Table of contents
- What is the cloud?
- What is the cloud used for?
- 1. Backup data
- 2. Quickly share files
- 3. Recover from cloud disasters
- How does cloud security work?
- Can the сloud be hacked?
- How secure is сloud storage?
- How secure is cloud computing?
- How to protect your cloud storage
- 1. Regularly assess your data and security
- 2. Control access to data
- 3. Monitor your cloud for threats
- 4. Password protect
- 5. Enable two-factor authentication
- 6. Regularly update your cloud software
- 7. Have a data recovery strategy in place
- 8. Stay informed
- 9. Invest in a powerful cybersecurity solution
- Is the cloud secure for business?
- What is the most secure cloud storage for personal use?
- Conclusion
What is the cloud?
The cloud refers to a network of computers and servers that store and manage data and applications via the internet. Instead of storing your data on your personal computer, you upload it to a company’s secure servers and let them manage the data for you. This means you can access your data from any device and store it off-site without needing physical storage.
What is the cloud used for?
The cloud has many uses for both individual consumers and organizations. The cloud lets you:
1. Backup data
What is data backup? By backing up your data in the cloud, you reduce the risk of losing it to hardware failure, ransomware, theft, or accidental deletion. It also lets you store large amounts of data in another location, meaning you don’t have to invest in new physical storage solutions like hard drives.
2. Quickly share files
Once your data is in the cloud, it’s easily accessible from any internet connection device. You can download your files and share them with others with ease.
3. Recover from cloud disasters
Cloud disaster recovery (CDR) is a backup strategy that companies (and individuals) can use to protect their data from cyberattacks. If your primary data storage gets infected with malware or hacked by an attacker, you can easily restore it from the cloud after the threat has been dealt with.
How does cloud security work?
Cloud security uses a combination of tactics to protect data, applications, and infrastructure within the cloud environment. These include access controls, data encryption, firewalls, physical security measures, and other network security strategies.
Can the сloud be hacked?
Yes, the cloud can be hacked. However, cloud services often use advanced security measures to make it much harder for hackers to compromise data in the cloud.
While cloud hacking is fairly rare, the most common way they are compromised is by uncovering a weak or reused password.
How secure is сloud storage?
Cloud storage providers invest significant resources into building a secure cloud environment. While vulnerabilities can exist in the cloud infrastructure, it’s generally much more secure than typical at-home data storage methods.
- File backup
- End-to-end encryption
- Round-the-clock security service
- Artificial intelligence tools and automatic patching
- Cloud firewall
1. File backup
When you upload your files to a cloud storage service, they will be copied onto multiple servers in multiple locations. This is called “redundancy,” and it ensures that if any one server fails, your files will still be safe elsewhere.
2. End-to-end encryption
Data encryption means that even if a hacker gains access to your data, they won’t be able to see what it is or do anything with it. Most cloud services encrypt your data “end to end.” That is, the data is encrypted from the moment you send it to the cloud service, so hackers can never intercept an unencrypted file.
3. Round-the-clock security service
Secure cloud storage services will protect your data with a 24/7 security service. They will monitor for signs of breaches, cyber threats, and any potential flaws in the cloud infrastructure. In the worst case, they’ll let you know what to do if a data breach occurs.
4. Artificial intelligence tools and automatic patching
New AI-powered security tools are being released every year. These automatically scan, monitor, and guard the cloud environment from cyberattacks. They can also identify vulnerabilities like missing or out-of-date software and apply updates as required.
5. Cloud firewall
Like a traditional firewall that secures your home network, a cloud firewall acts as a barrier that protects your cloud-based data from unauthorized access. By monitoring and controlling all incoming and outgoing network traffic, a cloud firewall can block malicious traffic, prevent access attempts, and ensure that your data remains secure.
How secure is cloud computing?
Cloud computing is when apps and programs are hosted in a cloud service, enabling individuals and companies to use those apps remotely without needing to install them on local devices. Most cloud services provide stringent security measures that make it far more secure than at-home or on-premise computing.
How to protect your cloud storage
If you’re investing in a cloud storage solution, the most important thing you can do is choose a trusted and reputable service provider. Ensure they have strong security certifications and a good track record for consumer data protection.
Other than that, here’s what you should do to make your cloud storage more secure:
- Regularly assess your data and security
- Control access to data
- Monitor your cloud for threats
- Password protect
- Enable two-factor authentication
- Regularly update your cloud software
- Have a data recovery strategy in place
- Stay informed
1. Regularly assess your data and security
Conduct regular cybersecurity assessments to make sure that your cloud environment is secure and up to date. For example, you should scan for vulnerabilities, conduct penetration testing, and review your security configurations to identify potential weaknesses.
2. Control access to data
If you let everyone have access to every file and folder on the cloud, it’ll be insecure. Instead, assign specific access rights and permissions to users based on their needs and roles. This will reduce the risk of exposing data to the wrong people.
3. Monitor your cloud for threats
Invest in a cloud security solution providing 24/7 threat monitoring with a powerful antivirus, strong cloud firewall, and real-time protection. Proper logging and monitoring tools can also help you identify suspicious or insecure activities in the cloud.
4. Password protect
Whether it’s just you or an entire organization, you need strong, unique passwords to protect your data. Without passwords, anyone can access your sensitive files. Make sure to use a new password that’s at least twelve characters long and made up of letters, numbers, and symbols.
5. Enable two-factor authentication
You should use robust authentication methods to make sure that only authorized people can access your data. Set up two-factor authentication (2FA) or multi-factor authentication (MFA) to add another layer of protection to your data.
6. Regularly update your cloud software
Cloud service providers (CSPs) constantly release new updates that protect the cloud from emerging cyber threats and ensure the cloud is secure.
Your cloud will quickly become vulnerable to attack if you fail to update it, so make sure to stay on top of all new security patches. Likewise, make sure to keep all of the apps and software in your cloud environment updated.
7. Have a data recovery strategy in place
Make sure your cloud service provider regularly backs up your data in multiple locations to ensure data redundancy. Likewise, back up your data on multiple hard drives if possible so that if the entire cloud service goes down, you still have access to your data.
8. Stay informed
Keep updated on the latest cloud security threats and best practices. Actively engage with industry security communities and subscribe to security alerts from your cloud provider to make sure you’re using the recommended security measures.
9. Invest in a powerful cybersecurity solution
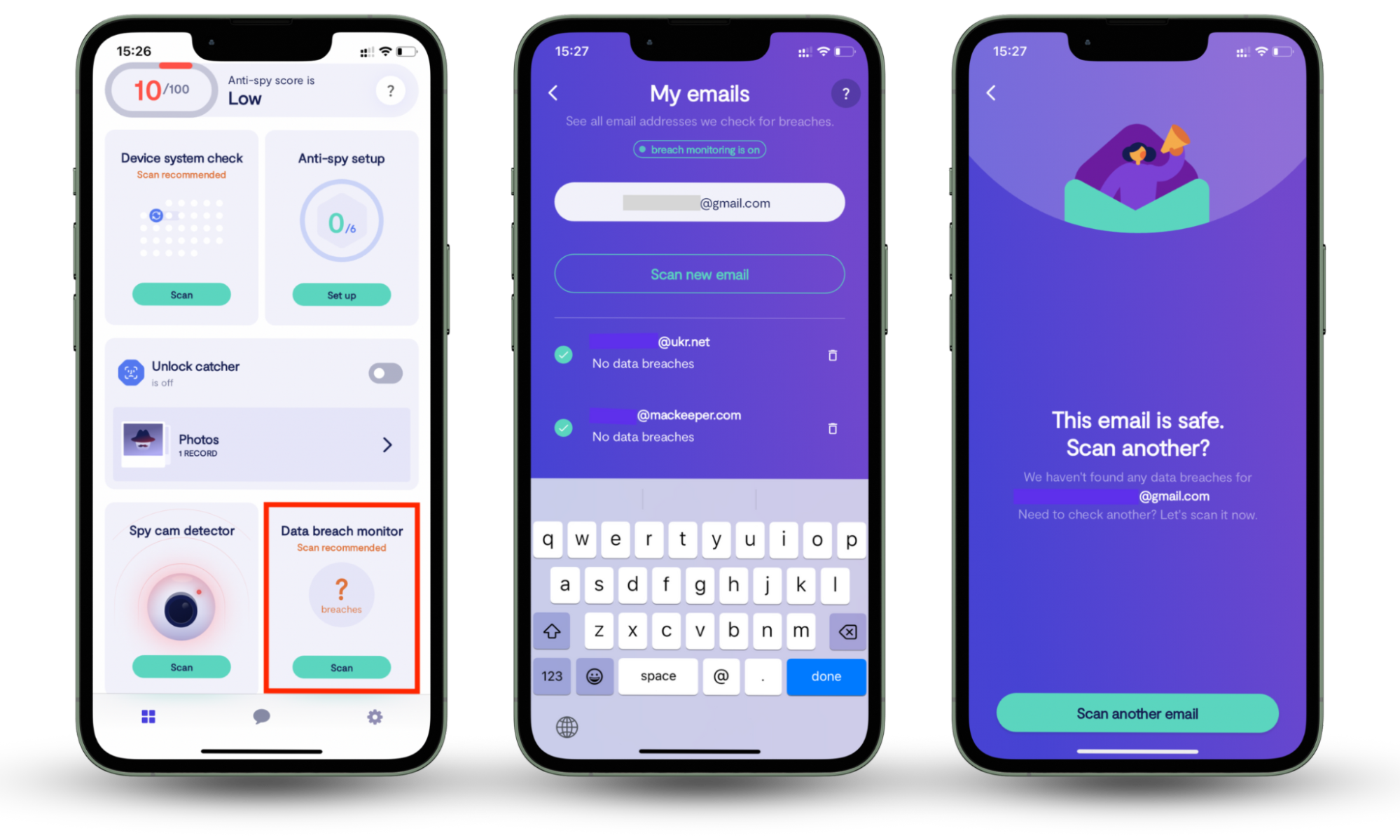
Cybersecurity experts designed Clario Anti Spy to protect your devices and data from digital spying and stalking. With a data breach monitor and device check tools, you can find out if someone is spying on your phone or computer and protect your devices from unauthorized access.
Here’s how to use Clario Anti Spy’s Data breach monitor on your phone:
- Download Clario Anti Spy, get a subscription, and create an account.
- Open the app and go to Data breach monitor.
- Enter your cloud email and click Scan to check if it has been exposed in any known breaches.
- Once the scan is done, you’ll get your results with steps to protect your account (if affected).
Is the cloud secure for business?
Cloud storage and computing are often much more secure for business, offering greater protection against cyberattacks and data loss than other methods.
What is the most secure cloud storage for personal use?
Some of the most secure cloud storage solutions for personal use include Google Drive, OneDrive, iCloud, Dropbox, pCloud, Mega, Sync, and iDrive.
Conclusion
With data encryption, access controls, and monitoring systems in place, the cloud can be very secure. However, it’s important to note that no system is completely immune to security risks. For this reason, it’s crucial to stay on top of your cloud security measures to ensure the cloud is safe. Always check the emails registered to your cloud storage. They might be compromised. Scan now with Clario Anti Spy’s Data breach monitor.


