Table of contents
- What Is Riskware?
- Riskware Examples
- Internet Relay Chat Clients
- Remote Access Software
- Internet Server Services
- How to Detect Riskware?
- 1. Software origin
- 2. Software permissions
- 3. Software updates
- 4. Terms of service violations
- 5. Lawfulness
- How To Get Rid of Riskware
- How To Prevent Riskware Threats
What Is Riskware?
Riskware refers to any legitimate software that puts your computer at risk of being targeted by cybercriminals. Not because the software is risky in itself but because it’s prone to software incompatibilities, legal violations, and security risks.
But don’t panic — not all riskware is problematic; it just has the potential to be targeted for cyber threats. That’s because cybercriminals know how to spot and take advantage of loopholes in such software. It makes it all the more important to prioritize cybersecurity, so you can keep your computer and files safe.
Finally, riskware is a type of malware, but not all malware is riskware. Remember, malware includes both legitimate and illegitimate software that is at risk of being compromised by cybercrime.
Riskware Examples
Riskware typically includes software that breaks the law, makes your computer vulnerable to malware, provides remote access, and monitors user behavior. Below are categories of such riskware.
Internet Relay Chat Clients
Some features in software programs for instant messaging services and programs for dialer services can be easily exploited by cybercriminals.
An example of a vulnerability in this instance would be a bad actor using a loophole to write a dangerous script without the knowledge of someone using a chat service. This opens them up to the risk of malware.
Remote Access Software
This category of software, also known as Virtual Network Computing (VNC), provides remote access to parts of your computer. This includes administrator privileges, as well as the desktop, utilities, and software.
Remote access software can pose security risks if it isn’t properly protected with the right cybersecurity software.
Internet Server Services
Hackers and bad actors are often prodding around to find vulnerable computers and programs. So, when they find that a user has given administrative privileges to file transfer protocol, they’ll take advantage of that.
In such cases, bad actors can access the files on your computer while you’re using the internet by installing a server.
Below are some popular riskware programs:
- Riskware.iStealer
Accesses and steals personally identifiable information like passwords and other stored credentials from chat programs, emails, etc.
- Riskware.ifeohijack
A form of malware that uses a registration key to set a debugger for other executables.
- Riskware injector generic
These game-hacking tools give players an unfair advantage over others using DLL injection. The tools can also be used for malicious purposes.
- Riskware.gamehack.generic
Similar to riskware injector generic, riskware.gamehack.generic gives players an unfair advantage and unauthorized access to gaming servers.
- Riskware.tool.ck
Allows people to use software for free illegally.
- Riskware kms
This software can illegally obtain a copy of the Windows OS software.
- Riskware.android.compromised key
As the name suggests, this one targets Android devices. It’s typically used by hackers who hijack and gain unauthorized access to your Android device to get your personal information.
- Riskware.tor
How to Detect Riskware?
Now that we know what riskware is and how you can get it, let’s jump into how you can detect it, so you can take action.
1. Software origin
Controlling and managing software is the best way to ensure it is free of malware. Check for any software on your computer that hasn't been installed by you or the IT company outsourced by your employer if using a work computer.
Pay attention
Learn how to check your Mac for viruses and malware in our guide.
A good starting point is combing through software that hasn’t been downloaded from the App Store or Google Play. Third-party software programs from unknown sources or developers sometimes come with vulnerabilities that can be easy for hackers to take advantage of. If you can’t verify the source of a software program on your computer, chances are you have a case of riskware.
2. Software permissions
Many of the apps and software programs we use daily require permissions like access to your computer’s camera, microphone, contacts, and more.
Make sure that any permissions granted on those apps and programs have been given by you or someone authorized to do so. If you can’t confirm this to be the case, you might be at risk and your privacy could be compromised. Bad actors misuse the data from such permissions.
3. Software updates
Check that any software and apps you have on your computer are still updated. Apps that haven’t been updated in a while or that don’t get updated consistently are prone to getting bugs and malware, and could also get riskware.
That’s because hackers can target such apps to get unsuspecting users to give up their sensitive information, which they can then misuse for malicious activity. The same is true for software updates on your computer.
4. Terms of service violations
When was the last time you read a software program’s terms of service? You probably can’t remember — and you wouldn’t be the only one.
Most people are guilty of rushing to agree to software terms and conditions without reading them because they’re too long or are filled with legal jargon.
Take the time to read these, so you can spot any violations you might want to steer clear of to avoid falling victim to hackers and bad actors.
5. Lawfulness
Let’s face it, not all programs completely abide by the law. However, some are blatantly illegal. You want to stay away from pirated software and any software that allows you to skirt the legal system, so you don’t expose yourself to hackers.
How To Get Rid of Riskware
Unlike viruses that typically exist natively on your computer, riskware exists within software programs that have security vulnerabilities.
If you’ve checked your computer and software programs and found evidence of riskware, you need to take action to remove it immediately. The best way forward is to use cybersecurity software to do the job.
Clario is an all-around antivirus and web protection app that can help you detect malware, so you can protect yourself from identity theft and other cybercrime. The Antivirus tool effectively removes malware, like riskware, before it’s too late.
Why not take advantage of Clario’s 7-day free trial and see for yourself? It allows you to check for any riskware and remove it within moments. Follow the steps below to remove riskware from your device with Clario:
- Download Clario on your computer
- Set up your account
- On the dashboard, click on Quick Scan and wait while Clario looks for any viruses on your computer
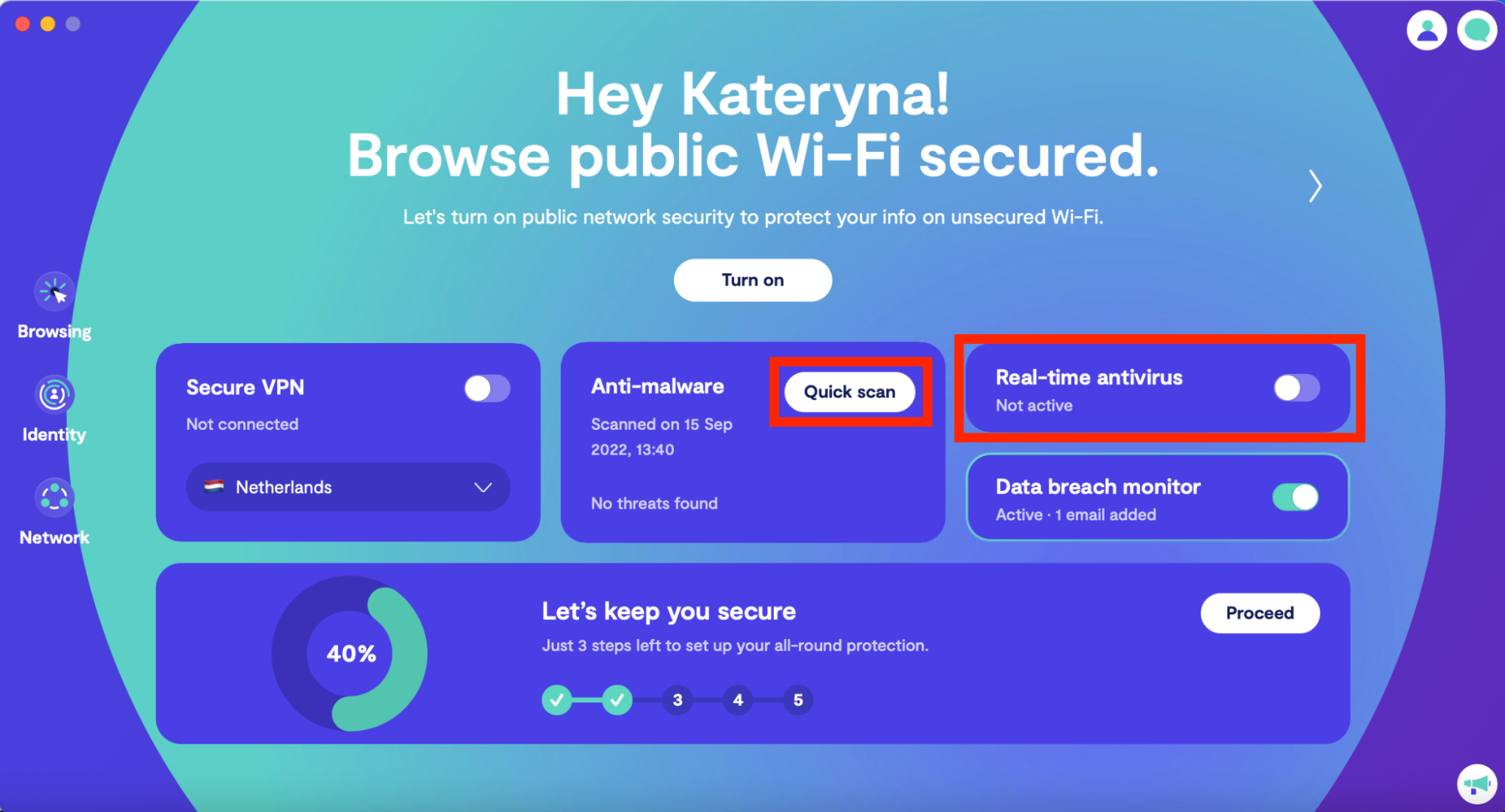
4. After the scan is done, Clario will show you any threats it identified and guide you in getting rid of them
5. Don’t forget to toggle the switch for Real-time antivirus to allow Clario to be on your guard 24/7.
If Clario finds any malware on your computer, follow the guide to remove it. Restart your computer when you’re done.
How To Prevent Riskware Threats
As you’ve seen, weeding out riskware is a process. It certainly isn’t something you would want to deal with if it can be prevented. Protecting yourself from riskware also helps you prevent identity theft.
Practice the following habits to avoid getting riskware threats on your computer:
- Only download apps from official vendors, like the App Store and Google Play. Not all software from other vendors is dangerous, so use your discretion and do your research before installing it on your computer.
- Read the terms of service or terms and conditions for any software you install.
- Be careful about accepting extensive and long-winded terms and conditions — especially those that don’t provide clear reasons for those terms and conditions.
- Research legal jargon in software terms and conditions to ensure you know what you’re agreeing to.
- Read the software prompts on the screen carefully while you install it on your computer.
- Ensure you keep the software you downloaded up to date.
- Keep your computer’s operating system (for example, macOS for Mac devices) up to date.
- Never leave your computer unattended, as people can install malicious software on it if they can access it.
- Get rid of any software programs you haven’t downloaded yourself or don’t recognize.
- Never take the risk of downloading illegal content and software programs (Remember: it’s illegal to download pirated movies and TV shows, just as it is to operate pirated streaming sites in the United States).
- Likewise, avoid downloading explicit content on your devices.
- Stay away from software programs that have administrator privileges.
While the list above may seem exhaustive, most of these are steps you should already be taking to protect your personal data. Along with the list of best practices we’ve mentioned, keep Clario’s Real-time antivirus feature toggled on. This will allow Clario to constantly scan your computer for viruses and malware in the background.


