Table of contents
- Types of identity theft
- Existing account takeover
- Synthetic identity theft
- Social Security identity theft
- Financial identity theft
- Tax identity theft
- Estate identity theft
- Medical identity theft
- Employment identity theft
- Criminal identity theft
- Senior identity theft
- Child identity theft
- How to Prevent Identity Theft
- Prevent different types of identity theft with Clario Anti Spy
Types of identity theft
There are several signs of when thieves commit identity theft—receiving bills for items you didn't buy, debt collection calls for accounts you didn't open, etc. Although there can be clues, one of the biggest problems with identity theft is that fraudsters can use your identity for years without you noticing.
According to the 2022 Identity Fraud Study, over 27 million consumers lost over $28 billion through identity fraud scams in the US in 2021. With this, it's no wonder that protecting your data from identity theft matters more than ever.
Aside from regularly checking your credit reports and financial statements for signs of unauthorized activity, you can do plenty of other things to prevent someone from stealing your identity online.
In this list, we've listed some of the most common types of identity theft you should watch out for, how each of them is different, and what to do when it happens:
- Existing account takeover
- Synthetic identity theft
- Social Security identity theft
- Financial identity theft
- Tax identity theft
- Estate identity theft
- Medical identity theft
- Employment identity theft
- Criminal identity theft
- Senior identity theft
- Child identity theft
Existing account takeover
When it comes to an existing account takeover or ATO fraud, a criminal not only gains access to your digital accounts but also modifies your personally identifiable information (PII). For example, hackers can change passwords, request a new card, or add an authorized user to your accounts.
Unfortunately, account take-overs can be difficult to undo, especially involving financial losses. In fact, it can be challenging to prove that you are the original owner of an account and it may be a lengthy process. To regain account access, you need to contact support in each platform and make your case for identity theft.
Synthetic identity theft
Unlike an existing account takeover, synthetic identity theft occurs when someone knows your personal information, which can be your full name, address, date of birth, etc., and uses it to create brand-new accounts under your name.
For example, fraudsters can use false and actual data or even different pieces of personal information from several individuals to create a fake identity. Aside from opening accounts, hackers can also use these fake identities to put up professional practices, dating profiles, etc.
To make sure no one uses your details to open accounts, avoid sharing your personal information unnecessarily. If possible, make fake names or contact details for sketchy sites.
Social Security identity theft
By using someone else's Social Security Number (SSN), thieves can avoid paying withholding taxes. Fraudsters can pretend to be legitimate contractors to claim the tax compensation.
If fraudsters use your SSN to open an account with a false name and address, the chances of it appearing on your credit report are low. Yet, the primary victims of synthetic identity theft are creditors and retailers, who may face financial losses.
To keep impersonators away from your SSN account, never post it online or even share it with people you know.
Financial identity theft
One is the most common type of identity theft; financial identity theft happens when cybercriminals use your PII to access your financial information, records, and accounts. For example, hackers can use your identity to enter your bank account or use credit card numbers to withdraw money from your accounts, take out loans, or make purchases.
Unfortunately, victims of financial identity theft can be held responsible for all the purchases, unpaid bills, loans, or other transactions made under their name.
To avoid financial identity theft, check your bills, accounts, and statements regularly to protect yourself from financial losses. And, if you notice credit or debit charges you didn't make, contact your bank or credit card company immediately.
Tax identity theft
While there is always the temptation to outsource tax filing, it's essential to make sure the person you trust your tax information with is a legitimate, registered professional. In some cases, cybercriminals steal your tax identity to steal your tax returns.
A clear warning sign that your identity has been stolen is if someone else has already filed a tax return under your name or when the IRS rejects your tax return. So, if you don't want to fall victim to this scheme, remember the IRS never initiates contact with taxpayers to request financial information through social media or call. Besides, the IRS always notifies you of any suspicious return bearing your name and SSN by sending you an official email.
Estate identity theft
While no one plans untimely death, thieves often prey on people who experience them. When a deceased person doesn't make the proper preparations, hackers can target their accounts, withdraw their money, get their benefits, and more.
To help prevent estate identity theft, you should create a last and will testament that specifies how your loved ones should handle your finances after you pass, even as a young person. In addition, you should notify credit bureaus and financial institutions immediately after a relative's death.
Medical identity theft
While other forms of identity theft can be a source of inconvenience, medical identity can be potentially life-threatening. Scammers can charge your insurance for medical services or prescriptions you didn't receive through medical identity theft. With this, insurance companies can deny your life-saving treatments if the bills exceed the limits of your medical coverage.
According to IDX, stolen health information is worth up to 50 times more than financial information, with victims of medical identity theft paying up to $13,500 in 2021. Medical identity theft can put your health at risk when it turns out someone else's diagnosis is in your medical file. Medical identity theft could also potentially impact your insurance price premiums, and the treatments recommended to you by your physicians.
To be safe, always check your medical records with your doctor to ensure their accuracy. In addition, if you start receiving unexpected medical bills, be sure to raise a dispute as soon as possible.
Employment identity theft
Aside from your Social Security Number (SSN), scammers can also use other types of PII to apple for a role or pass a background check. Afterward, these fraudsters can use this information to collect income, including taxes the IRS will demand from you.
To discover employment identity theft before the IRS sends you a tax bill, use the e-Verify website and review all the employers that have checked your records. And, if there are any unfamiliar ones, be sure to contact the Federal Trade Commission to get advice or a personal recovery plan.
Criminal identity theft
No one wants to end up in jail, and cybercriminals aren't an exception. For this reason, criminals will use various means of avoiding justice, including stealing someone's identity and framing this poor person. Afterward, clearing your name gets more problematic when the evidence points to your identity.
The worst part of this type of identity theft is that you won't be able to detect it until there are consequences—from an unpaid speeding ticket, turning down a job, or even an arrest. If this happens to you, the only thing you can do is contact law enforcement immediately.
Senior identity theft
Seniors are less likely to monitor their accounts regularly and tend to be more trusting, making them ideal victims for identity thieves. Seniors may have social benefits, financial savings, and limited technical knowledge. So, we recommend seniors place a security freeze on their credit reports or even lock them if they aren't in use.
But most importantly, younger family members should try to educate the older generation about cybersecurity. Thankfully, Clario's blog is the perfect source for that.
Child identity theft
Sadly, children are also at risk of identity theft. Cybercriminals can steal information from school databases, store accounts, or even access it from social media. Besides, most children under 16 have blank credit reports, which means fraudsters can open credit accounts under their names undetected.
Unfortunately, it may take years to uncover a crime until a victim applies for a job or student loan. To determine if your child's information is being misused, check for a credit report with three nationwide credit bureaus (Equifax, Experian, and TransUnion).
If you spot something suspicious, go to IdentityTheft.gov to report and recover from identity theft. As much as possible, it is also good to remind children not to overshare personal information online.
How to Prevent Identity Theft
When it comes to identity theft, one of the biggest threats is the time it takes to identify it. Once thieves steal your data, they can use it in various fraudulent activities.
While it can be terrifying to suspect identity theft, there are things you can do to prevent identity theft. However, the most convenient way to protect yourself from having your identity stolen by hackers is by investing in software like Clario Anti Spy.
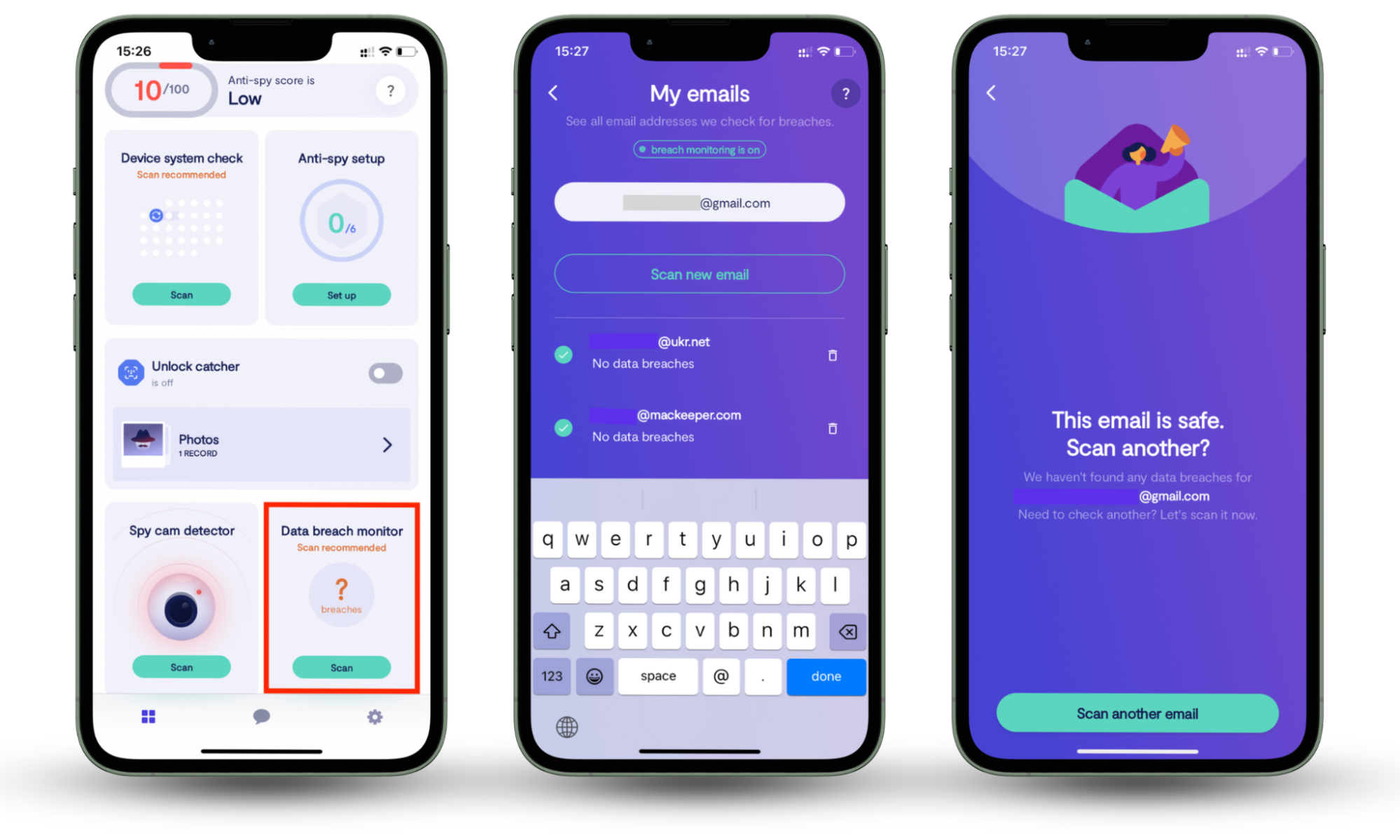
Even in your sleep, you can use Clario Anti Spy's 24/7 Data breach monitor to track multiple email addresses for possible identity theft.
Here's how to use Clario Anti Spy's 24/7 Data breach monitor:
- Download Clario Anti Spy, get a subscription, and set up an account.
- Once you’re in the app, click Scan under the Data breach monitor option.
- Now select Check for breaches at the bottom of the section. Clario Anti Spy will let you know if your email address was included in a breach. If so, follow its instructions to secure it.
- Click on Scan another email to repeat the process for another email address you want to monitor.
Prevent different types of identity theft with Clario Anti Spy
The thought of your identity being stolen is scary, but it’s a very real possibility. For this reason, responding as quickly as possible to a breach is imperative to prevent identity theft and other consequences, like financial losses.
Clario Anti Spy understands this, which is why its Data breach monitor checks for data leaks containing your email in real time, so you can secure it and all accounts linked to it urgently. Use Clario Anti Spy’s Data breach monitor to stay on top of breaches affecting you and prevent identity theft.


