Table of contents
- Can turning off your phone stop hackers?
- Why powered-off phone cannot be hacked
- Rare exceptions when hacking might still be possible
- How to know if your phone is hacked?
- You notice apps you don’t recognize on your phone
- Your phone works slowly
- Mysterious data usage spikes
- Strange behavior
- Spammy pop-ups
- How can you stop someone from hacking your phone?
- Change your passwords immediately
- Run anti-malware software to detect any malicious applications and processes
- Turn off your mobile data and Wi-Fi when not using them
- Remove the suspicious apps immediately
- Inform your friends and contacts
- Stop broadcasting your personal hotspot
- Restore your phone to its factory settings
- Conclusion
Can turning off your phone stop hackers?
Yes, turning off your phone can stop hackers. In many cases, it disrupts and stops a hacker's activity, but it's not a guaranteed solution against the most advanced attacks, as any hidden malware may reactivate once the phone is turned back on. For the majority of users, a completely powered-off phone cannot be hacked remotely.
Why powered-off phone cannot be hacked
When your phone is completely powered off, all active processes are shut down. Wi-Fi, Bluetooth, background services, and all apps stop running, which means there's no way for the device to send or receive data.
Since the phone is no longer communicating with any network, a hacker can't push commands, collect information, or maintain a connection.
On a normal, non-compromised device, the shutdown process also stops any malware that may have been running in memory. With no power, the hardware can't execute code at all, and that makes remote hacking impossible in everyday situations.
Rare exceptions when hacking might still be possible
There are rare exceptions involving highly sophisticated attacks that can bypass a phone's normal shutdown behavior. These fall into the category of state-level or hardware-based threats, and they are far beyond anything an everyday user would ever have to deal with.
These rare exceptions include:
- Firmware-level compromises: If malware infects low-level components such as the baseband or bootloader, it can survive a shutdown and activate again when the device boots up.
- Fake shutdown attacks: Some advanced spyware can imitate the shutdown screen while quietly keeping certain hardware components active in the background.
- Low-power mode chip exploits: Modern phones have tiny co-processors that stay on for features like Find My. In extremely rare cases, an expert hacker could try to target these chips.
Again, these situations require a lot of expertise and access to expensive, specialized tools. For regular users, fully powering the phone down is more than enough to interrupt and block any real-world attack.
How to know if your phone is hacked?
Just like any other device, your phone can be hacked. While hackers can be subtle, there are always telltale signs to know if your phone is hacked. If you have suspicions, here are common indicators of a hacked phone:
- You notice apps you don’t recognize on your phone
- Your phone works slowly
- Mysterious data usage spikes
- Strange behavior
- Spammy pop-ups
Let’s take a closer look at these hacked phone signs.
You notice apps you don’t recognize on your phone
You probably know your personal phone better than anyone else. If you suddenly see unfamiliar apps or settings, it could be hacker activity. Also, look out for text messages or calls you didn’t send or purchases you didn’t make. All this activity indicates unauthorized access to your phone.
Your phone works slowly
If your phone is suddenly slow, frequently crashing, overheating, or if the battery drains quickly, a hacker could be the culprit. Hacking tools and techniques consume a significant amount of resources and can compromise your phone’s performance. Malicious apps and software installed by hackers can also max out your system and cause performance issues.
Mysterious data usage spikes
Are you suddenly out of mobile data? An abrupt increase in data usage could be due to a compromised device. Malware or spyware running in the background of your phone to track your activity could be using data to transmit information.
To be sure, run Clario Anti Spy’s Hidden app scan and check if any hidden apps are secretly using your data. Clario Anti Spy’s Hidden app scan can reveal if spyware or stalkerware is behind it. These malicious apps don’t just eat up your data; they can also spy on your calls, texts, location, and accounts. Running a scan helps you catch them early, remove the threat, and stop someone from quietly monitoring your private life.
Follow these steps to run the Hidden app scan:
- Download Clario Anti Spy, and create an account.
- Tap Hidden app scan, then Scan.
- Review results and follow the app’s recommendation on what to do with the detected apps.
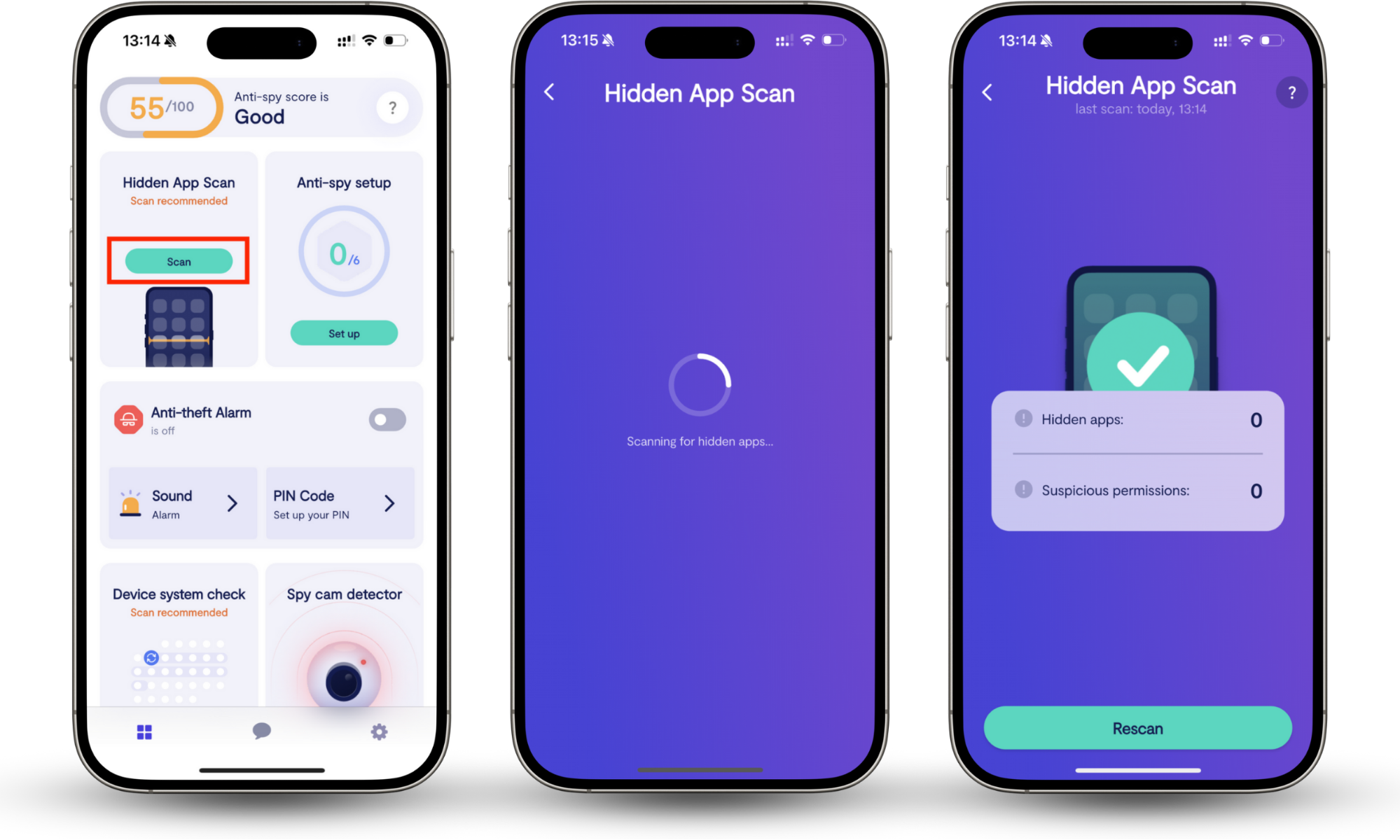
After running a Hidden app scan, it's a good idea to take advantage of the other features in Clario Anti Spy. You can run a Device system check to confirm your phone is up to date and that it hasn't been jailbroken or rooted. You can also go through the Anti-spy setup, which helps enhance the privacy and security settings of both your device and your online accounts.
If anything feels off or you need extra help, tap the Messages icon to talk to a Clario expert 24/7. They deal with all kinds of security concerns, and here's what one expert shared about a customer who suspected their device had spyware:
"The customer contacted us with a concern that their WhatsApp messages might be monitored, expressing suspicion that a hidden application may have been installed on their device without consent.
In response, we recommended running a comprehensive Hidden app scan, designed to detect potentially malicious or unauthorized apps that could facilitate covert surveillance or data interception.
Following the scan, the tool flagged a suspicious application, which the customer confirmed they did not recognize or recall installing. Based on the app’s characteristics and name, it appeared highly likely to be the source of the unauthorized access. We advised the immediate removal of the app and provided clear instructions on how to do so safely.
To further protect the customer's privacy, we offered guidance on how to enhance the security of their WhatsApp account, including steps such as enabling two-step verification and reviewing linked devices.
Additionally, we recommended contacting their cellular service provider to verify and reinforce the security of their SIM card, as SIM-based attacks can also compromise messaging services.
The customer expressed sincere appreciation for the detailed support and confirmed that they felt reassured by the steps taken."
Strange behavior
The end goal of many hackers is to get access to your device. If you notice strange device or account behavior, they may have achieved that goal. Be wary of new account activity, changed passwords and account settings, or login attempt notifications.
Spammy pop-ups
Frequent pop-up ads are a sure sign of adware or spyware. Hackers are trying to get you to click them—don’t. These pop-ups link out to malicious websites or downloads that result in malware and unauthorized device access.
Though these are some common signs, you should use your instincts. Hackers are crafty and may use unconventional methods to hack someone’s phone. If you suspect something, take a close look at your phone’s activity.
How can you stop someone from hacking your phone?
To stop a hacker, you must cut off their access to your device and personal data. It’s crucial to act quickly. Failure to do so could result in device damage, financial repercussions, and the spread of the attack to your contacts.
Here’s how to stop a phone hack:
- Change your passwords immediately
- Run anti-malware software to detect any malicious applications and processes
- Turn off your mobile data and Wi-Fi when not using them
- Remove the suspicious apps immediately
- Inform your friends and contacts
- Stop broadcasting your personal hotspot
- Restore your phone to its factory settings
Change your passwords immediately
From email to social media to banking, your online accounts are highly valuable targets for hackers. If you’ve been hacked (or even suspect you have been) you should immediately change your account passwords. The data held within those accounts are too valuable not to take this precaution.
Run anti-malware software to detect any malicious applications and processes
Quality anti-malware software can provide comprehensive protection against hacker threats. Anti-malware tools are designed to scan your phone for apps and files that shouldn’t be there. They look for spyware, trojans, adware, and other malicious code that can slip through suspicious links, downloads, or fake apps. A good program will also check app permissions, monitor for unusual background activity, and alert you when something is trying to tamper with your system.
Running regular scans helps you catch threats early, remove dangerous apps before they steal your data, and restore your phone’s normal performance.
On Android and iPhone, don't forget that you can run a Hidden app scan with Clario Anti Spy to quickly detect apps that are hidden or have excessive permissions.
Turn off your mobile data and Wi-Fi when not using them
Turning off your mobile data and Wi-Fi may stop a hacker tool that feeds off an internet connection. In general, you should avoid public Wi-Fi—especially without a VPN—it’s an easy way for hackers to get to your device.
Remove the suspicious apps immediately
Suspicious apps may be installed on your device by hackers, who use them to carry out attacks. Removing these apps could help to reduce damage and stop the threat. Be sure to delete the app you don't recognize completely, and not just disable it.
To check and delete apps on your phone:
- Open the Settings app.
- Go to General > iPhone Storage (iPhone) or Apps > See all apps (Android).
- Go through the list of apps, tap any app you don't recognize, and select Delete App or Uninstall.

Inform your friends and contacts
If a hacker gains access to your friends and other contacts, the attack could spill over to them. Inform them about your situation so that they can stay vigilant to any suspicious activity or strange communication from your number. This could prevent the potential spread of the threat.
Stop broadcasting your personal hotspot
Broadcasting a personal hotspot gives others access to the internet using your data—including hackers, if you’re not careful. If you’ve been hacked, chances are the threat is using your hotspot to access your device and data. Turn your personal hotspot off to prevent this possible point of connection.
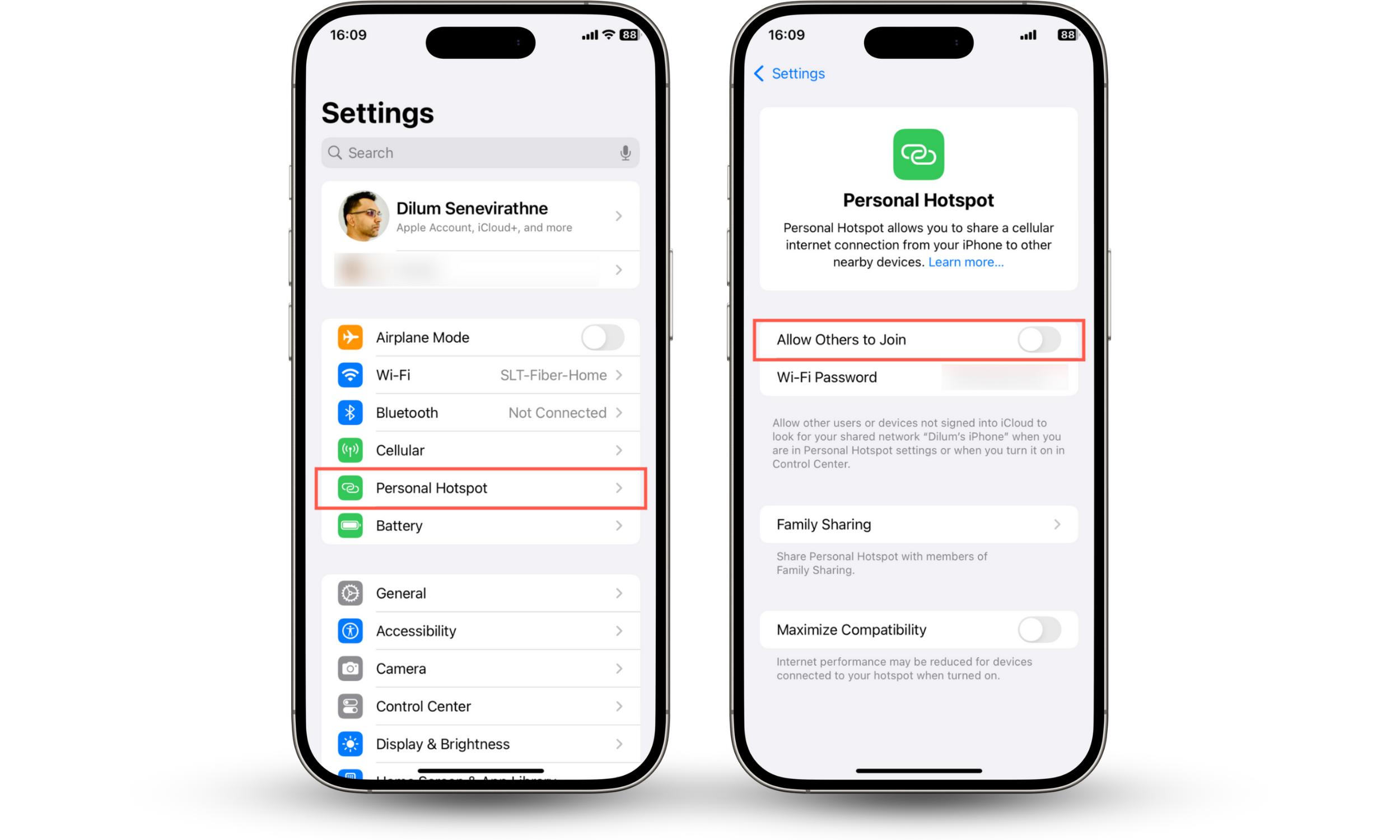
To stop broadcasting your personal hotspot:
- Open the Settings app.
- Go to Cellular > Personal Hotspot (iPhone) or Network & internet > Hotspot & tethering (Android).
- Disable the Allow Others to Join or Wi-Fi hotspot switch.
Restore your phone to its factory settings
If a hacker has gained access to your phone, they may overrun it with hacker tools, pop-ups, and malicious apps. If you don’t properly remove these items, the threat can linger. Restoring your phone to its factory setting will cleanse the device of all the gunk that hackers have left behind.
Make sure to back up your data to the cloud or a computer so that you can get back your photos, documents, and files after the reset procedure.
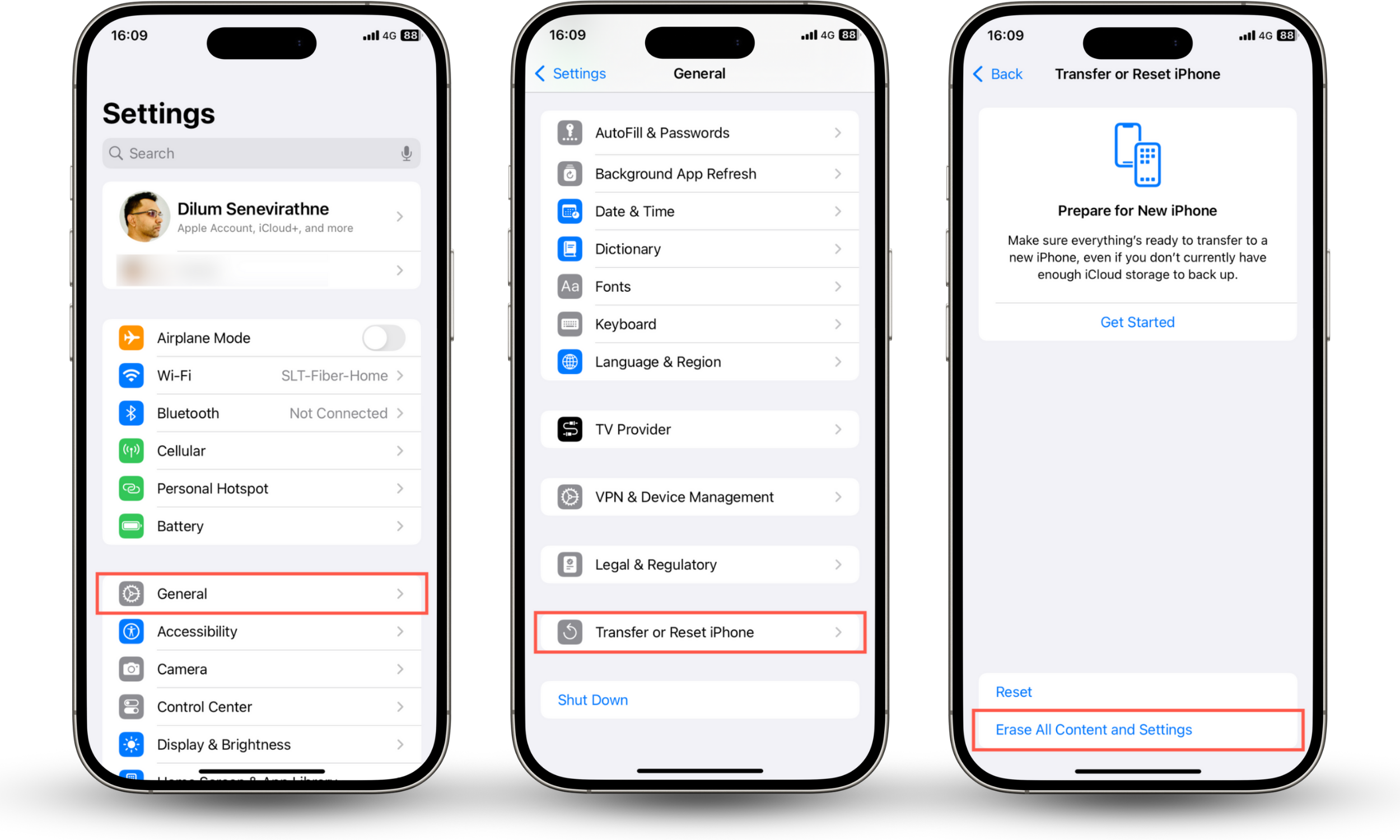
To restore your phone to factory settings:
- Open the Settings app.
- Go to General > Transfer or Reset iPhone (iPhone) or System > Reset options (Android).
- Tap the Erase All Content and Settings or Erase all data (factory reset) option.
Conclusion
Though technically your phone can be hacked when it is turned off, it’s rare. Newer iPhones are vulnerable via their Bluetooth chip. But hackers need to first hack and jailbreak the device before they can gain access and exploit the Bluetooth chip.
But whether it’s on or off, your phone is vulnerable to a number of threats. The best weapon against hackers is prevention. Clario Anti Spy’s Hidden app scan helps you spot spyware and other malicious apps that could be secretly running on your device. You can also use Device system check to see if your phone has been tampered with or jailbroken, which is often how hackers gain deeper control.
Together, they make it harder for hackers to access your phone and give you more confidence in its security.


