Table of contents
- Can someone access my Android remotely?
- How to detect remote access apps on Android
- 1. Strange device behavior
- 2. Problems with performance
- 3. Security notices
- 4. Unusual apps and activity
- How to block remote access applications on Android devices
- 1. Remove suspicious programs
- 2. Disable call forwarding
- 3. Enable multi-factor authentication
- 4. Install security software
- 5. Review your accounts
- 6. Update your passwords
- 7. Update your phone's operating system
- 8. Complete factory reset
- 9. Avoid jailbreaking or rooting your phone
- 10. Use security networks
- 11. Turn off Bluetooth when not in use
- 12. Avoid logging into accounts from unrecognized devices
- Conclusion
Can someone access my Android remotely?
Yes, someone can access your Android device remotely—but they’ll need to install malicious software on your Android first. This software, known as remote access tools (RATs), can give hackers control over your smartphone over the internet. If you’ve fallen victim to a phishing scam or a cybercriminal has gained access to your phone, they may have infected it. You can read more about how to stop remote access to your phone in our detailed guide.
How to detect remote access apps on Android
To detect remote access on Android apps, you need to learn how to detect spyware on Android phones. Keep your eye out for unusual behavior like battery drain or data usage. Check app permissions, review installed apps, and use reputable anti-spyware software to scan your device for suspicious activities.
Here’s the list of signs your phone will exhibit if there is a remote access app on your Android device:
1. Strange device behavior
If your device starts doing things on its own, like randomly opening apps, navigating through settings, or sending messages, it could be a sign of remote access. These behaviors suggest that an unauthorized user is controlling your device remotely, collecting your personal information, and sending it back to their servers.
2. Problems with performance
Remote access apps run continuously in the background, draining your device’s resources significantly. This can cause noticeable slowdowns, frequent app crashes, and increased battery use. If your device suddenly starts underperforming (and there’s no clear reason why), you may have fallen victim to a remote access hack.
3. Security notices
Android’s security features might alert you if they detect suspicious activity or apps trying to access sensitive permissions without your consent. Remote access tools attempting to access your camera, microphone, or contacts will prompt these warnings, encouraging you to take action and secure your device.
If you’re worried about someone remotely accessing your camera, find out how to know if someone is watching you through your phone camera.
4. Unusual apps and activity
If you notice apps that you don’t remember downloading, a hacker may have installed malicious software (like malware, spyware, or adware) on your device. If one of these apps is showing strange behavior, like accessing data that it shouldn’t need, the hacker might be using it as a remote access tool to control your device from afar.
How to block remote access applications on Android devices
To block remote access apps on Android devices, start by reviewing all installed apps and removing any suspicious ones, especially those that could be controlling your device remotely. Disable unwanted permissions and use security software to detect and block potential threats actively. Regularly update your device's operating system and apps to ensure security patches protect against vulnerabilities.
Here’s how to block remote access apps on your Android:
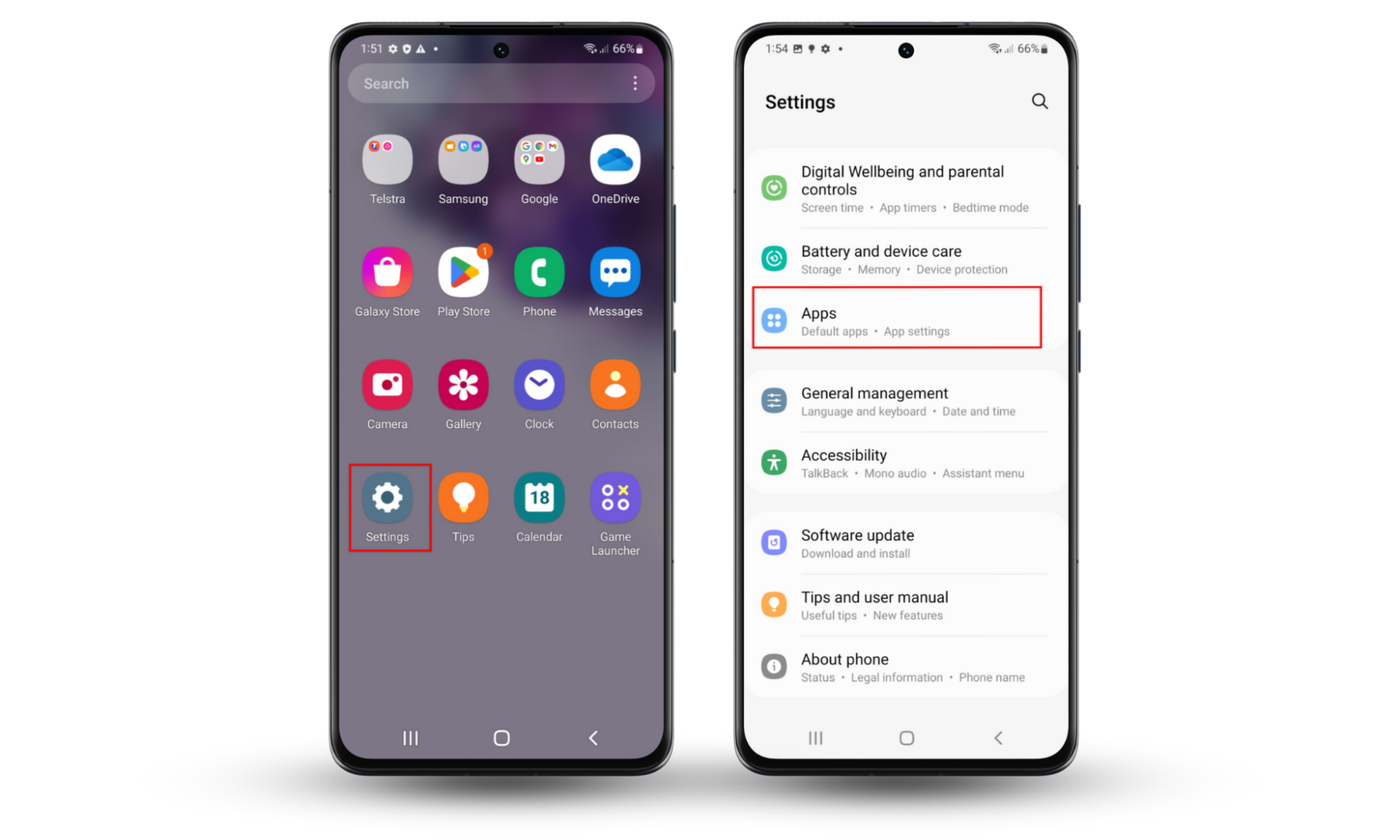
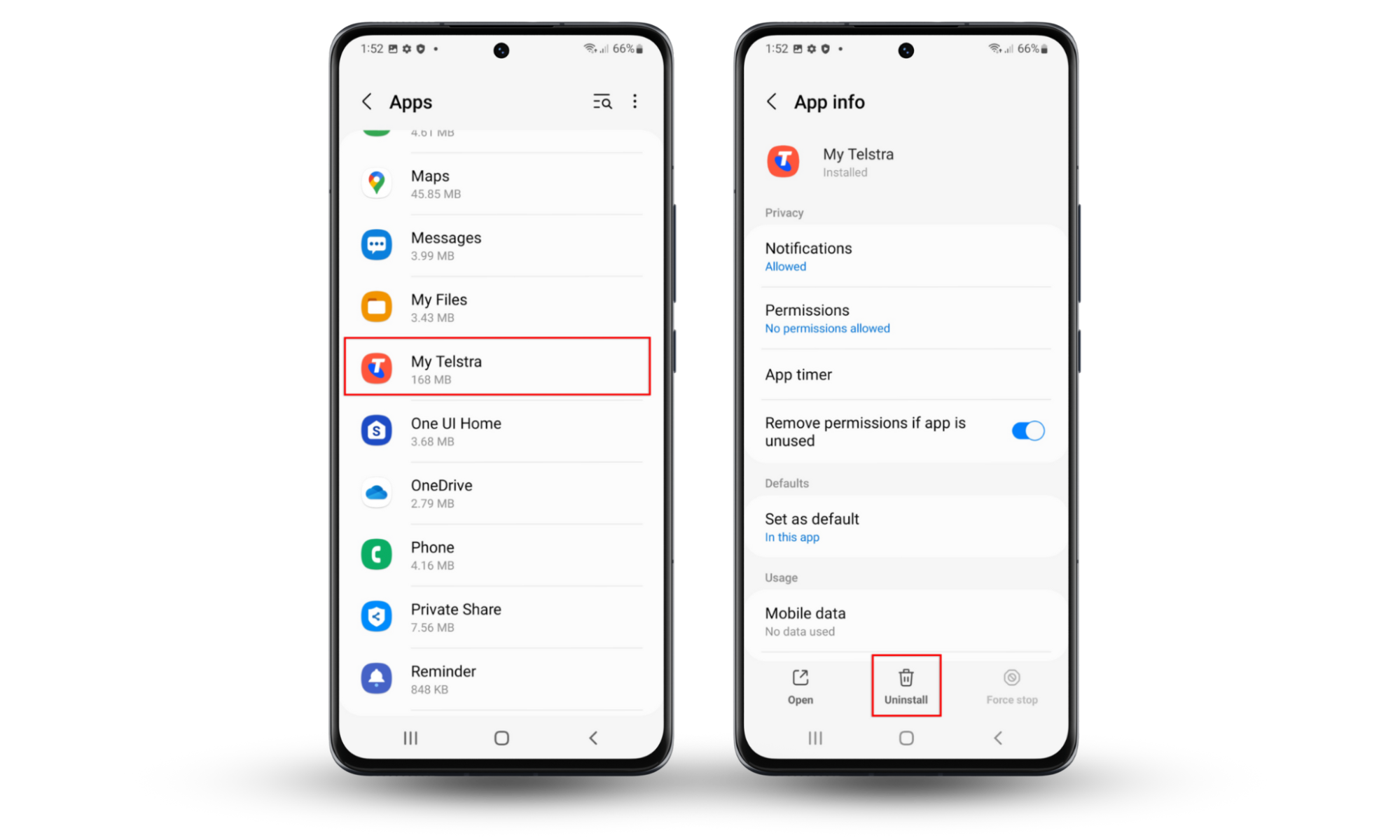
1. Remove suspicious programs
Scan your device for suspicious applications and remove any you don’t remember installing:
- Open Settings and navigate to Apps.
- Browse through the list of apps and select any that flag your suspicions.
- Press Uninstall to remove them.
2. Disable call forwarding
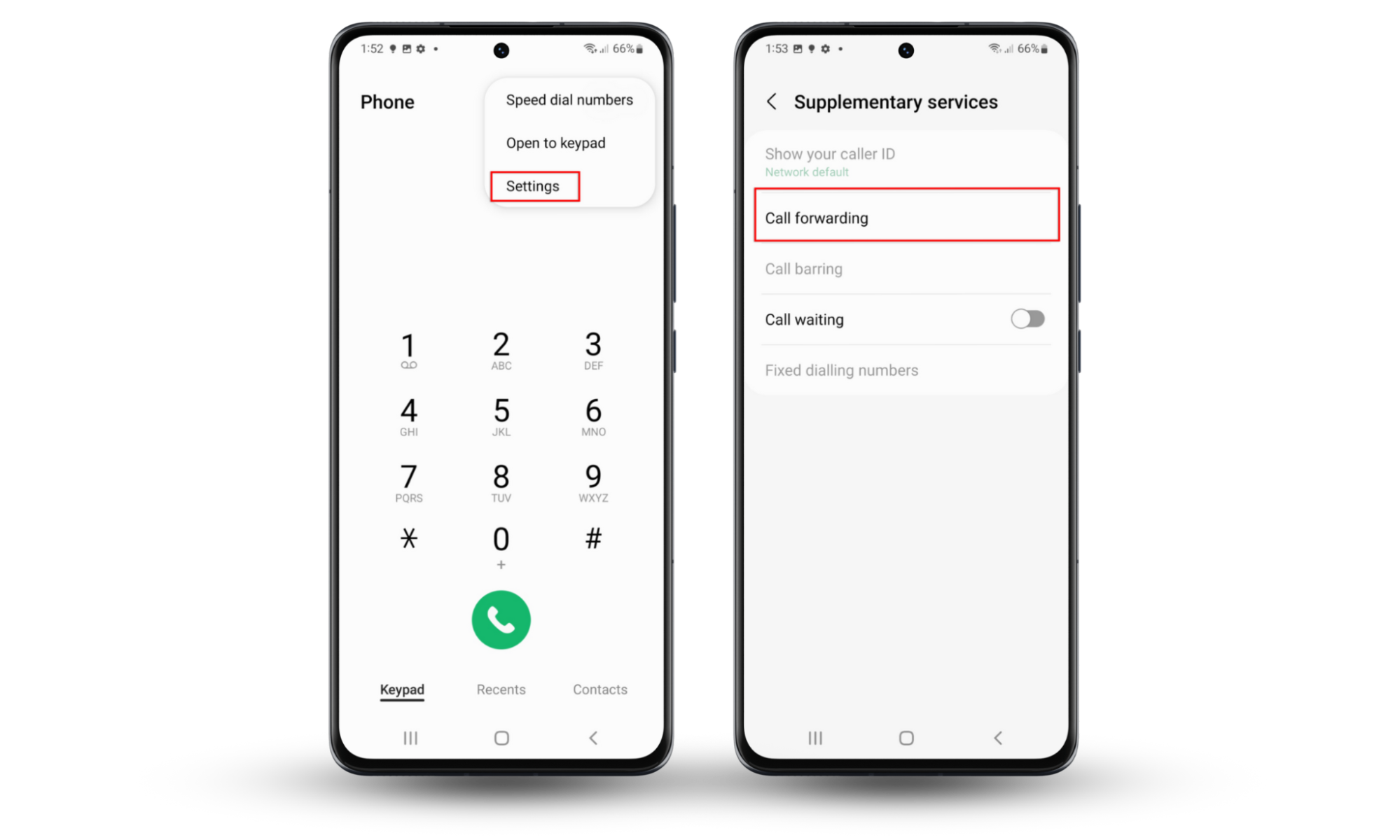
Some remote access and spyware apps will enable call forwarding to track your calls or make calls on your behalf. Here’s how to disable it:
- Open the Phone app and press the menu icon at the top-right of the screen.
- Press Settings > Supplementary services.
- Tap Call forwarding and check whether it’s enabled. If it is, disable each number to ensure calls aren’t redirected without your consent.
3. Enable multi-factor authentication
Two-factor authentication (2FA) provides an extra layer of security against unauthorized access to your accounts, requiring a second step of verification. Multi-factor authentication (MFA) adds even more layers—but not all apps will have it.
The process to enable 2FA or MFA on your accounts will differ depending on the app or service. Typically, you can enable it by accessing your account settings (e.g., on Google, Dropbox, or whatever service). Find the “Security” section and locate two-factor or multi-factor authentication. Follow the instructions to enable it—you may need to install an authenticator app.
4. Install security software
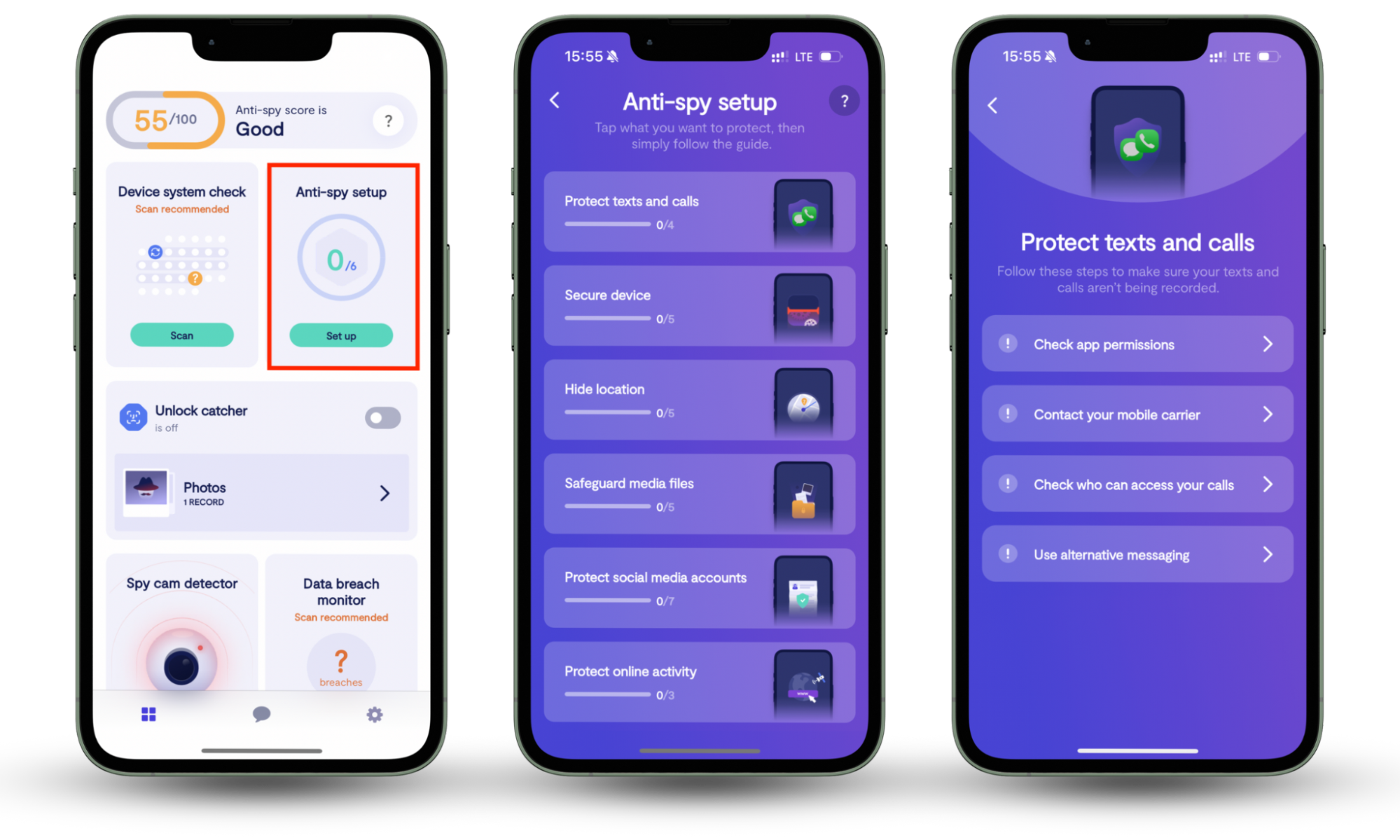
Anti-malware software like Clario Anti Spy helps protect your devices against common cyber threats like remote access apps and phishing scams. Using Clario Anti Spy’s Anti-spy setup feature, you can adjust security settings and make it harder for hackers to install remote access apps on your phone.
Here’s how to use Clario Anti Spy’s Anti-spy setup:
- Download and install Clario Anti Spy and create an account.
- Under Anti-spy setup, press Set up.
- Follow the instructions to secure your device, lock down your permissions, and scan for untrustworthy apps.
5. Review your accounts
Regularly check online accounts for unusual activity. Access each account’s security or account settings and look for evidence of unauthorized logins or changes to key settings. If possible, enable security notifications to alert you as soon as suspicious activities take place so that you can take measures to secure your accounts.
6. Update your passwords
Regularly update your passwords with strong, unique combinations of letters, numbers, and symbols. Make sure you create unique passwords for each account that are at least 12 characters long—and don’t use publicly accessible personal information like your birthday or pet’s name inside the passphrase.
Consider using a password manager to securely generate and store complex passwords, reducing the risk of breaches even further.
7. Update your phone's operating system
Operating system updates include security patches that protect your device against the latest threats. However, some Android apps aren’t trustworthy either—find out what Android apps are spyware in our guide.
To update your Android operating system:
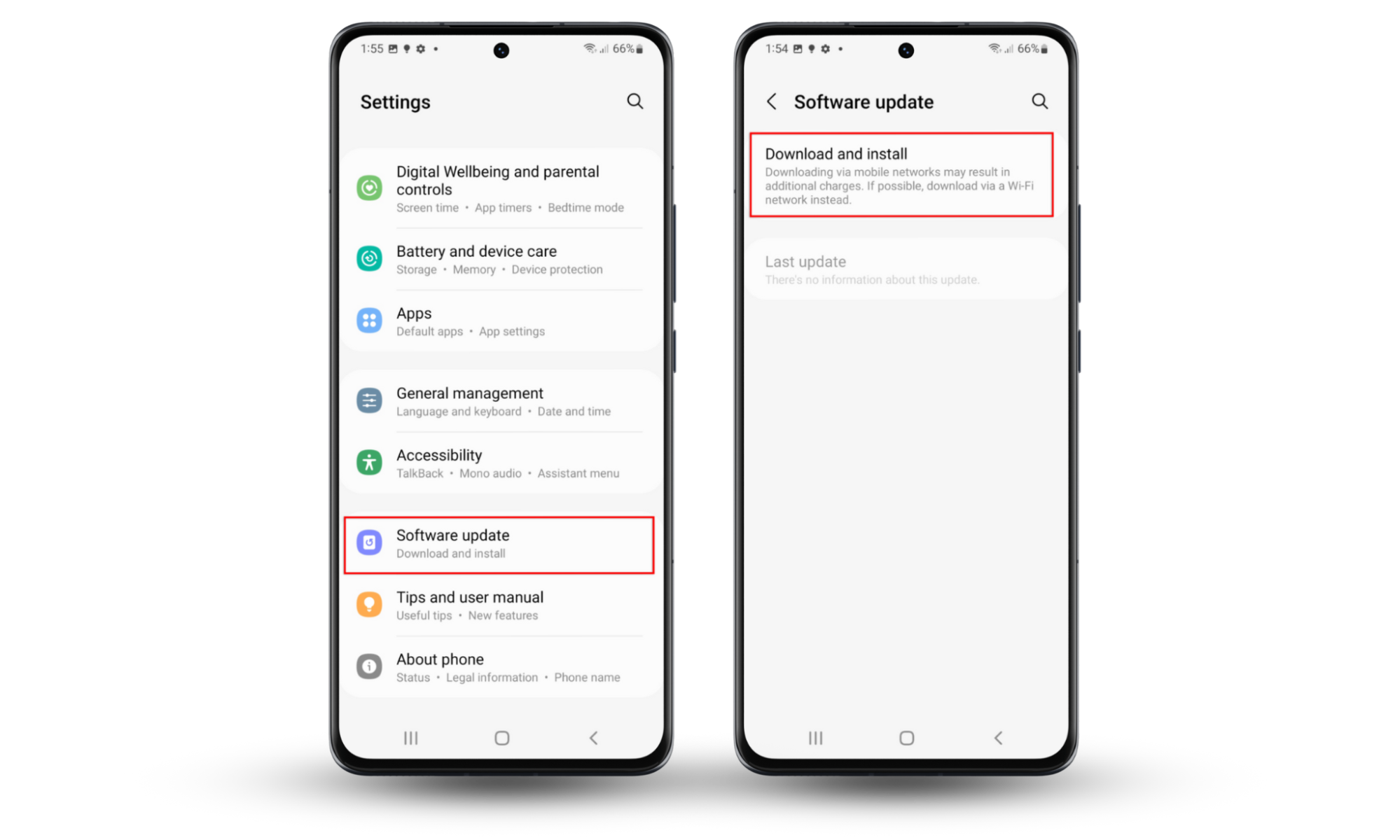
- Go to Settings and scroll down to Software update (it may be System update or Check for updates depending on your phone manufacturer and Android version).
- If an update is available, press Download and install then follow the prompts to download and install it.
8. Complete factory reset
If the steps above didn’t help you remove the remote access app, a factory reset will. Factory resets restore your device to its original factory condition, deleting all apps and creating a fresh start.
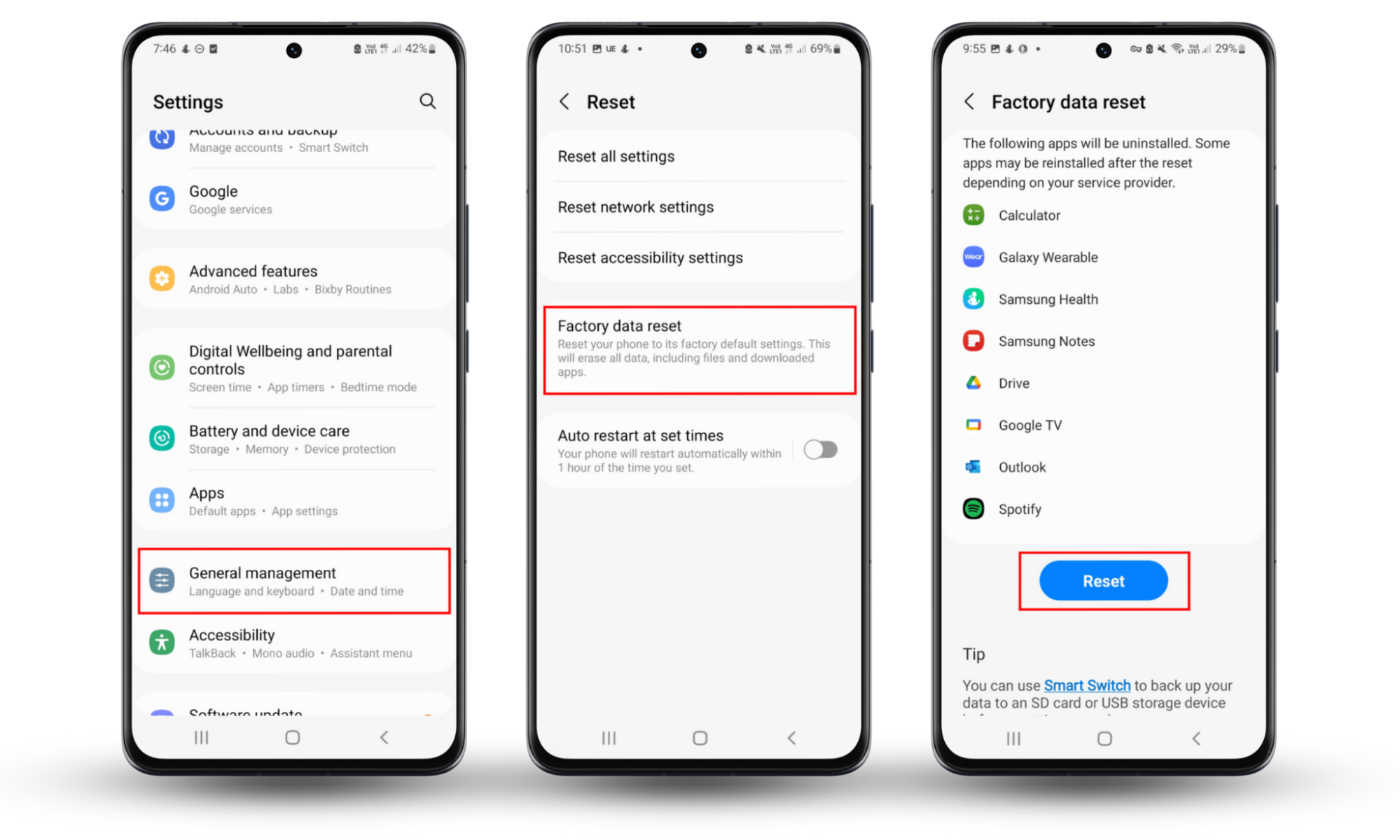
To factory reset your Android:
- Open Settings and tap General management.
- Choose Reset.
- Press Factory reset > Reset.
- Follow the on-screen instructions to complete the process. Don’t forget to back up your device before resetting, otherwise you may lose all of your personal information.
9. Avoid jailbreaking or rooting your phone
Avoid modifying your device's software to ensure it retains the security measures put in place by the manufacturer. Jailbreaking or rooting introduces vulnerabilities by removing these protections, increasing risks from malware and compromised system integrity. If you think someone has hacked your device and jailbroken it remotely, learn how to fix a hacked phone.
10. Use security networks
Only use private or secure Wi-Fi networks for internet access. When on public networks, use a virtual private network (VPN) to encrypt your data and protect your device against hackers who might exploit unsecured connections to capture sensitive information.
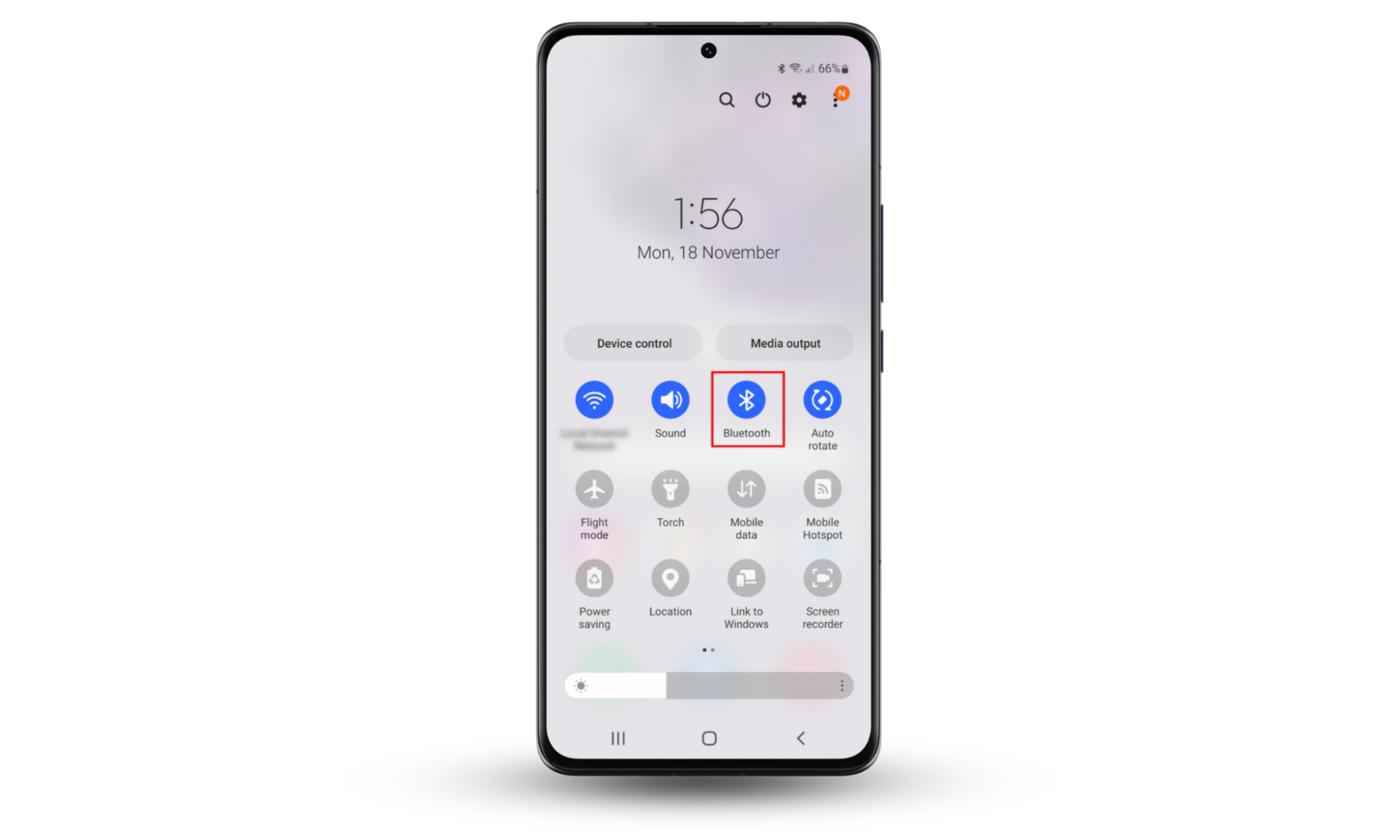
11. Turn off Bluetooth when not in use
Avoid leaving Bluetooth enabled when not in use to prevent unauthorized pairing attempts and potential data breaches from nearby devices trying to access your phone. To disable Bluetooth, drag down from the top of your screen and tap the Bluetooth icon.
12. Avoid logging into accounts from unrecognized devices
Only log in to your accounts from recognized, secure devices. If you need to use a shared or public device, use private browsing mode and log out after each session. Regularly monitor account activities and set alerts for any unfamiliar login attempts to safeguard your accounts.
Conclusion
Staying vigilant for signs of suspicious apps helps find remote access apps on Android and keep your device secure. Monitor for suspicious device behavior, regularly review your apps, and update your settings to protect your data from hackers and scammers.
For enhanced protection, use Clario Anti Spy’s Anti-spy setup to scan your device for threats and implement more secure settings. Download Clario Anti Spy today to learn more and safeguard your privacy.


