Table of contents
- What is a macro virus?
- How does a macro virus work?
- How do macro viruses spread?
- What is Microsoft doing about this problem with macros?
- What are some macro virus examples?
- Concept
- Melissa
- Attack on Macs
- How do I know if my computer is infected with macro virus?
- How to prevent a macro virus attack?
- Conclusion
It’s a day like any other. You’re going through your inbox. You open an email from a friend and they’ve attached a Word document. Looks interesting! You download it, open it and…
This is how quickly you can be tricked into infecting your computer with a macro virus. Once on your computer, it can carry out a number of malicious actions such as infecting your email contacts, stealing your passwords, and even gaining control over your webcam.
Macro viruses are still a common and effective attack method because they rely on trusted documents and human error rather than software flaws. In this article, you’ll learn how macro viruses work, how they spread through everyday files, how to recognize the warning signs, and what practical steps you can take to prevent them from infecting your computer.
But don’t worry, we’re here to show you how to prevent macro viruses from infecting your devices.
What is a macro virus?
Definition
A macro virus is malware embedded in document files that runs automatically when macros are enabled, allowing attackers to execute harmful actions without installing traditional software programs.
A macro virus is a piece of malicious code written in the same macro language used in everyday applications, such as Microsoft Word, Excel, and Powerpoint. The attack code commonly hides in documents and spreadsheets and is activated as soon as you open the file.
Once the macro virus has infected one of your applications, it triggers malware designed to cause damage to your computer and further spread the virus. Since the code runs on software and not on operating systems, it can infect any computer, even your Mac.
How does a macro virus work?
A typical macro virus attack follows a predictable sequence:
- A user receives a document containing hidden malicious macros.
- The document is opened and prompts the user to enable macros.
- Once enabled, the macro executes its embedded code.
- The macro downloads or activates additional malware.
- The infection spreads to other documents or contacts on the device.
To unleash macro viruses, cybercriminals create a malicious code, insert it into documents, and then trigger it to run as soon as you enable any macros. To better understand how it works, let’s discuss what a macro is.
A macro (short for “macroinstruction”) is a kind of code designed to instruct applications like Excel and Word to perform certain actions. Macros are intended to make your life easier by speeding up or eliminating repetitive tasks.
⚠️ Security warning
Attackers often disguise malicious macros as legitimate document features. Messages such as “Enable Content to view this document correctly” or “Macros must be enabled to see the full file” are common social engineering tactics used to trick users into activating malware.
For example, a real estate agent may need to add a client’s personal information to multiple documents every time he sells a house. The agent can use Microsoft Word’s macros to record and automate the frequently used formatting settings. This way, he can fill up numerous documents with the press of a button and save valuable time.
Now here comes the caveat: malicious macros can be created just as easily as helpful ones. But instead of instructing applications to perform helpful tasks, a macro virus wreaks havoc on your computer by setting destructive activities in motion. It could end up corrupting your data, reformatting the hard drive, and creating new files.
How do macro viruses spread?
Macro viruses spread easily and silently. First, they infect other documents on your computer. If you send one as an attachment in an email, you will have inadvertently sent the virus to your recipient. Secondly, a macro virus can quickly gain access to your email contacts, then resend the infected document to your contacts on your behalf. This is known as a phishing email.
You may be wondering how a macro virus can end up on your computer. Unfortunately, it’s surprisingly easy to pick one up when you’re going about your daily online business. You may catch malicious macros from the following sources:
- Phishing emails with infected attachments
- Files from the internet
- Files from a home network, company intranet, or public Wi-Fi
- Files stored on external storage devices like flash drives, hard drives, and discs
These sources spread macro viruses in different ways:
- Email attachments: Infected Word or Excel files execute malicious macros once opened and enabled.
- Downloaded files: Documents from unverified websites may contain hidden macros designed to run automatically.
- Shared networks: Infected documents stored on shared drives can spread when accessed by multiple users.
- External storage: Macro-infected files on USB drives or external disks can transfer the infection between devices.
Hackers use social engineering techniques or psychological manipulation to get people to click on malicious links or infected files lurking in your email or on a USB flash drive your friend lent you.
What is Microsoft doing about this problem with macros?
Macros in Microsoft Office used to be enabled by default. However, following increasing numbers of macro virus attacks, Microsoft made the decision to disable them.
Now, macros are disabled by default in all versions of Microsoft Office, from 2000 onwards. When you open a document containing macros, Office will ask you if you’d like to enable them.
In newer versions of Microsoft Office, documents downloaded from the internet or received via email may also open in Protected View, which restricts editing and blocks macros by default. These additional safeguards are designed to prevent macros from running unless a user explicitly trusts the file.
This certainly reduces the risk that you’ll catch a macro virus. However, cybercriminals are nothing if not persistent and still find ways to trick users into enabling macros and infecting their devices with malware.
What are some macro virus examples?
Editor's note
Although many well-known macro viruses first appeared decades ago, these early attacks laid the groundwork for modern macro-based malware that still targets users today.
Macro viruses had their heyday in the nineties. With the growing sophistication of antivirus software, hackers are reviving their old tricks — with a twist.
Here are some examples of macro viruses that have wreaked havoc on our digital world.
Concept
In 1995, a virus called Concept became the first macro virus to spread through Microsoft Word. Microsoft shipped out hundreds of CD-ROMs called “Microsoft Compatibility Test” that accidentally included the virus. From there, users inadvertently spread the virus via infected email attachments.
While Concept didn’t have the capability to send itself via email, it was a forerunner to the Melissa virus, which very effectively diffused itself.
Melissa
In 1999, the Melissa virus spread via an infected Word document through email. The email contained the message:
“Here is the document you asked for … don't show anyone else ;-).”
The attachment was usually called list.doc. When the recipient opened the document, the virus infected their computer and sent itself to the first 50 people in the user’s email address book. It caused the virus to spread rapidly with estimates suggesting it went on to infect more than a million computers.
Attack on Macs
In 2017, hackers created a macro virus specifically targeting Macs. The virus spread via email in a macro virus-infected Word document titled “U.S. Allies and Rivals Digest Trump's Victory — Carnegie Endowment for International Peace.docm.”
When the user opened the document they would see the familiar dialogue box inviting them to enable the document’s macros. Doing so infected the user’s computer with malware, allowing hackers to access the user’s browser history, monitor webcams, and steal passwords and encryption keys.
Explainer
These examples show how macro viruses have evolved rather than disappeared. Today, attackers continue to use macros because they exploit trusted software, rely on user interaction instead of system vulnerabilities, and can serve as entry points for more advanced malware attacks.
How do I know if my computer is infected with macro virus?
Macro viruses are tricky to detect. You may only realize your computer is infected once you start getting calls from your contacts asking about a strange email you supposedly sent.
Here are some other macro virus symptoms to look out for are:
- Your computer is running slower than usual
- Strange changes being made to your documents
- Menu items missing from your software application
- The appearance of unusual dialog boxes you don’t normally see
- Your computer saving files as “templates”
- Your computer asking you for passwords to access files that are not usually password protected
Needless to say, macro viruses can greatly affect the performance of your computer so it's important that you learn how to prevent them from infiltrating your device.
Note
It’s important to note that macro viruses rely on user actions to run. They cannot activate on their own without a document being opened and macros being enabled, which is why cautious file handling remains one of the most effective defenses.
How to prevent a macro virus attack?
Hackers use cunning tricks, so manually removing a macro virus isn’t easy. That’s why macro virus prevention is by far the most effective way to avoid an attack. Here are some simple, yet highly effective actions you can take now to enhance your protection.
- Use a dedicated anti-spy protection app. Some macro-based attacks are designed to install spying software or abuse app permissions rather than behave like traditional malware. Clario Anti Spy helps detect this kind of hidden threat on mobile devices.
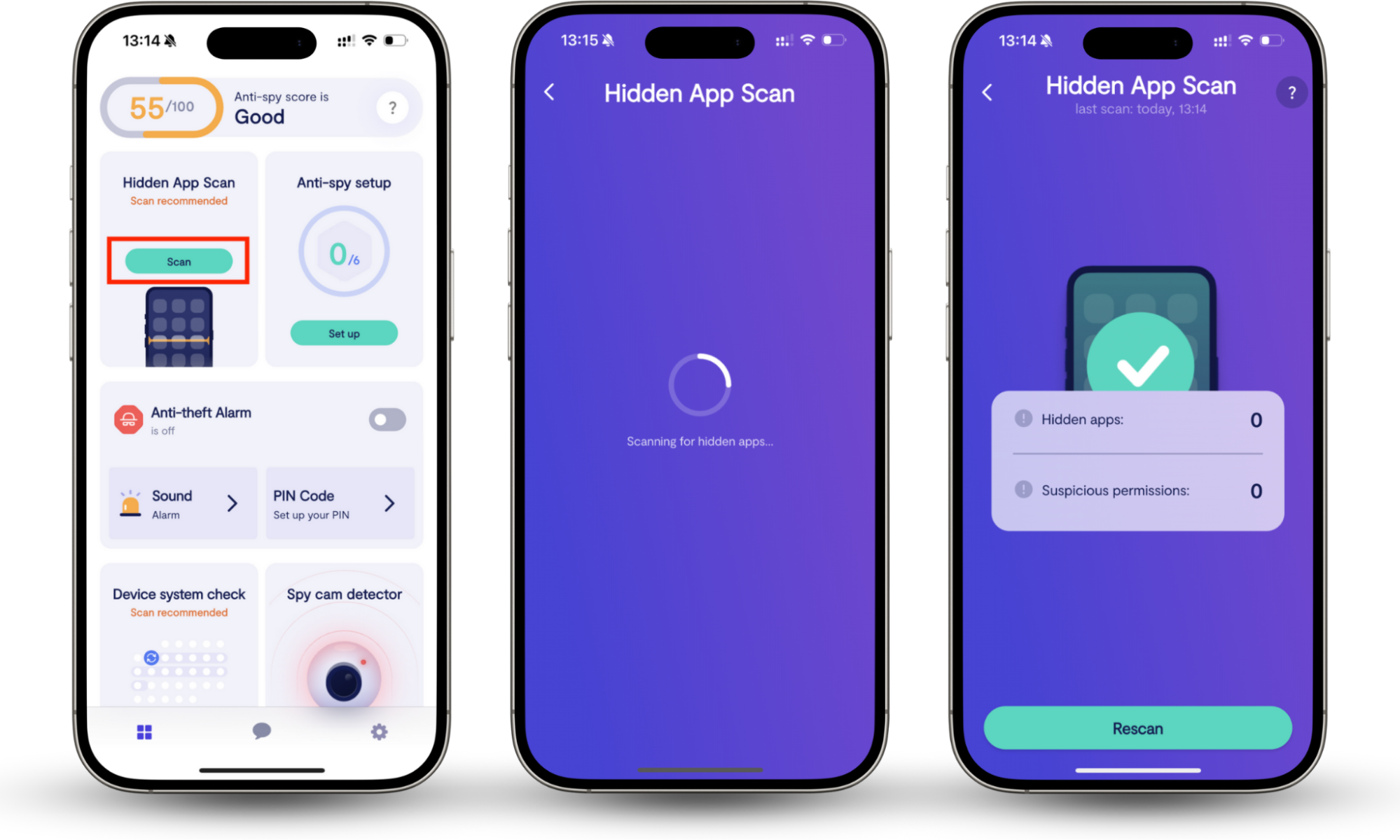
Clario Anti Spy is available for iOS and Android and includes a Hidden app scan that analyzes your device for signs of spyware, stalkerware, or monitoring apps that may be secretly installed. It also reviews app permissions to help identify suspicious access to messages, files, or system features.
If you are concerned about actual threats on your phone, use Clario Anti Spy to check for malicious software:
- Open Clario Anti Spy and select Scan under the Hidden app scan feature.
- Clario will run a full scan of your mobile device. This looks for signs of spying apps, like spyware and parental control apps that someone may have secretly installed.
- Review the results. The tool analyses all requested app permissions, helping you to detect suspicious ones that don’t belong.
- Filter out phishing emails. The fewer spam emails you come across, the less chance you’ll be tricked into downloading something you shouldn’t.
- Update all software and patches. Always keep your operating system and programs up to date for maximum security.
- Don’t open attachments from unknown senders. Why would this person have your email address? Always avoid opening emails from people you don’t know.
- Don’t open suspicious-looking attachments, even if they’re from someone you know. This is a very common way for macro infection to spread.
- Avoid clicking on banner ads. It’s possible you could download a document containing a macro virus by clicking on malicious links in ads. Be careful what you click.
- Make sure macros are disabled on your Microsoft Office programs. And don’t allow cybercriminals to trick you into enabling them.
You can disable macros on Microsoft programs by following these steps:
- Go to the Word or Excel Menu.
- Choose Preferences from the dropdown options.
- Click on Security.
- Select Disable All Macros Without Notification.
Conclusion
Macro viruses are now more sophisticated than when they first came out in the nineties. They’re more damaging and can even be used to activate other malware attacks.
These viruses hide behind the cloak of trusted applications, so avoiding them may not always be easy. Now more than ever, you need to make sure you’re taking extra precautions and that you’re armed with the right antivirus software.
For added protection, tools like Clario Anti Spy can help uncover risks that may go unnoticed after an attack. Its Hidden app scan checks your mobile device for spying or suspicious apps that could be silently accessing your data, helping you identify potential threats early and regain control over your privacy.


