Table of contents
- What is Anatsa
- Infection vectors and distribution channels of Anatsa
- Technical analysis and capabilities of Anatsa
- Should regular Android users worry about Anatsa
- How to protect yourself against Anatsa
- Conclusion
What is Anatsa
Anatsa, also known as TeaBot and Toddler, represents a sophisticated banking trojan targeting primarily Android devices. It is a combination of a traditional Trojan horse virus and a remote administration Trojan (RAT), i.e., it allows hackers to remotely control your device in stealth mode. They can access system files and run arbitrary commands.
Arbitrary commands are dangerous because they are not part of your device's intended functionality. When attackers can run these commands, they can compromise and control your system, install malware, and steal data without your participation or consent.
This full control enables long-term spying on victims' financial activities. The thing is, Anatsa malware was designed to penetrate your banking app and drain your account. It can lead to significant financial losses. Moreover, since the hackers can steal your sensitive information, it can result in identity theft and further damage to your reputation.
Recovering from this type of attack always takes a lot of time and effort. Besides, full reimbursement is never guaranteed even if you're insured. What you can do is take preventive measures. Try Clario Anti Spy to scan your Android or iOS device for potential threats.
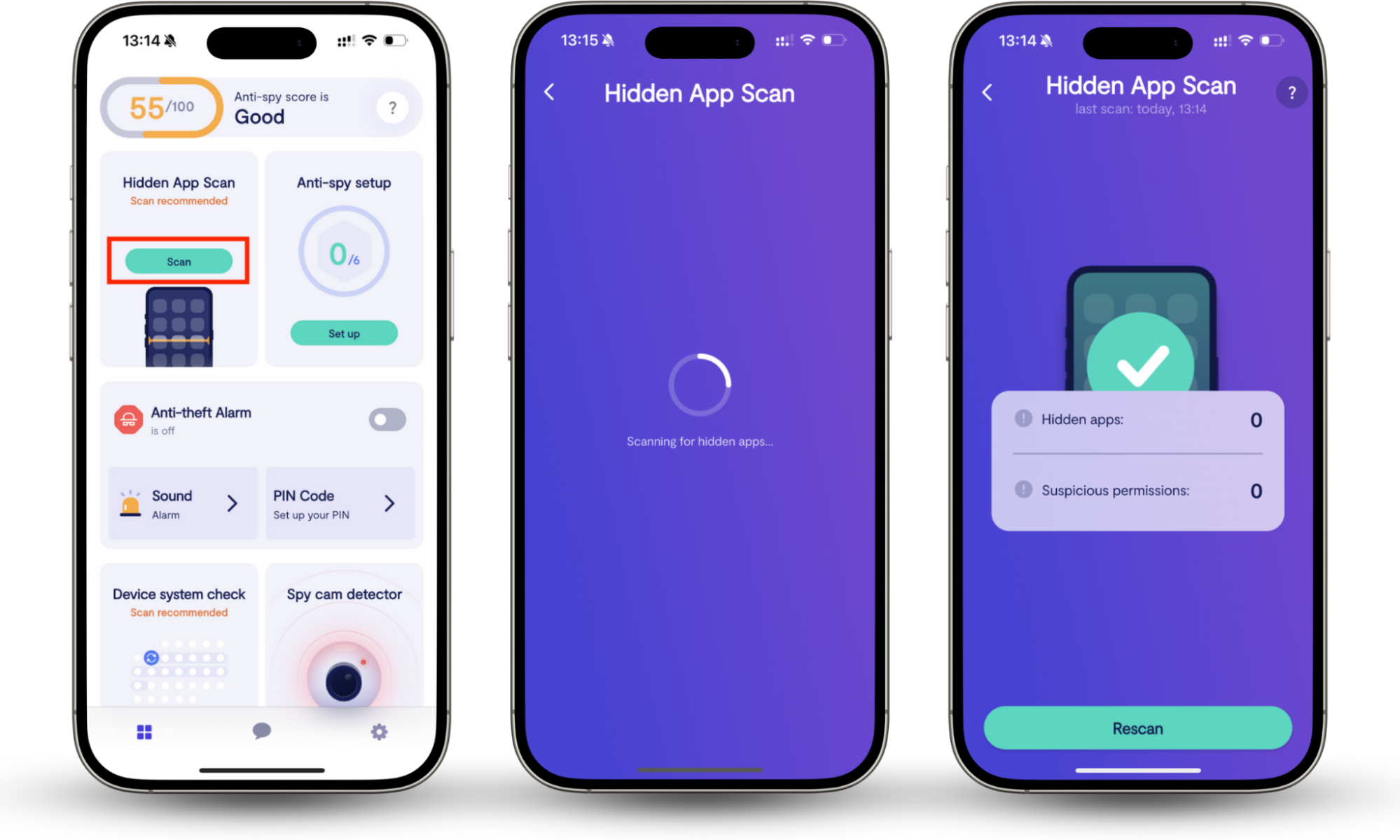
Our Hidden app scan examines your mobile phone for suspicious apps that might've been installed without your knowledge. It also scans all your apps and the permissions they have, so you can stay in control of what info different apps can access.
Here’s how to use Hidden app scan:
- Download Clario Anti Spy and set up your account.
- Navigate to Hidden App Scan feature and tap Scan.
- Wait for scan results. If our app detects suspicious permissions, it will notify you and advise on further steps.
Infection vectors and distribution channels of Anatsa
Anatsa often uses Google Play dropper as its distribution strategy. It masquerades as a legitimate app, most often as QR code scanners, PDF readers, document viewers, and office suites. Once downloaded, the fake app notifies the user that it needs to be updated. After the update, it redirects the user to an unknown source for other app downloads. This way, Anatsa opens backdoors to different types of malware, such as viruses, adware, spyware, keyloggers, ransomware, etc.
Once the installation is finished, Anatsa requests Accessibility Service for further access to the user account. It then infiltrates and takes over the victim's device.
Note
A recent example of an app that served as a dropper for Anatsa is Document Viewer - File Reader. Sensor Tower shows that since the app's release on May 7, 2025, users have downloaded it around 50,000—100,000 times. It successfully evaded detection due to the cyclical nature of the Anatsa malware. The app functioned as advertised for a certain period of time after download. However, at a predetermined time, upon receiving a command from its command-and-control server, the dropper app installed the actual Anatsa payload. In this particular case, the Document Viewer - File Reader app transformed into a malicious one roughly six weeks after release.
Visiting compromised websites can trigger drive-by downloads—unintentional downloading of malicious software. A user doesn't even have to click on any links or attachments to install Anatsa malware unintentionally. The website's compromised plugins or vulnerable browser can contain a Trojan downloader that triggers the download as soon as the user appears on the site.
Technical analysis and capabilities of Anatsa
Once installed, the Anatsa malware obtains configuration data and target lists specific to the infected device's location from its command-and-control servers. To avoid detection, it employs runtime decryption. Using dynamically generated Data Encryption Standard (DES) keys, the malware implements anti-analysis techniques, preventing security researchers from analyzing and detecting it.
Anatsa’s behavior post-installation exemplifies its advanced technical capabilities. The malware captures screenshots of users’ interactions with financial apps and records keystrokes. This allows for real-time credential harvesting, which then enables Anatsa to bypass two-factor authentication. It steals login credentials and passwords, then uses this information to conduct Device-Takeover Fraud (DTO) and initiate fraudulent transactions from the victim's devices.
One of Anatsa's most dangerous technical capabilities is overlaying. This is a screen overlay attack in which a threat actor places a scam window on top of an actual banking app. A user interacts with the app, providing info directly to cybercriminals without suspecting any malicious activity. These overlay attacks create opportunities for immediate financial theft.
Should regular Android users worry about Anatsa
Anatsa poses significant risks not only for financial institutions but also for regular Android users. Since malware often piggybacks on average legitimate apps or disguises itself as one, even security-conscious users may be exposed to this type of threat. Individuals who frequently transact significant sums represent high-value targets for Anatsa attacks.
In early 2024, Anatsa was detected primarily on devices in the UK, Germany, Spain, Slovakia, Slovenia, and the Czech Republic. Now, however, the malware also infects devices in the US, Germany, Austria, and Switzerland. Its latest modification has attacked over 831 financial institutions worldwide, adding users in South Korea to its long list of victims.
How to protect yourself against Anatsa
Anatsa continues to evolve, so you need to stay vigilant and take action to protect your device. Here are some steps you can take to stay safe and protect yourself against this malware:
- Avoid app downloads from third-party sources and unknown websites to protect yourself from SMS Trojans.
- Read user reviews and check ratings before installing new apps.
- Don’t click on links received via SMS or emails from an unknown contact.
- Don’t click on ads when browsing through websites.
- Regularly inspect your device for suspicious permissions or apps you didn’t install.
- Utilize tested and proven security tools and antivirus applications.
Note:
Clario Anti Spy’s Hidden app scan helps you detect and delete potentially harmful apps from your device. It will also review your other mobile applications and their data access permissions so you can maintain oversight of what information these apps can view.
If your device is infected with Anatsa and you’re still in control of your device, you can try to remove the malware yourself. Here are several tips on how to do it:
- Disconnect your device from the internet.
- Reboot in safe mode.
- Conduct a full system scan with the help of a reputable antivirus software.
- Once the antivirus finds the malware, delete it.
- Conduct a full system scan again.
- Set new passwords for your accounts and stay alert to any suspicious activity.
Conclusion
Anatsa’s ability to run undetected, conduct overlay attacks, and bypass two-factor authentication makes it one of Android users' most dangerous security threats. To avoid Anatsa Trojan attacks, carefully inspect the app before downloading it. Read through user comments and ratings, and try to find developer information online. Also, avoid clicking on links you receive via email or SMS from an unknown sender.
To check your smartphone for malware, use Clario Anti Spy’s Hidden App Scan. It will scan your mobile device, whether iOS or Android, for signs of suspicious apps so you can detect and remove them immediately. It will also analyze all your other apps and their permissions to your data to identify intrusive ones.


