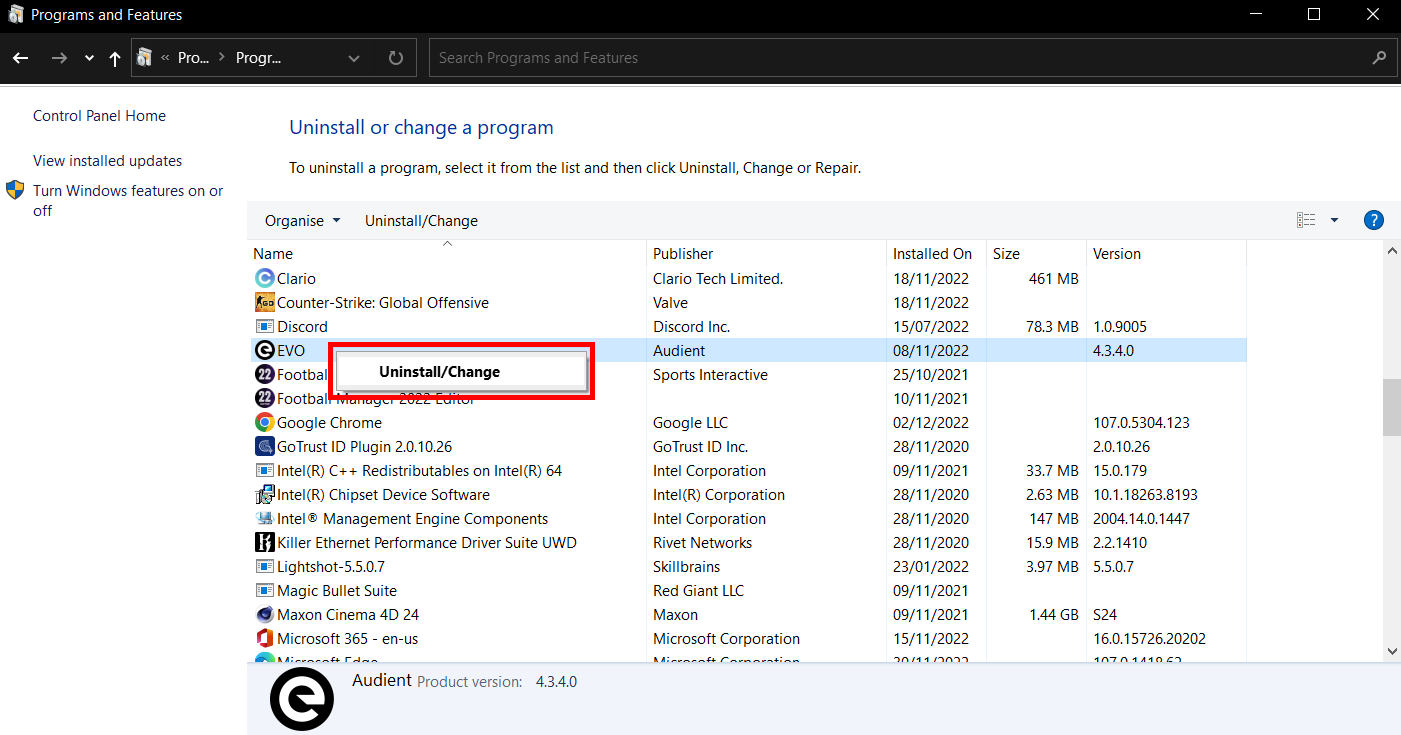
Use Control Panel to inspect programs and features
By launching the programs and features section of your control panel, it will load up a list of every program currently installed on your device. Using this menu, you can track down any unusual programs that you don’t remember installing or have no use for anymore and remove them.
Follow these steps to launch the programs and features page from your control panel:
- Launch the Start Menu by clicking the Windows button in the bottom-left corner
- Type “Control Panel” in and click the Control Panel App
- Click Programs
- Press Programs and Features
- Scroll down the list and look for any unusual or suspicious programs. If you spot one, search it up online and check if it is harmful.
- If yes, right-click the program and press Uninstall.
Clean Windows Registry
When an application is installed on your device, it creates registry keys essential for the program's function. When you uninstall or remove a program, the registry keys may be left behind, so it is important to clear any remnants left behind when you uninstall applications on your device.
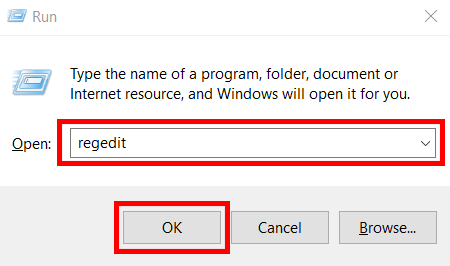
Follow these steps to access your Windows Registry:
- Press the Windows Key + R Key together to launch the Run command
- Type ‘regedit’ into the Open section and press OK to launch the registry editor
3. On the left-hand bar, double-click to expand the HKEY_CURRENT_USER folder
4. Scroll down to the SOFTWARE folder and double-click to expand it
5. Look through the folders listed in the SOFTWARE Folder and right-click on and press Delete on any program names you know you have since deleted from your device
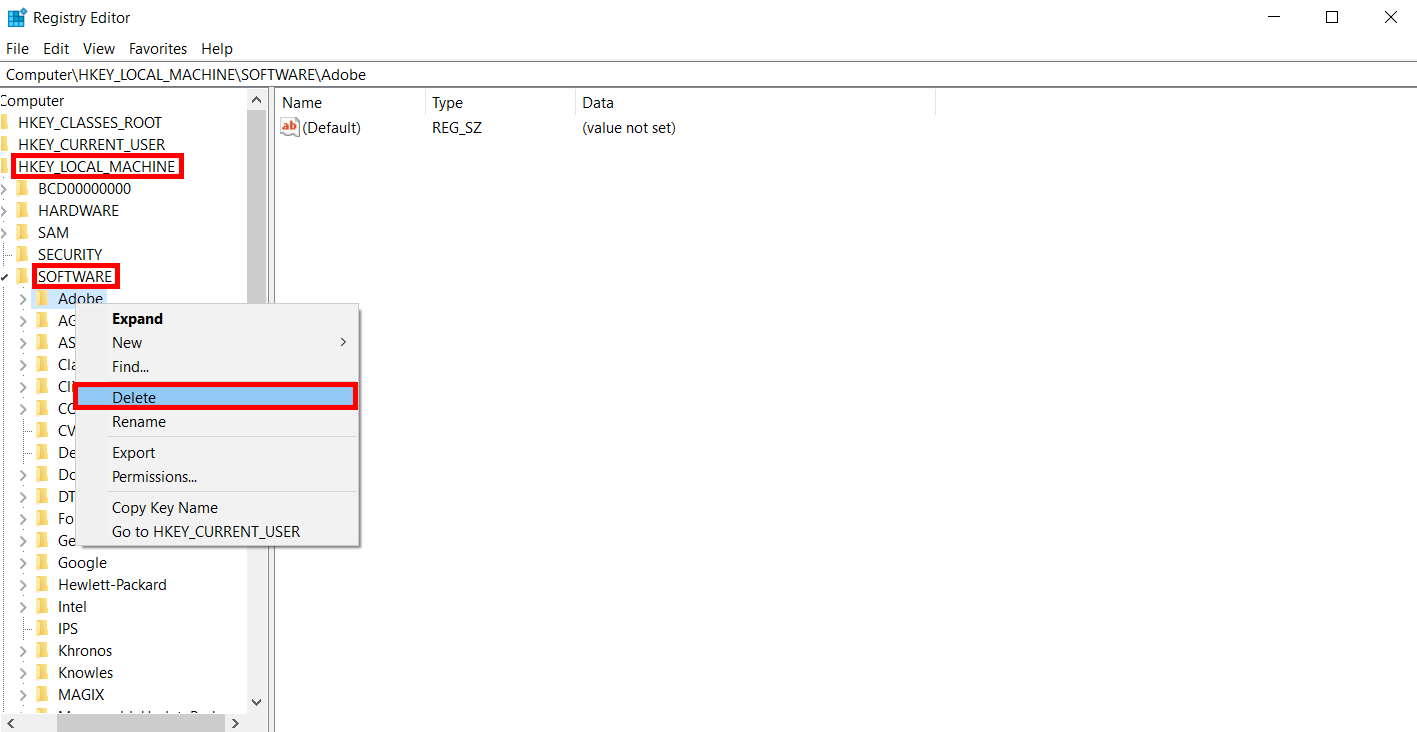
6. Double-click on the SOFTWARE and HKEY_CURRENT_USER folders to minimize them.
7. Double-click on HKEY_LOCAL MACHINE, then double-click on SOFTWARE folders to expand them.
8. Repeat step five and scroll through the sub-folders to identify any programs that have previously been uninstalled from your device, right-click on them, and press Delete to remove them.
On Mac
Scan for keyloggers using antivirus software
Anti-virus software like Clario can be a helpful keylogger detector by finding any harmful spyware on your device. If you can’t detect the problem manually, try running a deep scan on your entire Mac and see if a trusted anti-virus software can find a malicious application operating on your system.
- Download and launch the Clario app on your device
- On the Clario dashboard, press Quick scan and toggle on the Real-time Antivirus
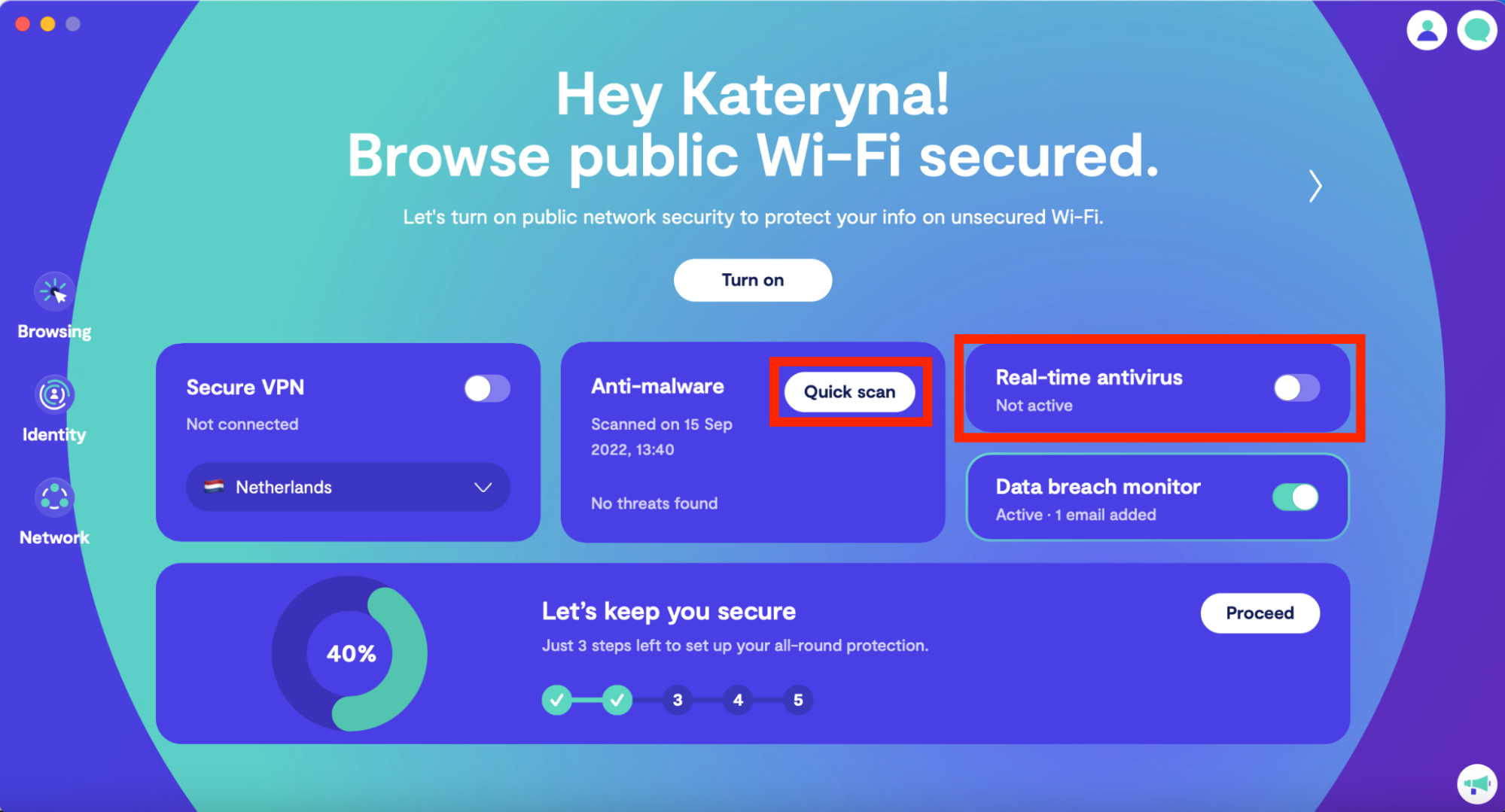
3. Once the scan is complete, follow Clario's instructions on how to get rid of the virus that infected your device.
Check your privacy and security settings
If your anti-malware scan comes back inconclusive, you can go into your device’s privacy settings and see which permissions are granted for individual apps. Here you can grant and revoke individual permissions and prevent unwanted apps from accessing certain features. Follow these steps:
- Open the Apple menu by clicking the Apple icon in the upper-left corner of your screen
- Select System Preferences
- Select Security & Privacy
- Scroll through the Full Disk Access, Screen Recording, and Accessibility tabs and look for unusual permissions
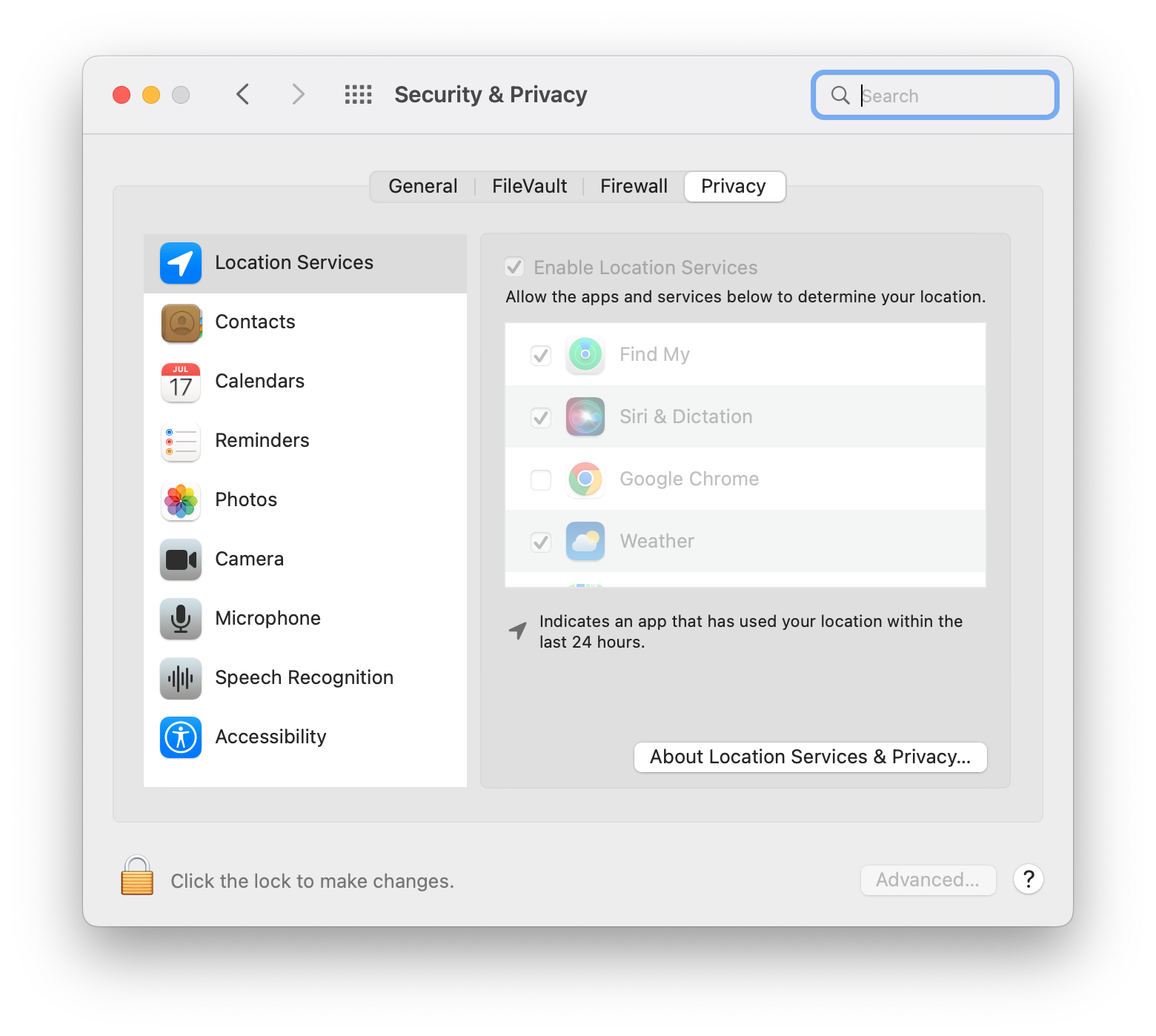
5. Select the Lock icon and enter your Apple ID password to disable the unusual permissions.
Check your Mac’s Login Items
Keyloggers can often launch upon setup. Going into your Login list can help you identify some unusual programs which are set to activate when you first log in to your Mac. Follow the steps below to access this list:
- Open the System Preferences app
- Select Users & Groups
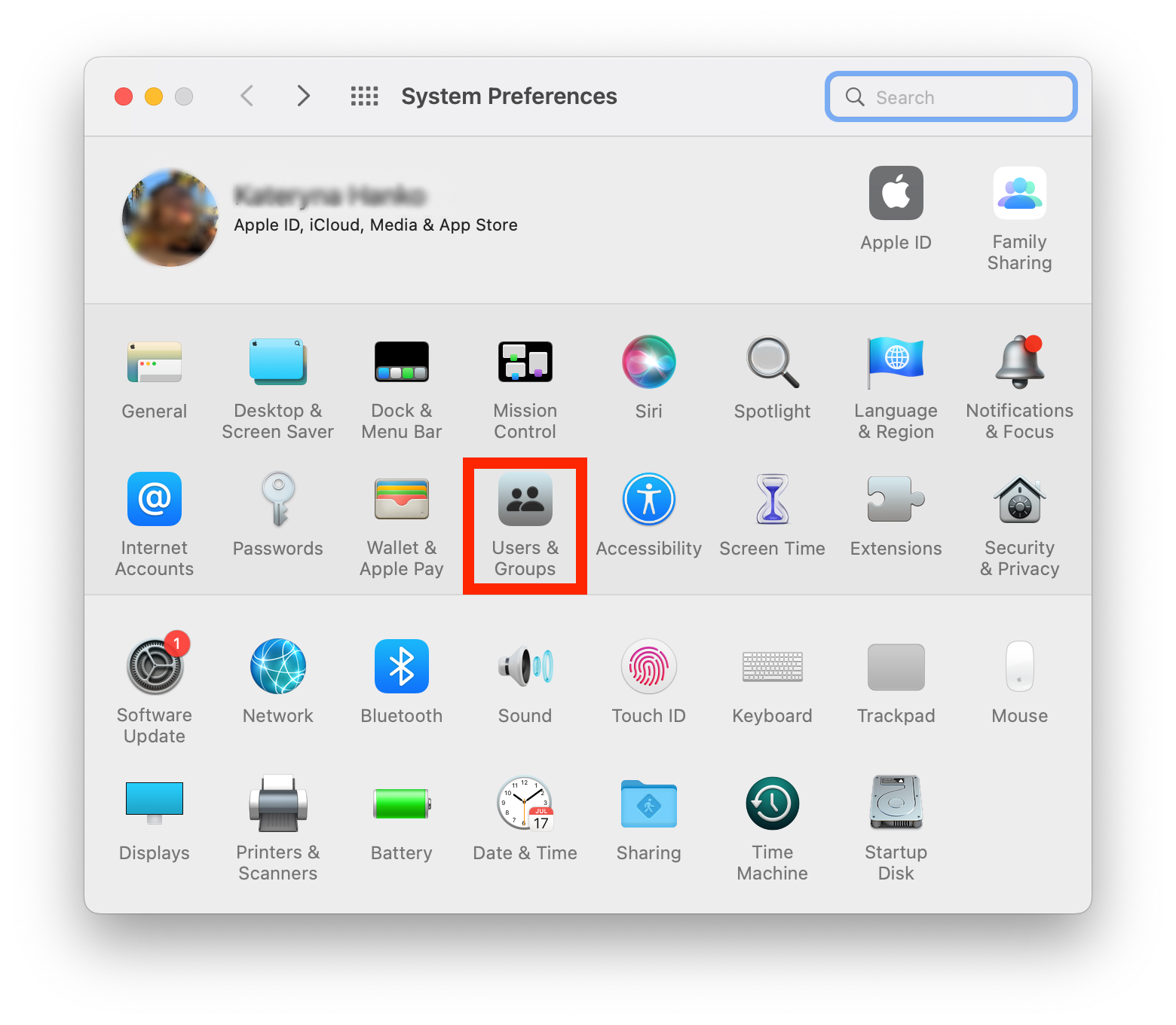
3. Click the Lock icon and enter your Apple ID password to make changes
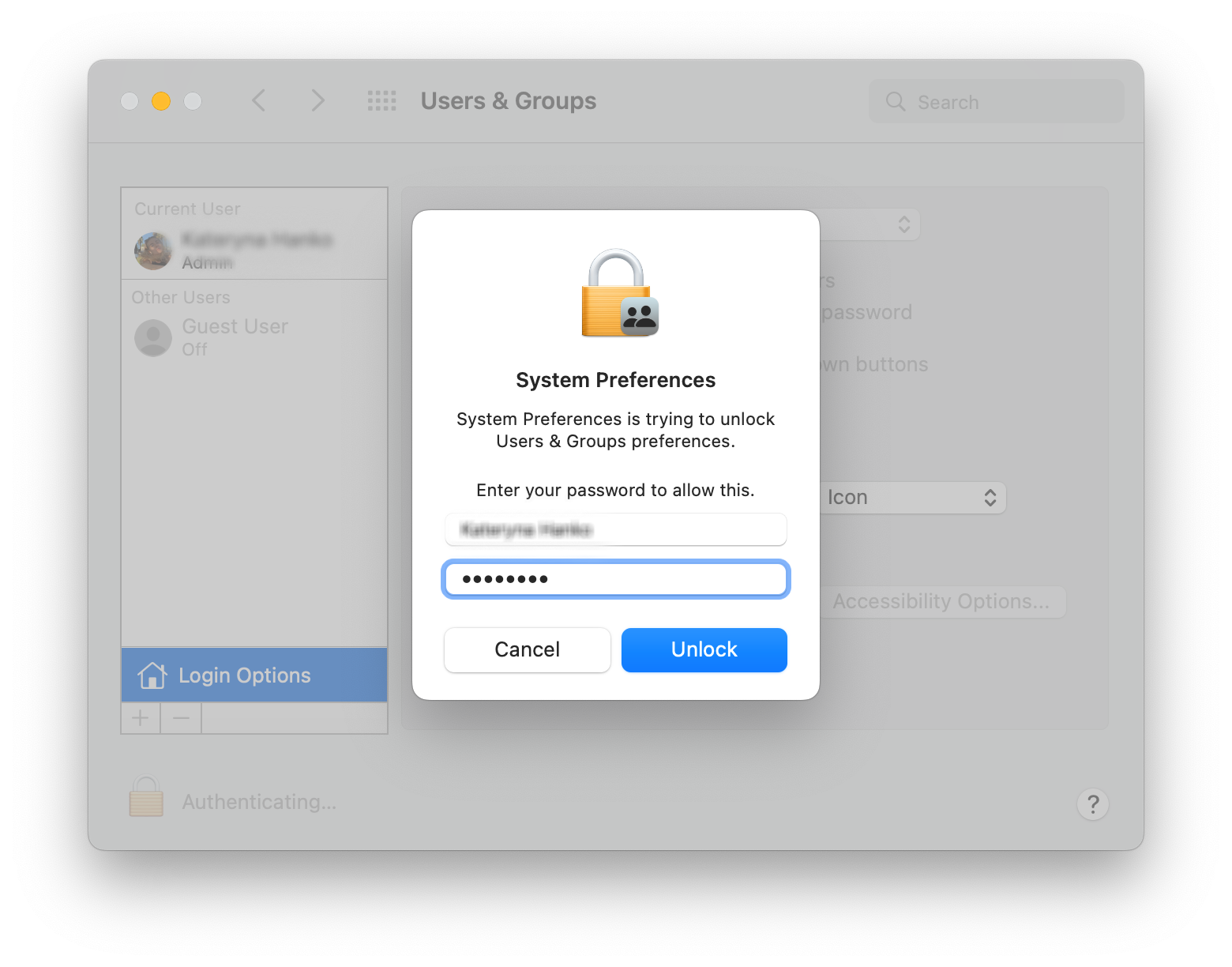
4. Select your account and switch to the Login Options tab
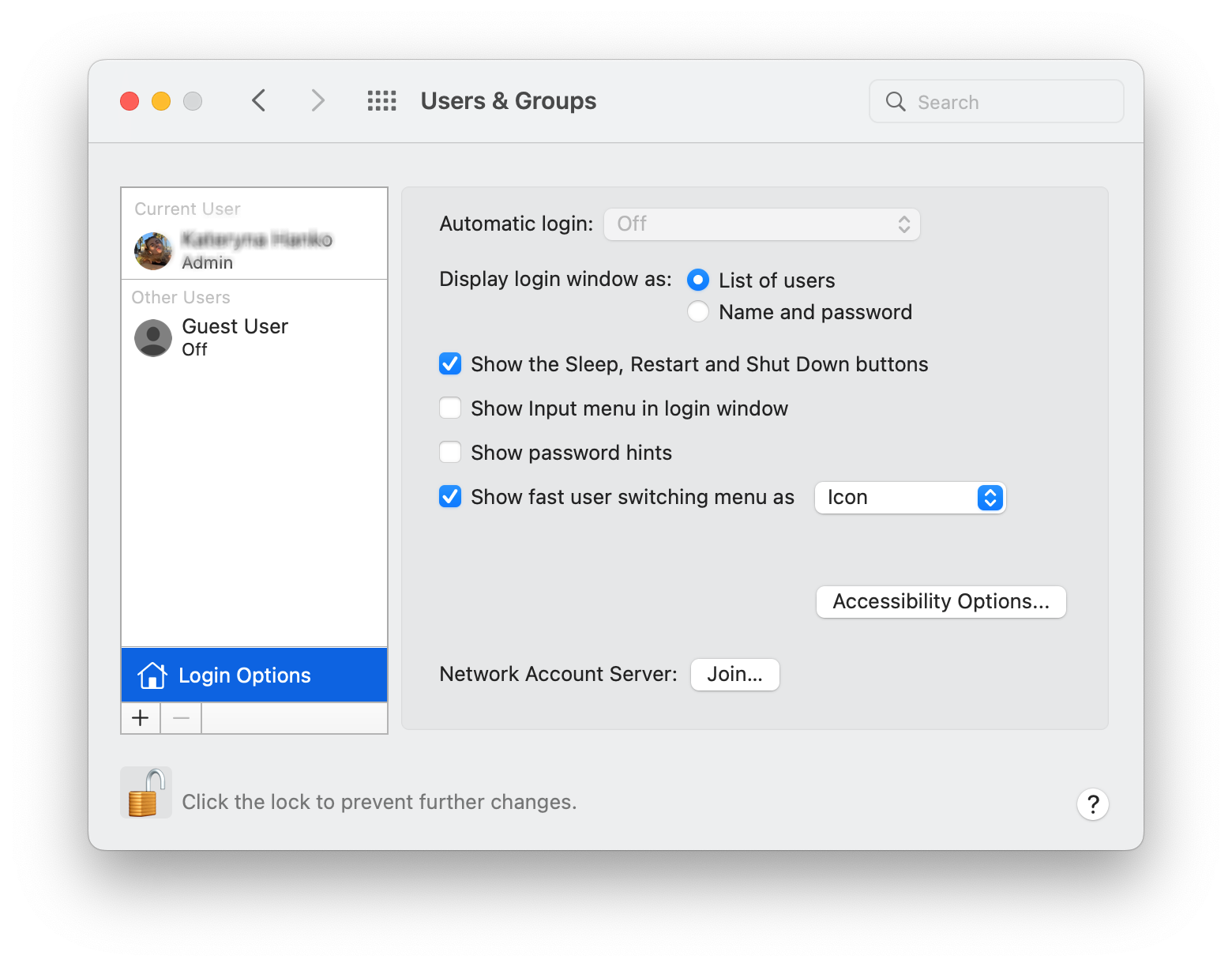
5. Highlight an item and select the Minus icon to remove it.
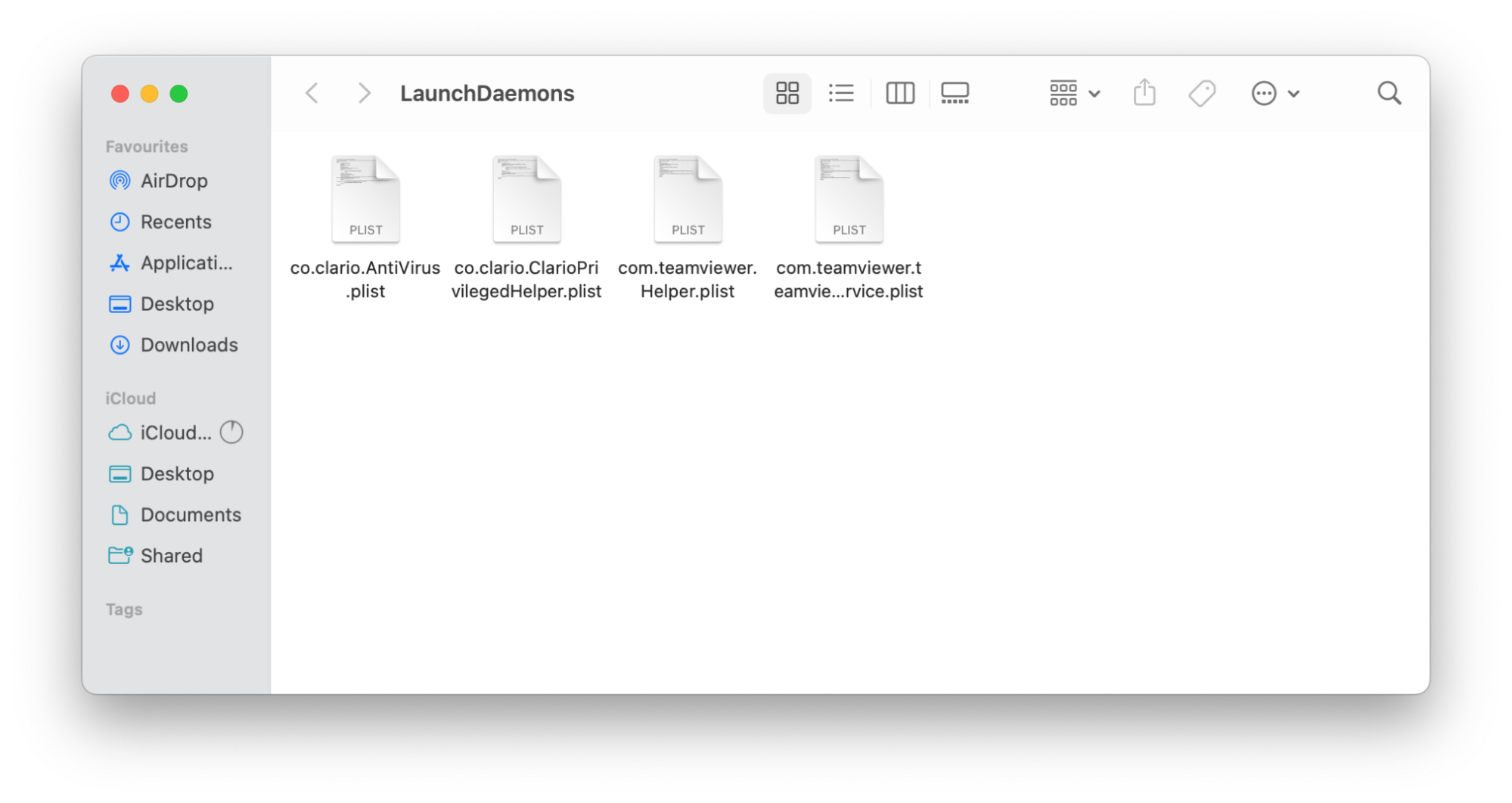
Some keyloggers can disguise themselves as launch agents and daemons on startup. Here’s a quick guide on how to remove the relevant property list (PLIST) files:
- Control-click the Finder icon and select the Go to Folder
- Visit the /Library/LaunchAgents/ and /Library/LaunchDaemons/ locations
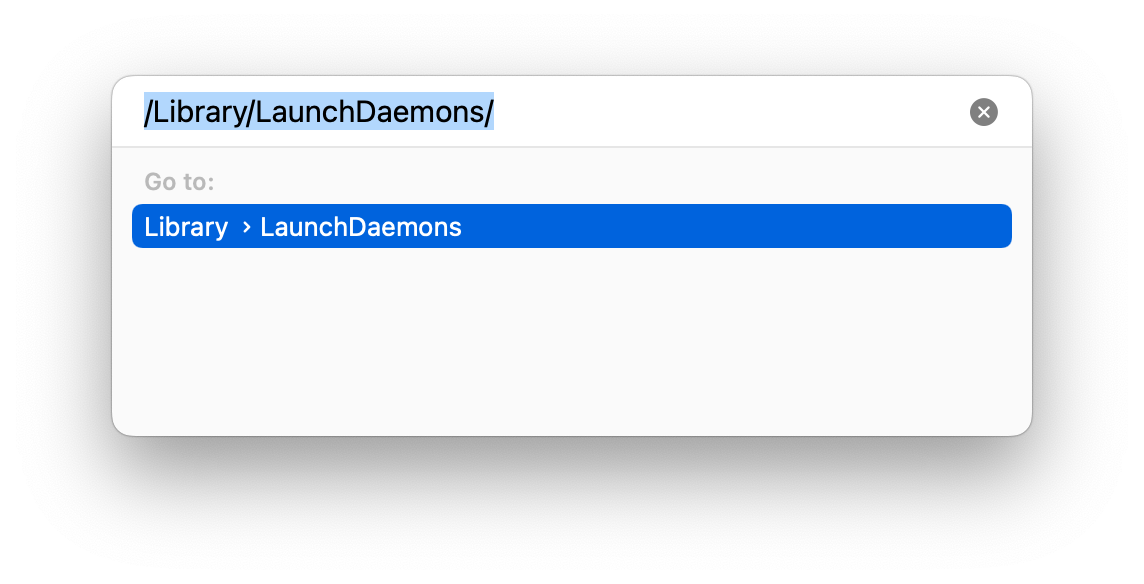
3. Locate and remove any PLIST files which look suspicious or unusual.
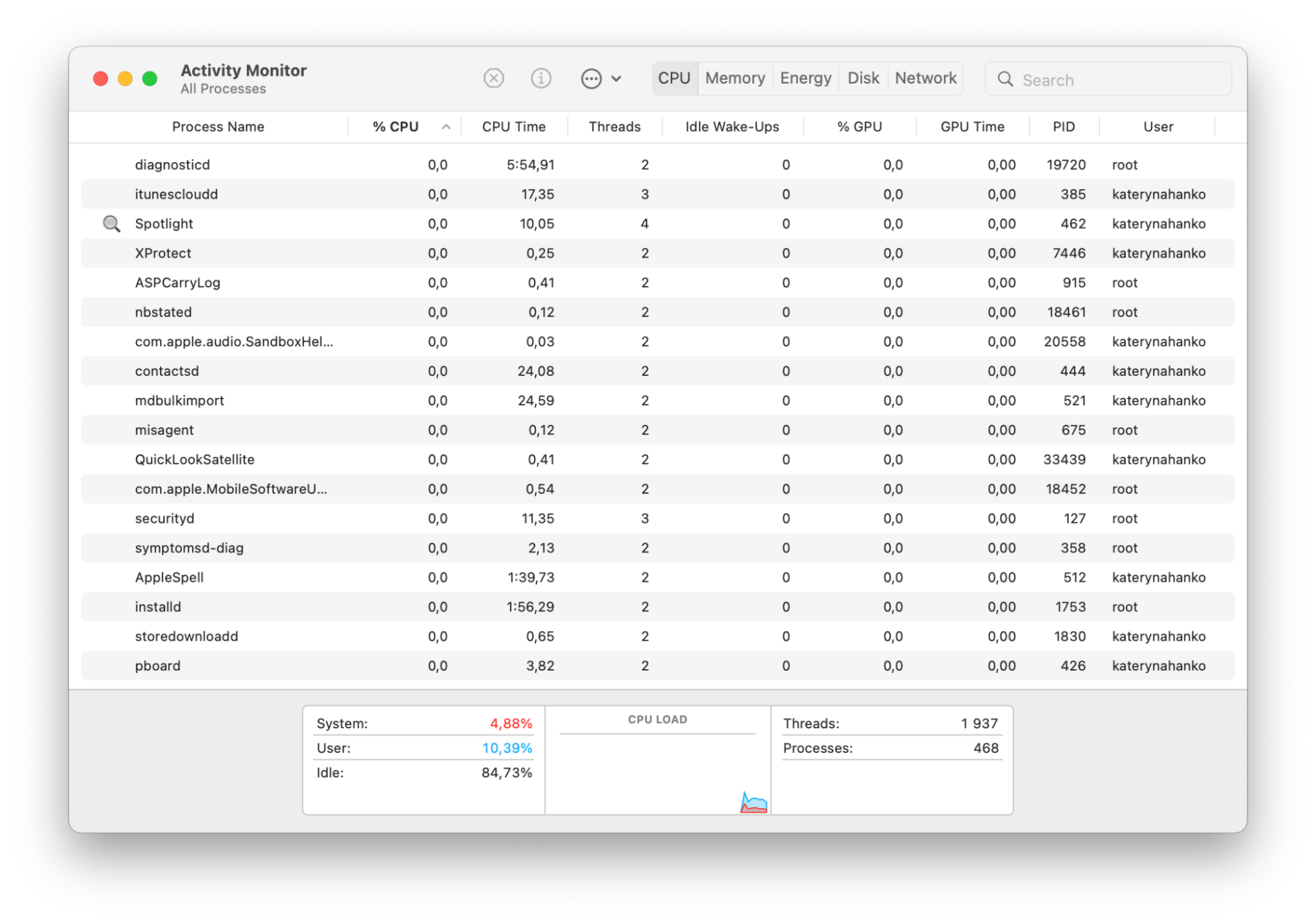
Review the running processors
This can be a little time-consuming due to how many processors operate in the background of your Mac to keep it running smoothly, but this step can help you identify any unusual processors that are out of place. Here’s how to launch the active processors list:
- Open the Launchpad from your Dock or by pinching your three fingers and a thumb together on your touchpad
- Select Other and click Activity Monitor
- Review the list of processes currently active
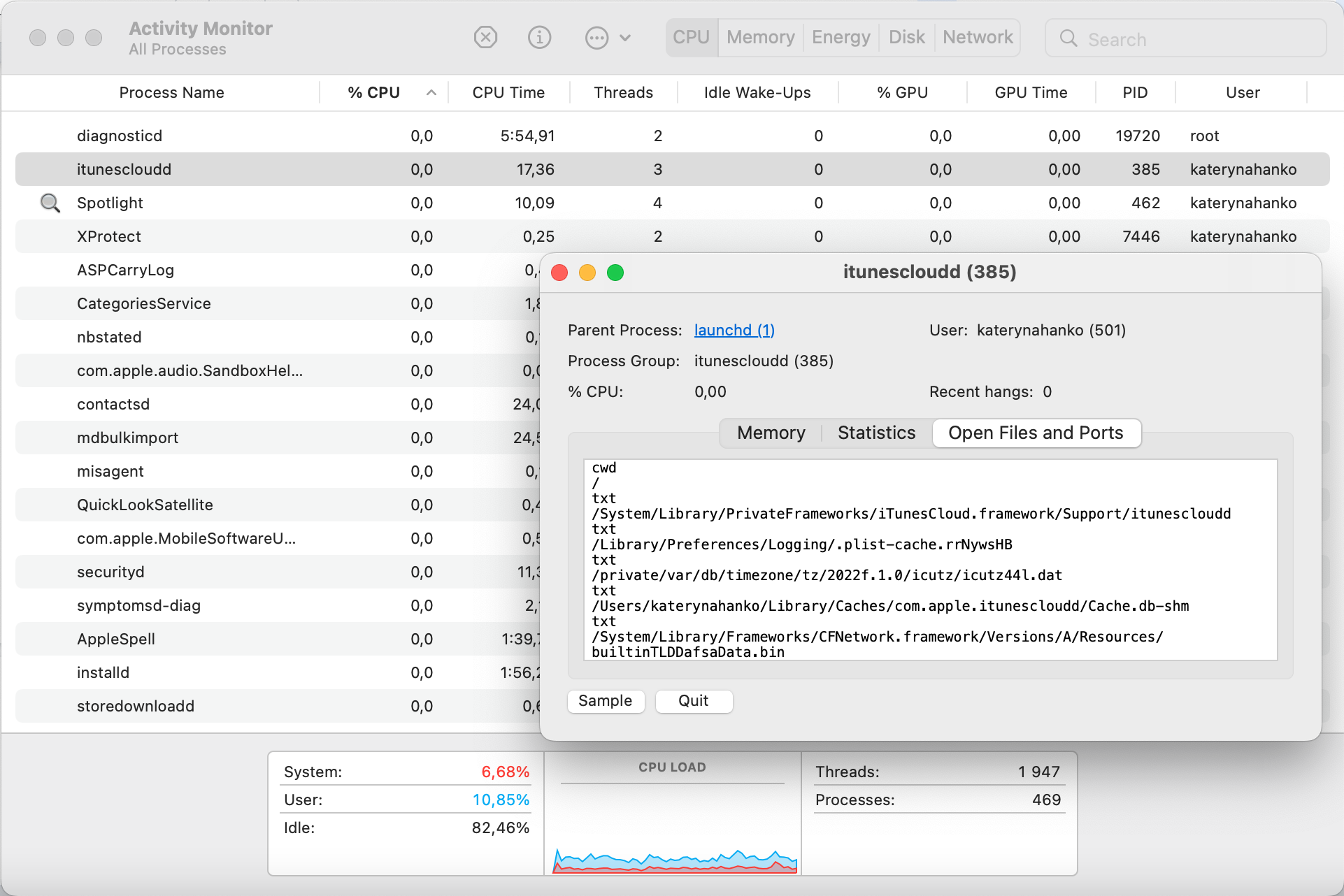
4. If a processor looks suspicious then double-click it and switch to the Open Files and Ports tab
5. Take note of the file pathway and select Quit to end the processor
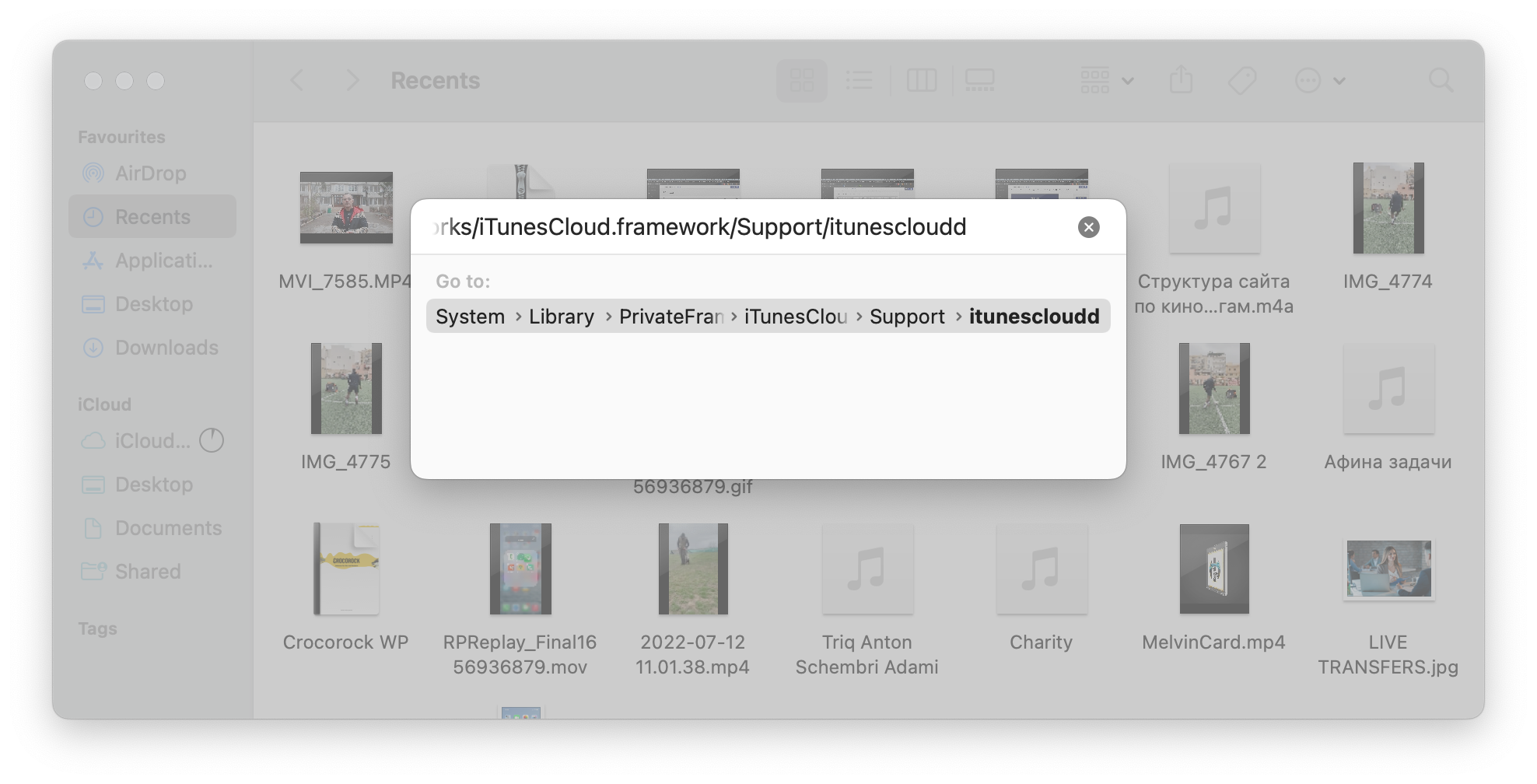
6. Open the Go to Folder
7. Locate the directory that you noted down and delete all files associated with this process.
Check the Library and Applications folders for unusual files
Most keyloggers won’t be found inside your applications folder but it’s better to be safe than sorry if you are yet to track down your keylogger. Have a look through the folder and investigate any files which look unusual to you or you don’t remember installing.
Erase and reinstall macOS
Make sure you have backed up your mac before taking this step! Sometimes the best move, when you have had a security breach, is to restart back to a point before the breach. Here’s how to factory reset your mac:
- Open System Preferences
- Select Erase All Content and Settings
- Work through the onscreen instructions to complete the reset.
Check for a physical keylogger
Sometimes keyloggers can be physically placed on your device. Check the USB ports of your device and make sure there isn’t anything you don’t recognize plugged into your device. This type of spyware is easy to remove once detected, as simply unplugging the gadget from your device will terminate its access unless it has installed a malicious application onto your device.
How to remove a keylogger from Windows
Detecting a keylogger may not be enough to actually solve your problem. Next, you need to know what the steps are for keylogger removal on your device to resecure your information. Here are some helpful methods to resecure your devices:
Uninstall programs
One of the simplest solutions to removing a keylogger is to uninstall the program which is recording your keystrokes. If you have used the control panel to identify a suspicious program, then you are already halfway through the process of securing your device once again. Follow the steps below to uninstall the program:
- Launch the Start Menu by clicking the Windows button in the bottom-left corner
- Type into your device “Control Panel” and click the Control Panel App
- Click Programs
- Press Programs and Features
- Scroll down the list and look for any unusual or suspicious programs. If you spot one, search it up online and check if it is harmful
- If yes, right-click the program and press Uninstall
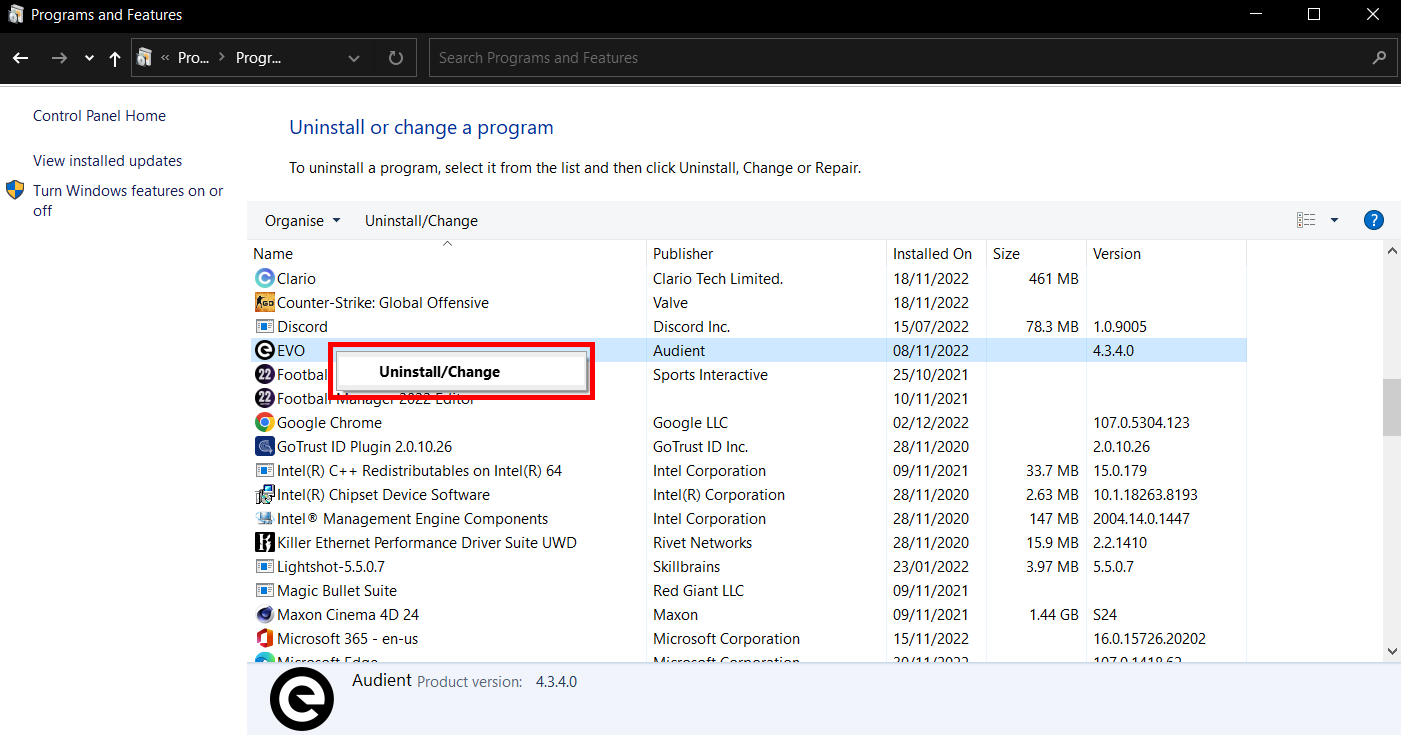
7. Follow the instructions on the uninstaller to remove the program.
Clear temporary files
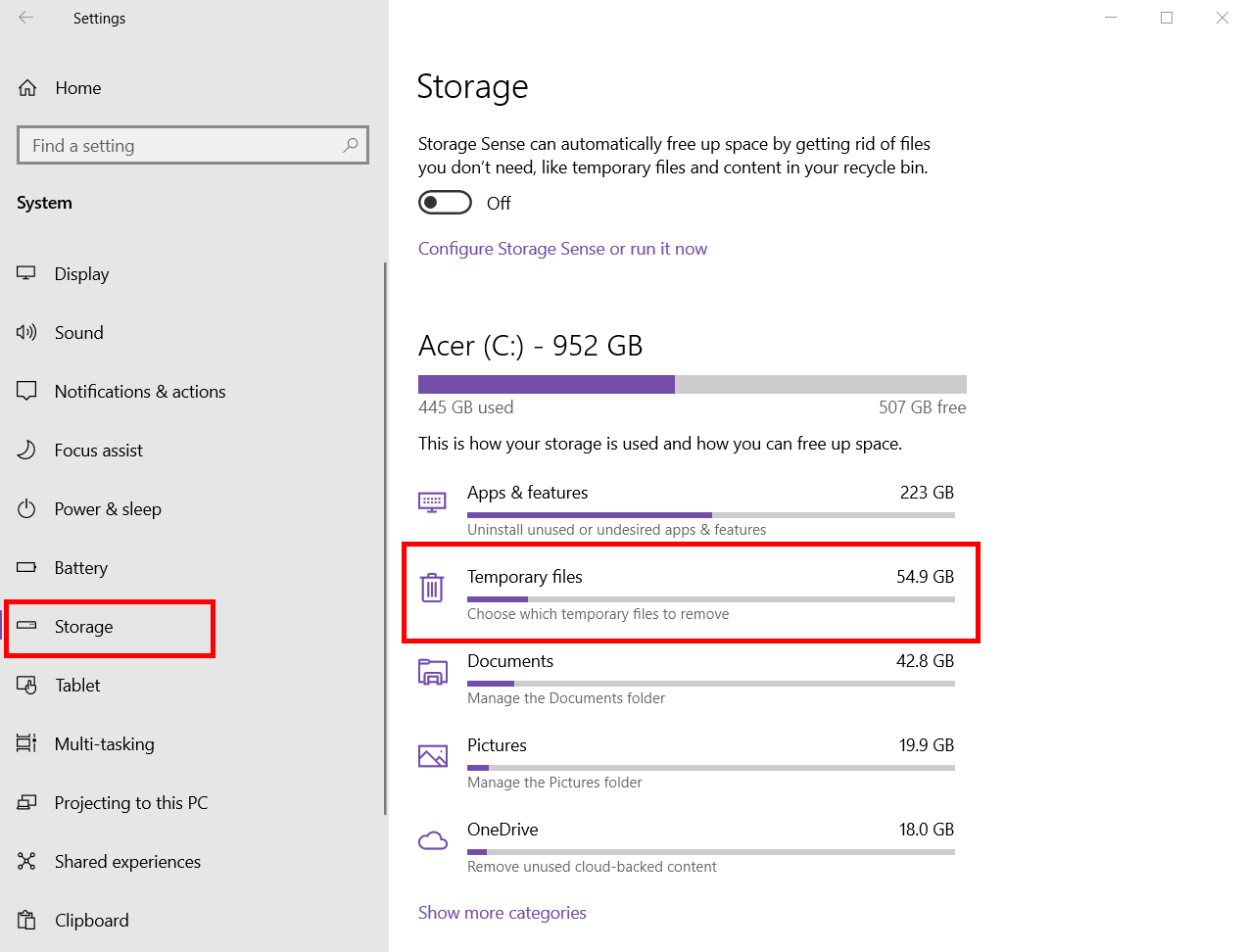
Your temporary files folder can be a common area on your device for keyloggers to hideout while they do their spying. It’s a good idea to regularly clean up your temporary files folder and remove any unnecessary files from your device and lessen the risk of spyware infiltrating your security. Use the steps below to locate your temporary files folder and clear it:
- Click the Windows icon in the bottom-left corner of the screen
- Press the Settings cog on the left
- Select the System category
- Scroll down the left-hand menu and press Storage
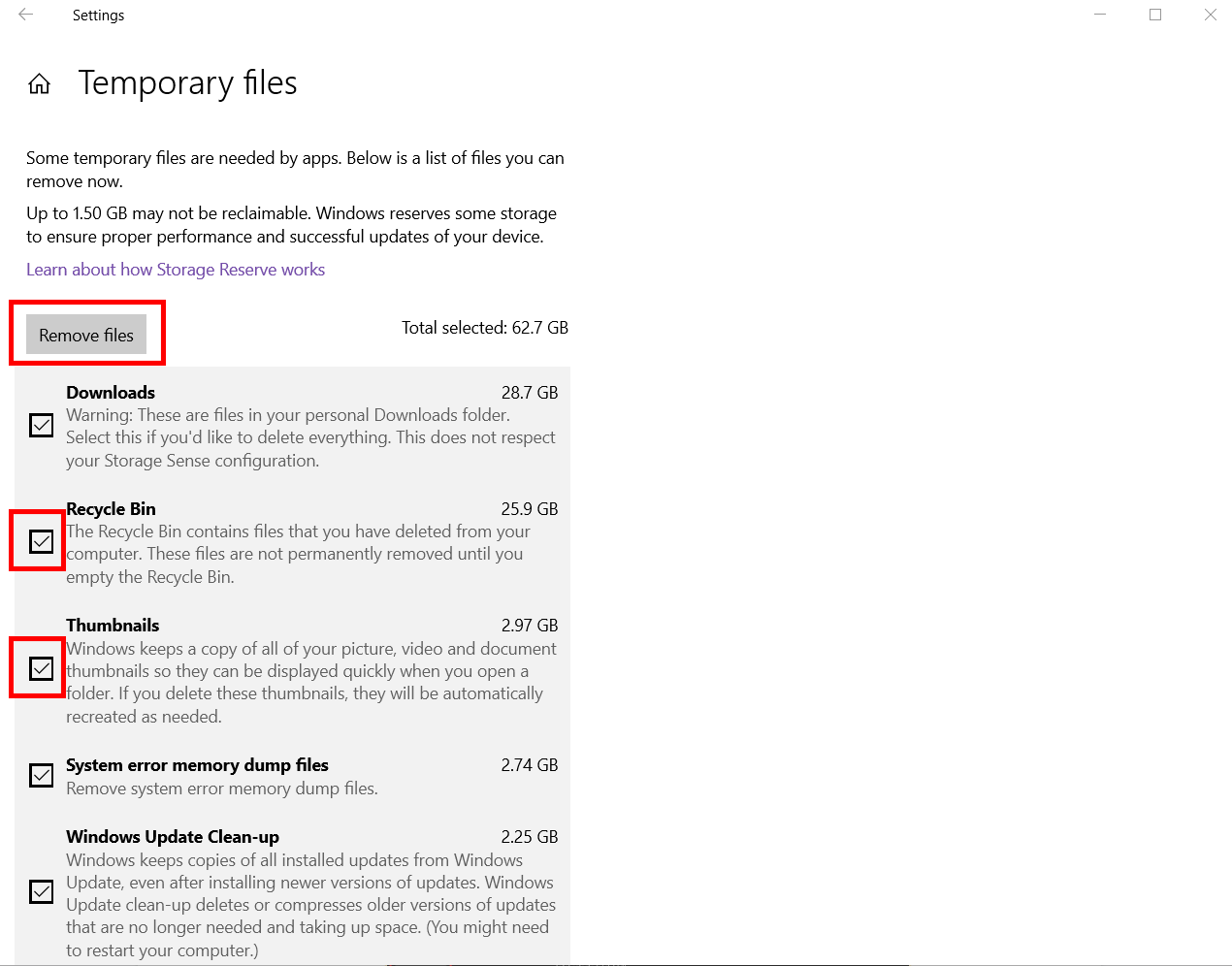
- Select Temporary Files
6. Use the checkboxes to select all temporary files and click Remove files.
Reset your PC
As a last resort, you can always reset your device to a point before the keylogger has infected your device. Make sure you have made backups of any important files that you need to keep as a reset can wipe all of your current files and programs off the device completely. Here are some simple steps to reset your device:
- Click the Windows icon in the bottom-left corner of the screen
- Press the Settings cog on the left
- Click the Update & security category
- Press Recovery on the left-hand menu and press Get started
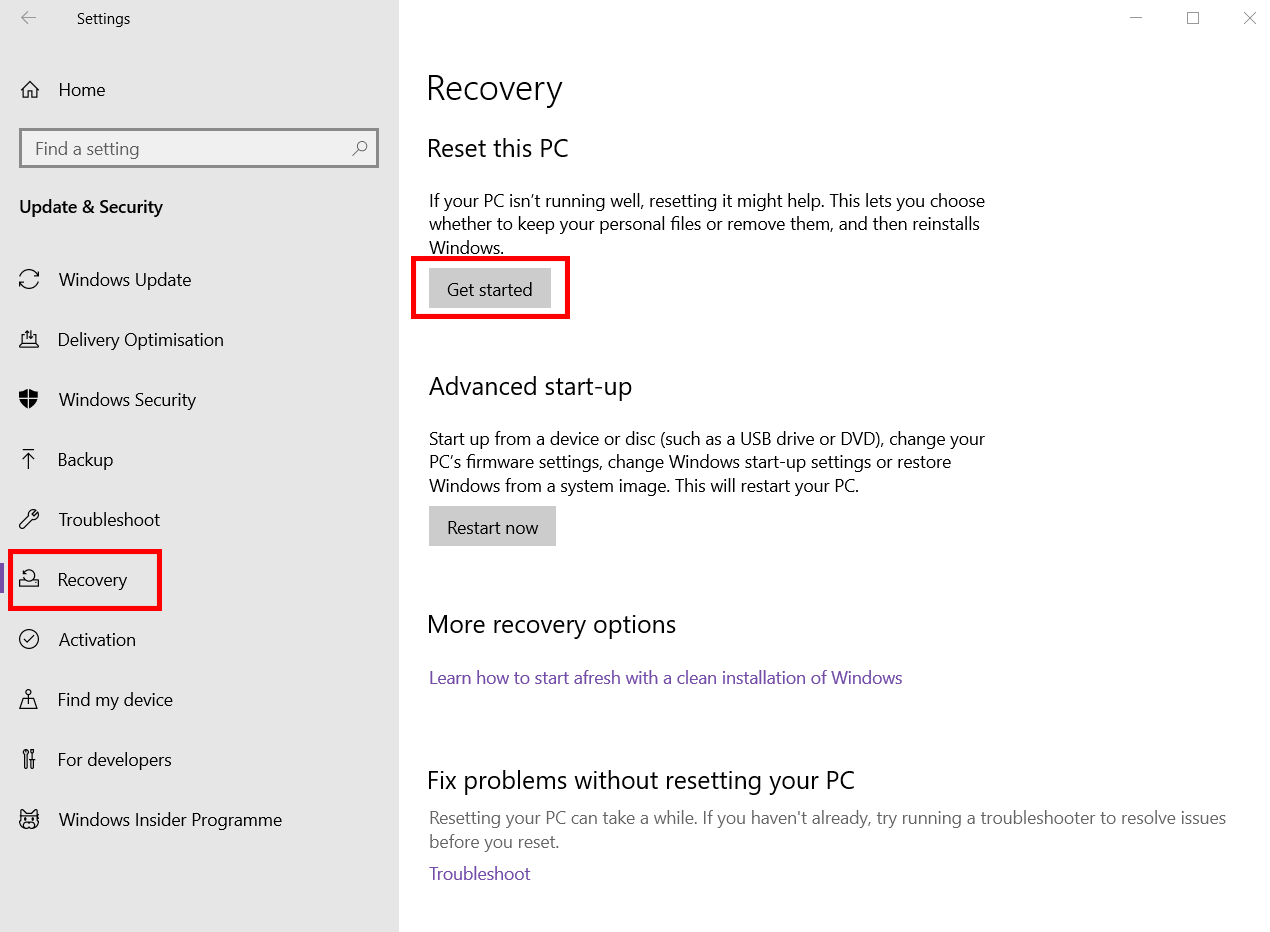
5. Select Remove everything to full-wipe your device.
How to remove a keylogger from Mac
If you are using a Mac then there are some different steps you’ll need to take to remove a keylogger from your device. Try some of the methods below.
Update macOS
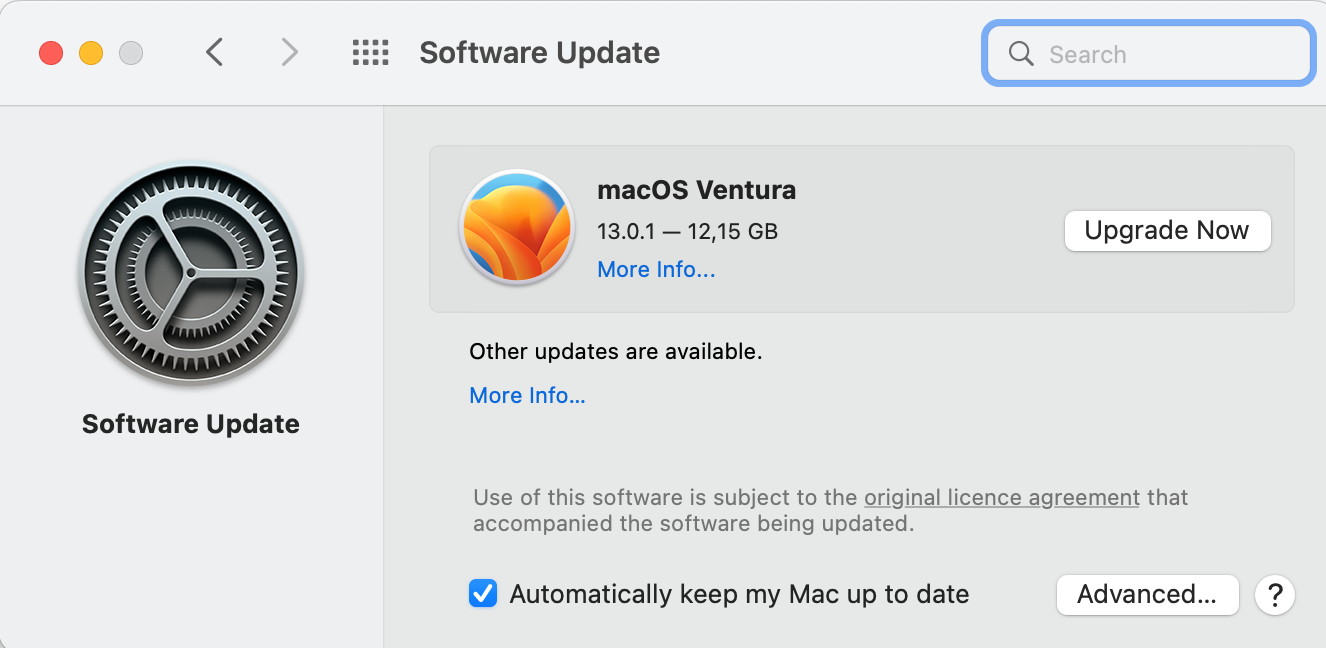
The best way to prevent keyloggers from infecting your mac is by keeping your system up-to-date. Apple has the latest defense systems in place for malware and spyware and is constantly upping its defenses with each software update. Follow these steps to take advantage of the latest macOS version:
- Open About this Mac
- Select Software Update
- Click Update Now.
Stop administrative access to others
You should consider creating separate profiles with limited access on your Mac if you share your device with others. This can reduce the risk of someone who isn’t as internet savvy as you, infecting your Mac with a keylogger without your knowledge.
Here are some quick and easy steps on how to set up an account with non-administrative privileges:
- Open System Preferences
- Select Users & Groups
- Press the Plus icon to create a new standard account.
Why are keyloggers dangerous?
A keylogger gives a criminal direct access to the data you are inputting into your device. The spyware records and tracks your individual keystrokes and can even grant access to your webcam, allowing the controller to record directly from your webcam.
This compromises any private information such as emails, passwords, recovery data, and confidential information that you access while the keylogger is installed on your device. Criminals will often use keyloggers to help breach your private accounts to commit more sophisticated crimes, or to extort you for money to regain access to your private data and accounts.
How do keyloggers infect your device?
Hackers will often use social engineering methods to try and breach your security and gain access to your device. Usually in the form of an email, SMS, or infected website link; a keylogger will be automatically downloaded onto your device and begin tracking your keystrokes.
Next time you receive an unexpected email, think twice before you open the attachment or you might be opening the door for a keylogger to spy on your data.
How to bypass an active keylogger
If a keylogger is present on your device and you need to access some private information to help you remove it, a good trick is to launch the on-screen keyboard and enter your private information. Typically keyloggers don’t track where or what you are clicking on your screen so this would hide your information in case of an emergency. This trick is, however, time-consuming and shouldn’t be used as an alternative to removing the keylogger.
Here’s how to launch the on-screen keyboard:
- Click the Windows button on the bottom-left of the screen
- Type “On-Screen Keyboard” into the search bar
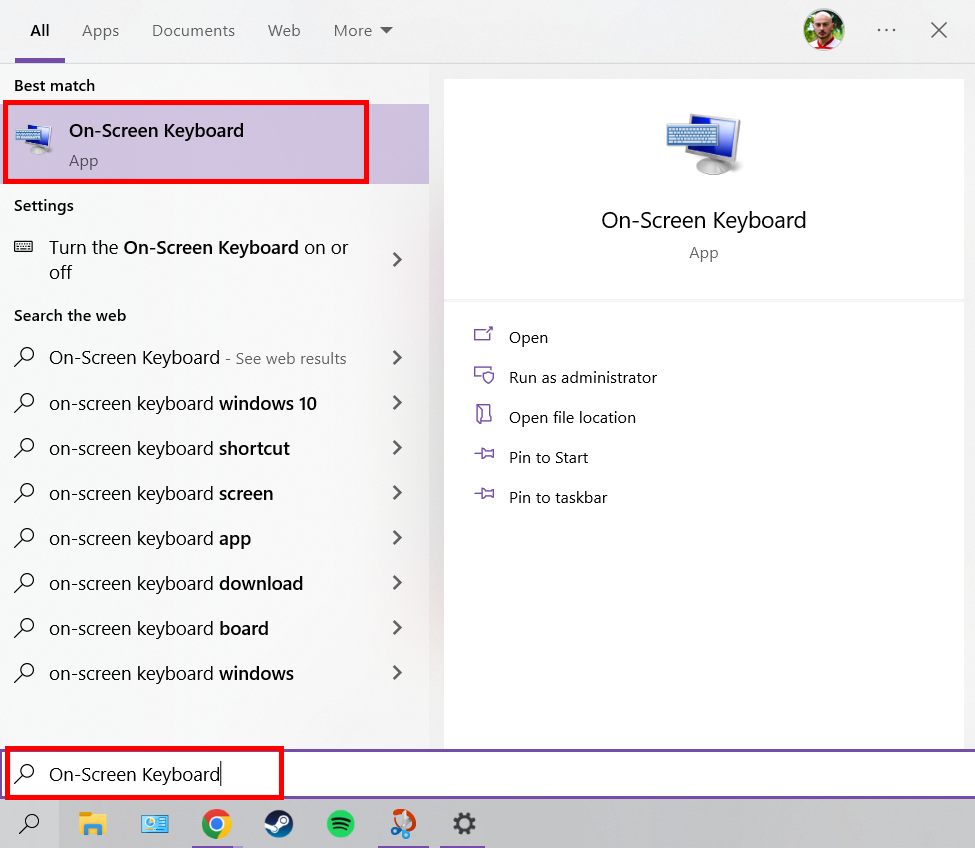
3. Press the On-Screen Keyboard App.
Do mobile devices get keyloggers?
While there aren’t currently any known keyloggers in hardware form for mobile devices, there are still software keyloggers that can put you at risk. Don’t be fooled by the myth that touchscreens are unaffected by keyloggers, as a simple google search will reveal many keyloggers readily available for download that can record your screen taps.
Mobile phone keyloggers are very dangerous as not only does it capture the screen, but it will also give the hackers access to your phone’s camera, screenshots of your emails, texts, and log-in pages, the microphone, and even connected printers
This access will allow cybercriminals to execute more elaborate attacks on your linked accounts, emails, and your private data. Often in the form of ransom attacks, where you can be blocked out of your accounts and have to pay the criminals to regain access or stop personal data from being leaked online.
For a full guide on how to remove keyloggers from your iPhone, then read this guide.
Protect yourself from keyloggers
The best defense is a good offense when it comes to preventing spyware from infecting your device. Use trusted antivirus software to regularly scan for keyloggers on your devices. Most people only discover a keylogger when it’s too late, so stay one step ahead of the criminals by keeping your device scanned and up-to-date with the latest software by Clario.


