Table of contents
- Why security in smartphones matters
- Best phones for security and privacy
- 1. Specialized and niche encrypted phones
- 2. Mainstream phones with hardened security
- Key security features and criteria for phones
- What is a secure phone
Why security in smartphones matters
If your smartphone has weak security settings, your data can be subject to government surveillance, malicious software, and hacker attacks. Threat actors can exploit vulnerabilities in your OS to install spyware and steal your personal information, including passwords to your online accounts, or even take full control of your mobile device. This kind of security breach can lead to the theft of money, identity fraud, and corporate espionage.
In 2024, mobile devices experienced approximately 2.8 million cyberattacks per month. In such a hostile environment, choosing the best security phone may not be enough. You need a trusted anti-spyware app to protect your data.
Clario Anti Spy offers powerful features to protect your calls, messages, location, contact list, photos and videos, and more from unauthorized access. If you're an iPhone user, our Device system check feature will analyze your OS for the latest security updates. Importantly, it will scan your device for signs of a jailbreak, which is one of the most dangerous safety threats to iPhones.
See, when your iPhone has been jailbroken, malicious actors can bypass Apple's security policy and gain unauthorized access to your phone. The Device system check feature will alert you if it detects signs of tampering or an outdated OS.
Here’s how to use Clario Anti Spy’s Device system check:
- Download Clario Anti Spy and set up an account.
- Locate the Device system check feature.
- Tap Scan, then wait for the results.
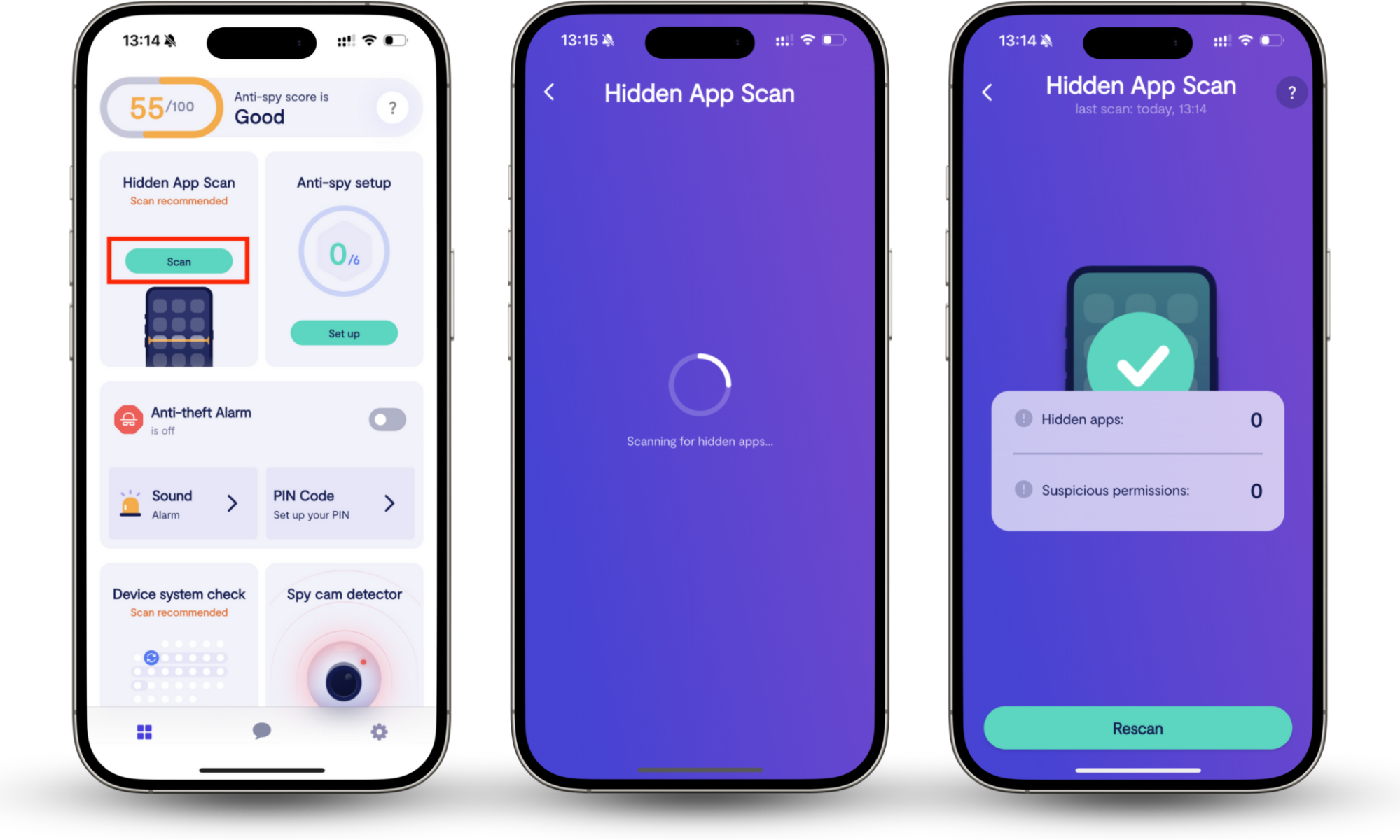
For both Android and iPhone owners, Clario Anti Spy created the Hidden app scan feature to help users locate and eliminate dangerous apps. The Hidden app scan conducts checks on your mobile device for signs of spyware or parental control apps that could be downloaded without your knowledge. Additionally, it verifies the requested app permissions, allowing you to identify any suspicious activity.
Here’s how to use Clario Anti Spy’s Hidden app scan:
- Download Clario Anti Spy to your mobile device.
- Create an account.
- Go to Hidden app scan and tap Scan.
- Wait for the results.
Best phones for security and privacy
The best phone for privacy should incorporate end-to-end encryption for texts and calls, use a hardened OS, and have a secure boot system.
Some of the most secure phones on the market include the Blackphone PRIVY 2.0, Bittium Tough Mobile 2C, and Purism Librem 5, as well as mainstream phones like the Samsung Galaxy with Knox, the iPhone with Secure Enclave, and Pixel phones running GrapheneOS.
1. Specialized and niche encrypted phones
These devices, like Purism Librem, Blackphone PRIVY 2.0, and Bittium Tough Mobile 2C, focus on security and convenience for users who either work with particularly sensitive materials or may find themselves in situations with considerable privacy risks (journalists, state officials, etc). However, this type of phone often provides less convenience and is more expensive than a mainstream device.
1.1 Blackphone by Silent Circle
Blackphone PRIVY 2.0 devices are designed for top-tier executives, government officials, classified information analysts, and journalists. It uses the custom Android Silent OS, which completely blocks Google services. This allows for secure calls, messages, and file transfers with minimal exposure of metadata.
Note
The Blackphone Privy 2.0 features a data-only SIM card, enabling multi-roaming connectivity. Additionally, you can only interchange files with users whose devices also use Sinent OS. Also, Blackphone Privy 2.0 features PRIVY Vault and PRIVY Chat, which provide embedded end-to-end encryption support. All this combined makes it the most secure phone in the world.
1.2 Bittium tough mobile series
The Finnish-made Bittium Tough Mobile 2C provides dual-boot environments separating work and personal data. It is designed to uphold military standards on secure booting, government-level encryption, and tamper-resistant hardware.
The smartphone is equipped with dual OSs, a fortified version of Android 11 and Bittium's bespoke Secure OS. The security features include AES encryption with secure element chips, YubiKey 5 NFC token interface, and Secure Suite Bittium end-to-end encrypted calls.
1.3 Purism Librem
If you’re wondering how to make your phone impossible to track, Librem 5 makes it a reality due to its open-source nature. Running on custom PureOS, Librem 5 from Purism promotes transparency and total user control over data and software.
The phone’s cellular modem is separated from the main CPU and random access memory. This prevents hackers from gaining access to the device's data via cellular network attacks. Librem 5’s kill switches make it impossible to monitor users covertly (due to air gaps) or to turn the switches back on without their knowledge.
1.4 K‑iPhone / CryptAll / secure custom iPhones
KryptAll's K-iPhone takes a unique approach to meet the needs of customers who require secure mobile communications without losing the standard iPhone’s simplicity. KryptAll employs VoIP applications to encrypt calls and disables telemetry, providing ultra-private Apple hardware to their clients, who often include government officials, business executives, and legal professionals.
2. Mainstream phones with hardened security
Mainstream phones come with certain security enhancements, but their primary focus remains UI and user convenience. Still, the security of devices from flagship brands is getting stronger, and unlike some hackable devices, mainstream phones can be challenging to hack.
2.1 Samsung Galaxy (Knox, secure vaults)
Samsung Galaxy devices come with an integrated Knox security system, offering a multi-layered defense. Knox is known for its hardware and software-level encryption featuring a special trust zone processor. The system reinforces protection with biometrics, secure boot verification, encrypted vaults, and Knox Management console. The console allows users to alter security settings and policies according to their needs.
If you're wondering how to secure your Android phone, regular software updates are your answer. This is where Samsung Galaxy surpassed itself. It runs on the latest Android 14-based One UI 6.1, which will receive seven years of OS updates, making it one of the most secure phones available.
2.2 Apple iPhone (secure enclave, iOS sandboxing)
Security is an integral part of Apple's iOS architecture. Apple itself does not possess the means to unlock a device without a passcode, thanks to device-specific hardware identifiers. Encrypted hardware is protected by decryption keys that are stored within the device. Furthermore, application data and system resources are siloed, meaning apps cannot access data from other apps or system resources, or fetch data without the user's explicit permission.
Secure Enclave is often compared against Knox in the context of iOS vs. Android security, and which is better. Secure Enclave and Knox are both powerful security systems. However, iOS tends to be safer due to its closed nature. Apple’s Secure Enclave coprocessor manages and secures your biometric and other sensitive data while performing other highly sensitive tasks separately from the main processor. All this, combined with the iOS closed ecosystem, makes the iPhone the best phone for security and privacy among mainstream options.
2.3 Pixel / Android devices running GrapheneOS / custom ROMs
Google Pixel devices have the added security of a Titan M2 security chip. In combination with the Google Tensor security core, it forms multi-layered protection against hardware/software attacks, keeping your data safe and sound. GrapheneOS-based Androids or custom ROMs allow users to create their versions of a secure Android OS.
Note
Unlike some hackable devices, mainstream mobile devices remain harder to hack. This is because most mainstream smartphones come with built-in encryption for storage. It protects your files, but doesn't always extend its protection to communication, like text or messages. This is why one of the flagship features of niche encrypted phones is safe communication.
Key security features and criteria for phones
The best security phones should feature hardware components that include security chips (such as Apple’s Secure Enclave or Google’s Titan M2), kill switches for cameras and microphones, and tamper-proof casings that protect devices from extreme environments. Some security features include secure boot, app sandboxing, and an open-source OS. Other must-have features of the best phone for privacy include end-to-end encryption, full-disk encryption, VPN capabilities, and multi-level authentication.
Hardware and software features of secure phones include:
- security chips
- hardware-kill switches
- dual-boot system
- hardened OS
- end-to-end encryption
- full disk encryption
- VPN capabilities
- multi-level authentication
- granular permission controls
What is a secure phone
The most secure phone in the world isn't a specific device, but rather, the one that best aligns with your specific needs as a user. The Blackphone PRIVY 2.0 is extremely competent in encrypted communications, the Bittium Tough Mobile 2C is military grade, and the Purism Librem 5 is ideal for users who prioritize privacy most. The K-iPhone is dual-use—for individuals needing encrypted phone calls within the iOS-friendly ecosystem, and for high-confidentiality mobile threats. The military-grade voice encryption and limited production of the units can justify their cost.
Protecting digital privacy, preventing personal data leaks, and mitigating spyware malware threats have become of utmost importance for modern mobile users. But simply choosing a safe device is not enough—you need to use reliable cybersecurity apps. Clario Anti Spy’s Hidden app scan feature can identify and eliminate malicious apps from your Android or iPhone, while the Device system check feature will scan your iPhone for signs of jailbreak.


