Table of contents
- What is a hacker?
- What data do hackers want to steal?
- Personally identifiable information (PII)
- Internet activity and browsing habits
- Emails and social media
- Data that enables access to connected devices
- How to know that you’ve been hacked
- How to protect your device from hackers: general tips
- Public Wi-Fi
- Secure passwords
- Encrypted websites
- Two-factor authentication
- Regular updates
- Cloud backups
- Reliable security app
- How to protect your online accounts
- How to protect your phone
- How to secure your computer
- Wrapping up
When was the last time you chatted online using public Wi-Fi? And are you sure that your chat remained private?
In the United States alone, there were 1001 data breaches in 2020, with over 155.8 million people affected. Over 60% of all data breaches are the result of either hacking or malware. It’s no surprise that Americans are now more concerned about their cybersecurity than physical crimes.
Feeling uneasy? Don’t be! Clario knows how to improve your cybersecurity no matter what device you use. In this article, we’ll talk about hacking and how to protect yourself on the internet.
What is a hacker?
A hacker is a tech expert who can solve a problem in a non-standard way by using their computer, network, or other technical skills. Today, the term may also refer to criminals using their skills to steal personal data or gain unauthorized access to systems.
By the way, along with their tech “voodoo,” hackers can also use psychological manipulation to trick people into revealing data or giving access to their devices. This is known as people hacking or social engineering.
What data do hackers want to steal?
Believe it or not, your device contains tons of valuable data that can be used or sold by hackers around the world:
- Personally identifiable information (PII)
- Internet activity and browsing habits
- Emails and social media
- Data that enables access to connected devices
Let’s now get the lowdown on each type:
Personally identifiable information (PII)
As the name suggests, PII is any information that can identify you. It may include your name, physical and email addresses, date of birth, marital status, information about family members, education, employment, social security numbers, and even medical records. By purchasing online, you also potentially expose your financial credentials and credit card information (numbers, expiry dates, secret codes) to criminals.
Why is it dangerous? With all this data at hand, hackers can hijack your online accounts and steal your identity. They can take money from the bank, track all your transactions, open a credit card, make purchases in your name, or sell your data on the dark web.
Internet activity and browsing habits
The internet service provider monitors your activity, while browser plugins and website cookies can track what pages you visit.
Why is it dangerous? Such practices are intrusive and can go too far, especially when it comes to advertising targeting. Without you knowing, cookies will transfer your ID data across different devices and platforms.
Emails and social media
Emails give access to all the accounts you have signed up to. Together with social media, it’s a perfect source of private communication records, including confidential business documents, personal videos, and others.
Why is it dangerous? An email breach often snowballs into a bigger problem with many accounts involved. Besides, all your contacts and private communication, including photos, videos, and confidential documents, can end up in the wrong hands.
Data that enables access to connected devices
Printers, Wi-Fi routers, keyboards, and even your webcam can be subject to a cyberattack.
Why is it dangerous? With access to your printer, criminals can review all the information you scan. A hacked router can make the whole home network vulnerable to attacks. Finally, by controlling your webcam, a hacker can spy on you and record your private life.
With all these opportunities your devices provide to criminals, it’s crucial to enhance your cybersecurity just like you ensure the safety of your house by locking the front door. The good news is that you don’t need to be a computer geek to stay on the safe side. But firstly, let’s learn how to recognize when you’ve been hacked.
How to know that you’ve been hacked
If you notice that your device is acting up, here’s what to pay heed to:
- Your device is overheating
- The battery is draining fast
- There are too many annoying pop-ups (even on a lock screen)
- You see new apps that you don’t remember downloading
- You notice unexplained transactions or unauthorized changes in your accounts and credit cards
Malware often triggers phishing pop-ups and worse device performance, so these are two obvious signs that something has gone wrong. To avoid this in the future, follow our detailed guide with practical tips on how to protect yourself from hackers.
How to protect your device from hackers: general tips
Regardless of whether you use a laptop or smartphone, there are some tips on how to avoid hacking that will work equally for both. Here are:
- Public Wi-Fi
- Secure passwords
- Encrypted websites
- Two-factor authentication
- Regular updates
- Reduced digital footprint
- Cloud backups
- Reliable security app
Let’s explore them in more detail.
Public Wi-Fi
A public network is extremely vulnerable and easy to hack. Just like you don’t need credentials to connect to Starbucks Wi-Fi, nor does the criminal! Keep this in mind and avoid purchasing online or accessing any personal or financial data when using public Wi-Fi, unless you use security apps like Clario Anti Spy.
If you’ve ever connected to public Wi-Fi and then noticed strange behavior on your device, it’s worth checking it for spyware. Clario Anti Spy helps you scan for hidden threats that might’ve slipped in and alerts you if your device has been compromised.
Secure passwords
We know you aren’t a fan of long passwords. Who is? But if you want to protect yourself from hackers, using your date of birth for both your Instagram and bank accounts is definitely not a brilliant idea.
Opt for long (at least eight, but better 16-20 characters) passwords with a mix of upper and lower cases, characters, symbols, and numbers. Create unique and secure passwords for your accounts and never use auto-complete. If the idea of long passwords makes you roll your eyes, consider using a password manager that will automatically generate and store bullet-proof passwords for you. And never, never use the same passwords for different accounts.
Encrypted websites
Don’t fret! Using encryption tools doesn’t require any technical skill from you. You already use them when texting a friend on WhatsApp, calling your granny via Skype, or enabling secret conversations on Facebook.
When browsing, trust websites with a padlock sign at the beginning of the address bar. A padlock means that this website uses SSL/TLS protocols to encrypt the data between your browser and the server. Simply put, this means that a hacker will need to invest some serious effort to infect your device with malware.
Two-factor authentication
Have you ever received a verification code to your smartphone when accessing an account? If yes, you know what two-factor authentication means. If hackers hijack your credentials, this feature will prevent them from entering your device remotely.
Most modern apps, including banking, finance, social media, and others, enable two-factor authentication or two-step verification for better security. Check settings and turn this feature on where possible.
Regular updates
Updates can be annoying and time-consuming but they are crucial if you want to keep your system’s security at its highest level. Usually, an update fixes the system or app’s vulnerability that hackers have newly found.
You can consider enabling auto-update to ensure your device has the most recent security protection. Keep in mind that third-party apps should be updated regularly, just like the entire system.
Reduced digital footprint
Pay attention to the information you put online on your social media channels: they collect more data about you than any other app (read this if you need the stats). The less information hackers can collect about you, the more secure you are.
Here are several tips that you can follow to enhance your security:
- Turn off location tracking and auto geotagging. Use them only when needed.
- Check all automatic features in social media and other accounts and disable what you don’t need (for example, you may not need Google to log your travel plans in the calendar automatically).
- Unsubscribe from old or unwanted services and emails.
- Keep your accounts private and restrict the content to real friends only.
- Pay attention to friend requests. If possible, restrict who can send you these requests.
- Never share personal or account-related information: be careful with what you post on social media and what you tell others. And be careful with photos: don’t show any identifying information such as addresses or phone numbers.
Cloud backups
Back-ups aren’t about security but rather about being prepared for the worst. If your data is stolen, you will still have a chance to restore it from cloud storage.
You can always check cloud storage comparison articles online to find the best one.
Reliable security app
When it comes to protecting your digital life, a reliable security app makes all the difference. Clario Anti Spy helps you spot suspicious behavior, check your device for hidden spyware, and protect your personal data from being misused, all in a few simple steps.
Here’s how to protect your device with Clario Anti Spy:
On Android:
- Install Clario Anti Spy.
- Create an account and subscribe.
- Tap Spyware scan to check for hidden threats.
- Follow the steps to remove anything suspicious.
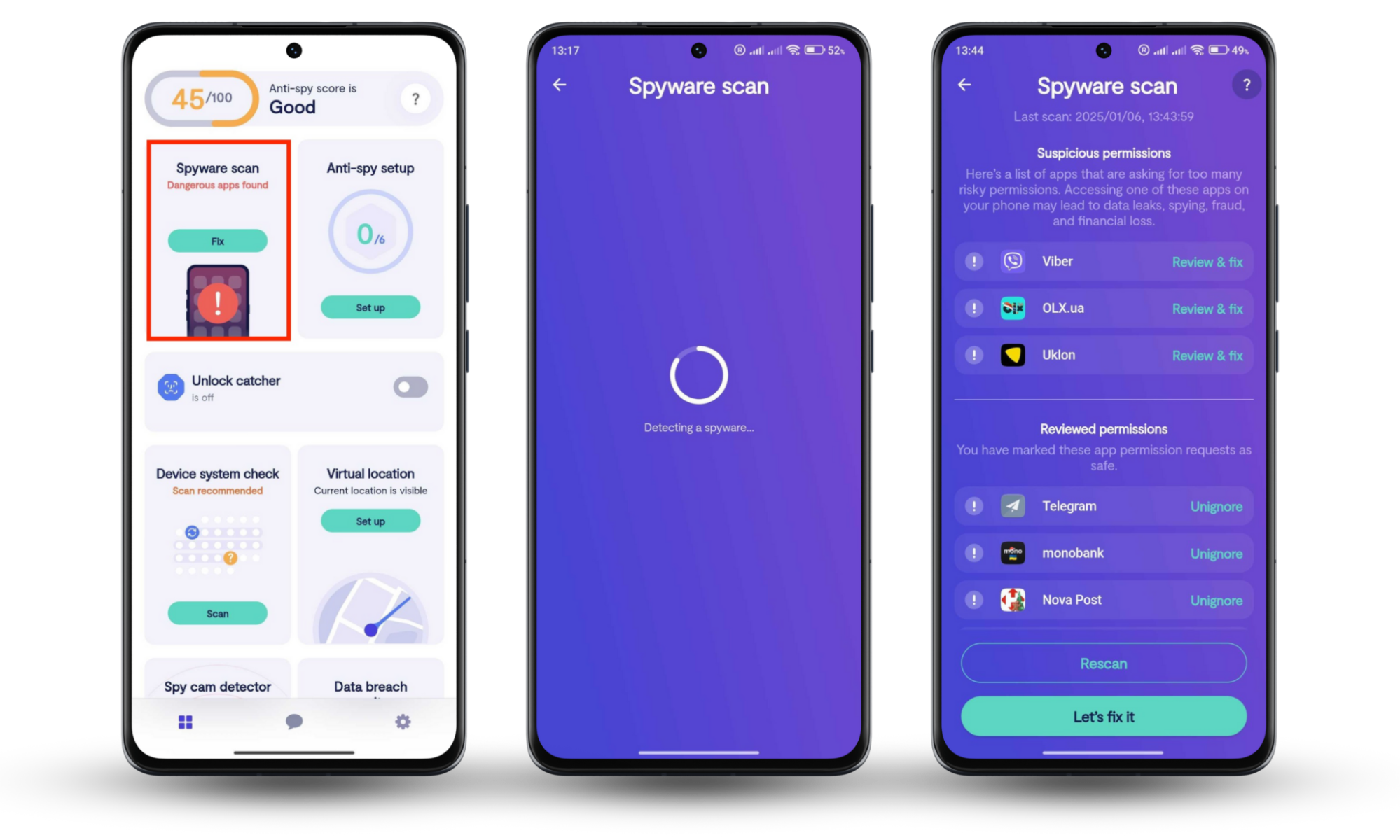
On iOS:
- Install Clario Anti Spy.
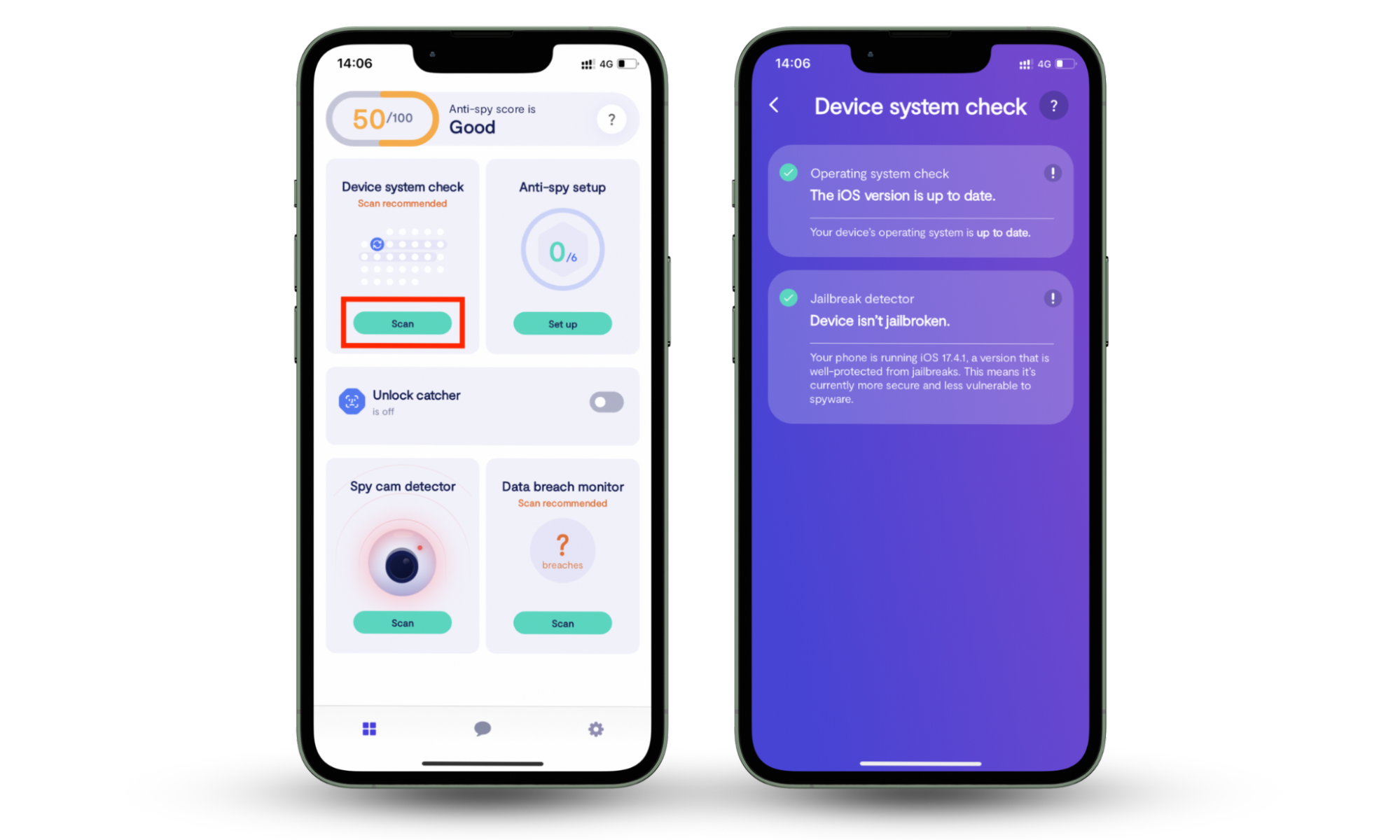
- Create an account and subscribe.
- Tap Device system check to scan for vulnerabilities.
- Follow any recommendations shown.
These are common tips to help you ensure higher protection from hackers. Along with them, make sure that you know how to protect yourself on the internet.
How to protect your online accounts
When browsing or working online, you need to protect your accounts and avoid phishing links or apps. This is how you can do it:
- Follow the general security tips we mentioned above: they work for all devices, be it on a phone or computer.
- Don’t link accounts: don’t sign in using your Google, Facebook, LinkedIn, or another app. Data breaches happen to companies of all levels, even giants like Facebook or Twitter (check if your email was exposed to a breach here).
- Always log out after finishing using an account, especially if you’ve been using via public network.
- Be attentive to what you click or download: if you aren’t sure about the source, don’t click.
- Be aware of cybersquatting and typosquatting. These are fake websites that look similar to famous domains (amzon.com instead of amazon.com; goggle.com instead of google.com, etc).
- Recognize phishing pop-ups, emails, and messages. Never click links or open attachments coming from them.
- Avoid websites with many redirects, automatic downloads, or pop-ups in the background.
- Don’t trust any site’s announcements about big prizes or unrealistic discounts — no one ever gives you a penny for free.
These simple rules will help you protect yourself from hackers. However, don’t underestimate the risk: once you open a spammy or malicious website, chances are, your device has been infected. Run your anti-malware app whenever you feel uncertain, or enable automatic real-time scanning to maximize your online security. If you’ve noticed that your email has been hacked, follow this guide to avoid more significant loss and protect other accounts.
Now that you know all the general tips, let’s move to device-specific ones and learn how to prevent phone hacking.
How to protect your phone
Here is what you can do to prevent phone hackers from attacking your device, be it Android or iOS:
- Follow the general security tips we mentioned above
- Use built-in phone protection: device tracking services, automated wipe after a set number of the wrong password tries, etc.
- Set a passcode or fingertip scanning to access the phone
- Never jailbreak or root your phone, as it can disable its default security
- Download apps only from reliable sources, such as App Store and Google Play
- Control and manage app permissions (access to camera, microphone, location, and your contacts)
- Regularly delete your browsing history, including cache and cookies
- Disable group photo sharing and automatic backups. Back up manually, and better if you do it from a laptop
Smartphones are vulnerable to hacking, especially Android devices that have inconsistent development standards and are more fractured than iPhones. Yet, it doesn’t mean that iPhone owners have nothing to worry about. Phishing attacks on Apple have more than doubled in 2019, and the number of fake emails (claiming to be from the developer) is growing by up to 40% per year.
This means that the risk is real, no matter what phone you use. Take the bull by the horns and leave cybercriminals empty-handed.
In the next section, we’ll talk in more detail about how to protect your computer from hackers.
How to secure your computer
Your computer security will only win against the scammer if you use all the tips we mentioned above. Here are some more things you can do specifically for your PC:
- Regularly run anti-malware scanning.
- Only download apps from reliable sources.
- Be attentive to sudden performance changes and check your C: drive (C:/Program File, C:/Program Files (x86), C:/Users/Downloads, etc.) for suspicious files or apps.
- Use special software for uninstalling because some malware isn’t easy to delete from your PC. Ensure that your software deletes hidden traces, including shortcuts and cache.
- Encrypt your hard drive to ensure that no one can use your data even after stealing it (you can opt for BitLocker for Windows and FileVault for MacOS).
- Shut down your computer after work. All-time running ruins your computer’s performance and opens the door to cyberattacks.
Following these simple rules will significantly reduce the chance that hackers can steal your data. However, ensuring high protection against hackers for your computer won’t be easy without the right software for malware screening, uninstalling, and data encryption.
Wrapping up
Your best protection against losing your data is remaining alert and having reliable software tools at hand. No matter how attentive you are, hackers always lurk in the shadows waiting for the right time to attack.
For this reason, always keep your guard up! Or let a top-notch security app like Clario Anti Spy do all the work for you. Сhange your digital life security for good.


