Table of contents
- Can the government spy on your computer
- Can the government spy on you through your computer camera
- How is the government spying on you
- Social media and AI
- Facial recognition
- Signs that the government is watching you through your computer
- What does the government do with the metadata it has collected
- What can you do to avoid being spied on through your computer
- Conclusion
Can the government spy on your computer
Yes, governments have the capability and generally have the legal authority to spy on your computer. Computer and network surveillance enables governments to manage societal order, target and monitor threats, and investigate crimes. On the other hand, the technology can potentially be used for mass societal surveillance.
In the USA, controversial laws like FISA and the USA PATRIOT ACT allow for the collection of computer data—but these laws require the government to meet certain criteria beforehand. Outside of these laws, the US has been known to collect large amounts of metadata (“data about data”) and use automated systems to monitor the social media of citizens.
Can the government spy on you through your computer camera
Yes, the government can technically spy on you through your computer camera or webcam. Though, generally, this would require exploiting security vulnerabilities in your device’s software or operating system, there have been instances where the government remotely accessed and activated computer cameras.
In 2013, the now infamous former NSA contractor Edward Snowden leaked documents documenting extensive surveillance programs conducted by intelligence agencies like the NSA, CIA, and the FBI. Besides revealing how these programs collected and analyzed the electronic data of citizens, the leak highlighted the potential for governments to remotely activate cameras and microphones.
The government can spy on you through your computer camera, but so can hackers and other cybercriminals. This makes it all the more crucial to learn how to know if your laptop camera is hacked or how to know if someone is watching you through your phone camera.
How is the government spying on you
The government can spy on your computer or other devices using an array of tools and techniques, including:
- Mass surveillance programs: By collecting and analyzing large swathes of data from various sources, like websites, emails, and social media, the government can form profiles of private citizens from their internet activity and spy on them.
- Legal avenues: Though controversial, governments can enact legislation that allows them to curb the privacy rights of their citizens and openly spy on their citizens. They can also obtain legal warrants and orders to target individuals.
- Malware and hacking: The government can watch us through laptops and other devices, using the same techniques as cybercriminals. In some instances, hackers actually advise governments on how to spy on you.
- ISPs: Governments can partner up with your ISP (internet service provider) to monitor and analyze web traffic. They may even ask your ISP for access to the network infrastructure for surveillance purposes.
- Data requests: Governments have been known to ask big tech companies and other businesses, like Facebook and Google, for user info, communications, and other data. Though some companies may refuse the requests, they may be legally obligated to comply.
- Backdoors: Some governments pressure technology companies to create backdoors in their software and programs, which would allow government agencies to freely access devices or systems. One example is the UK’s Investigatory Powers Act.
Social media and AI
That’s right, the government might be stalking your social media profiles using AI. Generally, governments are allowed to collect information from public places, including social media. So, government agencies monitor and gather social media-related data about individuals, groups, events, and trends.
Analyzing large amounts of social media data is a tedious process. But with the help of AI, governments are getting better at it. Governments can use AI scraping to comb through large data sets to make faster connections and inferences from them.
Here’s what governments can do with your social media info using AI:
- Map out your relationships
- Interpret the meaning and attitude of your posts
- Analyze your past and present locations to predict your future movements
- Enhance facial recognition technology (more on that right below)
- Gather information about your personal views and identity, like religion, sexual orientation, and political views.
Facial recognition
With facial recognition technology, the government can collect and create a database of faces for surveillance, law enforcement, and border protection. But where do they get the faces? Along with government-issued ID photos and border control points, governments can fill their facial recognition database from surveillance and social media profile images.
Signs that the government is watching you through your computer
Think the government is watching you? Probably not. Unless you’re engaged in explicitly illegal activity or a threat to national security, the government is not likely to be watching you. But that doesn’t mean the CIA isn’t collecting large amounts of metadata for mass surveillance—including yours.
But just to be safe, it’s important to recognize the signs of potential government spying. Like with general cyber spying, it could be difficult to recognize when you’re being watched. So don’t jump to conclusions, but at the same time: stay vigilant and protect yourself.
Here are possible signs the government is watching you through your computer:
- Unusual surveillance activity: Are you seeing unmarked vehicles or individuals outside your home, workplace, or daily activities? These could be federal agents monitoring your activities.
- Unusual phone activity: Are you hearing distinct noises or echoes while on the phone? Someone could be listening in on your calls.
- Unexpected invites: Are you getting invitations or requests to meet with people claiming to be government agents, law enforcement agencies, or intelligence officers? First, ask to see their identification. Next, if you can, get a lawyer before talking to anybody.
- Technical issues: Are your device batteries draining quicker than usual? Are you experiencing strange technical issues, or is your data draining rapidly? These are all signs of device hacking and/or remote access.
- Online monitoring: Are your online accounts being accessed from unfamiliar locations or devices? How about notifications about failed login attempts? Someone could be trying to get into your accounts.
- Friends and family are questioned: Are your friends and family informing you that they’ve been questioned by people claiming to be government agents or law enforcement? Agencies might be trying to influence your contacts or get more information on you.
Again, don’t get too spooked. Even if you are noticing some of these signs, you’re more likely being spied on by cybercriminals than the government. To stay clear of snoops, learn how to protect yourself from cyberstalking.
What does the government do with the metadata it has collected
Through bulk data collection programs, the government can acquire, analyze, and piece together large amounts of metadata to learn about patterns of communication and connections between individuals. In essence, it’s a way for governments to spy on us without being explicit about it—though in some societies, there are oversites and regulations that limit access to metadata
Individual metadata may not reveal much about you. Considered the “data about data,” metadata are seemingly insignificant bits of information found within emails, photos, websites, documents, phone calls, and social media posts. But with enough metadata on an individual, valuable insights into their communications and relationships emerge—all without revealing the actual content of the source data.
Here’s the kind of information metadata can reveal about you:
- The places you visit
- Your hobbies and interests
- Your relationships with others
- Who you call and how often
- How you communicate with others
What can you do to avoid being spied on through your computer
If you want to avoid being spied on, you’ll need to reduce attack vectors. The more cybersecurity vulnerabilities you have, the bigger the target you are. Here’s how to avoid being spied on through your computer:
- Watch what you post on social media: Sharing too much on social media gives spies more information to work with. Especially with sophisticated programs like AI scraping. To keep a low profile, limit what kind of personal information you publicize online.
- Use a VPN: A VPN (virtual private network) will fully encrypt all your network traffic to help you evade snoops and location-based restrictions. Stay away from free products, a premium VPN is much more reliable.
- Use a password manager: Think about all your profiles, accounts, and devices that are secured with passwords. Are you sure your password is strong enough to stop a motivated hacker or spy? Invent complex passwords and use a password manager to keep track of them. Also, use two-factor authentication when you can.
- Cover camera lenses: Place a piece of tape or something else to obscure your computer camera or webcam. Though not exactly the most sophisticated solution, it’s one of the most effective ways to prevent a remotely accessed camera from recording you.
- Avoid suspicious links, sites, and apps: Untrustworthy links, sites, and apps may contain malware or remote access tools (RATs), which can give spies unauthorized access to your devices. Always stick with verified technology and services.
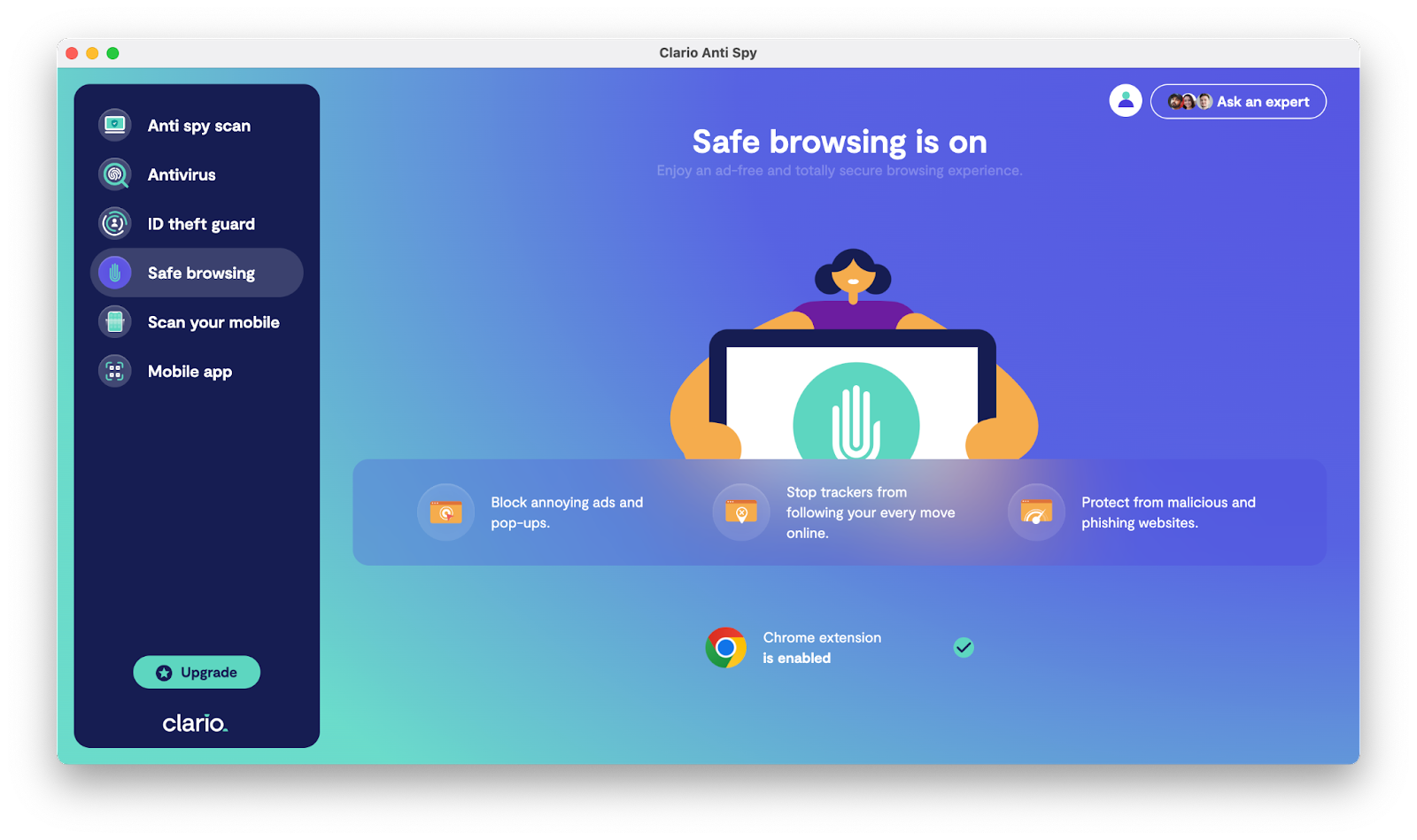
Clario AntiSpy contains a safe browsing feature that’s specially designed to stop spying and other threats. This multi-function feature will block pesky advertisements and phishing attacks or stop advertisers and other data collectors from tracking your online behavior and accessing your personal data.
Here’s how to use Clario AntiSpy safe browsing feature:
- Download Clario AntiSpy and get a subscription to create an account
- On the dashboard, choose Safe browsing
- Enable the Clario AntiSpy extension for Chrome and Safari
- Enjoy the four pillars of Clario’s Safe browsing: Web security, Anti-malware, Ad blocker, and Anti-tracking.
Conclusion
Is the government spying on us through laptops and other devices? It depends. As an individual: probably not. As part of a mass surveillance program: probably yes. Either way, hackers and other cybercriminals are more likely to be your spying culprits. Protect yourself with a dedicated anti-spying app, like Clario AntiSpy.
Our comprehensive cybersecurity tool contains a data breach monitor to stop spies in real time, plus a safe-browsing feature to stop data collectors from leeching on your online activity. Along with these detection tools, an anti-spy scan will quickly analyze your device for all kinds of spying threats. Keep spies and other threats in the dark with Clario AntiSpy.


