Table of contents
- What is phishing in a nutshell?
- What are the phishing techniques?
- Spear phishing
- Clone phishing
- Whaling
- Pop-up phishing
- Vishing
- Smishing
- Search engine phishing
- Pharming or DNS poisoning
- Man-in-the-middle
- Business Email Compromise (BEC)
- How to protect yourself from phishing attacks
- What to do if you suspect a phishing attack
- How to report phishing scams
- How to prevent phishing attacks
- How to avoid phishing attacks
What is phishing in a nutshell?
Phishing is a criminal activity used by scammers to obtain private information such as account login details or credit card numbers through malicious emails, calls, or text messages. The term itself was coined around 1995 when hackers started stealing America Online (AOL) account details en masse by luring users into disclosing their credentials, just like fishers do. Hackers traditionally substitute f with ph, so ‘fishing’ became ‘phishing’.
The way phishers behave is predictable. The information they usually try to get out of you includes:
- Full name
- Full address
- Date of birth
- Bank account number
- Credit card number and security code
- Social Security Number
- Online account passwords
- Answers to any security questions like your mother’s maiden name
For example, you might receive an email that allegedly comes from your bank or credit organization, stating there are issues with your account that need your immediate attention. Or else…
A common phishing email might look like this:
From: Customer Support Team csupt@yourtrustedbank.com Topic: Your bank account is on hold pending further verification!
Dear Customer,
We have noted some suspicious activity with your account within the last 24 hours and have put all transactions on hold until further approval.
Please log in at your earliest convenience to resolve the matter using this account recovery link. You will not be able to access the account until the restrictions are removed.
Looking forward to your prompt action,
Your Customer Support Team |
The telltale signs that indicate this spoof email is, in fact, fake mail include:
- Alerting topic
- Spoofed email headers to make you trust this email came from your bank
- General greeting, not by your name or surname
- Vague explanations of having some issues without any details
- Providing a link you must click
- Creating a sense of urgency to make you act without thinking
While you cannot entirely avoid phishing emails, the best course of action when dealing with them is to stop and think — the one thing phishers don’t want you to do.
- First of all, your bank, credit company, or any other law-abiding entity will never ask for your Social Security Number, card PIN, or CVV2 code via email, phone, or text message.
- Secondly, you can easily check if everything is okay by simply logging into your account the way you usually do it — via the app or web version directly from the browser, not by following the link they sent. Should there be any actual issues, you will be informed once you’ve logged in.
- Lastly, such emails often contain grammatical mistakes, typos, or weird wording as they are mostly devised and sent by people with a bad command of English.
The moment you hop online, your privacy is at risk from all directions—phishing attacks, data collection by websites and apps, social media companies mining your information … you name it. But that's where Clario Anti-Spy can help. This anti-spyware tool not only checks for hidden jailbreaks, spyware, and data breaches but also features an Anti-spy setup to configure your phone, online accounts, and social media for maximum privacy.
Here's how to run an Anti-spy setup with Clario Anti Spy:
- Download Clario Anti-Spy and subscribe to create an account.
- Tap Set up under Anti-spy setup.
- Select Protect online activity and follow the suggestions to enhance your online privacy.
- Repeat the process for all other categories to increase overall device privacy.
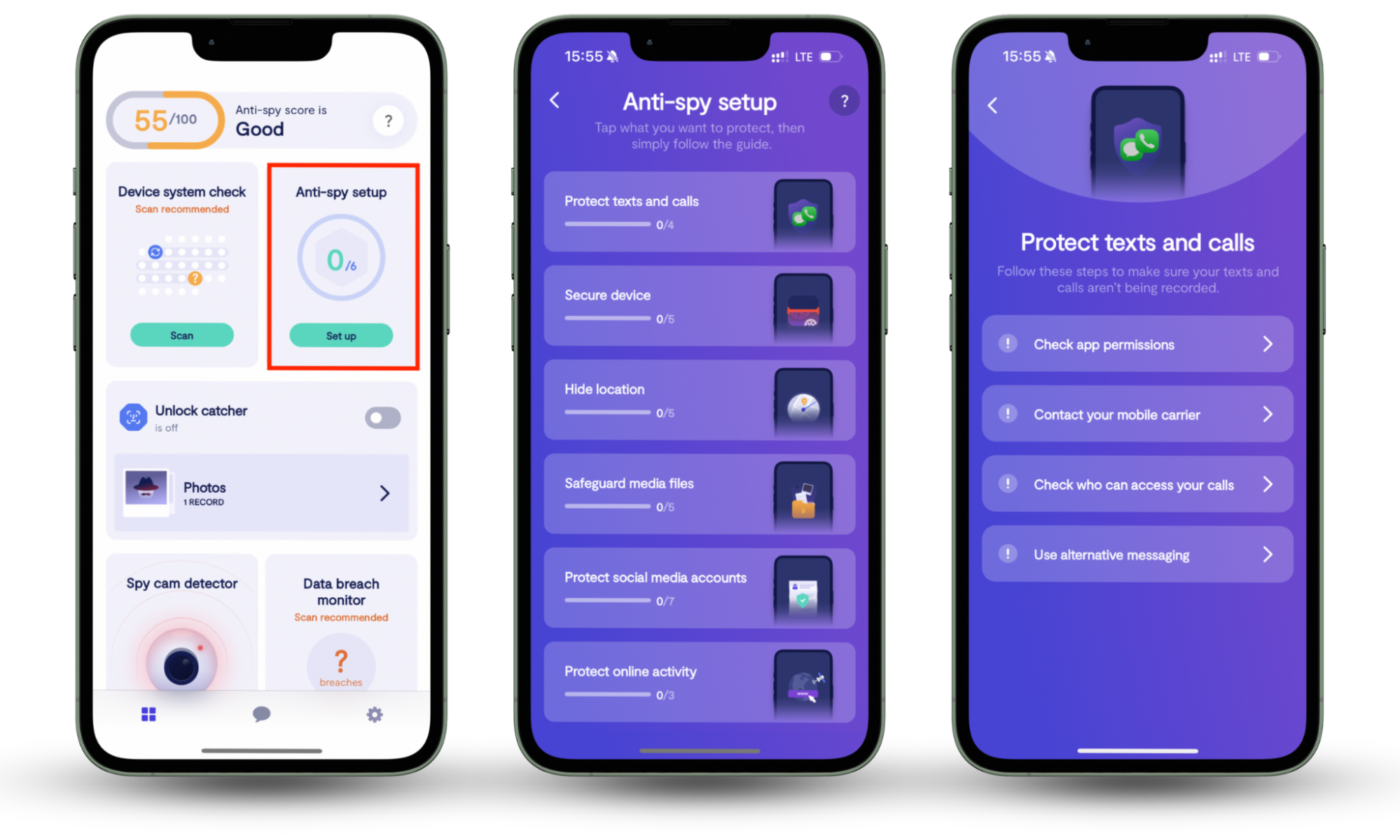
Clario Anti Spy also offers 24/7 tech support. Unsure if an email you received is a scam? Or have any other security questions? Simply tap the Messages icon to chat with a security expert anytime.
What are the phishing techniques?
Now, let’s now take a closer look at the ten most widespread types of phishing:
Spear phishing
Spear phishing targets people with access to important corporate information. For example, such email scams might appear to come from one of your work peers or superiors who need access to certain data. Unlike phishing, which aims at broad audiences, spear phishing focuses on a particular type of target.
Other times, scammers use this technique to target a demographic more prone to being susceptible to phishing than others. For example, American senior citizens are statistically more vulnerable to phishing attacks, according to a 2019 study by the Aspen Institute's Tech Policy Hub.
Clone phishing
Clone phishing often happens when criminals duplicate an email originally sent by a bank. Crooks add a fraudulent attachment or link into a legitimate email and send it as a reminder to a list of bank customers to trick them into revealing sensitive information.
Whaling
In the phishing world, whales refer to those people in the big league. They can be C-level executives like CEOs or CFOs who earn more than your average professional and have access to company funds. Getting a hold of their details means huge success for phishers and enormous losses for companies.
Pop-up phishing
This is also known as in-session phishing. People are usually browsing or visiting a website when a pop-up appears, asking them to complete a survey or perform a similar action. Once they click the pop-up, their device gets infected.
Alternatively, the pop-up might inform the victim that the website has experienced a virus attack from their computer, and they must install specific antivirus software immediately. And when the victims install it, they actually get malware or adware into their computer.
Vishing
Vishing is a combination of the words ‘voice’ and ‘phishing’ and occurs when criminals call you to request private information. They often sound professional by pretending to be representatives from banks or insurance companies so that you feel at ease sharing your personal details with them.
Smishing
Using SMS (Short Message Service) or text messages to phish is called smishing. In smishing, look out for misspellings or typos. Unprofessional-sounding messages are usually a red flag too.
Search engine phishing
Fraudsters publish fake websites that resemble authentic ones and are intended to collect your login details. They promote such websites using Google Ads to highlight them in search engine results for popular searches.
Pharming or DNS poisoning
Pharming reroutes legitimate traffic to a spoofed web page to gather sensitive personal information using the internet DNS (Domain Name System).
Man-in-the-middle
The most widespread of such types of attack is setting up free Wi-Fi networks in airports, railway stations, hospitals, coffee shops, etc. — in places where people might have to make online purchases quickly.
Once you connect to such a network and make a purchase, your credit card details are captured.
Business Email Compromise (BEC)
This type of spear phishing scam is the most damaging of all. It usually comes from alleged “company executives” and urges employees to promptly make small transactions like purchasing gift cards. According to the FBI, BEC accounted for nearly half of the cybercrime-based financial losses in 2019.
There are multiple variations of these phishing techniques, but they fall under one of the categories listed above.
How to protect yourself from phishing attacks
The bad news is that we can never be completely safe from phishing. But the good news is that there are plenty of ways you can protect your email and personal information.
Here are a few practical pieces of advice to help you secure your email from phishing attacks:
- Use special cybersecurity software to keep your data safe. Having effective security software in place gives you an extra layer of protection and peace of mind.
- Enable multi-factor authentication (or 2FA) for your online accounts. With 2FA, along with typing in the password, you will also be prompted to enter a security code sent to your phone. It’s a longer process, but it also makes your account much harder to hack.
- Use a password manager. With these apps, you can log in without keeping a physical copy of your passwords. Services like LastPass or KeePass securely keep track of all your data.
- Browse securely with a VPN. Using a VPN (Virtual Private Network) allows you to hide your location or transaction details by encrypting any information you send. It’s like sending a coded message to the internet, and only the intended recipient has the key to break the code and access it. Thanks to this, phishers and other hackers can’t spy on your online activities.
- Make sure you install the latest updates to your OS/browser. We know updates usually come when you don’t have the time to install them. But they are made for a reason: the software provider may have found vulnerabilities in their system and created fixes to improve security.
These points might seem blatantly obvious, but let’s be honest: how often do you use a password manager or VPN when browsing Instagram over your favorite coffee shop’s free Wi-Fi? That’s what we thought. Are you sure your device isn’t infected yet?
What to do if you suspect a phishing attack
What if you accidentally clicked on a malicious link? Or if the phisher was so good, they fooled you despite all our warnings?
Fret not, here are some steps you can take to ensure no further damage is done:
- Immediately disconnect your device from the internet. This is applicable if you’ve just clicked on a malicious link and are redirected to a dubious website.
- Change the passwords of all your online accounts.
- If you think your credit card has been caught up in this phishing attack, call your bank and cancel the card immediately.
- If your account was taken over, make sure you inform friends and colleagues about the breach.
- Watch out for the warning signs of identity theft. Set up a fraud alert with your bank or any relevant government agencies.
- Back your files up and reformat your device if needed.
- Scan your device for viruses and malware.
Dealing with phishing scams is good and all — but what about fighting back? Once you get rid of the infection, you might ask yourself, how do I report a suspicious email?
How to report phishing scams
When you have identified an email as phishing, it’s time for payback. There are ways you can take action to keep yourself more secure:
- Forward the email to the Anti-Phishing Working Group at reportphishing@apwg.org. If you receive a phishing SMS text, forward it to SPAM (7726).
- Report the phishing attack to the FTC at ftc.gov/complaint.
- Mark the email as spam. This reminds your email provider or network to automatically direct emails from this address straight to the bin.
- If the sender has a Gmail address, you can also report it to Google so they can deactivate the account. Simply click those three little dots beside the Reply button and look for the option Report as a phishing email.
So, you’ve identified phishing and even reported it. Great job! Now, you need to learn the best ways to prevent phishing attacks.
How to prevent phishing attacks
The ways online criminals attack internet users are constantly evolving, but there are steps you can take to stay protected from phishing attacks:
- Use spam filters. This will intelligently filter out the spam, automatically sending phishing emails to the spam folder.
- Configure browser settings. In many web browsers, the phishing and malware detection option is turned on by default. So if you’re being redirected to suspicious websites, you should see a warning message.
- Change your browsing habits. When purchasing online deals, don’t hesitate to contact the company personally before entering any personal details.
- Hover over the URL first if you received it in a suspicious email. A secure website address will always begin with HTTPS. Now, go back to the beginning of the article and take a look at the account recovery link provided…
Forming a habit of responsible browsing takes effort, but the result is definitely worth it. These steps are easy to make, and they pay tenfold in the long run.
How to avoid phishing attacks
Be careful when you get an email from an unknown sender asking for personal information such as your phone number or login credentials. If you get this type of email:
- Don’t follow any links or provide personal information until you are sure the email is real.
- Report any suspicious-looking emails using one of the methods above.
When you get an email that looks like a phishing attack, here are a few things to look out for:
- Check if the email address and sender name match.
- Check if the email domain is authenticated.
- Check the message headers to make sure the "from" header isn't showing an incorrect name.
In the end, all you really need is a bit of common sense and to avoid acting on impulse. Make staying on constant lookout your ingrained habit when browsing — it takes much less effort to prevent phishing than dealing with the consequences. Don't forget—Clario Anti Spy can help protect your phone from data breaches, and with 24/7 tech support, you can always get help if you're unsure about anything.


