Table of contents
- What is multi-factor authentication?
- Why is multi-factor authentication important?
- Improved security
- Reduced costs
- Increased efficiency and flexibility
- How does multi-factor authentication work?
- Multifactor authentication methods
- Major multi factor authentication examples and methods
- Knowledge-based MFA
- Possession-based MFA
- Inherent MFA
- Passkeys
- Other multi-factor authentication examples and methods
- Location/time-based authentication
- Risk-based or adaptive authentication
- Social media login
- Push-based two-factor authentication or 2FA
- Multi-factor authentication vs. other authentication methods
- Multifactor authentication vs. two-factor authentication
- Multifactor authentication v. single sign-on or SSO
- How to get started on the multifactor authentication process
- How to set up MFA on your Google account
- How to set up MFA on your Microsoft account
- FAQ
- 1. Is MFA 100% hack-proof in 2025?
- 2. What happens if I lose my phone?
- What if MFA isn't enough?
In 2025, online threats are more sophisticated than ever, putting your personal data at risk. If you're still relying on just a password to protect your information, it’s time to rethink your strategy.
We understand how significant the login process is. It’s the frontline defense verifying a user’s identity so unwanted third parties can’t access your data. With password leaks reaching record highs, relying on a simple login is no longer enough.
Have you ever wondered why you’re sometimes required to input a little more than your username and password? That’s what we refer to as Multi-Factor Authentication (MFA).
What is multi-factor authentication?
MFA is an extra but uncomplicated step in the login process.
It is a verification method requiring users to confirm their identities through two or more independent factors. They will only be able to gaining access to an online account, website, application, or any other online resource by providing these details.
It goes beyond the regular ‘input your name and password’ to log in.
This way, the chances of infiltration or breach are reduced because further verification factors are required.
This authentication process is a part of the identity and access management (IAM) policy put in place to reduce the chances of a security breach taking place. The MFA process usually requires at least two authentication methods.
Why is multi-factor authentication important?
Multifactor authentication benefits any security strategy and has a couple of advantages for individuals and organizations alike. They include:
Improved security
When compared to basic passwords and single-password authentication processes, MFA helps to offer systems greater security from hacking or phishing. The main benefit of MFA is that it brings in that extra security to protect user data. It can also enhance the reputation of a company and trust in an online product to provide a competitive advantage.
Reduced costs
In the bigger picture, the cost of phishing can be pretty high. However, raising security standards through MFA can reduce the cost of fixing damage on network resources.
Increased efficiency and flexibility
Even though it may include more than two authentication methods, MFA is improving to make greater use of passive methods like software tokens and biometrics and reduce its reliance on static passwords.
This means it’s improving the login process and the entire user experience. A flexible login process means a lot to users, as it makes their lives easier and more straightforward.
When users write reviews about enjoying an exceptional experience using an online product or service, it may just be another way of saying “I was able to log in without any stress!”
How does multi-factor authentication work?
Ultimately, MFA works by using extra verification methods to prevent unauthorized users from gaining access to an online network or account. It goes two steps ahead of static usernames and passwords and a step ahead of two-factor authentication (2FA).
Therefore, even if an impersonator gets through the first steps, they are unlikely to provide the correct information to pass through the next required steps.
The idea is that the different authentication methods don’t come from the same category to qualify as MFAs.
Multifactor authentication methods
The additional verification credentials required must be met using information from the following categories:
- Something the user knows (knowledge) such as passwords or pins,
- One thing the user has (possession) such as a smartphone app, or
- Something the user is (inherent) such as fingerprints, retina scans, facial recognition, voice recognition, or behavioral analysis.
Aside from using the ATM at the bank, the most common MFA requirement example is the one-time based password (OTP) method. With OTP, you’re required to log in and provide a temporary passcode sent through an email, phone call, or text message.
However, there’s more to this authentication method than this, and that’s what we’re here for.
Major multi factor authentication examples and methods
Here are some concrete examples to better understand MFA…
Knowledge-based MFA
This is the most commonly used and vulnerable method of multifactor authentication. It’s usually based on passwords, PINS, or answers to security questions. Having just passwords in place can be a bit tardy and pose a threat to security, despite being seemingly straightforward.
First, we have different platforms where we need to enter passwords to gain access. It’s very tempting to use one password across all platforms. However, doing so can pose a significant security threat. If one platform is breached, the impersonator can potentially access all of a person’s internet resources.
On the flip side, maintaining different passwords for different platforms can be tiring. Besides, one can easily forget a particular password.
Security questions may seem like a more efficient option, especially when based on a user-friendly, dynamic, and contextualized question the user has quick access to.
The reality is that knowledge-based methods are less secure than the rest. This is why it’s important to pair them up with other categories of authentication. That’s the problem MFA has come to curb in the first place.
Possession-based MFA
Another method of authentication is through possession factors a user has. It’s likened to having a key to a lock. In this case, it’s usually via a readily available smartphone using authenticator apps, QR codes, or physical security keys (like YubiKey).
They’re usually harder to infiltrate compared to knowledge factors. This is because they’re outside the network resource. However, this method isn’t 100% foolproof as smartphones and mobile networks can present internal security issues.
A soft token is a piece of code stored in a cookie on a device. This way, the user will require software and a level of expertise to use it properly. They may get copied if they aren’t properly stored.
One-time passwords can be categorized as both knowledge and possession factors. You know them, and you get them on something you possess (in this case, your smartphone).
⚠️ Expert warning
The Risk of SMSWhile SMS text codes are common, cybersecurity experts in 2025 advise against them when possible. Hackers can use "SIM-swapping" to steal your phone number and intercept your codes. Always prefer an app-based generator or a physical key over SMS.
Inherent MFA
This category uses biological traits to verify you are who you say you are. In 2025, this is standard on most devices, including Apple’s FaceID and Android’s fingerprint sensors.
It includes biometrics like:
- Fingerprint scans
- Face recognition (FaceID)
- Voice recognition
- Behavioral analysis (how you type or hold your phone)
However, the problem with this is how some devices are not equipped with the software, processing power, and hardware necessary to use this MFA category.
What makes an authentication process multifactor is when you combine more than two different verification factors.
Beyond these three major categories, other multifactor authentication solutions are becoming mainstream too.
Passkeys
If you are tired of remembering complex passwords, there is good news. Major tech giants (Apple, Google, Microsoft) are moving toward Passkeys.
A Passkey is a digital credential stored on your device that replaces passwords entirely. It uses cryptography to log you in via FaceID or TouchID. Because there is no password to steal, it is phishing-resistant and significantly more secure than traditional MFA methods.
Other multi-factor authentication examples and methods
These methods incorporate machine learning and artificial intelligence to make more sophisticated authentication methods. They include:
Location/time-based authentication
With a combination of GPS coordinates, network metadata and parameters, and device recognition, it’s possible to authenticate systems with these adaptive data points. They don’t usually require a large amount of data from the user because they work in the background.
This type of authentication increases productivity because of their flexibility. They suit large organizations best because of the level of software and expertise needed.
Risk-based or adaptive authentication
This method is about algorithms and calculated risks derived from the context of specific login requests. It attempts to answer questions like:
- What were the user's time and location when they attempted to access information?
- What kind of device is it and how often is it used?
- What type of connection is used?
This method aims to lessen redundant logins and provide a more user-friendly workflow. It requires software to learn how users interact with a system and expertise to set up and manage. Again, it’s suited for large organizations.
Social media login
Social media logins (e.g., "Log in with Facebook") provide convenience, but they are not true MFA.
Actually, they can be a security risk. If an attacker breaches your Facebook account, they gain access to every other site you logged into with it.
Tip from our experts
Avoid using social logins for sensitive accounts like banking or healthcare.
Push-based two-factor authentication or 2FA
This is an advanced level of two-factor authentication because of the additional layers of security it works with. It sends notifications via data networks to give users data access on their mobile devices.
Multi-factor authentication vs. other authentication methods
Are there other types of authentication methods? And how is it different from MFA?
Multifactor authentication vs. two-factor authentication
It’s not uncommon to see these two terms used interchangeably. However, 2FA is just a subset of MFA. Like the names suggest, 2FA restricts the verification methods to two (usually knowledge and possession). At the same time, MFA gives liberty to go beyond two.
Multifactor authentication v. single sign-on or SSO
The single sign-on system (SSO) allows you to use a particular set of login credentials to access different systems and applications that usually require separate logins. SSO is simply about improving productivity. MFA, on the other hand, is a security enhancement channel. SSO can be a part of the MFA process but shouldn’t be independent of the latter.
How to get started on the multifactor authentication process
Okay so now you know how important it is to activate MFA for your online accounts, what are the steps you have to take?
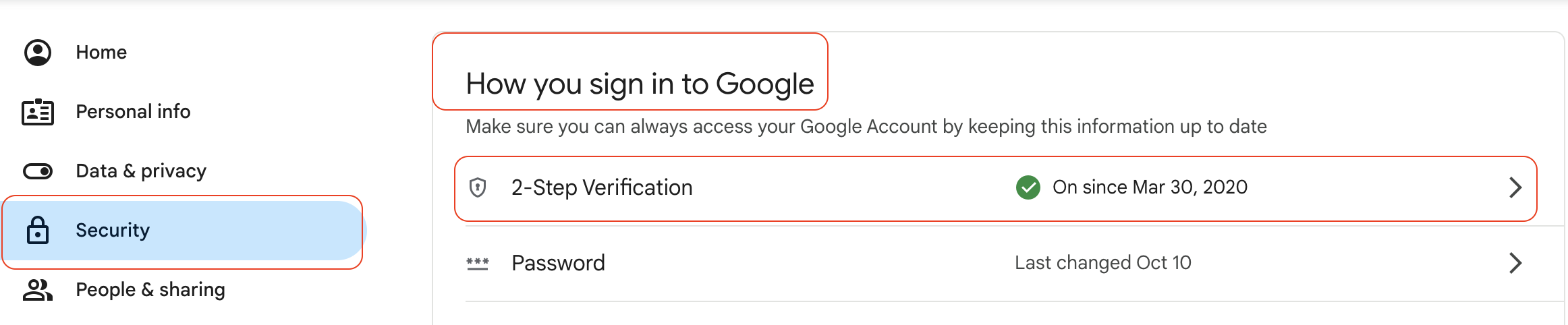
How to set up MFA on your Google account
Ready to secure your data? Here is how to enable 2-Step Verification on a Google account in 2025:
- Go to your Google Account settings.
- Select Security on the left navigation panel.
- Under "How you sign in to Google," select 2-Step Verification.
- Click Get Started and follow the on-screen prompts.
How to set up MFA on your Microsoft account
Whether you use Outlook, Xbox, or Windows 11, securing your Microsoft account is critical. In 2025, Microsoft strongly encourages going "Passwordless" using their app, but standard 2FA is the first step.
Steps to enable:
- Sign in to your Microsoft Account dashboard.
- Click on the Security tab at the top.
- Select Advanced security options.
- Scroll down to Additional security and find Two-step verification.
- Click Turn on and follow the prompts to link your phone number or authentication app.
FAQ
1. Is MFA 100% hack-proof in 2025?
No security method is perfect. Sophisticated hackers use "MFA Fatigue" (bombarding you with notifications until you click 'Approve') to bypass it. However, MFA still blocks 99.9% of automated account attacks.
2. What happens if I lose my phone?
If you lose your verification device, you can use backup codes (which you should save when setting up MFA). Without these codes, account recovery can be difficult, which proves how effective MFA is at keeping unauthorized users out.
What if MFA isn't enough?
While MFA is essential, it only protects your login. It doesn't stop spyware already on your device or physical snoopers.
That is where Clario Anti Spy steps in to cover the gaps:
- Data breach monitor: Instantly alerts you if your passwords or emails are leaked, so you can change credentials before hackers use them.
- Unlock catcher: Curious who is trying to bypass your screen lock? This feature secretly snaps a photo of anyone unlocking your device without consent.
- 24/7 human assistance: Get live help from security experts anytime you suspect a breach.
Don't leave your privacy to chance. Download Clario Anti Spy today.
Read more:


