Table of contents
- What is a watering hole attack
- Goal of watering hole attack
- Signs and symptoms of watering hole attack
- How does a watering hole attack work
- 1. Intelligence gathering
- 2. Analysis
- 3. Preparation
- 4. Execution
- Watering hole attack examples
- How to prevent a watering hole attack
- Conclusion
What is a watering hole attack
A watering hole attack targets a specific group of individuals by compromising the websites or online resources that the group frequently uses. These attacks are sneaky because targets are less likely to be cautious of familiar web pages. Also, the strategy helps prevent the attack from being traced back to the perpetrator.
The victim of wateringholing can be an individual, a network, or a group of individuals. Sometimes, governments use waterhole attacks via state-sponsored agents to spy on private companies or political enemies.
Since watering hole exploits are crafted specifically for their target, they are considered a form of social engineering. Like phishing, their deceptive nature helps them effectively breach several layers of security. And though they are uncommon, their consequences can be severe since they often target large enterprises or high-profile individuals.
Goal of watering hole attack
A watering hole attack aims to infect the targets with malware, gain unauthorized access to their devices, or steal their sensitive data. Wateringholing often targets high-profile individuals and enterprises, and there are many objectives watering holes attackers can carry out with network access.
Here are some goals associated with watering hole attacks:
- Data theft: Attackers may hope to steal valuable and sensitive data, like intellectual property, financial data, login credentials, and personal data. And, in some cases, classified information.
- Infiltration: For some attackers, waterholing is network access, leading to malware attacks or reconnaissance for future attacks.
- Disruption: Other times, a watering hole attack is meant to sabotage the normal operations of an organization, resulting in a disruption of services and/or a loss of profits.
Signs and symptoms of watering hole attack
It’s difficult to detect a watering hole attack due to the indirect nature of the exploit.
By definition, a watering hole attack does not directly target the victim. Instead, it targets the victim’s resources first. So, the origins and intent of a watering hole attack are deliberately obscured.
Still, though not definitive, there are some approaches to identify an attack. Waterholing directly compromises trusted websites, so it’s a good place to start looking. Here are some signs and symptoms of a watering hole attack:
- Unusual behavior on trusted websites: Frequent crashes, unexpected errors, and suspiciously slow load times are all signs of watering hole attacks—and other website-based cyber attacks. Learn how to avoid pharming and other website-related cyberattacks.
- Security warnings: If your antivirus or antimalware tools start alerting you that trusted websites are dangerous, take note. Also, watch out for browser warnings about outdated or invalid security certificates.
- Strange pop-ups and redirects: It’s suspicious if trusted websites are suddenly flashing pop-ups or redirecting you to unfamiliar (i.e., unsafe) websites. Also, look out for website appearance or content changes, which could be due to tampering.
- Unwanted downloads: It’s not a good sign if your browser suddenly starts downloading files or software you didn’t initiate. If this occurs, delete the downloaded file—do not open it!
- Login issues: It’s a definite red flag if you're having trouble logging into your accounts—especially if you're getting notifications that your login credentials are incorrect. An attacker may have changed your login details.
- Weird account activity: Immediately address any notifications or alerts about unusual account activity or access attempts. Or of any changes to account settings or personal information. Someone might be trying to hijack your account.
How does a watering hole attack work
A watering hole attack works in four distinct stages:
To understand the ins and outs of waterholing, let’s dig deeper into these stages:
1. Intelligence gathering
Since waterholing compromises a target’s commonly used web pages, the attacker must research what websites and services the target frequents. This can include industry-specific forums and websites, social media, or even the target's website.
2. Analysis
Once the attacker narrows the attack vector, they will poke around to determine how the target interacts with the web page. They will also use tools and techniques to identify and exploit possible vulnerabilities on the web page.
3. Preparation
Once the attacker homes in on the targeted service’s weaknesses, they can craft their attack. They may exploit vulnerabilities in software, inject malicious code into a site’s content, or gain unauthorized access to a website’s server. Some common attacks are:
- Injecting malicious SQL code into a website’s input fields or URL parameters
- Cross-site scripting (XSS) malicious code into web pages.
4. Execution
Once the target visits the compromised web page, they may unknowingly download and execute the payload from the step above. Because the web page is “trusted,” the attack can bypass a network’s security. Once it enters the network, the attack could spread or gain more info for future attacks.
Watering hole attack examples
Watering hole attacks are relatively rare. But since they go after ambitious targets, like large enterprises or important individuals, they can be very consequential when they're successful. Waterholing is also commonly used by some governments to restrict and control private citizens. Here are some notable examples of watering hole attacks:
- The Chinese government (ongoing): Several reports have indicated that the Chinese government carries out watering hole attacks against government agencies, businesses, and organizations in multiple countries. All in an attempt to obtain sensitive government and corporate information.
- DarkHotel APT Group (ongoing): The DarkHotel advanced persistent threat (APT) group has been behind several watering hole attacks targeting high-profile individuals, like business executives and government officials. The group compromises the Wi-Fi networks at luxury hotels and the victims unknowingly download malware when they connect to the Wi-Fi.
- Hong Kong (2021): According to Google’s Threat analysis group, during protests against Hong Kong’s government in 2021, a high number of watering hole attacks were implemented on people visiting media and pro-democracy websites. Specifically, the attack would install a malware backdoor on individuals using Apple devices.
- Holy Water (2019): This attack targeted religious, charity, and volunteer websites. “Holy water” used a malicious Adobe Flash player pop-up for a drive-by download attack, in which malware is automatically installed on a victim's computer without their knowledge.
How to prevent a watering hole attack
Though they are crafty, you can prevent a watering hole attack. Like with other cyber attacks, prevention requires taking proactive steps to protect yourself and your organization. Here’s how to prevent a watering hole attack:
- Use cybersecurity best practices: Most cyberattacks, including a watering hole attack, can be avoided by using cybersecurity best practices. This involves recognizing suspicious web activity and being careful about downloading files and attachments from untrusted sources.
- Employee training and awareness: Because waterholing often targets businesses, it’s key that employees understand how this sneaky attack operates so they can spot one before it spreads.
- Network segmentation: Watering hole attacks aim to spread throughout an entire network. Network segmentation will make it more difficult for a successful waterholing ploy to run through an entire network.
- Website security: Ensure that the websites that you use are secure. Look out for any suspicious changes that suggest it’s been compromised.
- Collaborate with cybersecurity experts: Waterhole attacks are deceptive. Cybersecurity experts can tailor-make a defense plan based on your network’s unique vulnerabilities. Learn what a honeypot is and identify them in your organization.
- Use a cybersecurity tool: Tools like Clario Anti Spy contain a suite of cyber protection tools to protect your network and devices from all angles. It includes a breach detector that alerts you to data leaks and a device system check that spots weak points attackers often rely on, such as outdated software or signs your phone’s security has been tampered with.
Steps to run Device system check on Clario Anti Spy:
- Download Clario Anti Spy and create an account.
- Open the app and tap Device system check.
- Tap Scan to check for jailbreaks, outdated software, or major threats.
- Apply any recommended fixes to secure your device.
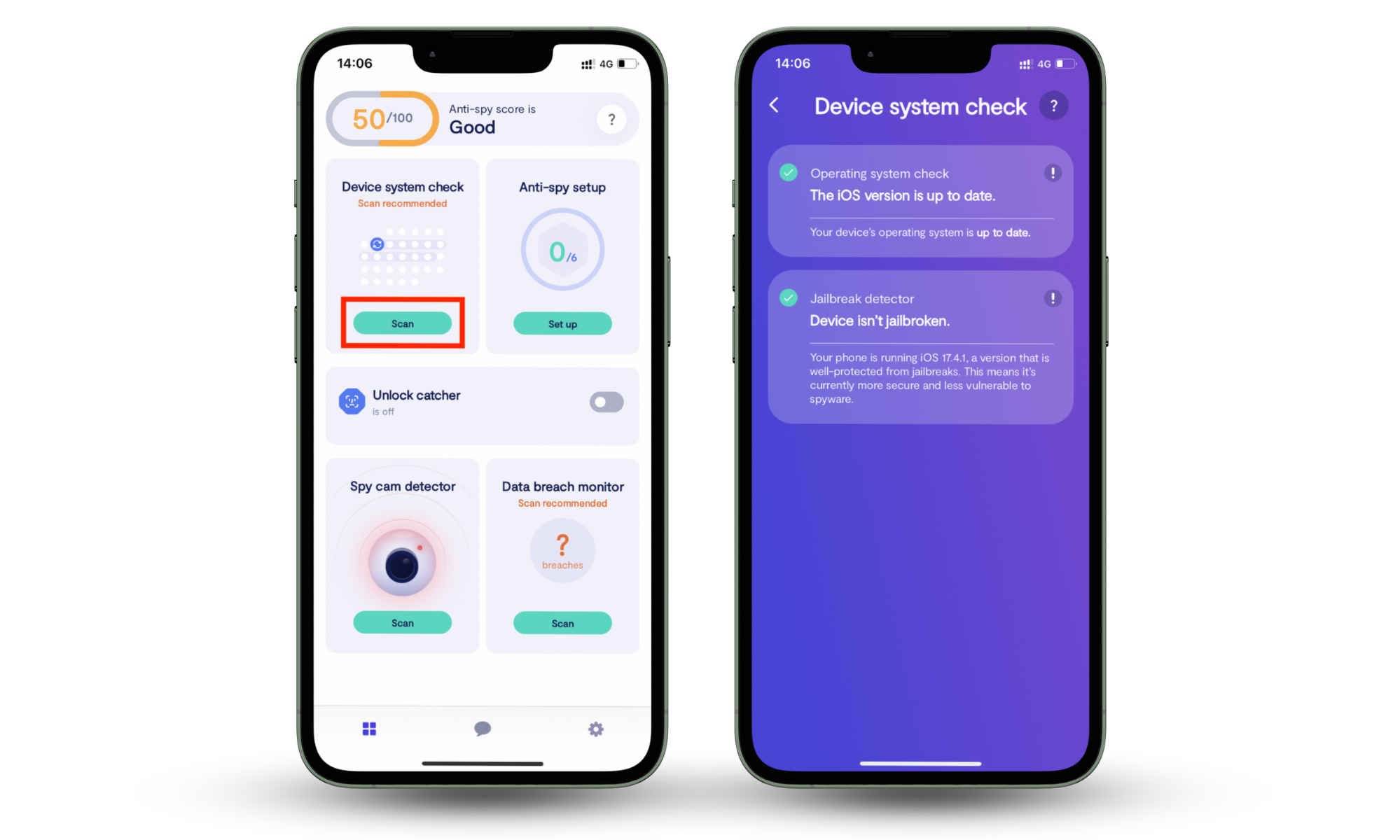
Clario Anti Spy helps you catch security issues early, especially if you have connected to a public network or visited a compromised site.
Conclusion
Although watering hole attacks are rare, they show how easily trusted sites can be used against you. To protect your device from this and other online threats, use a dedicated anti-spy tool like Clario Anti Spy. Its device system check can spot jailbreaks or outdated software, making these attacks easier to pull off.
Run that scan today and find out if your phone is as secure as you think.


