Table of contents
- What is the O.MG Lightning cable?
- How does the O.MG Lightning cable work?
- Devices Potentially Affected
- Can iPhones Be Hacked This Way?
- How to protect yourself from a cable hacker?
- Carefully examine your cable
- Check for signs of hacking
- How to protect your Mac from cable hacking
- Wrapping Up
What is the O.MG Lightning cable?
Expert note
The O.MG Lightning cable is a malicious hardware implant disguised as a normal charging cable. It contains hidden wireless components that allow remote access to connected devices. Because it looks identical to legitimate cables, it represents a form of hardware-based cyberattack known as a supply chain or physical access attack.
A Lightning cable conducts around 12 watts of power, which is more than enough to charge your iPhone, iPad, or Mac. It’s also enough to charge a secret transmitter implanted into a fake Lightning cable by hackers.
The O.MG Lightning to USB-A cable is a hacking tool almost indistinguishable from the standard cable certified by Apple. Just like real cables, the Lightning-USB hacking device supports power and data transfer. However, unlike legit cables, it can be used for remote access to a victim’s device.
It’s sold freely on the internet for $119.99 and there’s no saying how many of them have been purchased by malicious individuals.
In 2019, the O.MG cable was created by a security researcher operating under the alias MG. After presenting the cable at a hacker conference, DEFCON 2019, the researcher started mass manufacturing the cable. These days, multiple versions of the cable are sold online, including Lightning to USB-A and USB-C to USB-A.
The O.MG cable itself is marketed as a security research tool. However, using it without consent to access someone’s device is illegal in many jurisdictions under computer misuse and cybercrime laws.
In 2021, the security researcher developed the O.MG Keylogger cable. As the name suggests, the cable functions as a covert keylogger hacking instrument. By replacing a detachable keyboard’s cable with the O.MG Keylogger, cybercriminals can collect a whopping 650,000 keystrokes to steal login details and other sensitive data.
How does the O.MG Lightning cable work?
At a technical level, the O.MG cable functions as a covert hardware implant embedded inside a seemingly normal charging cable. Security professionals categorize this type of attack as a “BadUSB-style” hardware implant, where trusted peripherals are modified to inject commands.
Once connected, it behaves like a trusted USB device while secretly enabling remote command execution over wireless communication.
- The cable contains a hidden microcontroller and Wi-Fi module.
- When plugged in, it establishes a covert wireless access point.
- The attacker connects remotely via Wi-Fi.
- Commands are injected into the device as if typed locally.
The O.MG Lightning cable consists of two connectors and a set of wires covered by insulation, allowing it to operate as a legit cable. However, one of the cable’s connectors conceals a memory chip and an 802.11 Wi-Fi transmitter. The transmitter is, essentially, no different from those in your iPhone and other Wi-Fi-enabled devices.
Once connected to an iPhone, iPad, or Mac, the Hak5 O.MG cable creates a Wi-Fi hotspot. This allows a hacker to remotely access the device and use it as if they were holding it in their hands. Importantly, the victim does not need to click anything—the attack relies on physical connection rather than phishing or social engineering.
For example, the hacker can run Terminal commands on your Mac or rummage through photos on your iPhone. The cable used for the iPhone charger hack also packs geofencing features, allowing cybercriminals to trigger the delivery of a virus payload based on a victim’s location. This means the malicious payload can remain dormant until specific conditions are met, reducing the likelihood of detection during casual inspection.
The Keylogger version of the USB hacking cable can log keystrokes from the hacked device and send them to the hacker located up to a mile away.
Devices Potentially Affected
While the O.MG cable is often associated with iPhones, the risk is not limited to Apple smartphones. Because the cable functions as a programmable USB device capable of injecting commands, any system that accepts USB input can potentially be targeted. The level of risk depends on how the device handles USB data connections and whether built-in protections are enabled.
Devices that may be affected include:
- Mac computers. If the cable is recognized as a USB input device, it can inject commands similar to a physical keyboard, potentially executing Terminal commands or altering system settings.
- iPhones and iPads. When connected via Lightning or USB-C with data transfer enabled, the cable may attempt to establish a data channel. Devices with additional protections enabled are less exposed.
- Any device that accepts USB keyboard input. Many operating systems automatically trust Human Interface Devices (HID), which makes keyboard-emulating attacks particularly effective.
- Systems without USB Restricted Mode enabled. On Apple devices, USB Restricted Mode limits data communication when the device has been locked for a period of time. If disabled, the attack surface increases.
Can iPhones Be Hacked This Way?
Yes, but only under certain conditions. The O.MG cable does not magically bypass Apple’s security protections. Instead, it relies on the device accepting USB data input and trusting the connected accessory.
An iPhone may be vulnerable if:
- The device is unlocked when the cable is connected
- The user taps “Trust This Computer” when prompted
- USB Restricted Mode is disabled
- The cable is recognized as a keyboard-like input device
Modern versions of iOS include safeguards that limit data communication when the device has been locked for an extended period. However, if a malicious cable is connected while the device is unlocked and trusted, it may be able to inject commands similar to those typed on a physical keyboard.
Importantly, this type of attack typically requires physical access to the device — it cannot be executed remotely without the cable being connected.
How to protect yourself from a cable hacker?
Hardware-based attacks are harder to detect than software malware because they originate from trusted physical accessories. Unlike typical viruses, they may not trigger traditional antivirus alerts.
You should take the following steps to ensure that a cable hacker cannot access your passwords or other sensitive data.
If you suspect that you’ve already been the victim of cable hacking, your personal details might be at risk. A hacker could have access to your email addresses, usernames, and passwords. Fortunately, Clario Anti Spy’s Data breach monitor can help you find out if your details have been compromised. The app will scan databases of data breaches and password leaks, and alert you as soon as your details are found.
How to check for data breaches with Clario Anti Spy:
- Download Clario Anti Spy and follow the on-screen directions to set up a subscription.
- Open the app and tap Scan under Data breach monitor.
- Check the on-screen guidance to check whether your email address has been involved in any data breaches—and add other email addresses if you regularly use more than one.
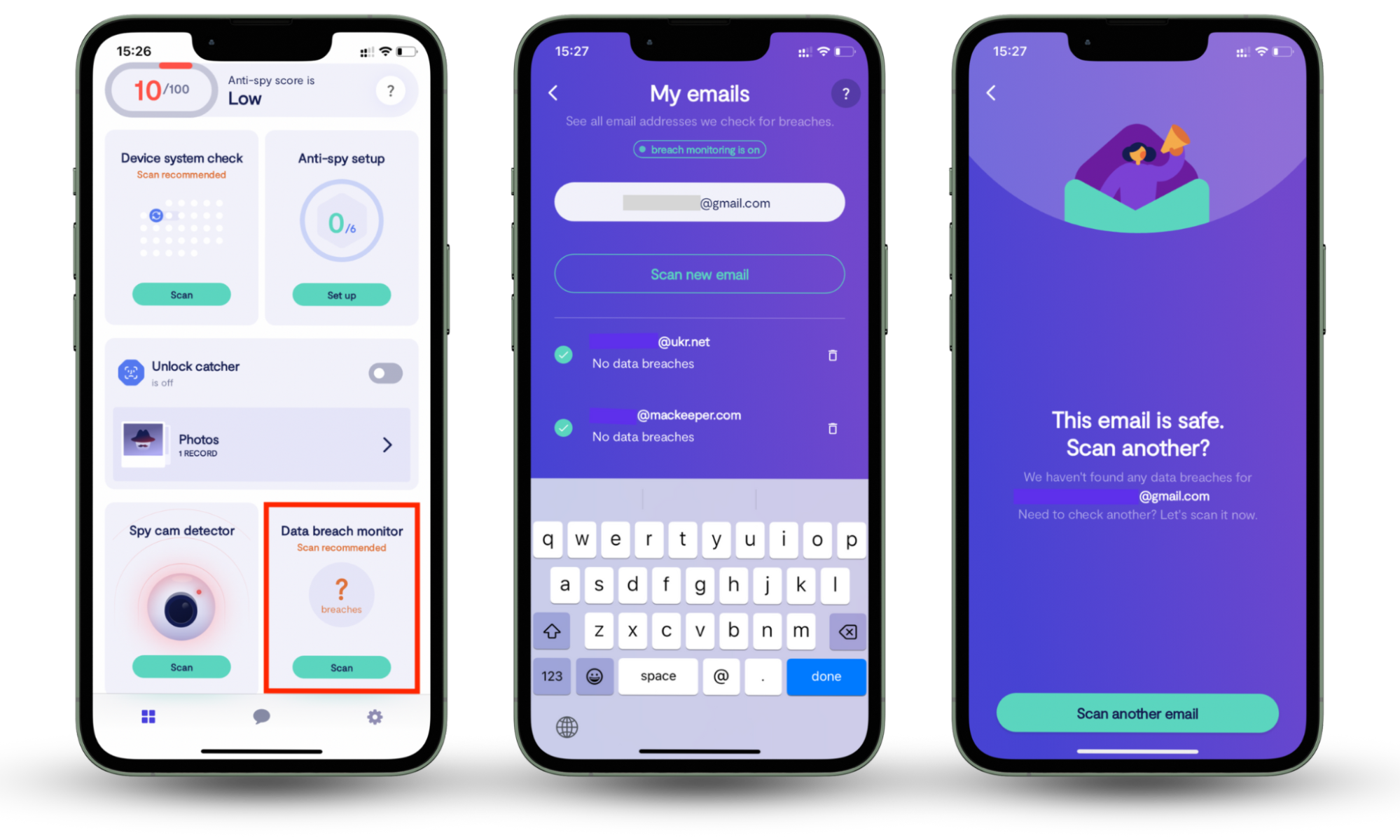
If your details were involved in a data breach or password leak, you can take action to secure your online accounts.
Expert Tip
Keep yourself safer online by using unique passwords for each website and account.
Carefully examine your cable
Cables certified by Apple come with the MFi badge on their packaging. The legit cables themselves bear a 12-digit serial number and the following text: Designed by Apple in California Assembled in Country.
Carefully examine your cable’s connectors. If you spot an uneven metallic finish, rough edges or varying insulator width, then you are probably dealing with either a counterfeit cable or O.MG cable.
Use the checklist below to quickly assess whether a cable may be counterfeit, tampered with, or unsafe to use:
- Look for irregular seams or connector asymmetry
- Check packaging for missing MFi certification
- Avoid unknown third-party promotional cables
- Never borrow cables from untrusted sources
If you’re suspicious of your cable’s origins, we’d suggest purchasing a new one—preferably directly from Apple, or from a reputable local retailer.
Check for signs of hacking
Hardware injection attacks often leave subtle behavioral traces rather than obvious malware warnings. Look out for these signs of hacking on your Mac, iPhone, or iPad: :
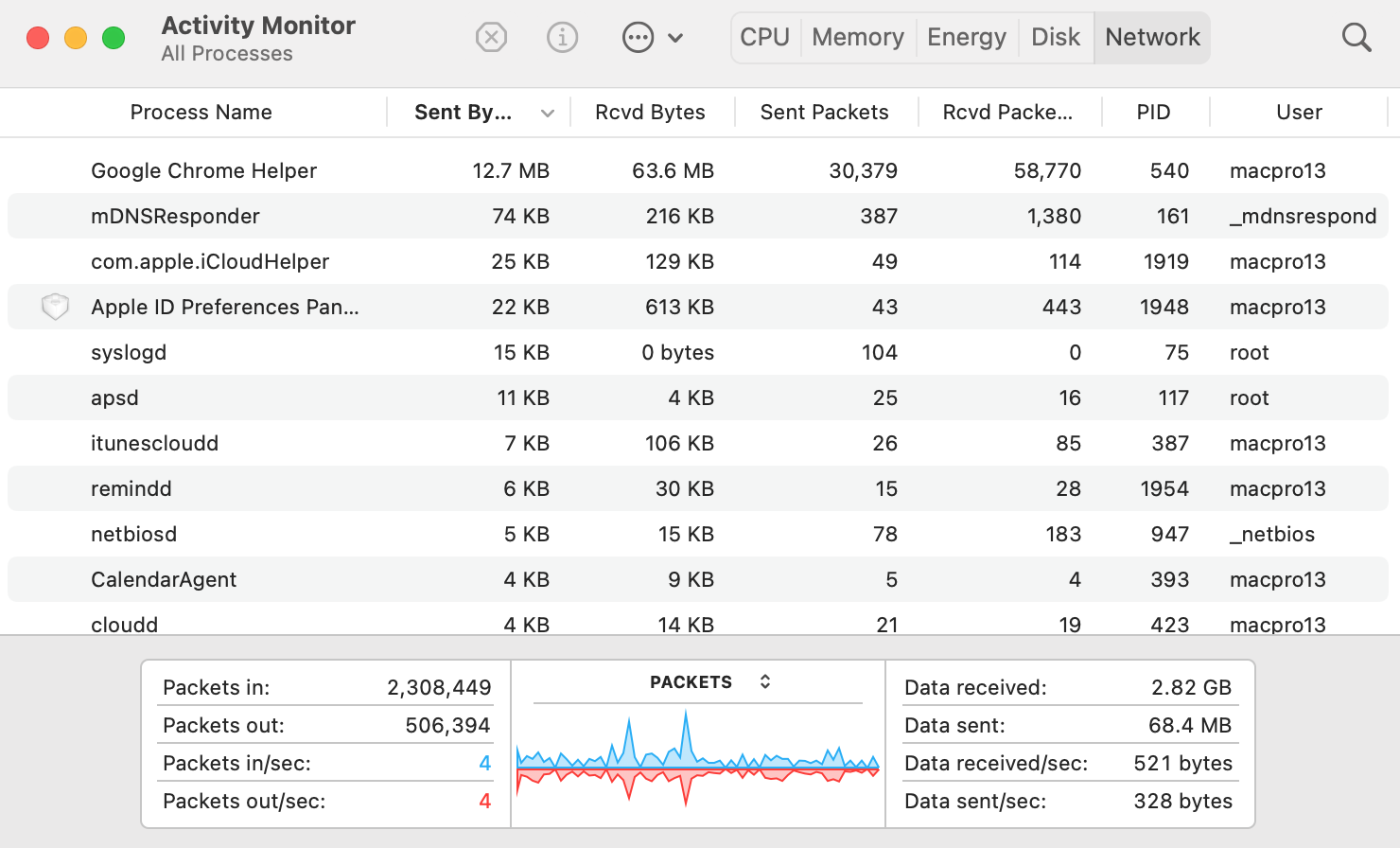
- Sudden spikes in the network activity, which can be tracked via Activity Monitor
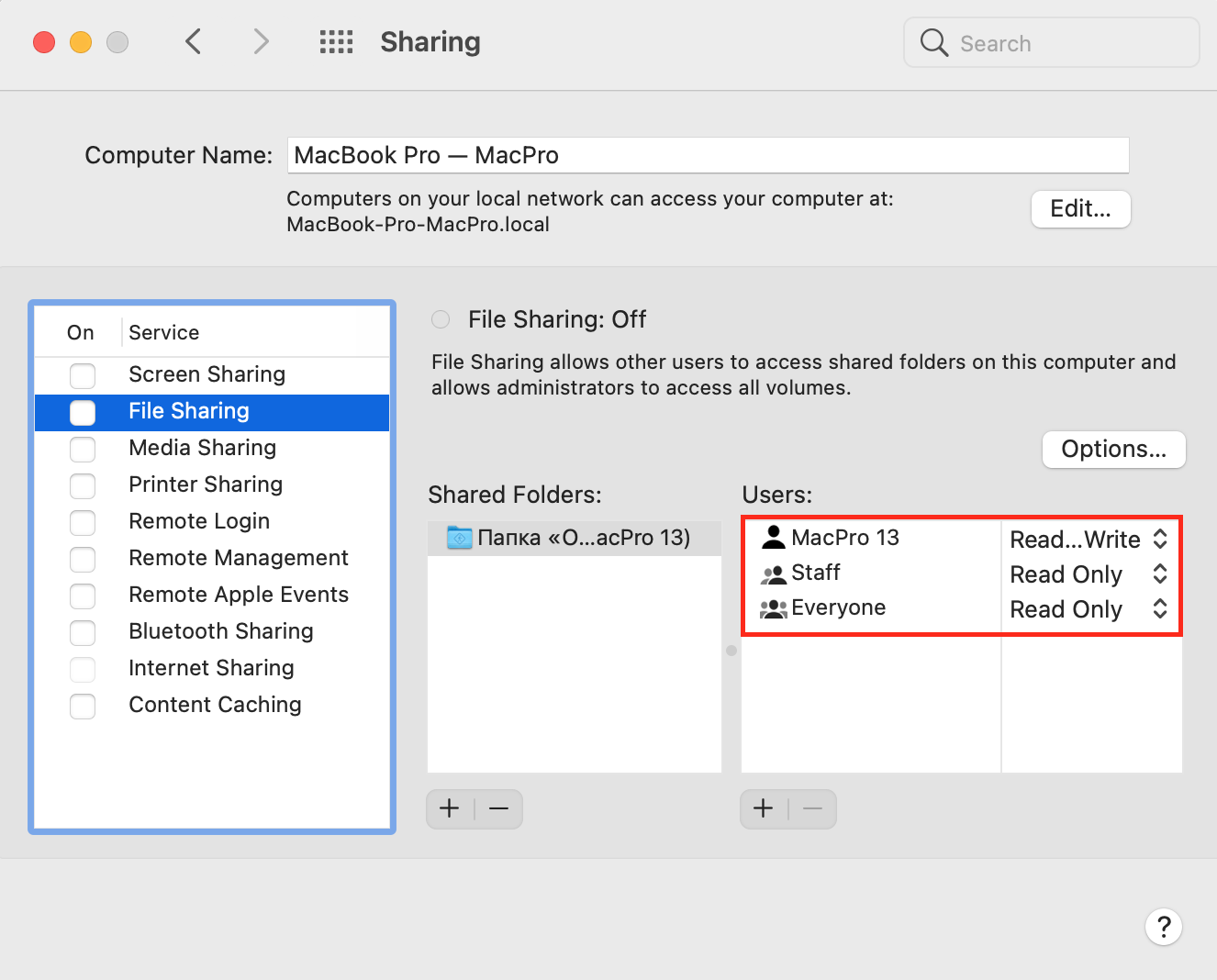
- Check for suspicious users in System Preferences > Sharing
- Hijacked email or social media accounts
- Unsolicited software installs
- Terminal opens randomly
- Unexpected pop-ups requesting your login details
How to protect your Mac from cable hacking
An O.MG cable is designed to look almost indistinguishable from a real cable. Given how difficult it is to determine a hacking cable by just looking at it, you need to make sure your devices and privacy are protected.
Make sure that you only use cables you trust—ideally, ones you’ve purchased yourself from reputable retailers.
Install reputable antivirus software, or if you’re using iOS, make sure that your security and privacy settings are configured. Clario Anti Spy’s Anti-spy setup can walk you through arranging your security settings so that your phone is as secure as possible.
If you notice any of the signs of a USB hacking device that we’ve mentioned above, immediately disconnect your cable and take action. This might include:
- Changing your password on online accounts
- Running an antivirus scan
- Uninstalling unexpected apps
- Contacting local law enforcement if you suspect that someone has access to sensitive data
It’s important to note that such attacks typically require physical access to your device or charger, which makes them less common than phishing—but potentially more dangerous when executed successfully.
Wrapping Up
With hacking cables sold freely on the internet, you have to constantly be on the lookout for a data breach.
Fortunately, Clario Anti Spy offers a data breach monitoring service that can do the checking for you—any time of day or night.


