Table of contents
- Common types of malware with examples
- Viruses
- Adware
- Fileless Malware
- Worms
- Trojans
- Bots
- Ransomware
- Spyware
- Rootkits
- Keyloggers
- How to prevent different types of malware attacks on your device
- Avoid suspicious emails, links, and sites
- Adjust spam filters
- Keep software up to date
- Use multi-factor authentication
- Back up files
- Know the signs to look out for
- Use antivirus software
- Summary
Common types of malware with examples
With malware attacks on the rise it’s essential for you to be clued up on what to look out for when browsing online. Take a look below on our breakdown of the different types of malware and become an expert on how to avoid falling victim to cyber crime. Malware examples include:
Viruses
Viruses often lay dormant inside infected applications or programs. In most cases it is the users who will trigger the attack on themselves by running a certain process, executing a certain file, or even downloading an email attachment.
If you fall victim to a virus then expect your applications on your device to be seized, infected files sent to your contact list to try and spread the virus to others, DDoS or ransomware attacks launched and your private data stolen.
Adware
If you are seeing an excessive amount of unwanted adverts on your device, there’s a chance you have got adware infecting your device. Advertising-supported software, as it is commonly called, is more of an annoyance to you but if it isn’t dealt with it can become a problem.
While adware will usually just spam you with unnecessary amounts of adverts, it can also track your data leaving you vulnerable to data theft should you access your private information during the time of infection. If you don’t want your data being shared with third parties or to fall victim to identity theft, it’s best to get rid of adware immediately.
Fileless Malware
Fileless Malware piggybacks off legitimate scripts to execute the malicious activity onto your device while the legitimate program continues to run. This method can be much harder to spot due to its stealthy nature and the fact that a user has no reason not to trust the legitimate application.
Fileless Malware is true to its name as it is a memory-based operation – meaning no files are needed for it to work. This Malware is often used to tamper with existing antivirus software leaving you more exposed to future attacks or to steal your sensitive data.
Worms
Don’t confuse the worms you may find in the garden to the worms you might find on your device — the latter can cause serious harm to your computer. Worm malware will look to replicate itself, but unlike a virus, it does not need a trigger to do so. By the time you notice you have worms, the damage may already be done.
Be wary of opening email attachments or direct messages containing links as it is often how criminals will gain access to your device. Since worms do not need a host to operate you should be very wary of opening the doors online to let one in.
Worms will often:
- Steal your data
- Launch DDoS or ransomware attacks
- Create botnets
- Infect many computers at once
- Delete or modify your files
- Install backdoors for hackers
Trojans
Trojans, much like the historic Trojan horse war strategy, are designed to infiltrate security. They are a type of malware which poses as legitimate software or files to trick the user into installing it on their device. Once installed, the Trojan will come out and begin to inflict damage onto your system and steal your personal data.
Email attachments and website downloads are often the easiest ways that hackers will get a Trojan onto your system and it will sit waiting for the action to be launched to start its attack.
Bots
Bots can be deployed online to scour the web in search of holes in security infrastructure which can be exploited by the criminal behind them. Bots or Botnets are a type of malicious coding which can be used to hack devices directly and grant remote control access to the hacker at the other end.
Ransomware
Ransomware is a type of malware that infiltrates your device and begins encrypting all of your files. This will essentially lock you out of your device and leave you at the mercy of the hacker on the other side. The financial sum that it can cost to buy control of your device back off the hacker can be very costly and doesn’t guarantee that they will give it back.
Spyware
Like a spy in real life, spyware aims not to be caught as it surveys your data. Spyware will track your internet activity, collect your password information, and retrieve other sensitive information. This can be a difficult type of malware to identify due to its stealthy nature, so often by the time you discover it, the damage is already done.
Rootkits
Often spread through phishing or malicious attachments, rootkits can give hackers remote access to your devices while remaining undetected. Their hidden nature makes them very hard to identify, so your device can have its antivirus software disabled and it can track the activity and data of your device.
Keyloggers
Keyloggers are used to track and record what people type into their devices. This can be very dangerous for users who access their banking or other important websites as you will be handing over your login information to the hacker who has access to the keylogger data.
The best way to avoid malware is to strengthen device security. Clario Anti Spy makes this easy by guiding you through the steps to protect your iPhone or Android from spyware and other malicious apps.
Here's how to run an Anti spy setup with Clario Anti Spy:
- Download Clario Anti Spy and subscribe to create an account.
- Tap Setup under Anti spy setup.
- Select Protect device and follow the instructions to secure your phone.
- Go through the other categories to enhance the privacy and security in other areas, such as web browsing and social media.
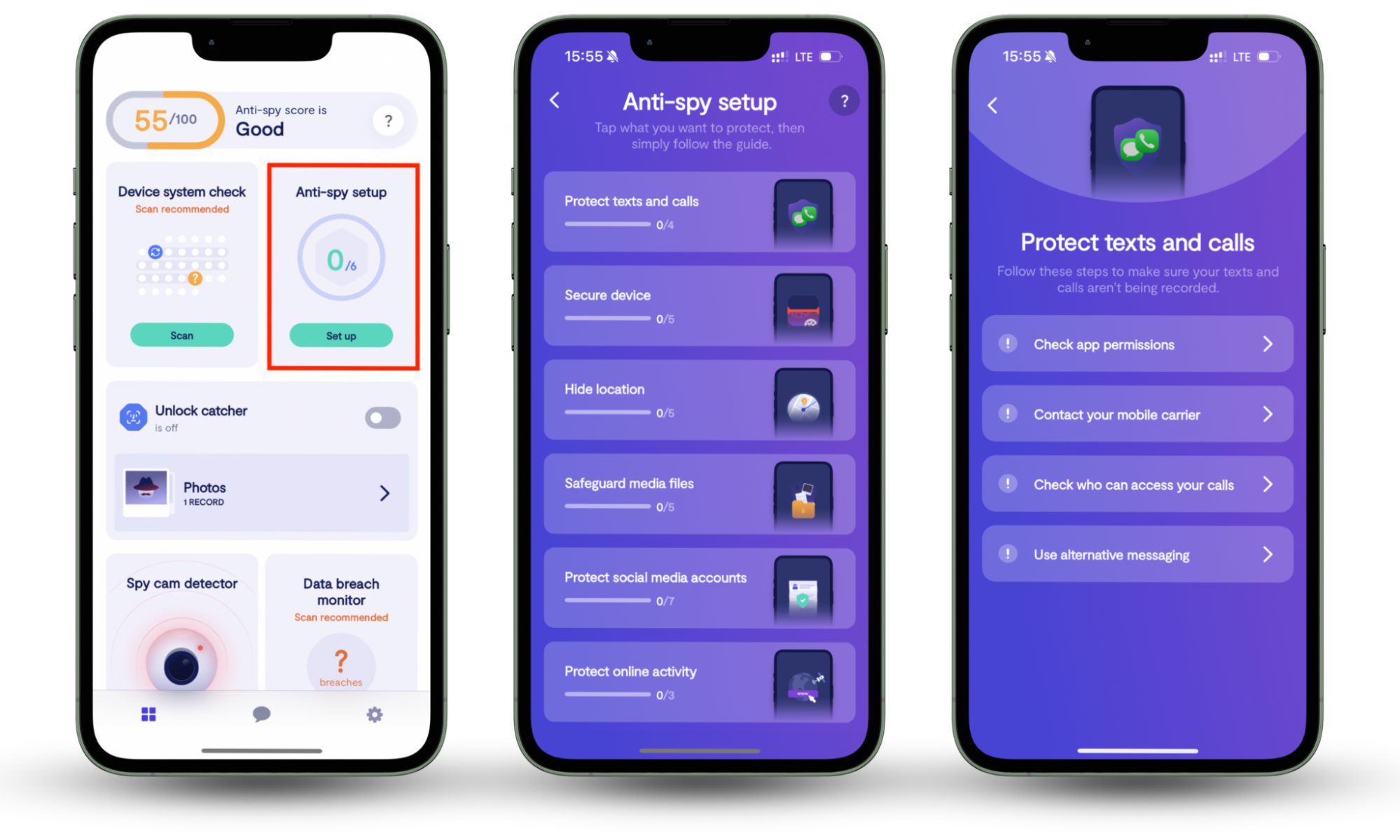
You can also run a Device system check to determine if you phone is running the most secure version of the system software. On Android, a Spyware scan allows you to detect monitoring tools and other privacy-invasive apps.
How to prevent different types of malware attacks on your device
Here’s some of the best tips and tricks you can use to help you identify and avoid malware before it infects your device — the best form of protection is prevention.
Avoid suspicious emails, links, and sites
Remember when navigating the internet it’s important to stay alert at all times. Always check for the padlock in the website address bar to make sure that the site is secure before you enter any private information. Clario's Web Protection is a browser extension that you can use to help keep you safe online. Why worry about the dangers of the world wide web? When you can simply download an extension that will analyze every link and give you the green light on the ones that are deemed safe-to-click. On top of this, should you click a suspicious link, Clario will pause the page from loading and tell you that the link isn’t safe and shouldn’t be trusted.
Adjust spam filters
Understanding where most malware exists is important. Since email is the easiest and most common place for hackers to target your device, up your spam filters to the highest settings and add an extra layer of protection to your online browsing.
Keep software up to date
There is a reason software updates are released so regularly. As the complexity of online scams and malware attacks increases and hackers become more sophisticated, so do company’s defense systems. Stay up to date with the latest software and you will benefit from the added layers of defense the company has added to combat the latest scams.
Use multi-factor authentication
Add an extra layer of security to your private accounts by adding a second layer of verification to each account’s login process. This can be the key between falling victim to a successful cyber attack or stifling the hackers attempt as they meet a second or third wall after breaching the first layer of defense.
Back up files
Since so many cyber attacks look to lock you out of your files or delete them, by having a regular backup of your data you can save yourself a lot of money and a headache by being able to simply and quickly restore your files if they ever become compromised.
Know the signs to look out for
Here’s some of the easiest signs you can look for to discover whether your device has been infected with malware:
- Your device's performance has become unexpectedly slow, sluggish or started to crash.
- Your individual programmes operate on their own, whether that be opening and closing without your command.
- Malware often drains your storage, so be sure to keep an eye out for any drastic storage reductions.
- Increased amount of obnoxious adverts showing on your device.
- Friends start asking you about emails containing links that you don’t recall sending — hackers will target your contact list to maximize their chances of infection.
Use antivirus software
Antivirus software is a useful way to let the experts handle your safety, especially on desktop devices. These programs continuously monitor for threats in real time to keep your system safe. There are plenty of options for Windows and Mac, so you should be able to find one that matches your security needs. For mobile devices, a reputed anti-spyware solution like Clario Anti Spy should be enough to keep your phone secure.
Summary
After reading this guide, you should feel confident about how to identify and, most importantly, avoid any malicious online threats. Not only are you now an expert on what the different types of threats are to look out for, but you’ve also got the top tips on how to safely navigate the world wide web.
For best results, you should also invest in a security solution to keep your devices secure—don't forget that Clario Anti Spy can help you shield your iPhone or Android from spyware and other malicious apps.


